CIS103 FINAL EXAM

CIS103 Final Exam Quiz
Welcome to the CIS103 Final Exam Quiz! This comprehensive assessment covers key topics in information systems. Test your knowledge and understanding with 50 carefully crafted questions.
Prepare yourself for a range of concepts, including:
- IT Infrastructure and Architecture
- CRM and E-Business
- Database Management and Design
- Feasibility Studies in IT Projects
1-is a high-level map or plan of the information assets in an organization.
IT Infrastructure
IT Components
IT Personal
IT Architecture
2-delegates (hiring) operations or jobs within a business to another company.
Insourcing
Outsourcing
Offshoring
Supply Chain
3-Yarmouk University has agreed with Transport Company to transfer its employees to and from the University, there is a bus station out of university which loads the employees to their homes at 5 PM; this agreement Called?
Insourcing
Outsourcing
Offshoring
Supply Chain
4- is the process of shaping, manipulating, and transmitting digitized content can be done at very high speeds, so that users do not have to think about these processes .
Virtual
Digital
Make to Order
Mobile
5-Digital divides are an example of which type of business pressure?
Market pressure
Social pressure
Technological pressure
Competitive pressure
6- Which of the following statement is/are correct about CRM.
Stands for Customer Relationship meaning
Stands For Customer Relationship management
Is an information system to manage the relationship between customer and companies.
B+C
7-is the difference between attracting and keeping customers by providing superb customer service to losing them to competitors.
Make To Order
Mass Customize
Customer Focus
Strategic System
8-buying, selling, transferring, or exchanging products, services, or information via computer networks, including the internet also refers to servicing customers, collaborating with business partners, and performing electronic transaction within an organization
E-Commerce
E-Business
Customer Focus
Mass Customize
10-is a particular characteristic or quality of a particular entity.
Entity
Attribute
Foreign key
Primary key
11-is a field in one table that uniquely identifies a row of another table.
Identifier
Foreign key
Primary key
A+b
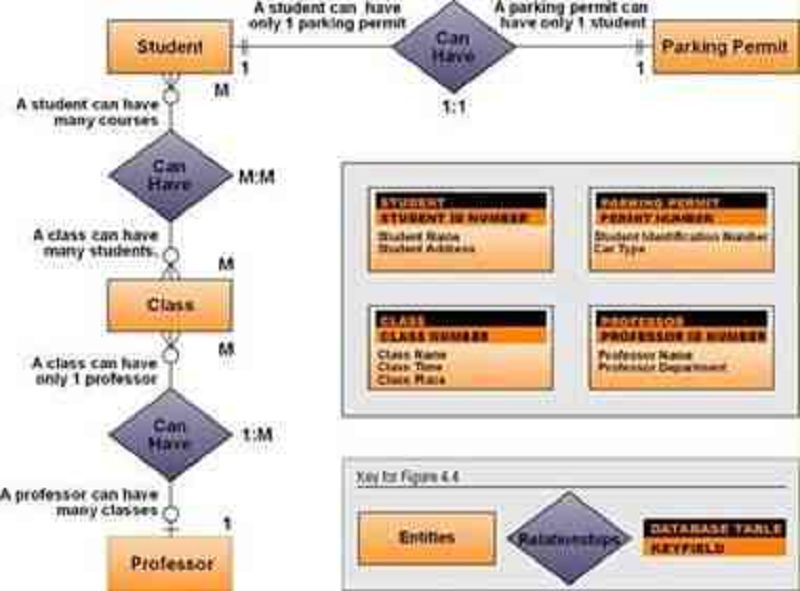
12-From the Image shown, which of the following Entities is/are Mandatory entity for the student.
Class
Professor
Parking
None.
