Sys admin
What component connects all the other components of a computer together?
RAM
USB Printer
CPU
Motherboard
What type of logic gate can function as a 1-bit Adder?
NOR gate
AND gate
XOR gate
Inverter
Where are logical operations performed in a CPU
Memory
ALU
Input Device
Control Unit
What determines what CPU works with a motherboard?
The amount of RAM installed
The type of expansion card slots on the motherboard
The CPU socket and Motherboard Chipset
If the power socket can power the CPU
UEFI does what a BIOS does with more features.
True
False
What type of memory is the fastest from the following?
L3 Cache
L1 Cache
RAM
SSD
What is one of the form factors current hard disk drives (HDD) use?
5.25"
2.5"
mSATA
M.2
The Von Neumann Architecture describes what type of computer?
Stored Program Computer
Fixed Program Computer
a desk calculator
Quantum Computer
Where do SSDs store their data?
Memory Chips
Read head
Controller board
Platters
What is the CMOS?
The boot loader
The Real Time Clock
the runtime environment
configuration of the UEFI/BIOS
The Windows Context Menu :
shows the actions you can do with the selected item
actions are also shown in the start menu
Shows up when you double tap the left mouse button
shows the same actions for all items
You sometimes need to use command line interface because:
The information is not available in the GUI
It is faster to configure the same settings on lots of computers
Can run a lot of commands in a batch file
All of the above
Virtual box running on windows or mac OSX is which type of Hypervisor?
Type 1
Type 2
None of these.
Type 3
Why do businesses want to run physical servers at 100% utilization?
They need the fans running fast to get proper airflow.
To get the maximum return on investment
Need to put the air conditioner to good use
To break the servers to get warranty replacements
Windows 10 Pro edition:
Can join domains
cannot run games
is not used in businesses
cannot use bitlocker encryption
Microsoft Active Directory:
Stores settings for client computers
Stores User information
Centralizes management
all of the above
Which of of these statements are true?
Windows 10 is the last numbered version of windows.
Windows 10 feature updates are free
So far, they only update windows once every 2 years
all of the above
Bitlocker was enabled. Your computer broke and you pulled the harddrive to try to retrieve your data. You can still retrieve your data if you lost your passkey.
True
False
Windows Server 2019 has which of the following features?
Microsoft Edge browser
Cortana voice commands
Runs with no graphical interface
Windows Store
By default, you can enable Bitlocker without a TPM chip in Windows 10 Pro
True
False
In the Computer Management Console, Where would you find the logs for the applications in windows
Event Viewer
Services Console
Device Manager
Performance Console
To recover your data in case of a physical computer component failure, you should save your data to:
The My Documents folder
An External USB drive
Use Shadow Copy snapshots
All of above
A new User you created in the Local Users and Groups console is part of which Group by default?
Power Users
Users
Administrators
Guests
Mary was working on her autocad drawing. It was a very large and detailed drawing and takes about 25 seconds to save. When she was saving it, the power went out. When the power came back on, she was unable to open the file in Autocad but was able to open the other drawings. What was the problem?
Software problem
Virus or Malware
Data corruption
Physical hardware failure
This ensures that files are copied to another medium and can be used to restore a current or historical version of the files if necessary
Data replication
Data Corruption
Data backup
Disk redundancy
Testing your backups ensure that
The backup will continue writing files
Your computer is running
The backup will stop working
The backup will actually restore
Editing the Windows Registry values apply when the computer is rebooted.
True
False
The company has setup data replication to another office building. Someone got a virus and encrypted all the data at the primary office. What is the outcome of this scenario?
The Company is fine, they can retrieve their data from the replica at the other office
The Company needs double the amount of storage space to recovery the data from the replica
The Company has lost all their data unless they have another form of historical backup
The Company doubled their profits after the event
You can view total CPU usage in which application?
Users and Computer
Service Console
Task manager
Event Viewer
Which type of Windows Backup can restore the entire computer to a different harddrive?
