AVT
Advanced Virus Technology Quiz
Test your knowledge on advanced virus technology and computer security with our comprehensive quiz. This quiz contains 32 challenging questions that dive deep into the world of viruses, assembly language, and system architecture.
- Multiple choice questions
- Assess your understanding of virus types
- Explore addressing modes and assembly instructions
Sub SP, 0002
Pop CX
None of these answers
Pop BX
Pop AX
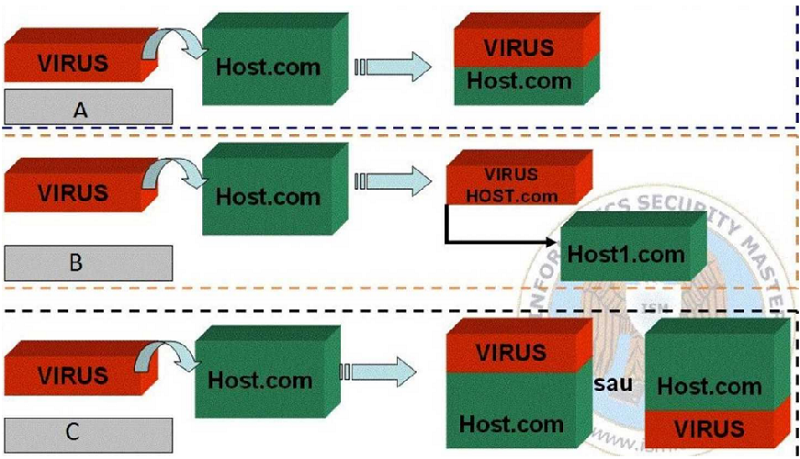
Indicate the correct type of the viruses described in next image:
A - parasitic, B - overwriting, C – companion
A - overwriting, B - parasitic, C - companion
A - companion, B - parasitic, C - overwriting
A - overwriting, B - companion, C - parasitic
A - parasitic, B - companion, C - overwriting
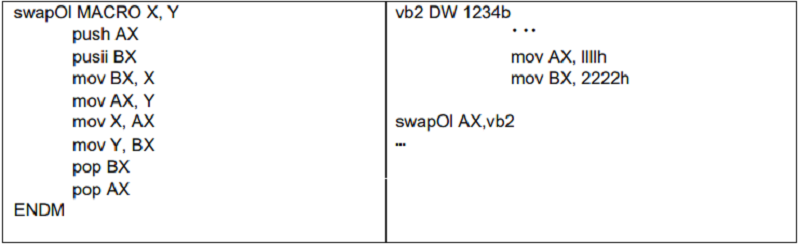
It is given the macrodefinition (left) and its call (right) in the next image:
What is the result obtained in AX and BX after its execution:
AX = 1234h and BX = 2222h
AX = 2222 and BX = 1111h
The result can NOT be determined because the source code has errors
AX = 1111h and BX = 2222h
AX = 2222h and BX = 1234h
What is a stack-frame ?
None of these answers
a run-time exception generated by a small stack
A memory zone created in the data segment
A memory zone created in the stack segment for local variables
A special area in the .com process header, like the DTA
The stack image at a precise moment during the process execution
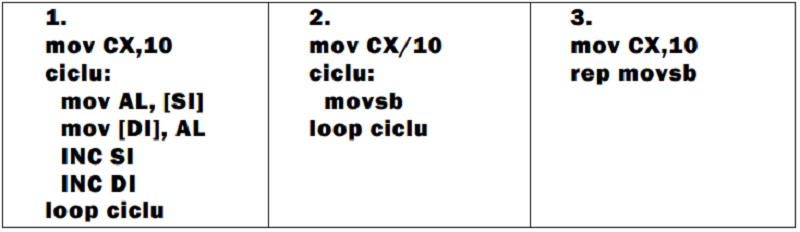
2 DB type arrays with size equal to 10 (they have their addresses stored in DS:SI and ES:DI) are copied from source into destination.
