Microsoft 70-697 Practice Test





You plan to deploy a Microsoft Azure RemoteApp collection by using a custom template image. The image will contain Microsoft Office 365 ProPlus apps. You need to ensure that multiple users can run Office 365 ProPlus from the custom template image simultaneously.
What should you include in the configuration file?

configured to automatically back up files by using File History. The user of the computer
uses the OneDrive desktop app to sync files. The Previous Versions settings from the local
group policy of the computer are shown in the following graphic.

configured to automatically back up files by using File History. The user of the computer
uses the OneDrive desktop app to sync files. The Previous Versions settings from the local
group policy of the computer are shown in the following graphic.

A company has 10 portable client computers that run Windows 10 Enterprise. The portable client computers have the network connections described in the following table.

None of the computers can discover other computers or devices, regardless of which connection they use. You need to configure the connections so that the computers can discover other computers or devices only while connected to the CorpWired or CorpWifi connections. What should you do on the client computers?
Your company upgrades a research and development department workstation to a Windows 10 Enterprise computer. Two of the workstation's folders need to be encrypted. The folders are named \ProtectedFiles and \Backups.You attempt to encrypt the folders. The output is shown in the following exhibit.

Your company upgrades a research and development department workstation to a Windows 10 Enterprise computer. Two of the workstation's folders need to be encrypted. The folders are named \ProtectedFiles and \Backups.You attempt to encrypt the folders. The output is shown in the following exhibit.

You have a computer that runs Windows 10 Enterprise that contains the following folders:

You have a local user named User1. User1 has read and execute permission to Folder1.You need to ensure that User1 can perform the following tasks.
- Create new files in Folder2.
- Edit all files in Folder3.
- Change the permissions of files in Folder5.
The solution must use the principle of least privilege. Which permissions should you assign to User1 on each folder? To answer, drag the appropriate permissions to the correct folders. Each permission may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
You have a computer that runs Windows 10 Enterprise that contains the following folders:

You have a local user named User1. User1 has read and execute permission to Folder1.You need to ensure that User1 can perform the following tasks.
- Create new files in Folder2.
- Edit all files in Folder3.
- Change the permissions of files in Folder5.
The solution must use the principle of least privilege. Which permissions should you assign to User1 on each folder? To answer, drag the appropriate permissions to the correct folders. Each permission may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
You have a computer that runs Windows 10 Enterprise that contains the following folders:

You have a local user named User1. User1 has read and execute permission to Folder1.You need to ensure that User1 can perform the following tasks.
- Create new files in Folder2.
- Edit all files in Folder3.
- Change the permissions of files in Folder5.
The solution must use the principle of least privilege. Which permissions should you assign to User1 on each folder? To answer, drag the appropriate permissions to the correct folders. Each permission may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
You are setting up a Windows 10 Enterprise computer.
The computer’s network connections are shown in the Network connections exhibit. (Click the Exhibit button.)

The computer’s network settings are shown in the Network Settings exhibit. (Click the Exhibit button.)

Advanced TCP/IP settings are shown in the Advanced TCP/IP Settings exhibit. (Click the Exhibit button.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
The computer is a Microsoft Hyper-V host:
You are setting up a Windows 10 Enterprise computer.
The computer’s network connections are shown in the Network connections exhibit. (Click the Exhibit button.)

The computer’s network settings are shown in the Network Settings exhibit. (Click the Exhibit button.)

Advanced TCP/IP settings are shown in the Advanced TCP/IP Settings exhibit. (Click the Exhibit button.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
The computer has a static IP address:
You are setting up a Windows 10 Enterprise computer.
The computer’s network connections are shown in the Network connections exhibit. (Click the Exhibit button.)

The computer’s network settings are shown in the Network Settings exhibit. (Click the Exhibit button.)

Advanced TCP/IP settings are shown in the Advanced TCP/IP Settings exhibit. (Click the Exhibit button.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
The computer is a Microsoft Hyper-V virtual machine:
You manage 50 computers that run Windows 10 Enterprise. You have a Windows To Go workspace installed on a USB drive named USB1.You need to configure USB1 to meet the following requirements:
- When you run Windows To Go from USB1, you can see the contents of the computer’s internal drives from File Explorer.
- When you connect USB1 to a computer that runs Windows 10, you can automatically view the content of USB1 from File Explorer.
In the table below, select the action that must be performed to achieve each requirement.