System Restore
Windows File History
Windows Shadow Copy
Windows Backup and Restore
Why is Linux popular to run of servers and devices
Small footprint
Stable server software
Low cose
All of the above
Linux is not case sensitive
True
False
Which is a valid folder path in linux
\home\root
None of these
/etc/
.\
Where is Linux used today
Cars
Security Cameras
Computer Servers and Desktops
All of the Above
CentOS distribution is derived from what other Linux distribution
Mandriva
Ubuntu
Slackware
RHEL
What command do you have to use in front of a command to run as root?
Chown
Root
Chmod
Sudo
Which program is used to schedule tasks in Linux
Bash scripts
Task Scheduler
Cron
Gnome
What do you need to do to be able to start writing data to a new disk you added to your Linux system? You already created the partition, and formatted the disk
You need to enable encryption on the disk
You don't need to do anything else. It is already availble for use
You need to enable shadow copies
You need to mount the partition into a folder
Where are the configuration files usually located in Linux? (you edited files here in your activities)
Etc
Proc
Dev
Var
Select the best definition of Cloud Storage
Storage that uses you LAN
Types of storage that can be remotely accessed
When you tie your data to a balloon and let it go into the sky
A type of Storage that can be accessed anywhere with an internet connection
Which command is used to list processes in Linux?
Ps
Proc
Ls
List
Which command is used to identify processes with the highest CPU usage in Linux?
Nice
Top
Cpuinfo
Ps -top
In Linux, what does a high "niceness" value indicate for a process?
Low CPU usage
Low Priority
High CPU usage
High Priority
What is the purpose of the dnf autoremove command in Linux?
To remove all installed packages
To remove packages that are no longer required
To remove packages that are currently in use
To reinstall packages
A Bash script is a text file containing a sequence of commands in Linux.
Ture
False
Storage on the local network is called
SAS
NAS
DAS
FAS
How is system mail used in Linux?
To notify users about system events and status.
To send personal emails.
To send spam emails.
To communicate with system administrators.
A software repository is a centralized location for distributing and managing software packages in Linyx.
True
False
What is syslog in Linux?
A messaging system for communicating between users
A graphical user interface for log mangement
A system for storing binary logs.
A standardized logging protocol used for system and application logs.
Which file sharing protocol does Microsoft Windows currently use?
SMB2
SMB
CIFS
NFS
How can you forcefully terminate a process in Linux that refuse to close using conventional methods?
Terminate -9
Kill -9
Stop -KILL
Kill -TERM
Which command can be used to access system mail in Linux when no mail client is available?
Open-inbox
Cat /var/mail/username
Viewmail
System-mail
Which text manipulation tool is commonly used in Unix/Linux script to isolate lines of text?
AppleTalk protocol is used currently on macOS
True
False
You can use the Terminal is macOS to run UNIX commands.
True
False
What is the default backup utility in MacOs which includes the system files
Time Machine
ICloud
Time Capsule
SuperDuper!
In Windows, Share permissions can limit what you can do when you are logged directly into local computer
True
False
What does DNS stand for?
Dynamic Network
Domain Network Server
Data Name System
Domain Naming System
In DNS, what is the purpose of an "A record"?
It indicated the authoritative DNS server for a domain
It maps a domain name to an IPv4 address
It specifies the top level domain of a website
It retrieves the MX record for a domain
Which type of loop is not available in Bash Scripting?
Do-While Loop
While-do Loop
For Loop
Until-Do Loop
What is the name of the default internet browser in macOs?
Chrome
Edge
Firefox
Safari
Malicious software performing unwanted and harmful actions in disguise of a legitmate and useful program is known as
Adware
Backdoor
Spyware
Trojan
What is the purpose of command substitution in Bash scripting?
To create new commands
To execute multiple commands simultaneously
To evaluate and use the output of a command in another command.
To create comments within a script
Which type of loop executes when the condition is false?