Which instruction block is going to do the copy:
Only 2
Only 2 and 3
Only 1 and 2
Only 3
Only 1
All
File viruses can infect:
a. BOOT
b. Driver and/or executable
c. C++ source file
d. Java source file
A + b + c + d
B + c
A + d
a + b
B + c + d
Knowing that the execution of a software interrupt, the microprocessor:
a. sets 0 in the TF (trap flag) and IF (interrupt enable flag) flag bits;
b. Seek the interrupt address in the interrupt vector table;
c. 9 does a FAR jump to the interrupt handler;
d. saves CS and IP of the calling program on the stack (the return address);
e. restore IP, CS and set flag bits;
f. Run the routine code until it encounters IRET.
A+b+c+f+e
A+b+c+d+e+f
A+b+d+e+c
None of these answers
B+a+d+c+f+e
B+a+d+e+c
Which one from the next statements it is NOT an indexed addressing mode:
MOV AX, SI
MOV AX, [SI][DI]
MOV AX, [SI]
MOV AX, [SI+2]
MOV AX, [Sl][2]
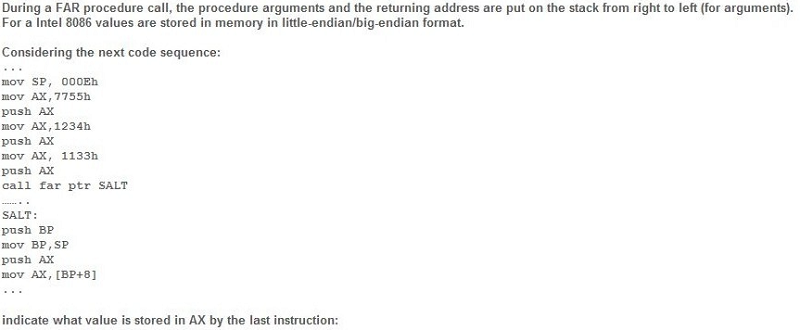
None of these answers
The value of the returning IP
The value can’t be determined because it is outside the stack (using BP indexed addressing mode you access data only from DS - data segment)
1133h
7755h
1234h
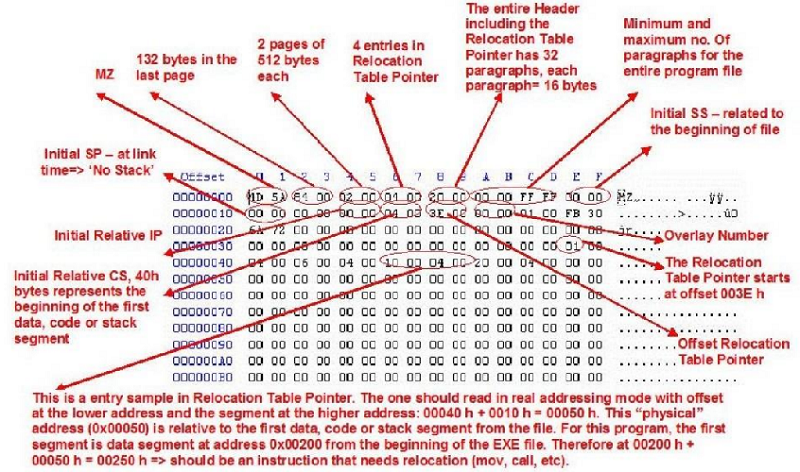
Knowing the structure of headers for 16-bit DOS executable (the next image).
