RSA Supply Chain Sandbox Trivia


How many suppliers does the average global brand have?
Tens
Thousands
Tens of Thousands
Hundreds of Thousands
In September 2020, which three members of the Quadrilateral Security Dialogue (aka the Quad) met to launch a supply chain security initiative?
India, South Korea, and Australia
Japan, Australia, and India
South Korea, Japan, and the U.S.
New Zealand, Australia, and the U.S.
Which of the following supply chain attacks did not employ hijacking updates as a mode of compromise?
CCleaner
NotPetya
Stuxnet
Wannacry
In supply chain security, SBOM refers to:
Software Bill of Materials
Supplier Bill of Materials
Software Based Operations Mitigation
Security Board of Managers
In December 2020, malware was inserted into an official government software toolkit that is used for issuing certificates and digitally signing documents in which country?
Kazakhstan
United Arab Emirates
Vietnam
Venezuela

The above alert was issued in reference to which malware that targets software providers?
Kwampirs
BlackEnergy
ShadowPad
EvilTwin
In 2015, NIST released which special publication that issues guidelines for managing risks within the information and communications technology supply chains?
800-161
800-171
800-53
8055
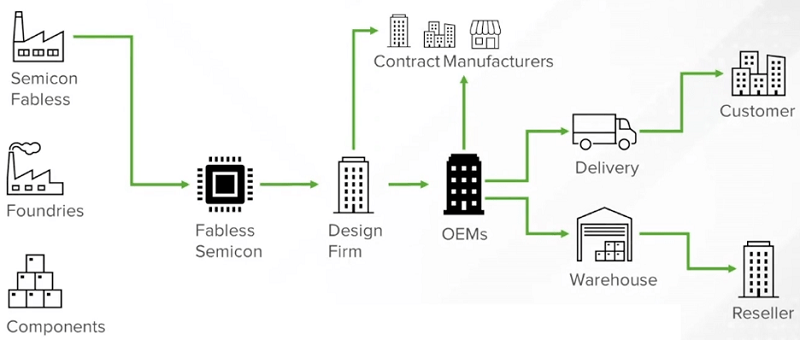
The image above depicts the electronics supply chain and highlights the importance of traceability for individual parts, such as chips. Uniquely identifying the properties and fun
Zero hardware trust (ZHT)
Hardware root of trust (HRoT)
Branch security (BS)
Trusted ecosystems and manufacturing (TEAMs)
Not ripped from the headlines! Which of the following third-party compromises was not a real headline?
How a fish tank helped hack a casino
Hackers broke in via HVAC system
~18,000 organizations downloaded backdoor planted by Cozy Bear hackers
Charming Kitten renews IoT focus, targeting smart feeders, smart collars, and activity trackers
ISO 9001 is an international standard that gives requirements for an organization’s quality management system. When discussing product standards, it refers to:
Tangible, physical products
Intangible products such as services or software
Both tangible and intangible products
Neither tangible nor intangible products - it focuses solely on certification
Which of the following is subject to malicious compromise?
Hardware
Software
Firmware
System data/information
All of the above
While Elderwood is more well-known for reportedly being responsible for Operation Aurora, the APT group also targets the supply chain in which industry?
Defense
Finance
Healthcare
Education
Spot the fake! Which of the following is not a U.S. Executive order pertaining to supply chains?
Executive Order on a Sustainable Public Health Supply Chain
Executive Order on Interagency Collaboration for Sustained Supply Chain Resilience
Executive Order on Ensuring Essential Medicines, Medical Countermeasures, and Critical Inputs are Made in the United States
Executive Order on Securing the Information and Communications Technology and Services Supply Chain
In September 2020, the European Parliament issued a draft report addressing the implementation of corporate due diligence and accountability legislation regarding which of the following areas?
Made in the EU certification
Mandatory human rights, environmental, and good governance
Net-zero emissions
5G trusted networks
Section 889 of the 2019 U.S. National Defense Authorization Act (NDAA) prohibits certain products in federal partners’ supply chains from all but which of the following companies?
Xiaomi
Dahua
Hikvision
ZTE
Huawei
Hytera
The Foundry problem refers to the notion that:
Open source libraries can be vectors for attacks
Critical mineral dependencies introduce vulnerabilities into supply chains
Hardware is difficult to validate since known-good versions cannot be guaranteed
A data transfer stovepipes in the backend
The 2013 Havex remote access trojan targets industrial control systems via:
Spearfishing
Compromising legitimate websites of vendors
Manipulating changes to software packages
All of the above
None of the above
The 2014 adware used in a man-in-the-middle attack to break into Windows encrypted web connections and came pre-installed in Lenovo was dubbed:
Superfish
Predator
Apex
Ghost machine
Although making headlines recently, counterfeit chips in the defense and tech supply chain have been an ongoing concern. A decade ago, counterfeit electronic parts were found on which critical military system?