Until...Do Loop
For Loop
Do..While Loop
While Loop
What is the purpose of an IP address in networking?
To differentiate between private and public networks
Resolve domain names
To uniquely identify devices on a network
To create subnets
A collection of zombies is known as
Extranet
Skynet
Botnet
Umbrella
Spammers want you to
Think first and act later
Act first, think later
Update your software
Not open any links
Best way to prevent malware outbreaks in an organization is
Firewalls
Email filters
Security doors
User Education
The part of malware code responsible for performing malicious action is referred to as
Logic bomb
Payload
Frame
Exploit
Software tools used to mask intrusion and obtain administrator level access to a computer is known as
Rootkit
Armored virus
Trojan
Adware
A method to identify phishing emails
Highlight links to check if they are correct
Bad grammer
Checking the email header
All of the above
Which of the following are examples of social engineering scams executed via phishing?
Banking link scams
Facebook message link scams
Password reset scams
All of above
Malicious software collecting information about users without their knowledge/ consent is known as
Backdoor
Trojan
Adware
Spyware
A computer program containing malicious segment that attaches itself to an application program or other executable called
Adware
Virus
Spam
Flash Cookie
The part of malware code responsible for performing malicious action is referred to as
Exploit
Payload
Logic bomb
Frame
To change the owner of a file in UNIX or Linux you would use which command
Chgrp
Passwd
Chomod
Chown
In Windows, what is a fast way to find out what permissions a user has for a particular file or folder, when the user is part of many groups?
Look at the ACL list and check the permissions for that user entry
Find out what groups the user is in and cross reference it with the permissions on the file or folder
Use the Effective Access tab
Ask the user to try out different tasks on the file or folder
Which ssd memory cell type holds 2 buts per cell?
Qlc
Slc
Plc
Tlc
Mlc
In an ssd, what determines how much data can be written at once?
the controller interface
The number of channels
the number of pages
The number of memory chips
Firmware version
Computer Security protects you from
Only intentional data loss
Intentional and unintentional damages
None of these
Only unintentional computer outages
What is shoulder surfing?
Avoiding triangulation by using your computer in a moving vehicle
Surfing on a surfboard on your back
Someone looking over your shoulder to find sensitive information
Walking closely behind someone when entering a secure building
In Windows, when a user is part of multiple groups, permissions on files and folder using those groups
Would only take the last group listed in the ACL
Would take the first group listed in the ACL
Would combine together
Would take only the most restrictive group permissions
Authentication is implemented by permissions.
True
False
Which Wi-Fi encryption is commonly used today?
WPA2.4
WPA
WEP
WPA2
Which feature on a motherboard uses “magic packets?
Fast boot
tpm
Wake on LAN
Secure boot
Power management
In UNIX and Linux file permissions, What is r-x represented in Octal?
5
6
4
7
In macOS, the @ symbol on file permissions represents
The file is corrupt
The file has extended attributes
The file is marked fo
What is a type of Ingress security?
Driving a car
Building access Security Cards
Working from starbucks
Cable locks
Powershell objects have
Functions only
Values only
Values and functions
Only string values
What is the function of PowerShell Modules?
Manage system files and directories
Organize and distribute PowerShell code
Define custom cmdlets
Execute complex mathematical operations
Which naming pattern do cmdlets in PowerShell follow?
Verb-Noun
Noun-Adjective
Noun-Verb
Adjective-Noun
Which conditional statement is true, when $A=22 and $B=34
$A -like $B
$A -It $B
$A -eq $B
$A -gt $B
Which type of memory is shared between cpu cores?
L2
Registers
L4
L1
L3
In PowerShell, what is the purpose of cmdlets?
Execute batch commands
Create graphical user interfaces
Manipulate text data
Perform various operations
What is a benefit of a type 2 hypervisor over a type1 hypervisor?
