IAS FINALS

Master the IAS Finals: Cybersecurity Quiz
Test your knowledge and expertise in cybersecurity with our comprehensive quiz designed for the IAS Finals. Dive into 126 meticulously crafted questions that cover a wide range of topics, ensuring you are well-prepared for your certification exams.
Whether you're a student or a professional looking to refresh your skills, this quiz will challenge you with:
- Real-world scenarios
- The latest security protocols
- Key concepts in network security
What is the purpose of a personal firewall on a computer?
� to increase the speed of the Internet connection
� to protect the computer from viruses and malware
� to filter the traffic that is moving in and out of the PC
� to protect the hardware against fire hazard
What is the main difference between the implementation of IDS and IPS devices?
� An IDS can negatively impact the packet flow, whereas an IPS can not.
� An IDS needs to be deployed together with a firewall device, whereas an IPS can replace a firewall.
� An IDS uses signature-based technology to detect malicious packets, whereas an IPS uses profile-based technology.
� An IDS would allow malicious traffic to pass before it is addressed, whereas an IPS stops it immediately.
Which two pieces of information should be included in a logical topology diagram of a network? (Choose two.)
� device type
� cable specification
� interface identifier
� cable type and identifier
� OS/IOS version
• connection type
What is a characteristic of a WAN?
� It is typically owned and managed by a single home or business.
� It requires a wireless access point to connect users to the network.
� It spans across a campus or city to enable sharing of regional resources.
� It connects multiple networks that are geographically separated.
What network monitoring technology enables a switch to copy and forward traffic sent and received on multiple interfaces out another interface toward a network analysis device?
� NetFlow
� network tap
� port mirroring
� SNMP
What is a function of a proxy firewall?
� drops or forwards traffic based on packet header information
� connects to remote servers on behalf of clients
� filters IP traffic between bridged interfaces
� uses signatures to detect patterns in network traffic
Which technology is used by Cisco Advanced Malware Protection (AMP) in defending and protecting against known and emerging threats?
� threat intelligence
� network admission control
� website filtering and block listing
� network profiling
How is a source IP address used in a standard ACL?
� It is the address that is unknown, so the ACL must be placed on the interface closest to the source address.
� It is the address to be used by a router to determine the best path to forward packets.
� It is used to determine the default gateway of the router that has the ACL applied.
� It is the criterion that is used to filter traffic.
Which statement describes the Cisco Cloud Web Security?
� It is a security appliance that provides an all-in-one solution for securing and controlling web traffic.
� It is an advanced firewall solution to guard web servers against security threats.
� It is a cloud-based security service to scan traffic for malware and policy enforcement.
� It is a secure web server specifically designed for cloud computing.
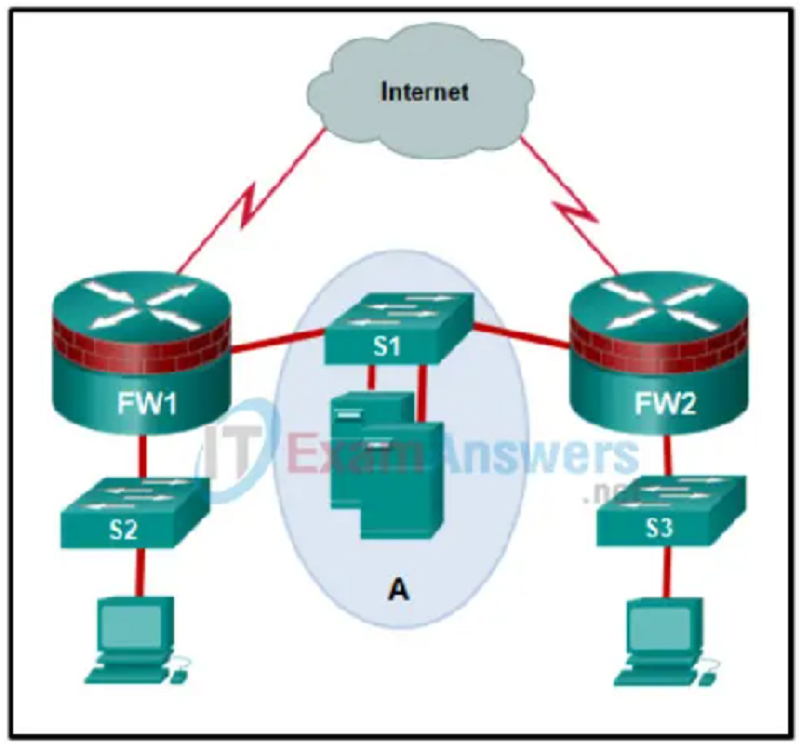
Refer to the exhibit. The network “A” contains multiple corporate servers that are accessed by hosts from the Internet for information about the corporation. What term is used to describe the network marked as “A”?