Specify for how many instructions in the source code, the OS need to readjust their internai code (because an EXE file "doesn’t knows" what values will have the segment registers DS, ES, CS, SS):
4 instructions
2 instructions
1 instruction
None of these answers
16 instructions
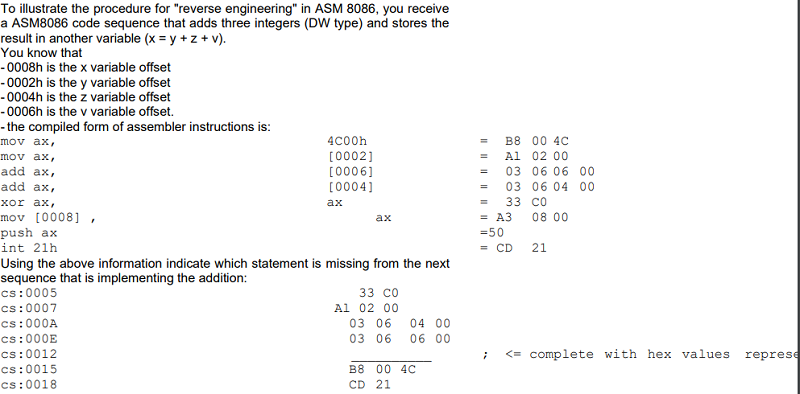
Mov [0008], ax = A3 08 00
Add ax, [0004] = 03 06 04 00
Add ax, [0006] = 03 06 06 00
Mov ax, [0002] = A1 02 00
None of these instructions
Companion viruses can have the type:
C source code file
Assembler source code file
None of these types
C++ source code file
Executable
Boot
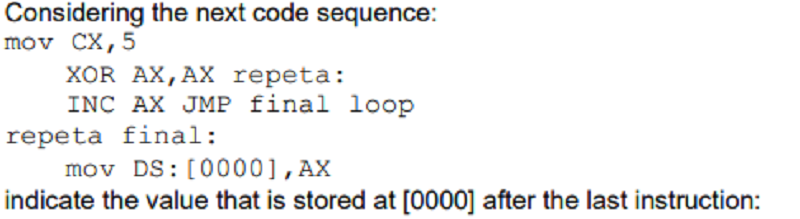
5
4
You can't determine it because the loop is infinite
0
1
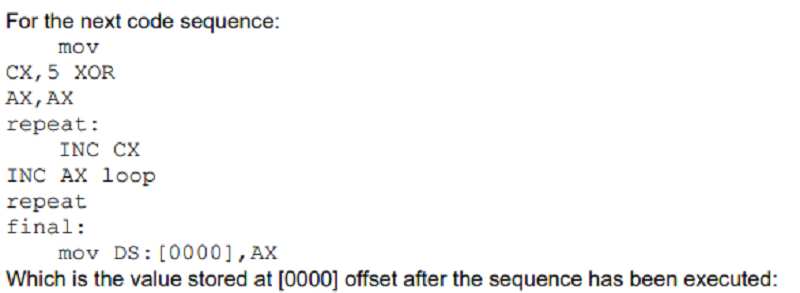
1
5
0
It is not possible to determine it because the sequence contains an infinite loop
4
It is NOT a feature of a memory resident viruses:
The virus hides in the memory & hooks a function of the interrupt 21 h
None of these answers
Inserts itself in the end of the .COM file O
The virus can be a parasitic one
DOESN’T destroy the host program
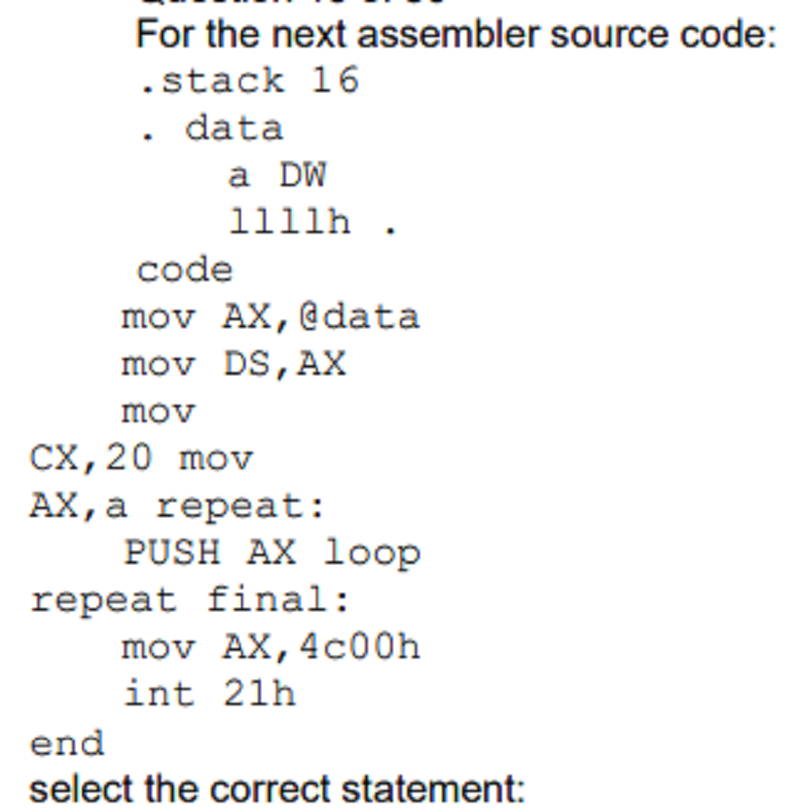
The source code is correct but the process will generate a Stack Overflow exception
The source code has errors because the final labei it is not used
The source code has errors because the CX register it is not initialized correctly