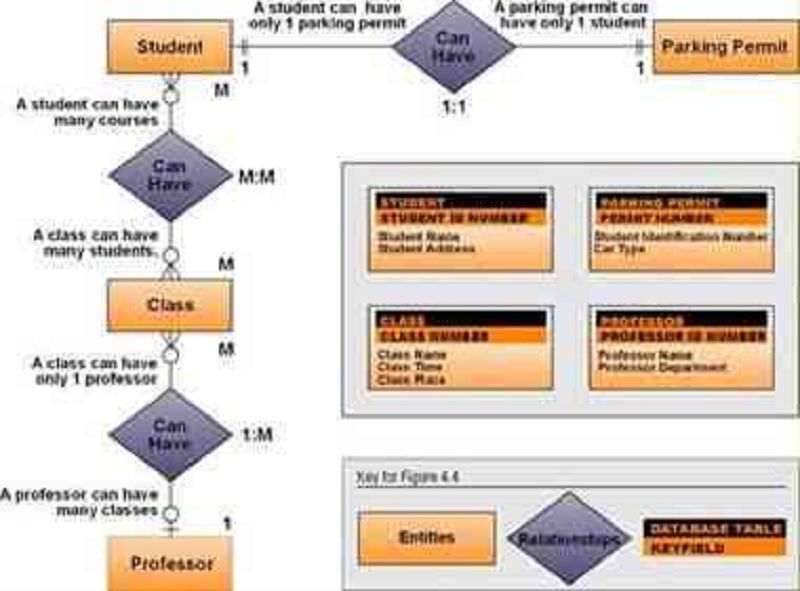
13-From the Image shown, which of the following Entities is/are Optional entity for the student.
Class
Parking
A+B
Non.
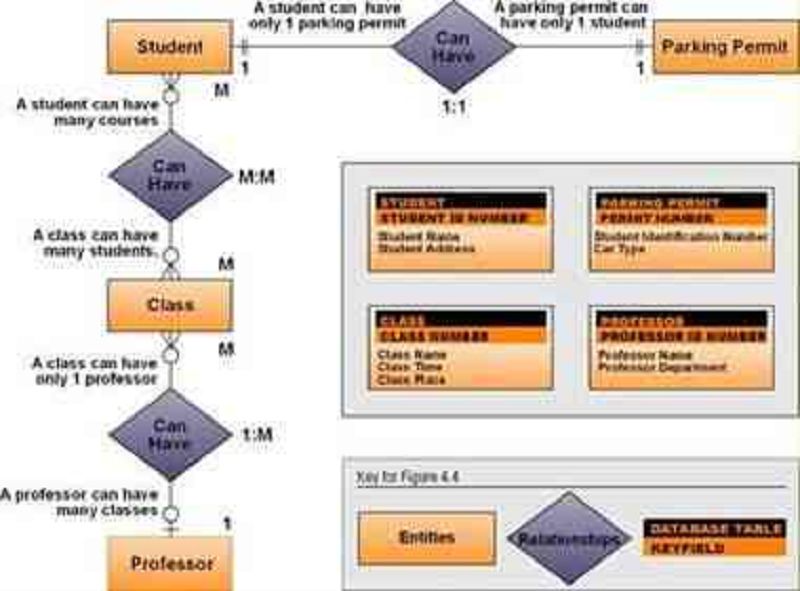
16-From the Image shown, the primary key of parking entity is:
Student ID number
Permit Number
Class Number
Car type
17-provides minimum redundancy , maximum data integrity , and best processing performance
Data base management system
Structured Query Language.
Programing Language.
Normalization.
18-is a small data warehouse, designed for the end-user needs in a strategic business unit (SBU) or a department.
Data Marts
Data base
Data storage
Non.
20-is the knowledge that has been documented in a form that can be distributed to others or transformed into a process or a strategy
Implicit knowledge
Explicit Knowledge
Formal knowledge
Organizations Knowledge
24-is a prioritized list of both existing and potential IT applications of a company.
Application systems
Application portfolio
Application management
Acquiring Application
25- A method of delivering software in which a vendor hosts the applications and provides them as a service to customers over a network, typically the Internet.
Customize a prewritten application
ASP
SaaS
Use open-source software
26- uses single database and single application for all customer.
Customize a prewritten application
ASP
SaaS
Outsourcing
27-The Deliverable from System analysis step in SDLF is:
Technical specification
Go/No Go
User requirements
Non.
28- Assessment of the human issues involved in a proposed project, including resistance to change and skills and training needs.
Economic feasibility.