� untrusted network
� perimeter security boundary
� internal network
� DMZ
Which network service allows administrators to monitor and manage network devices?
� SNMP
� syslog
� NTP
� NetFlow
Which protocol provides authentication, integrity, and confidentiality services and is a type of VPN?
� MD5
� ESP
� AES
� IPsec
What is a feature of the TACACS+ protocol?
� It hides passwords during transmission using PAP and sends the rest of the packet in plaintext.
� It utilizes UDP to provide more efficient packet transfer.
� It combines authentication and authorization as one process.
� It encrypts the entire body of the packet for more secure communications.
Which layer of the hierarchical design model is a control boundary between the other layers?
� distribution
� core
� access
� network
Which asymmetric algorithm provides an electronic key exchange method to share the secret key?
� Diffie-Hellman
� RSA
� WEP
� DES
� hashing
What encryption algorithm uses one key to encrypt data and a different key to decrypt data?
� transposition
� symmetric
� asymmetric
� one-time pad
What type of cipher encrypts plaintext one byte or one bit at a time?
� block
� stream
� hash
� enigma
� elliptical
What cryptographic algorithm is used by the NSA and includes the use of elliptical curves for digital signature generation and key exchange?
� ECC
� RSA
� AES
� El-Gamal
� IDEA
What is the term used to describe the science of making and breaking secret codes?
� factorization
� cryptology
� impersonation
� spoofing
� jamming
Which three processes are examples of logical access controls? (Choose three.)
� intrusion detection system (IDS) to watch for suspicious network activity
� firewalls to monitor traffic
� guards to monitor security screens
� fences to protect the perimeter of a building
� swipe cards to allow access to a restricted area
� biometrics to validate physical characteristics
What term is used to describe concealing data in another file such as a graphic, audio, or other text file?
� masking
� hiding
� obfuscation
� steganography
What are three examples of administrative access controls? (Choose three.)
� policies and procedures
� encryption
� background checks
� hiring practices
� intrusion detection system (IDS)
� guard dogs
Which three protocols use asymmetric key algorithms? (Choose three.)
� Secure File Transfer Protocol (SFTP)
� Telnet
� Pretty Good Privacy (PGP)
� Secure Shell (SSH)
� Advanced Encryption Standard (AES)
� Secure Sockets Layer (SSL)
A warning banner that lists the negative outcomes of breaking company policy is displayed each time a computer user logs in to the machine. What type of access control is implemented?
� masking
� deterrent
� detective
� preventive
Which term describes the technology that protects software from unauthorized access or modification?
� copyright
� watermarking
� access control
� trademark
What encryption algorithm uses the same pre-shared key to encrypt and decrypt data?
� hash
� asymmetric
� one-time pad
� symmetric
Which two terms are used to describe cipher keys? (Choose two.)