The source code is correct and the process will run without problems
The source code has errors because the hex value, 1111 h, it's too large for a Word variable
For these 2 logic addresses:
Address1 - 5732:001A
address2 - 572D:006A
indicate their physical order in memory, if you consider a Intel 8086 processor that uses a real addressing mode
Address1 < address2 (2D din hexadecimal in decimal = 45, vine 257245 : 00110 iar 5732:00110)
The real addressing mode is not for Intel 8086 processors and you can't determine their physical addresses
None of these answers
Address l > address2
Addressl and address2 represent identical physical addresses
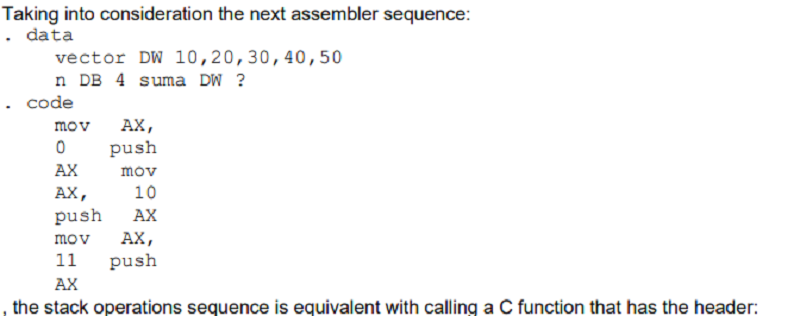
Void suma(int* suma, int n, int *vector)
Void suma(int* suma, int *n, int *vector)
Void suma(int* vector, int n, int *suma)
Void suma(int* vector, int *n, int *suma)
Void suma(int* suma, int *vector, int n)

0008h
000Ah
000Eh
0010h
1111 h
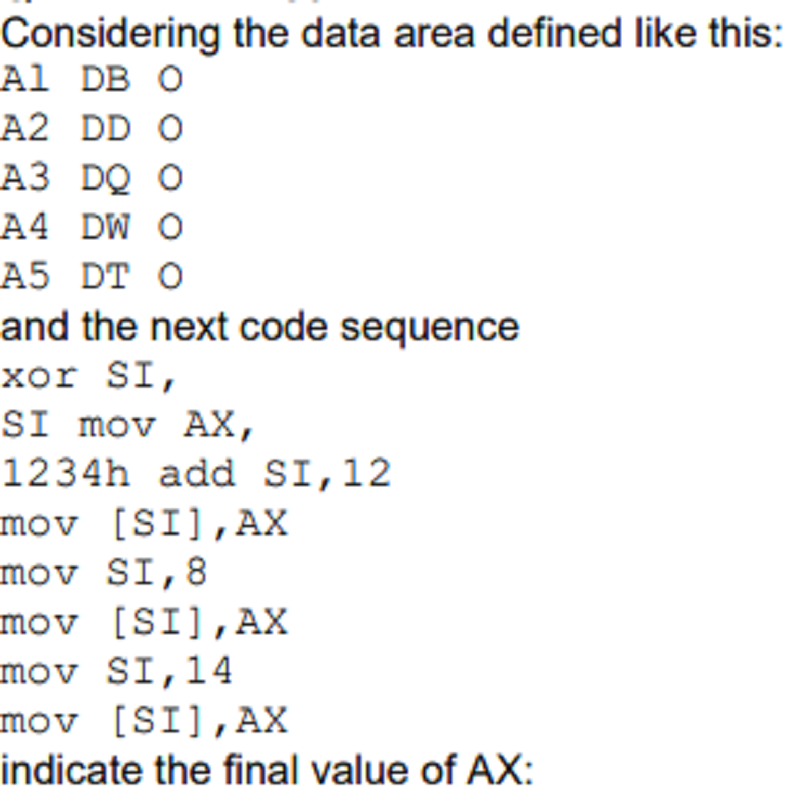
1111h
3412h
The value can not be determined because there are errors
0000h
1234h
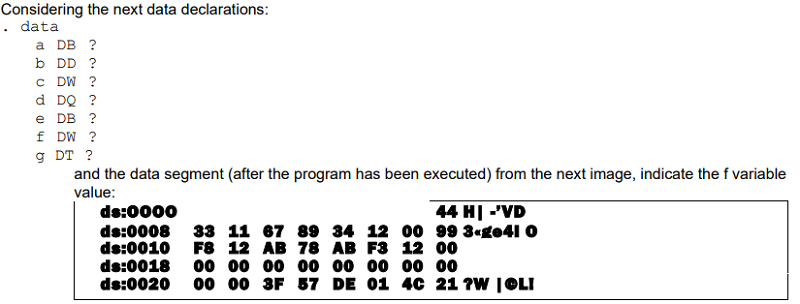
12F8h
AB12h
F899h
9900j

1
0
65535 as adecimal value
The AX value can’t be determined because the sequence has an infinite loop
FFFFh
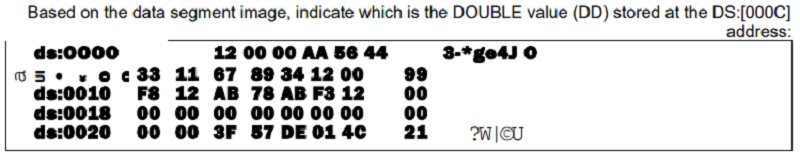
99001234h
34120099h
1234h
None of these values
3412h
