AWS-DA(251-260)

AWS Security and Optimization Quiz
Test your knowledge of Amazon Web Services (AWS) with our engaging AWS Security and Optimization Quiz. This quiz is designed for developers and cloud professionals looking to deepen their understanding of AWS best practices, including encryption methods, IAM roles, and performance optimization techniques.
- 10 challenging questions
- Multiple-choice format
- Focus on real-world scenarios
A developer chooses to use Amazon S3 to store highly secure data and want to build server-side encryption (SSE) with granular control over who may access the master key. For security reasons, company policy demands that the master key be established, cycled, and deactivated easily as necessary. Which option is most appropriate for meeting these requirements?
A. SSE with Amazon S3 managed keys (SSE-S3)
B. SSE with AWS KMS managed keys (SSE-KMS)
C. SSE with AWS Secrets Manager
D. SSE with customer-provided encryption keys
A server-side application running on Amazon EC2 instances needs access assets contained in an Amazon S3 bucket that have been secured using AWS KMS encryption keys (SSE-KMS). To decrypt the items, the program must have access to the customer master key (CMK). Which sequence of actions will provide access to the application? (Select two.)
A. Write an S3 bucket policy that grants the bucket access to the key.
B. Grant access to the key in the IAM EC2 role attached to the application's EC2 instances.
C. Write a key policy that enables IAM policies to grant access to the key.
D. Grant access to the key in the S3 bucket's ACL
E. Create a Systems Manager parameter that exposes the KMS key to the EC2 instances.
Amazon Cognito is being used by a social networking firm to synchronize profiles across many mobile devices, enabling end users to enjoy a consistent experience. Which of the following setups enables customers to be notified quietly whenever an update is ready for their other devices?
A. Modify the user pool to include all the devices which keep them in sync.
B. Use the SyncCallback interface to receive notifications on the application.
C. Use an Amazon Cognito stream to analyze the data and push the notifications.
D. Use the push synchronization feature with the appropriate IAM role.
The Lambda function below is invoked through an API request made using Amazon API Gateway. The Lambda function typically executes in less than a second. The Lambda function's pseudocode is displayed in the exhibit.
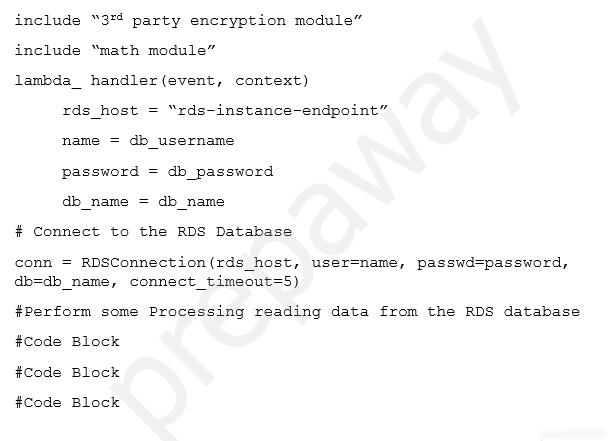
Which two measures may be performed to increase this Lambda function's performance without raising the cost of the solution? (Select two.)
A. Package only the modules the Lambda function requires
B. Use Amazon DynamoDB instead of Amazon RDS
C. Move the initialization of the variable Amazon RDS connection outside of the handler function
D. Implement custom database connection pooling with the Lambda function
E. Implement local caching of Amazon RDS data so Lambda can re-use the cache
A developer has constructed a huge Lambda function, but deployment encounters the following error: ClientError: When invoking the CreateFunction action, an error occurred (InvalidParameterValueException): The unzipped file size must not exceed XXXXXXX bytes€TM, where XXXXXXXX is the current Lambda limit. What is the Developer's role in resolving this issue?
