Secure Programmingn Foundation

Secure Programming Foundation Quiz
Test your knowledge and awareness of security principles and practices with our comprehensive quiz on secure programming. This quiz is designed to provide insights into various topics that specialists in the field must know.
- 47 Engaging Questions
- Multiple Choice Format
- Improves Security Awareness
Welcome to the Secure Programming Foundation quiz!
This quiz serves to give an impression about security knowledge and awareness. The most honest results are obtained when you do the quiz without using Google or any other reference - which wasn't your intent anyway, because integrity is one of your Friss habits, right? ;-)
Hope this quiz gives you some extra insights and awareness - enjoy!
Attackers and defenders are two players within the field of security. Why is the attacker at an advantage?
An attacker only needs to find one flaw; defenders need to consider all possible flaws.
An attacker is more skilled and determined than a defender
An attacker abuses new technologies that a defender has to install.
An attacker has more computing power that he can use for performing all kind of attacks.
Some well known security principles are used when designing secure systems. One of them is an application design that prevents single points of failure with security redundancies and layers of defense. What principle is used to accomplish this design?
Defend in depth
Grant least privilege
Fail securely
Separate privileges
The following authorization header is sent by the browser to the server in response to a "401 Authorization Required" response: Authorization: Basic bmFtZTpwYXNzd29yZA== Is it safe to send this header using the HTTP protocol?
Yes, because the value is encrypted and cannot be reversed.
Yes, because the value is used only once and changes with every request.
No, because the value is encrypted using a weak algorithm.
No, because the value can be sniffed and reversed to valid credentials.
The term SOP most commonly refers to the mechanism that controls access for JavaScript and other scripting languages to the DOM properties and methods across domains. Which conditions have to be satisfied to grand access between two interacting pages that do NOT use the document.domain property?
Protocol, IP number and - for browsers other than Microsoft Internet Explorer - port number
Protocol, domain name and - for browsers other than Microsoft Internet Explorer - port number
Protocol, PTR record and - for browsers other than Microsoft Internet Explorer - port number.
Protocol, FQDN and - for browsers other than Microsoft Internet Explorer - port number.
An application allows a user who is logged in to change his/her password. This function is only available for authenticated users and uses the HTTPS protocol to send the data. What is considered BEST PRACTICE to perform the password change?
Ask the user for the login name, old password, new password and confirmation of this password.
Ask the user for the new password and confirmation of this password.
Ask the user for the old password, new password and confirmation of this password.
Use the session data to identify the user and ask for the new password and confirmation of this password.
When storing passwords in a file or a database, what is the BEST approach?
Store the hashed value of the password that the user has chosen including a random salt.
Store the hashed value of the password that the user has chosen including a fixed salt.
Store the plain text value of the password that the user has chosen.
Store the encrypted value of the password that the user has chosen including the initialization vector.
HTTP sessions are used to keep state between several requests and use a session ID for identification. What is the MOST important practice in regard to the session ID?
The session ID should be kept secret at all times.
The session ID should change with every POST request.
The session ID should be at least ten characters long.
The session ID should be encrypted using a strong algorithm.
An application uses a single sign-on implementation that is specifically designed for web-based environments. The user logs in through the identity provider and uses two different applications that participate in the same single sign-on implementation. You are facing some challenges when implementing the logout feature. What is the BEST way to solve implementing the logout feature for these two applications?
Implement a logout function that invalidates the session for the current application and not the single sign-on session.
Implement a logout function that invalidates the single sign-on session and depend on the session-timeout for participating applications.
Implement a logout function that invalidates the single sign-on session and the session for the current application.
Implement two logout functions: one for the current application and one that in addition invalidates the single sign-on session.
Your web application uses sessions to maintain state. A user logs in but does not allow cookies to be set. You have to implement an alternative solution for keeping track of the session ID. The session ID is a random 96 bits value and all communication is based on HTTPS. Within this scenario, what is the BEST way to keep track of the session ID?
Use a URL parameter that contains the session ID.
Use a hidden parameter that contains the session ID.
Use a URL parameter that contains the encrypted session ID.
Use a combination of HTTP headers to generate the session ID.
What is CSRF?
Cross Script Reference Fault: mistakenly, the browser references a script file from another website
Cross Server Response Forgery: an attacker intercepts the response sent from server to client and replaces it by his own (malicious) response
Cross Site Request Forgery: an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated
Constructed SQL Result Forgery: by injecting SQL commands an attacker obtains other/additional data than originally was aimed for by the application
What is the BEST solution to prevent CSRF attacks?
Use the Referrer-header to check the origin of the previous request.
Make requests unpredictable by adding a random value and check this value.
Use HTTPS to protect all communication between the client and the server.
Make sure that session fixation is not possible which also prevents CSRF attacks.