� key space
� key randomness
� keylogging
� key length
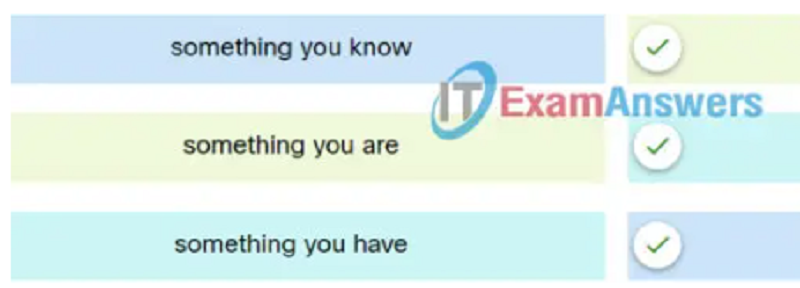
Something you know
A fingerprint scan
A security key fob
A password

Something you are
A fingerprint scan
A security key fob
A password

Something you have
A fingerprint scan
A security key fob
A password
What is the name of the method in which letters are rearranged to create the ciphertext?
� substitution
� transposition
� one-time pad
� enigma
Which 128-bit block cipher encryption algorithm does the US government use to protect classified information?
� Vignere
� AES
� Caesar
� 3DES
� Skipjack
M1: steganography
Hiding data within an AUDIO FILE
Discovering that hidden information exists within a GRAPHIC FILE
Creating a message that says one thing but means something else to a SPECIFIC AUDIENCE
Making a message CONFUSING so it is harder to understand
Replacing sensitive information in a file with nonsensitive information
M1: steganalysis
Hiding data within an AUDIO FILE
Discovering that hidden information exists within a GRAPHIC FILE
Creating a message that says one thing but means something else to a SPECIFIC AUDIENCE
Making a message CONFUSING so it is harder to understand
Replacing sensitive information in a file with nonsensitive information
M1: social steganography
Hiding data within an AUDIO FILE
Discovering that hidden information exists within a GRAPHIC FILE
Creating a message that says one thing but means something else to a SPECIFIC AUDIENCE
Making a message CONFUSING so it is harder to understand
Replacing sensitive information in a file with nonsensitive information
M1: obfuscation
Hiding data within an AUDIO FILE
Discovering that hidden information exists within a GRAPHIC FILE
Creating a message that says one thing but means something else to a SPECIFIC AUDIENCE
Making a message CONFUSING so it is harder to understand
Replacing sensitive information in a file with nonsensitive information
What term is used to describe the technology that replaces sensitive information with a nonsensitive version?
� blanking
� whiteout
� masking
� hiding
� retracting
Which type of cipher is able to encrypt a fixed-length block of plaintext into a 128-bit block of ciphertext at any one time?
� transform
� stream
� hash
� symmetric
� block
Which three devices represent examples of physical access controls? (Choose three.)
� locks
� routers
� swipe cards
� firewalls
� servers
� video cameras
What contains information on how hard drive partitions are organized?
BOOTMGR
Windows Registry
MBR
CPU
Name given to AMATEUR HACKER
Script kiddle
Blue team
Black hat
Red hat
User accounts AUTOMATICALLY CREATED when a user installs Windows to new computer
Root
System
Administrator
Superuser
Which Windows version was the FIRST TO INTRODUCE 64-bit windows OS
Windows 7
Windows XP
Windows 10
Windows NT
WHERE are the SETTINGS that are chosen during the installation process STORED
Recovery partition
Registry
BIOS
Flash memory
Which organization offers the vendor-neutral CySA+ certification
IEEE
(ISC)^2
CompTIA
GIAC
How can a security information and event manager system in an SDC be used to HELP PERSONNEL FIGHT against security threats
By encrypting communications to remote sites
By filtering network traffic
By collecting and filtering data
By authenticating users to network resources
Command used to MANUALLY QUERY a DNS server to resolve specific hostname
Nslookup
Net
Ipconfig
Tracert
What utility is available to VIEW CURRENT RUNNING APPLICATIONS and PROCESSES
Task manager
Nslookup
Control panel
Ipconfig
Function provided by the windows task manager
Provides information on system resources and processes
Provides an active list of TCP connections
Maintains system logs
Selectively denies traffic on specified interfaces
Two pings were issued from a host
The default gateway is not operational
Security rules are applied
The default gateway device is configured
The TCP/IP stack on the default gateway
What utility is used to show the system resources consumed by each user
Task manager
Event viewer
Device manager
User accounts
How can a user prevent specific applications from accessing a windows computer over a network
Block specific TCP or UDP ports in windows firewall
Disable automatic IP address assignment
Enable MAC
Change default usernames and passwords
What technology was created to REPLACE THE BIOS program on modern motherboards
UEFI
RAM
MBR
CMOS
Statement that best describes a motivation of hacktivists
They are part of a protest group behind a political cause
They are curious and learning hacking skills
They are interested in discovering new exploits
They are trying to show off their hacking skills
User creates a file with a .ps1 extension. What type of file is it?