Which of the following statements it is NOT true regarding the characteristics of a macro-virus:
Infect other documents on the host computer
None of these answers
May contain binary executable code as data
Is written in MS Office applications suite language - VBA = Visual Basic for Applications
Can launch executable viruses
is usually transmitted by e mail

A+c+d
B + c
None of the arguments is correct
A + b +c +d
A + c
The virus structure contains as mandatory routines:
a) search
b) processing
c) infection
d) anti-detection
e) stealth
A+b+c
A+c+e
A+b+c+e
B+c
A+c
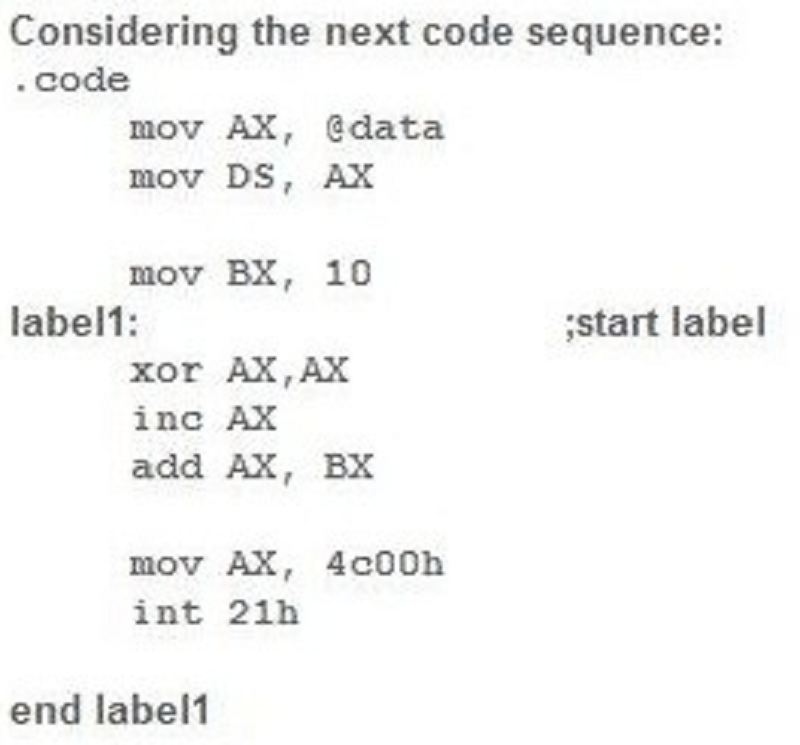
Indicate the value of the AX register before executing move AX, 4c00h
000Bh
0011h
You can’t determine the value because the result depends on the iniţial value of BX
0001 h
0001 h
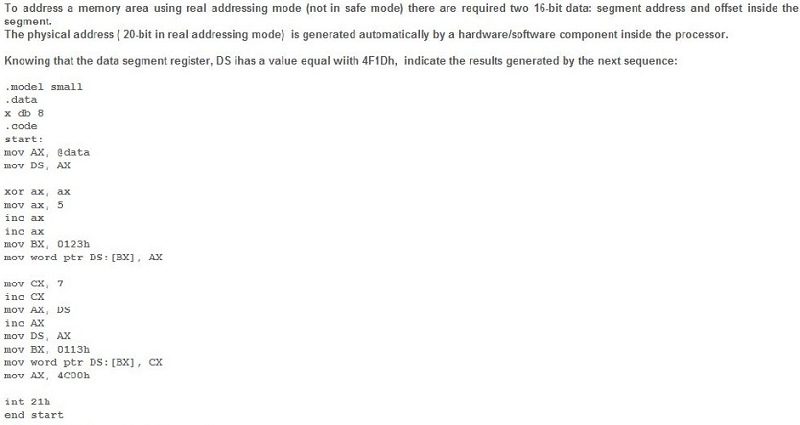
None of these answers is correct
At the 4F1Dh:0123h address (seg:off) it is stored 8, and at 4F1Eh:0113h it is stored 7
At the 4F1Dh:0123h address (seg:off) it is stored 5, and at 4F1Eh:0113h it is stored 8
At the 4F1Dh:0123h address (seg:off) it is stored 7, and at 4F1Eh:0113h it is stored 8
At the 4F1Dh:0123h address (seg:off) it is stored 8, and at 4F1Eh:0113h it is stored 8
At the 4F1Dh:0123h address (seg:off) it is stored 5, and at 4F1Eh:0113h it is stored 7
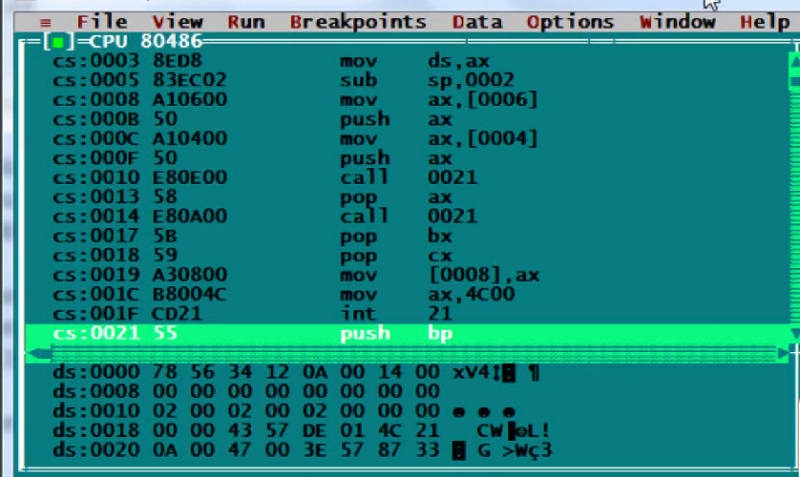