A. Submit a limit increase request to AWS Support to increase the function to the size needed.
B. Use a compression algorithm that is more efficient than ZIP.
C. Break the function into multiple smaller Lambda functions.
D. ZIP the ZIP file twice to compress it further.
A developer is using Amazon S3 to store sensitive data created by an application. The developer want to encrypt the data while it is in transit. A corporate policy demands an audit trail detailing when and by whom the master key was used. Which encryption method will satisfy these criteria?
A. Server-side encryption with Amazon S3 managed keys (SSE-S3)
B. Server-side encryption with AWS KMS managed keys (SSE-KMS)
C. Server-side encryption with customer-provided keys (SSE-C)
D. Server-side encryption with self-managed keys
An Amazon EC2 instance is configured with an IAM role that expressly forbids access to all Amazon S3 API activities. The EC2 instance credentials file contains the IAM access key and secret access key, both of which provide full administrative access. Which of the following statements is accurate in light of the fact that this EC2 instance supports several types of IAM access?
A. The EC2 instance will only be able to list the S3 buckets.
B. The EC2 instance will only be able to list the contents of one S3 bucket at a time.
C. The EC2 instance will be able to perform all actions on any S3 bucket.
D. The EC2 instance will not be able to perform any S3 action on any S3 bucket.
A developer is storing application data in Amazon DynamoDB. The developer want to further optimize the application's performance by minimizing the time required to conduct read and write operations. Which DynamoDB functionality should be utilized to accomplish these goals?
A. Amazon DynamoDB Streams
B. Amazon DynamoDB Accelerator
C. Amazon DynamoDB global tables
D. Amazon DynamoDB transactions
A developer wrote configuration requirements for an AWS Elastic Beanstalk application in a file entitled healthcheckurl.yaml in their application source bundle's.ebextensions/directory.
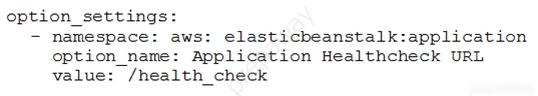
The following information is included in the file: Following the application's start, the health check is not executed on the right route, despite the fact that it is legitimate. How can this configuration file be corrected?
A. Convert the file to JSON format.
B. Rename the file to a .config extension.
C. Change the configuration section from options_settings to resources.
D. Change the namespace of the option settings to a custom namespace.
A developer is developing an AWS Lambda function to produce and publish a weekly newsletter to 100,000 subscribers dynamically. This mail includes both static and dynamic content. The developer need a highly scalable and quick storage location for the photographs that will be hyperlinked throughout the newsletter. Where is the developer supposed to save these images?
A. Use an Amazon DynamoDB table with DynamoDB Streams and read capacity auto scaling enabled.
B. Use an Amazon S3 bucket and S3 Transfer Acceleration to speed up the image download.
C. Use an Amazon Aurora database with a public DNS endpoint and auto scaling enabled.
D. Use an Amazon S3 backed Amazon CloudFront distribution with a high Time-to-Live (TTL) to maximize caching.
{"name":"AWS-DA(251-260)", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Test your knowledge of Amazon Web Services (AWS) with our engaging AWS Security and Optimization Quiz. This quiz is designed for developers and cloud professionals looking to deepen their understanding of AWS best practices, including encryption methods, IAM roles, and performance optimization techniques.10 challenging questionsMultiple-choice formatFocus on real-world scenarios","img":"https:/images/course1.png"}
More Quizzes
Cloud Fundamentals
1478
AWS-DA(151-160)
10513
100
Who knows me the worst?
12612
Test Your E - IE Stem Changing Spanish Verbs - Free
201055321
Egyptian Language Phrases: Master Common Greetings
201039893
Test Your Nature Trivia: Ultimate Tree Challenge
201049212
Free General Aptitude Assessment
201029881
US History Since 1877
15820407
Free Counseling Theories Knowledge Test
201027995
Which Avatar: The Way of Water Character Are You? Find Out!
201026630
Parental Anxiety: Panic & Anxiety Disorders Test
201030225