Powershell documentation
Powershell script
Powershell function
Powershell cmdlet
A technician can ping the ip address of the web server
Tracert
Nslookup
Ipconfig
Netstat
How does SEM in a DOC help the personnel fight against security threats
By dynamically implementing firewall rules
By integrating all security devices
By analyzing logging data
By combining data from multiple technology
If a SOC has a goal of 99.999% uptime
30 mins per year
10 mins per year
5 mins per year
20 mins per year
How much RAM is addressable by a 32-bit
4 GB
32 GB
16 GB
8 GB
The term ALERT ANALYST, which group?
Tier 1
Tier 3
Tier 2
SOC managers
Term used to describe a logical drive that can be formatted to store data
Track
Cluster
Sector
Partition
In the operation of a SOC, which system is frequently used to let an analyst SELECT ALERTS
Registration system
Security alert knowledge-based system
Ticketing system
Syslog server
Reasons for entering the ipconfig command
To ensure that the PC can connect to remote networks
To check if the DNS server can be contacted
To display the bandwidth
To review the network configuration on the PC
Advantage the NTFS compared with FAT32
NTFS provide more security features
NTFS allow the automatic detection of bad sectors
NTFS allow faster formatting of drives
NTFS is easier to configure
A technician is troubleshooting... command... To check IP adsress
Tracert
Ping
Nslookup
Ipconfig
A user logs in to windows with a regular user account... Requires administrative privileges
Right click the app and choose runs as privilege
Right click the app and choose run as superuser
Right click the app and choose run as administrator
Right click the app and choose run as root
When a user makes changes to the settings... Where are these changes stored
Boot.ini
Registry
Win.ini
Control panel
Which organization is an INTERNATIONAL NON-PROFIT organization that offers CISSP certification
GIAC
(ISC)^2
IEEE
CompTIA
Purpose of the cd\ command
Changes directory to the root directory
Changes directory to the next lower directory
Changes directory to the next highest directory
Changes directory to the previous directory
What was used as a cyberwarfare weapon to attack... IRAN?
PSYOPS
SQL injection
DDoS
Stuxnet
Name given to hackers who hack a political or social cause
Hacktivist
Blue hat
White hat
Hacker
Net ad needs to ensure that local computers CANNOT PING EACH OTHER... What settings
Firewall settings
Smartcard settings
File system settings
MAC address settings
Personnel assigned of verifying whether an alert triggered by monitoring software... TRUE SECURITY incident
Tier 2
Tier 1
Tier 3
SOC manager
Which technology should be included in an SOC security information
Proxy service
Intrusion prevention
Threat intelligence
User authentication
Window powershell command... RETURNS AN OUTPUT or object TO THE NEXT COMMAND
Routines
Scripts
Functions
Cmdlets
Personnel assigned of HUNTING FOR POTENTIAL THREATS
Tier 1 analyst
SOC manager
Tier 3 SME
Tier 2 incident reporter
Why do IoT devices pose a greater risk
IoT devices cannot function on an isolated network
IoT devices require unencrypted wireless connections
Most IoT devices do not require an internet connection
Most IoT devices do not receive frequent firmware update
CYBERWARFARE
It is internet based conflict that involves the penetration of information systems of other nations
It is a series of personal protective equipment developed for soldiers
Cyberwarfare is an attack carried out by a group of script kiddles
It is simulation software for Air Force pilots
Net command used to establish a connection to a SHARED DIRECTORY on a remote server
Net start
Net session
Net use
Net share
Purpose of using the NET ACCOUNTS COMMAND in windows
To start a network service
To review the settings of password and logon requirements for users
To display information about shared network resources
To show a list of computers and network devices on the network
What thing can be determined by using the PING command
The average time it takes each router in the path between source and destination to respond
The destination device is reachable through the network