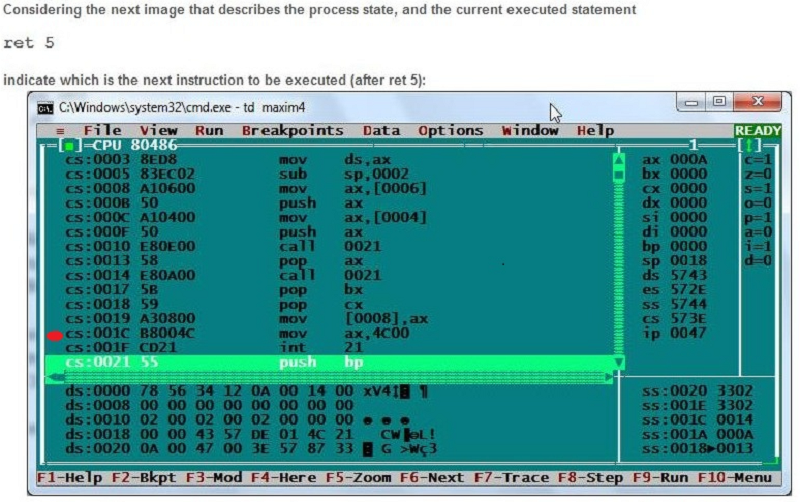
Considering the process state from the next debugger image, indicate what value will have the AX register after the "move AX, [0006]" instruction
0014h
0A00h
1400h
00h
000Ah
14h
6
Impossible to determine
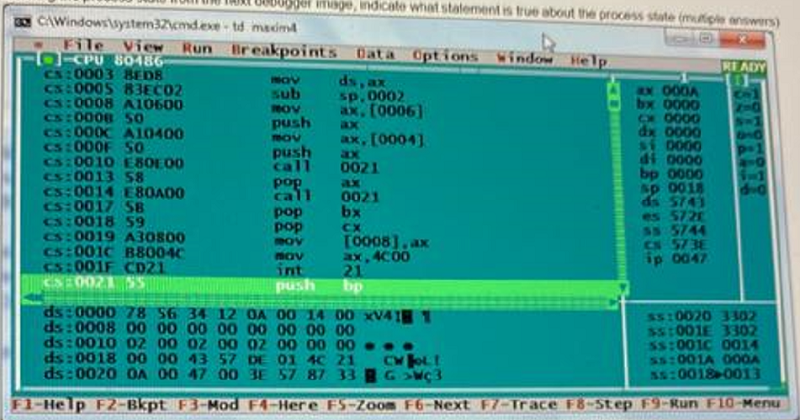
Considering the process state from the next debugger image, indicate what statement is true about the process state (multiple answers)
The next instruction to be executed is at offset 47h from the beginning of the code segment
The next instruction to be executed is at 47 bytes from the beginning of the code segment
The sign flag is set
The Carry flag is set
The data segment, code segment and stack segment are all equal
The zero flag is set
The parity flag is set
The overflow flag is set
When you create a COM file, what is the meaning of the "org 100" statement
Defines the stack size
Defines the data segment size
Instructs the operating system to place the process machine code after the first 256 bytes
Defines the process size
Defines the code segment size
Which statement is correct regarding the next code sequence:
mov AX, @data
mov DS, AX
Initialize the data segment register with the data segment address of the process
Initialize the code segment register with an address determined at run-time
Initialize the data segment register with a constant value, randomly generated by the processor
The sequence has assembler errors because the 2 operands of the mov AX, @data instruction have different size
The sequence has assembler errors because @data is not a valid statement
Initialize the code segment register with a constant value, randomly generated by the processor
{"name":"AVT", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Test your knowledge on advanced virus technology and computer security with our comprehensive quiz. This quiz contains 32 challenging questions that dive deep into the world of viruses, assembly language, and system architecture.Multiple choice questionsAssess your understanding of virus typesExplore addressing modes and assembly instructions","img":"https:/images/course6.png"}
More Quizzes
StegTech - Student Quiz
10516
Seguridad 2
10528
Lets get to know Royal Selangor!
10519
PAES 401-403
502536
Upper Extremity Bones - Test Your Arm Anatomy
201021016
MLP Name Generator - Find Your My Little Pony Name
201018220
Green Flag Test - Discover Your Relationship Strengths
201016647
Synonyms and Antonyms - Free Word Power Challenge
201017319
Are You Smarter Than a High Schooler? Free Online
201017066
Bible Prophecy - Questions & Answers (Free)
201017516
Am I Annoying - Are You Irritating to Others?
201018448
Which Aggretsuko Character Are You? Free
201016647