Supports wider range of hardware
Lower resource usage
Higher performance
More secure
Facilitates easy migration of vms
In powershell, to get all the values of all fields in an object:
It already displays all values by default
Use the Select-Object * cmdlet
Use the .count function
Use the get-member cmdlet
Your company requires bitlocker to be enabled on all computers that access the company [network. You](http://netwok.You) try to enable it but you get an error: “This device cant use a Trusted Platform Module.” What do you do to enable Bitlocker on your computer?
Change the hard drive to a different one
Reboot the computer into safe mode
Change a local group policy setting
Enable windows encrypting file system
Use a bitlocker startup key
Which statement is true:
Bash script uses text manipulation for extracting data when scripting
Powershell is not available on linux or macOs
Zsh in not compatible with bash scripts (don't choose this)
Powershell script use text manipulation for extracting data when scripting
When would you consider purchasing windows 2019 datacenter edition over the standard edition?
When you have more than 2tb of physical AM in the physical server
When you plan on having more than 12 windows vms per physical server
When you need to sign in with a microsoft account to sync your settings
When you plan to cluster more than 2 servers together
When your host has more than 8 cpus
What is the purpose of Script Execution Policies in PowerShell?
Define naming convention for scripts
Automate script execution
Enhance script readability
Control the execution of scripts for security
Backups protect against data loss due to
Hardware failure
File corruption
Accidental deletion
All of the above
What is Powershell?
An Object-oriented shell language
An open-source Linux Shell
A text manipulation based scripting language
A new version of Command Prompt
What is the primary purpose of PowerShell's foreach loop?
Perform conditional looping
Iterate through a sequence of numbers
Execute a block of code repeatedly
Traverse a collection of elements
Marcus was trying to customize his windows boot process through the registry and accidentally deleted some keys. Which statement is true?
The deleted keys are back when he reopens regedit
He restores the deleted keys using the restore registry option in regedit
The deleted keys are back when he reboots his computer
He can retrieve the deleted keys from the windows recycling bin
the deleted keys are gone when he opens regedit
A window service can
Only have one single instance started
Not recover automatically
Not start automatically
Not start automatically at boot
Only use local system account
Have multiple instances running concurrently
You need to connect the network between one building and a remote site which does not have any data infrastructure located a few kilometers apart. Which type of communication channel is most appropriate?
Wired channel
Wireless channel using microwaves
Wireless channel using radio waves
Bluetooth channel
Ethernet over powerline
In Centos linux, what group does your user need to be in to be able to escalate and run a program with root privileges?
Root
Sudo
Admin
Wheel
Plugdev
Gary is computer savvy and sets up a mirrored hard drive so he doesn't have to worry about physical failures. He sets up shadow copies to take snapshots twice a day, and sets the registry to have max 256 snapshots. He has been running this for a year, but when he needs to retrieve something from 30 days ago, it was not available in the shadow copies. He can only see the snapshots from the last 7 days why?
File history and shadow copies conflict
The hard disk is low on disk space
He did not test his shadow copies
The scheduler was not set up properly
The snapshot limit of 7 days was executed
What determines the size of your computer case?
The cpu type and socket
The motherboard size
The number of connectors
The amount of ram
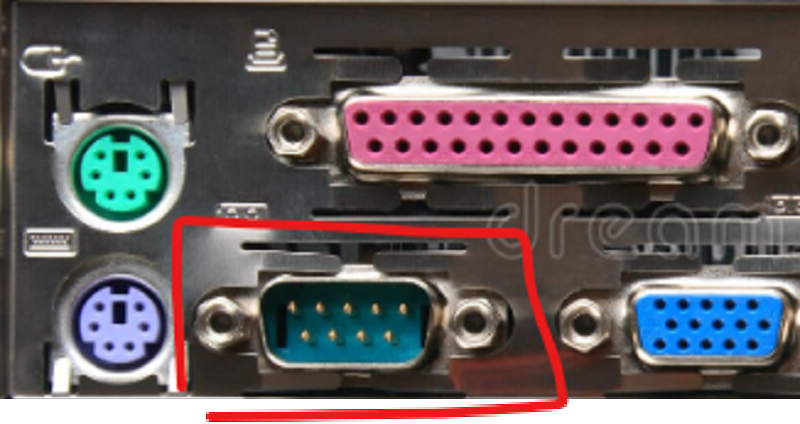
What kind of port is this?