The IP address of the router nearest the destination device
The number of routers between the source and destination device
Consider the path... C:\Users\Jason\Desktop\mydocu.txt. What does Users\Jason component represent
File directory and subdirectory
File attribute
Current file directory
Storage device or partition
Command used to check if DNS name resolution is working properly on a Windows PC
Ping cisco.com
Nbstat cisco.com
Net cisco.com
Ipconfig
What type of startup must be selected for a service that should run each time the computer is booted
Automatic
Boot
Manual
Start
What service are provided by SECURITY OPERATIONS CERTIFIERS
Responding to data center physical break-ins
Providing secure internet connections
Ensuring secure routing packet exchanges
Monitoring network security threats
What is a potential risk when using a FREE AND OPEN WIRELESS-HOTSPOT IN PUBLIC LOCATION
Network traffic might be hijacked and information stolen
Purchase of products from vendors might be required for the internet access
The internet connection can become too slow
Too many users trying to connect to the internet may cause a network traffic jam
User reports that a database file on the main server cannot be accessed
Ransomware
Trojan-horse
DOS attack
Man-in-the-middle attack
After a security incident is verified in a SOC, an INCIDENT RESPONDER reviews the incident but cannot identify the source of the incident
The SOC manager to ask for other personnel to be assigned
An SME for further investigation
A cyberoperations analyst for help
An alert analyst for further analysis
What is a ROUGE wireless hotspot?
It is a hotspot that was set up with outdated devices
It is a hotspot that does not implement strong user authentication
It is a hotspot that does not encrypt network user traffic
It is a hotspot that appears to be from a legitimate business but was actually set up by someone without the permission from the business
It is an example of the individual user profile identify on a social network site.
online
Avatar
How can a user prevent others from eavesdropping on network traffic when operating a PC on a public Wi-Fi hot spot?
Data encryption
Connect with a VPN service
This is the primary goal of a DoS attack.
Prevent the target server from being able to handle additional requests
Gathering target information: gathering target information
As data is being stored on a local hard disk, which method would secure the data from unauthorized access?
Data encryption
a duplicate hard drive copy
What is the best method to prevent Bluetooth from being exploited?
always disable Bluetooth when it is not actively used.
Prevent the broadcast of an SSID
Which configuration on a wireless router is not considered to be adequate security for a wireless network?
Prevent the broadcast of an SSID
Prevent the broadcast of an MAC
A user is surfing the Internet using a laptop from a public WiFi cafe. What should be checked first when the user connects to the public network
If the laptop does not require user authentication for file and media sharing
If the laptop requires user authentication for file and media sharing
Which tool can identify malicious traffic by comparing packet contents to known attack signatures?
IDS
IDM
Which tool can identify malicious traffic by comparing packet contents to known attack signatures?
Drninjaphd
Mk$$cittykat104#
How can users working on a shared computer keep their personal browsing history hidden from other workers that may use this computer?
Use only an encrypted connection to access websites.
Operate the web browser in private browser mode
This tool is used to provide a list of open ports on network devices
Nmap
IDS
Which component belongs to the CIA triad?
Confidentiality
Reliability
This tool is used to provide a LIST OF OPEN PORTS on network devices.
IDS
Nmap
Which method is used to CHECK THE INTEGRITY of data?
Checksum
Antispyware
What is a reason that internal security threats might cause greater damage to an organization than external security threats?
External users have direct access to the infrastructure devices.
Internal users have direct access to the infrastructure devices.