THAAD missiles
F-35
SeaRAM
Flintlock submarines
Due to a range of national security concerns, how many Chinese-based companies did the U.S. Department of Commerce add to its entity list in 2019 and 2020?
Less than 10
Between 10 and 99
Between 100 and 200
Over 300
In 2015, the XcodeGhost iOS compiler malware modified versions of Apple’s Xcode development inserted via apps containing malicious code. Approximately how many users were affected?
Less than 1 million
100 million
Over 500 million
Over 1 billion
When did the U.S. Department of Defense adopt a trusted foundry model for procuring microelectronics?
Early 2000s
Mid-1990s
Late 200s
2010-2015
Software supply chain attacks can support which objective(s):
Data exfiltration
Extortion
Manipulation
Destruction
All of the above
The 2012 Telvent supply chain attack demonstrated that:
The aerospace and defense industry is susceptible to IP theft
Counterfeit hardware chips can go years without detection
Legitimate software updates can be compromised to steal healthcare information
Smart-grid systems can be compromised through injecting malicious code in project files
Operation Skeleton Key targets the semiconductor industry in:
Vietnam
Taiwan
Hong Kong
Singapore
Spot the fake! Which one of the following pieces of U.S. Supply chain legislation has not been introduced?
Supply Chain Adaption for Resilient Ecosystems Act
Securing the Homeland Security Supply Chain Act
Federal Acquisition Supply Chain Act
Secure and Trusted Communications Network Act
Which of the below countries has not imposed some version of formal restrictions on the Chinese telecom giant, Huawei?
Australia
Sweden
Italy
Canada
Which country has allocated over $4 billion to fund firms to shift production and reshore away from China?
New Zealand
Australia
Japan
South Korea
Which country or political entity has not recently signed a trade or investment pact with China?
New Zealand
European Union
Mauritius
Sweden
In 2017, NotPetya inflicted over $10 billion in global damages by compromising what software?
Ukrainian accounting software
CCleaner software updates
SWIFT banking software
Brazilian mobile money transfer software
Open RAN is often touted as a more secure and resilient 5G technology alternative that includes interoperable software run on vendor-neutral hardware. The acronym RAN stands for:
Recursive area neutrality
Radio access networks
Resilient accounts nationwide
Read-only and adaptable navigation
Applications increasingly play an essential role in conducting business, but also can be a source of compromise in supply chain attacks. Approximately how many applications does a large firm (i.e., over 2000 employees) have on average?
125-150
10-25
25-50
75-100
In February 2021, a researcher demonstrated a new supply-chain attack based on the dependency confusion problem. A dependency confusion attack refers to:
The insertion of counterfeit hardware at the earliest stages of development
The insertion of malicious code into private code repositories by replicating their naming convention
The insertion of malicious JavaScript code into a webpage form
The insertion of malicious updates into legitimate software
Operation NightScout initially targeted which industry and geography?
Financial services industry in Europe
Manufacturing in South America
Online gaming in Asia
Telecommunications in North America
In what year were South Korean banking and media hit with a DDoS attack linked to a compromise of two file-sharing services’ auto-updates?
2019
2005
2010
2013
{"name":"RSA Supply Chain Sandbox Trivia", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"How many suppliers does the average global brand have?, In September 2020, which three members of the Quadrilateral Security Dialogue (aka the Quad) met to launch a supply chain security initiative?, Which of the following supply chain attacks did not employ hijacking updates as a mode of compromise?","img":"https://cdn.poll-maker.com/64-2789828/alert.png?sz=1200-00000000001000005300"}
More Quizzes
Digestive system:quiz 9
1050
These questions will reveal your true intelligence
1058
100
Discover Dhivagar
11633
Nineteenth-Century American Fiction
15819932
Ace Your ACCT 202 Exam 1: Free Cash Flow & Practice
201027231
Which WW2 Fighter Plane Are You? Free WW2 Plane
201032220
Free 9th Grade Math Test & Final Exam Review
201025712
Computer Applications
15819932
Free Design System Knowledge Test
201021715
Free Earth Science & Test Review
201028077
Free Trade Skills Knowledge Assessment
201031429