USB port
Serial port
Parallel Port
VGA port
Which step is not part of the machine cycle?
Fetch
Flow
Execute
Store
What is the Full rotational latency of a 5400rpm drive?
4ms
8ms
6ms
11ms
Bitlocker
Encrypts your disk drive
Encrypts some Files
Requires TPM
Backs up your data
In bash and command prompt, what does ">>" do?
Creates a new file if one already exists
Erases the target file
Overwrites text in an existing file
Appends text to an existing file
Most reliable backups are
External Full backups
Data replication
Data Snapshots
Verified Restorable
In windows, to do a full restore if your SSD or HDD drives fails you need
A backup using backup and restore
A backup from file history
A backup from shadow copy
A backup from time machine
Where is the best place to put file backups?
Inside your SSD
In RAM
External storage
In your notepad
Windows Application logs are stored in...
Task manager
Disk management
Performance Monitor
Event Viewer
You set up shadow copies to take 7 times a day, changed the max snapshots to 476. How many days of retention do you have?q
79
68
119
54
How often does Time Machine backups and what is the retention?
Backups every 4 hours and kept for 24 hours
Backups every hour and kept for 24 hours
Backups every 12 hours and kept for 48 hours
Backups every day and kept for a week
What are Linux Daemons?
Program bugs
Service processes
Linux Logo
IoT device
To get help in Linux, we use...
-help
/?
/man
Man
Sudo is short for
Supreme user do
Super user do
Super duper user
Do this user
In Linux centos, adding a user to the ____ group grants Administrator rights.
Wheel
Sudo
Admin
Root
What does this line mean? "20**** rsync -a /home /mnt/sdb1/homeok it "
Schedule a cron job that runs every 20 seconds past every hour
Schedule a cron job that runs every 20 mins
Schedule a cron job that runs every 20 mins past every hour
Schedule a cron job that runs every 20 seconds
In Linux, what command do you use to grant permission to a new folder?
Chgrp
Chmod
Su root
Chown
In Linux, what command do you use to give the user admin privileges?
Usermod -aG wheel
Usermod -a wheel
Usermod -m wheel
Usermod -aG root
What is the last host IP address of a computer that has an IP address of 172.16.23.155/27.?
172.16.23.159
172.16.23.158
172.16.23.155
172.16.23.255
Which NSlookup command would you use to find the IPv6 address of bcit.ca?
Nslookup -type=A bcit.ca
Nslookup -type=AAAA bcit.ca
Nslookup -type=NS bcit.ca
-type=NS bcit.ca
There are 5 network topology in total, what are they?
Point-to-point, star, train, circle, mixed
Point-to-point, star, bus, ring, mixed
2point, star, train, ring, mixed
Network, star, bus, ring, mixed
There are many types of wireless security protocols. What does WEP stand for?
Wired Equivalent Privacy
Wired Ethernet Protocol
Wired Electric Protocol
Wi-Fi Equivalent Protocol
Which wireless security protocol is considered the standard for secure Wi-Fi?
WEP
WPA2
WPA3
WPA
A linux process with niceness of 4 is
High priority than process with niceness of 1
Is the same priority of niceness -4
Is lower priority than a niceness of 0
Is the lowest priority
What does this code do? "chmod +x"
Adds read only permissions
Adds executable permissions
Adds read and write permissions
Adds write only permissions
Env command shows
Disk space
Cpu info
Environment variables
Memory info
MacOS 9 uses:
UNIX
Linus
Mac system software
Zsh
It is possible to log into a mac without a password
True
False
You use macOS finder for?