Why do IoT devices pose a greater risk than other computing devices on a network?
Most IoT devices do not require an Internet connection and are unable to receive new updates.
Most IoT devices do not receive frequent firmware updates.
What is another name for confidentiality of information?
Privacy
Access control
Which type of technology can prevent malicious software from monitoring user activities, collecting personal information, and producing unwanted pop-up ads on a user computer?
Antivirus
Antispyware
It is the last stage of the Cyber Kill Chain framework.
gathering target information
Malicious action
A consumer would like to print photographs stored on a cloud storage account using a third party online printing service. After successfully logging into the cloud account, the customer is automatically given access to the third party online printing service. What allowed this automatic authentication to occur?
The cloud storage service is an approved application for the online printing service.
The infrastructure service is an approved application for the online printing service.
The cloud storage service is an approved application for the online printing service.
Worm
DDoS
What is the purpose of a rootkit?
to gain privileged access to a device while concealing itself
to masquerade as a legitimate program
It is a group of compromised or hacked computers controlled by an individual with malicious intent.
Spyware
Botnet
In what way are zombies used in security attacks?
They are infected machines that carry out a DDoS attack
They are infected machines that carry out a Trojan Horse attack
This technology removes direct equipment and maintenance costs from the user for data backups
DDoS
cloud service
A user is having difficulty remembering passwords for multiple online accounts. What is the best solution for the user to try?
Save the passwords in a centralized password manager program.
Write it in paper
What method that can be used to ensure confidentiality of information?
Data decryption
Data encryption
This type of attack allows an attacker to use a brute force approach.
password cracking
DDoS
Which protocol is used by the Cisco Cyberthreat Defense Solution to collect information about the traffic that is traversing the network?
DataFlow
NetFlow
What is an example of “hacktivism”?
A group of environmentalists launch a denial of service attack against an oil company that is responsible for a large oil spill.
A country tries to steal defense secrets from another country by infiltrating government networks.
A group of environmentalists launch a denial of service attack against an oil company that is responsible for a large oil spill. S
An email is sent to the employees of an organization with an attachment that looks like an antivirus update, but the attachment actually consists of spyware.
An SMS is sent to the employees of an organization with an attachment that looks like an antivirus update, but the attachment actually consists of spyware. C
What is the motivation of a white hat attacker?
discovering weaknesses of networks and systems to improve the security level of these systems
discovering strengths of networks and systems to improve the security level of these systems
What is the most common goal of search engine optimization (SEO) poisoning?
to decrease web traffic to malicious sites
to increase web traffic to malicious sites
Which tool can perform real-time traffic and port analysis, and can also detect port scans, fingerprinting and buffer overflow attacks?
IDS
Snort
Another component belongs to the CIA triad?
Intervention
Integrity
This characteristics describes a worm.hides
It travels to new computers without any intervention or knowledge of the user
To increase web traffic to malicious sites
To increase web traffic to malicious sites
Firewall
Control Panel
{"name":"IAS FINALS", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Test your knowledge and expertise in cybersecurity with our comprehensive quiz designed for the IAS Finals. Dive into 126 meticulously crafted questions that cover a wide range of topics, ensuring you are well-prepared for your certification exams.Whether you're a student or a professional looking to refresh your skills, this quiz will challenge you with:Real-world scenariosThe latest security protocolsKey concepts in network security","img":"https:/images/course8.png"}
More Quizzes
Quiz 14
10516
DNS BY Yousif Essam
8480
Boilermaker Trivia
211065
Kuiz
522622
Direct vs Indirect Rule - Colonial History
201019959
Which Euphoria Character Are You? - Free Personality
201016924
Childhood Emotional Neglect Test - Free Self-Assessment
201018498
Homestuck Character - Discover Your Skaia Title
201017234
Free Ecommerce: E‑Business vs Online Commerce
201021894
Which SK8 the Infinity Character Are You?
201017428
One Word to Describe Me - Free, Instant Result
201016984
Vilken Mumin är du? Gratis personlighetstest online
201016863