You manage 50 computers that run Windows 10 Enterprise. You have a Windows To Go workspace installed on a USB drive named USB1.You need to configure USB1 to meet the following requirements:
- When you run Windows To Go from USB1, you can see the contents of the computer’s internal drives from File Explorer.
- When you connect USB1 to a computer that runs Windows 10, you can automatically view the content of USB1 from File Explorer.
In the table below, select the action that must be performed to achieve each requirement.

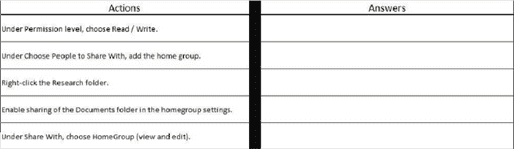
You administer Windows 10 Enterprise computers in your company network, including a computer named Wst1. Wst1 is configured with multiple shared printerqueues.Wst1 indicates hardware errors. You decide to migrate the printer queues from Wst1 to a new computer named Client1.You export the printers on Wst1 to a file. You need to import printers from the file to Client1.From the Print Management console, which Print Management node should you select? To answer, select the appropriate node in the answer area.

You have a Windows 10 Enterprise computer. The computer has a shared folder named \Marketing. The shared folder is on an NTFS volume. The current NTFS and share permissions are configured as follows.

UserA is a member of both the Everyone group and the Marketing group. UserA must access \Marketing from across the network. You need to identify the effective permissions of UserA to the \Marketing folder.
What permission should you identify?
You have a desktop computer and a tablet that both run Windows 10 Enterprise. The desktop computer is located at your workplace and is a member of an Active Directory domain. The network contains an Application Virtualization (App-V) infrastructure. Several App-V applications are deployed to all desktop computers.
The tablet is located at your home and is a member of a workgroup. Both locations have Internet connectivity. You need to be able to access all applications that run on the desktop computer from you tablet. Which actions should you perform on each computer?
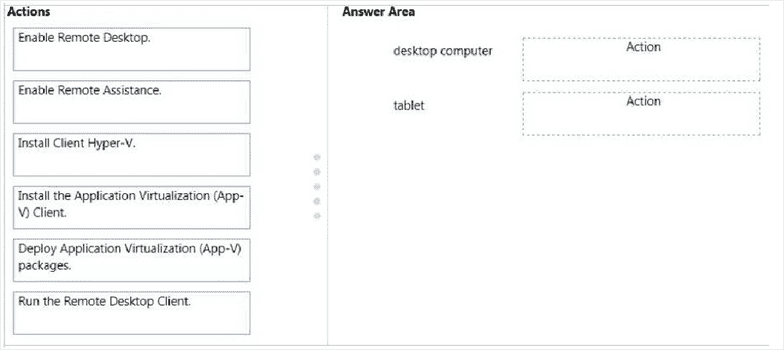
You have a desktop computer and a tablet that both run Windows 10 Enterprise. The desktop computer is located at your workplace and is a member of an Active Directory domain. The network contains an Application Virtualization (App-V) infrastructure. Several App-V applications are deployed to all desktop computers.
The tablet is located at your home and is a member of a workgroup. Both locations have Internet connectivity. You need to be able to access all applications that run on the desktop computer from you tablet. Which actions should you perform on each computer?

You manage 50 computers that run Windows 10 Enterprise. You have a Microsoft Azure RemoteApp deployment. The deployment consists of a hybrid collection named Collection1. All computers have the Hyper-V feature installed and have a virtual machine that runs Windows 7. You plan to install applications named App1 and App2 and make them available to all users. App1 is a 32-bit application. App2 is a 64-bit application. You need to identify the installation method for each application. The solution needs to minimize the number of installations. Which deployment method should you identify for each application? To answer, drag the appropriate deployment methods to the correct applications. Each deployment method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.

You manage 50 computers that run Windows 10 Enterprise. You have a Microsoft Azure RemoteApp deployment. The deployment consists of a hybrid collection named Collection1. All computers have the Hyper-V feature installed and have a virtual machine that runs Windows 7. You plan to install applications named App1 and App2 and make them available to all users. App1 is a 32-bit application. App2 is a 64-bit application. You need to identify the installation method for each application. The solution needs to minimize the number of installations. Which deployment method should you identify for each application? To answer, drag the appropriate deployment methods to the correct applications. Each deployment method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.