Search
Browsing web
File explorer
Configurating system
The default terminal shell in macOS is
Bash
Zsh
UNIX
Powershell
APFS is used in iphones
True
False
What does the command chmod 770 do to a file in a Unix or Linux system?
Sets the file permissions to allow read, write, and execute for the owner and the group, but no permissions for others.
Gives read and write permissions to everyone: the owner, the group, and others.
Makes the file hidden from all users except the root user.
Locks the file, preventing any user from reading, writing, or executing it.
A function returns a value
True
False
Powershell commands use the noun-verb naming pattern.
True
False
Security breaches are mostly caused by:
Exploits
Man in the middle
Certificates
Human error
Echo '$(cat hellow.txt)' outputs
$(cat hello.txt)
Contents of hello.txt
(blank)
Error would occur
Cable locks on your laptop is an example of
Egress security
Ingress security
Visual security
Waste of your money
Powershell does not have post test loops
True
False
If your subnet mask 255.255.255.252, what is the short form?
/24
/16
/26
/30
In password complexity, which would take longer to brute force? A password with...
Special characters
Simple words
More characters
Random characters
When you Authenticate a user
You give permissions
You verify identity
Assign tasks
Get banking information
What type of cryptography is typically used when sending the session key for an HTTPS connection?
Asymmetric key cryptography
Hash Function Cryptography
Symmetric key cryptography
Quantum cryptography
To block unwanted communications use:
Firewall
Email filtering
Website screening
All of the above
You see -rw-r--r--@ on a file, what does @ mean?
There are extended attributes
There is an error with the file
The file is a link
The file is a folder
What permissions does chmod 007 give?
Give owner rwx
Gives group rwx
Gives other rxw
Gives owner, group, and other rwx
What does https:// denote? (opposed to http://)
The site is high definition
The site traffic is encrypted
The site is the newest version
they are the same
Which is an example of a phishing attack?
Email from someone you know with malicious link
fake website that tricks user into entering personal information
A winning contest text message with malicious link
All of the above
A group of zombies is
Apocalypses
Botnet
Rootkit
DDos
You found your files encrypted, and unable to access data until you pay the criminal. This is called?
Botnet
Spam
Ransomware
Scareware
If public wifi requires a password, is it safe to use for sensitive activities?
Yes
No
Maybe
Definitely
Which security risk is minimized when using a VPN?
Key logging
Phishing attacks
Shoulder surfing
Use of insecure wifi networks
Hackers use _____ to gain information from you without specialized computer programs.
ARP poisoning
Worm infection
Social enginerering
DDos
Updating your computer as soon as a patch is released minimize the risk of:
Ransom attack
Botnet infection
Zero-day exploits
Social engineering
Your computer was infected with ransomware, the hacker is demanding $25,000. What do you do?
Send email to IT guy in the office
Try to get rid of it before someone finds out
Pay the ransom, you need your files
Disconnect your computer from the network
Tell your boss to pay for it
{"name":"Sys admin", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"What component connects all the other components of a computer together?, What type of logic gate can function as a 1-bit Adder?, Where are logical operations performed in a CPU","img":"https://www.quiz-maker.com/3012/CDN/96-4712563/screenshot-2023-12-09-141241.png?sz=1200-00000000000507805300"}
More Quizzes
Road ecology
520
Ontdek hoe jij geluk aantrekt
520
Missmen
1588
How well do u know me and my family
14717
Conditional Probability: Can You Ace It?
201026253
Can You Ace This Ultimate Image? Test Your Skills!
201030396
Ultimate 13 Reasons Why Book - Test Your Knowledge
201023839
Which Animal Are You? Horse, Dog or Cat
201028438
Radiative Transfer & Remote Sensing
15820223
What Is a Phrase vs Clause? Take the Free Now
201023839
Free Love Oracle Online: Reveal Your Heart's Future
201031123
Cell Theory Questions: Challenge Your Biology Brain
201038888