Organizational feasibility.
Technical feasibility.
Behavioural feasibility.
29-Is a process that introduces components of the new system in stages, until the entire new system is operational.
Direct conversion.
Pilot conversion.
Phased conversion.
Parallel conversion.
30- A process that continues throughout the life of the system.
Maintenance.
Debugging.
Updating.
Testing.
31- A group –based tool for collecting user requirements and creating system designs.
Joint application design (JAD).
Integrated Computer-Assisted Software Engineering (ICASE) Tools
Rapid Application Development (RAD)
Computer-Assisted Software Engineering (CASE)
32- is a development method that uses special tools and an iterative approach to rapidly produce a high-quality system.
Agile.
Computer-Assisted Software Engineering (CASE)
Integrated Computer-Assisted Software Engineering (ICASE) Tools
Rapid Application Development (RAD)
33-Development method that delivers functionality in rapid iterations requiring frequent communication, development, testing, and delivery.
Agile.
End-User Development
Component-Based Development
Rapid Application Development (RAD)
34- is a collection of principles that are intended to guide decision making by members of an organization.
Ethics
Code of Ethics
Legal
Illegal
35-means a determination of who is responsible for actions that were taken.
Responsibility
Liability
Accountability
Code of ethics
36- the issue which involves the authenticity, fidelity and accuracy of information that is collected and processed.
Privacy Issues
Accuracy Issues
Property Issues
Accessibility Issues
37- is the right to determine when, and to what extent, information about yourself can be gathered or communicated to others.
Privacy
Information privacy
Security
Non.
38- is an informal, personal journal that is frequently updated and intended for general public reading
Blogs.
Forums.
Lack of management support
Information on Internet Bulletin Boards.
39-occurs when Company A’s systems are attacked and taken over by the perpetrator. Company A’s systems are then used to attack Company B system.
Government legislation
Cybercrime
Downstream liability
Unmanaged devices
40-is the possibility that the system will suffer harm by a threat.
Threat to an information
Exposure of information resources
System’s vulnerability
Risk
41-all of the following options indicate Human errors which affect information Security except.
Viruses
Carelessness with one’s office
Carelessness with using unmanaged devices
Careless Internet surfing
42- is a computer program that hides in another computer program and reveals its designated behavior only when it is activated.
Virus
Worm
Trojan horse
Logic bomb
43 -An attacker sends so many information requests to a target system that the target cannot handle them successfully and can crash the entire system.
Virus
Trojan horse
Logic bomb
Denial-of-service
44- takes advantages of newly discovered, previously unknown vulnerability in a software product.
Virus
Logic bomb
Zero-day-attack
Phishing attack
45- Software that gathers user information through the user’s Internet connection without their knowledge
Spyware
Spamware
Adware
Cookies
46-are small amounts of information that Web sits store on your computer, temporarily or more or less permanently.
Data warehouses
Spyware
Spamware
Cookies
47-determines which actions, rights, or privileges the person has, based on verified identity.
Authentication.
Authorization.
Communication control.
Application control.
48-Includes Regular ID card, Smart ID card, Tokens (chips and digital display).
User is
User has
User knows
User does
{"name":"CIS103 FINAL EXAM", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Welcome to the CIS103 Final Exam Quiz! This comprehensive assessment covers key topics in information systems. Test your knowledge and understanding with 50 carefully crafted questions.Prepare yourself for a range of concepts, including:IT Infrastructure and ArchitectureCRM and E-BusinessDatabase Management and DesignFeasibility Studies in IT Projects","img":"https:/images/course3.png"}
More Quizzes
Database Normalization
84489
Introduction to database concept
1050
The Orcas Quiz
1266
How Compatible Are We Actually?
840
Free Root Word: Which is the Root?
201024326
Lyric Theatre Voice
15824533
Government and Politics of Japan
15819899
158/92 Blood Pressure: Test Your Secondary Hypertension Smarts
201051417
Test Your Skills: Direct and Indirect Characterization
201025183
What Country Should I Visit? Find Your Dream Spot
201033352
Free Circumcenter Practice Problems
201022472
Electromagnetic Fields II
15827419