You have a server that runs Windows Server 2012 R2 server named Server1. Server1 has Remote Desktop Services (RDS) installed. You create a sessioncollection named Session1 and publish a RemoteApp in Session1.Server1 has an application named App1. The executable for App1 is \Apps\App1.exe.You need to ensure that App1 is available as a RemoteApp in Session1.What command should you run?

[First paramater]:
You have a server that runs Windows Server 2012 R2 server named Server1. Server1 has Remote Desktop Services (RDS) installed. You create a sessioncollection named Session1 and publish a RemoteApp in Session1.Server1 has an application named App1. The executable for App1 is \Apps\App1.exe.You need to ensure that App1 is available as a RemoteApp in Session1.What command should you run?

NewRDRemoteApp [second paramater]:
You have a server that runs Windows Server 2012 R2 server named Server1. Server1 has Remote Desktop Services (RDS) installed. You create a sessioncollection named Session1 and publish a RemoteApp in Session1.Server1 has an application named App1. The executable for App1 is \Apps\App1.exe.You need to ensure that App1 is available as a RemoteApp in Session1.What command should you run?

NewRDRemoteApp -CollectionName "Session1" -DisplayName "App1" [third paramater] "C:\Apps\App1.exe"
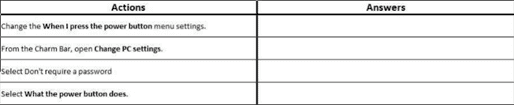
You plan to use a Group Policy to configure the power settings of several laptops. You need to ensure that the laptops meet the following requirements:
- Enter hibernation mode when the lid is closed.
Which two Power Management Group Policy settings should you modify? To answer, select the appropriate settings

You plan to use a Group Policy to configure the power settings of several laptops. You need to ensure that the laptops meet the following requirements:
- Enter sleep mode when the battery level is critical.
Which two Power Management Group Policy settings should you modify? To answer, select the appropriate settings

You have an image of Windows 10 Enterprise named Image1. Image1 has version number 1.0.0.0 of a custom, line-of-business universal app named App1.You deploy Image1 to Computer1 for a user named User1. You need to update App1 to version 1.0.0.1 on Computer1 for User1 only. What command should you run?

You have an image of Windows 10 Enterprise named Image1. Image1 has version number 1.0.0.0 of a custom, line-of-business universal app named App1.You deploy Image1 to Computer1 for a user named User1. You need to update App1 to version 1.0.0.1 on Computer1 for User1 only. What command should you run?

You manage a Microsoft Azure RemoteApp deployment. The deployment consists of a cloud collection named CloudCollection1 and a hybrid collection named HybridCollection1. Both collections reside in a subscription named Subscription1. Subscription1 contains two Active Directory instances named AzureAD1 and AzureAD2. AzureAD1 is the associated directory ofSubcsription1. AzureAD1 is synchronized to an on-premises Active Directory forest named constoso.com. Passwords are synchronized between AzureAD1 and the on-premises Active Directory. You have the following user accounts:

You need to identify to which collections each user can be assigned access.What should you identify? To answer, select the appropriate options in the answer area.
User1:
You manage a Microsoft Azure RemoteApp deployment. The deployment consists of a cloud collection named CloudCollection1 and a hybrid collection named HybridCollection1. Both collections reside in a subscription named Subscription1. Subscription1 contains two Active Directory instances named AzureAD1 and AzureAD2. AzureAD1 is the associated directory ofSubcsription1. AzureAD1 is synchronized to an on-premises Active Directory forest named constoso.com. Passwords are synchronized between AzureAD1 and the on-premises Active Directory. You have the following user accounts:

You need to identify to which collections each user can be assigned access.What should you identify? To answer, select the appropriate options in the answer area.
You manage a Microsoft Azure RemoteApp deployment. The deployment consists of a cloud collection named CloudCollection1 and a hybrid collection named HybridCollection1. Both collections reside in a subscription named Subscription1. Subscription1 contains two Active Directory instances named AzureAD1 and AzureAD2. AzureAD1 is the associated directory ofSubcsription1. AzureAD1 is synchronized to an on-premises Active Directory forest named constoso.com. Passwords are synchronized between AzureAD1 and the on-premises Active Directory. You have the following user accounts:

You need to identify to which collections each user can be assigned access.What should you identify? To answer, select the appropriate options in the answer area.
User3:


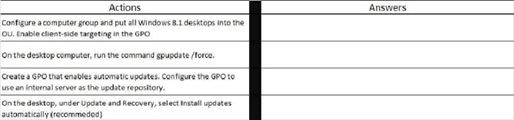
You plan to deploy a Microsoft Azure RemoteApp collection by using a custom template image. The image will contain Microsoft Word and Excel Office 365ProPlus programs. You need to install the Word and Excel programs. The solution must minimize the amount of Internet traffic used during installation. Which four actions should you perform in sequence?
You plan to deploy a Microsoft Azure RemoteApp collection by using a custom template image. The image will contain Microsoft Word and Excel Office 365ProPlus programs. You need to install the Word and Excel programs. The solution must minimize the amount of Internet traffic used during installation. Which four actions should you perform in sequence?

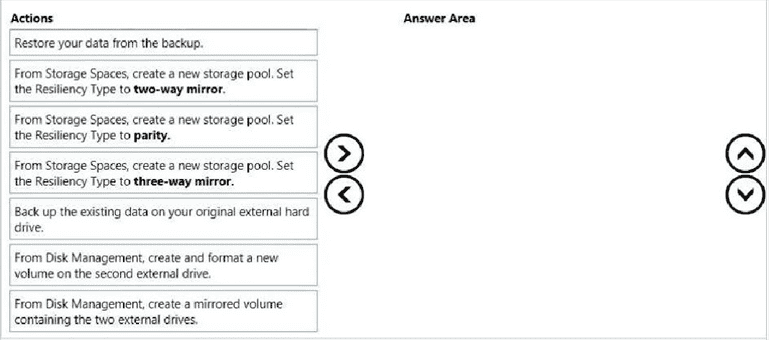
You plan to deploy a Microsoft Azure RemoteApp collection by using a custom template image. The image will contain Microsoft Word and Excel Office 365ProPlus programs. You need to install the Word and Excel programs. The solution must minimize the amount of Internet traffic used during installation. Which four actions should you perform in sequence?

You plan to deploy a Microsoft Azure RemoteApp collection by using a custom template image. The image will contain Microsoft Word and Excel Office 365ProPlus programs. You need to install the Word and Excel programs. The solution must minimize the amount of Internet traffic used during installation. Which four actions should you perform in sequence?

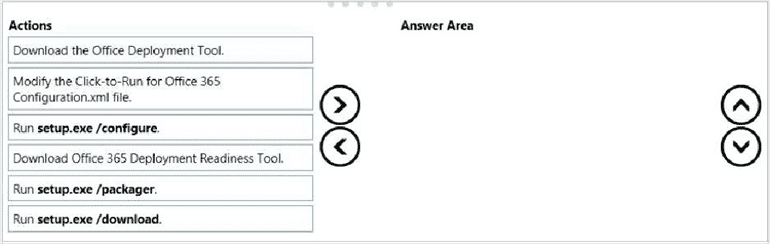
You manage Microsoft Intune for a company named Contoso. You have an administrative computer named Computer1 that runs Windows 10 Enterprise. You need to add a Windows Store universal app named App1 to the Company Portal Apps list for all users. Which three actions should you perform in sequence?

Step 1:
You manage Microsoft Intune for a company named Contoso. You have an administrative computer named Computer1 that runs Windows 10 Enterprise. You need to add a Windows Store universal app named App1 to the Company Portal Apps list for all users. Which three actions should you perform in sequence?

Step 2:
You manage Microsoft Intune for a company named Contoso. You have an administrative computer named Computer1 that runs Windows 10 Enterprise. You need to add a Windows Store universal app named App1 to the Company Portal Apps list for all users. Which three actions should you perform in sequence?

Step 3:












http://www.gratisexam.com/
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.
http://www.gratisexam.com/
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.

http://www.gratisexam.com/
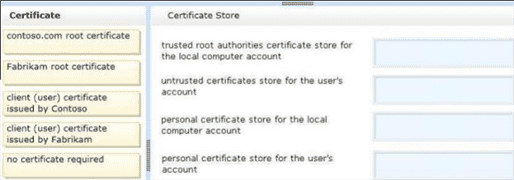
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.

http://www.gratisexam.com/
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.