Direct and parameterized queries are two techniques to execute queries that are partly based on user input. Which of the following statements in regard to direct and parameterized queries when used properly is correct?
A direct query filters meta-characters more efficiently than parameterized queries.
A direct query filters meta-characters less efficiently than parameterized queries.
A direct query uses placeholders to process input and a parameterized query uses the supplied parameters
A direct query uses the supplied parameters for input and a parameterized query processes input through placeholders
Vulnerabilities exist in different contexts. Two identifiable contexts are the server side and client side contexts. It is important to understand whether a vulnerability is focussed on the server portion of the application (server context) or the client running it (client context). SQL injection and XSS are two different types of vulnerabilities. In which context do these two vulnerabilities exist?
SQL injection vulnerabilities exist on the client side and XSS vulnerabilities exist on the server side
SQL injection vulnerabilities exist on the server side and XSS vulnerabilities exist on the client side.
Both SQL injection and XSS vulnerabilities exist on the client side.
Both SQL injection and XSS vulnerabilities exist on the server side.
You are assigned the honorable task to prevent SQL injection in a small web application. You have listed all lines of code where user input ends up in a SQL query. You also want to make sure that future involvements do not introduce new SQL injection vulnerabilities. What is the BEST solution to accomplish this task?
Write and use your own routines that escape all input for all database products and rewrite the necessary lines of code.
Use a transparent layer provided through standard libraries that escapes all input and rewrite the necessary lines of code.
Prevent the leakage of information about the database product that is used to make SQL injection impossible.
Prevent the application from showing detailed error messages since these are needed to exploit a SQL vulnerability.
Testing input against a list of known negative inputs which is implemented when you compile a listing of all the negative or bad conditions and then verify if the received input is not included in the list is a technique for filtering input. What is the name of this filtering technique?
Implementing the Graylist method for input validation.
Implementing the Blacklist method for input validation.
Implementing the Whitelist method for input validation.
Implementing Regular Expressions for input validation.
Validation of user input is possible at the client (browser) and at the server portion of the application. What is the BEST solution to perform validation of user input?
Perform validation of user input at the client (browser).
Perform validation of user input at the server portion of the application.
Perform validation of user input both at the client (browser) and the server portion of the application
Perform validation of user input either at the client (browser) or the server portion of the application.
Your web server is set to use UTF-8 encoding for input and output. Some of your validation routines are based on legacy libraries that only accept ISO/IEC 8859 character sets. You have written conversion routines to be used for handling input and output to the validation routine. A user is allowed to enter his/her name in a web form. The input is validated by the validation routines and reflected to the user in the HTML body. What needs to be done with the input to display the output properly and safely?
The input needs to be normalized, converted and HTML encoded.
The input needs to be normalized, stripped and HTML encoded.
The input needs to be converted, stripped and HTML encoded.
The input needs to be normalized, stripped and converted.
An attacker has found two input fields that result in a buffer overflow condition. This condition happens within a function that converts all upper case input into lower case and is than used to execute a search. Where does the buffer overflow reside and what does it allow for?
This buffer overflow resides on the heap and allows for code execution.
This buffer overflow resides on the heap and allows for data manipulation.
This buffer overflow resides on the stack and allows for data manipulation.
This buffer overflow resides on the stack and allows for code execution.
An attacker found a vulnerability within a web application. He discovered that one of the parameters in the URL can be used to add JavaScript code which is executed within the browser when he sends the request to the website. Which of the following statements BEST describes this vulnerability?
This is a stored XSS vulnerability. The attacker needs to entice the victim to visit the URL.
This is a stored XSS vulnerability. Exploitation occurs when someone uses the web application.
This is a reflected XSS vulnerability. The attacker needs to entice the victim to visit the URL.
This is a reflected XSS vulnerability. Exploitation occurs when someone uses the web application
As the developer of a web application, you are assigned the task to implement a strong defense against server XSS. What is the easiest and strongest defense against Server XSS?
Stripping all JavaScript from user input.
Context-sensitive server side output encoding.
Using safe JavaScript APIs.
Using safe third-party JavaScript code.
Members of the HR department within your company are responsible for maintaining your personal information that resides in the HR application. Information in regard to your working performance is also stored through the HR application but read/write access to this information is limited to the manager of your department. One of the HR members is allowed to read the working performance for monitoring purposes. Authorization for the HR application is implemented according to the desired access model. On what type of authorization is access to data within the HR application based?
On horizontal authorization
On vertical authorization
On object and attribute authorization
On horizontal and vertical authorization
An authenticated user is authorized to edit, view and delete records that describe all individual parts that belong explicitly to a product that is manufactured by the department he is working for. The company manufactures other products, but the user is not authorized to access parts that belong to these other products. The authenticated user discovers that he is able to get access to unauthorized parts by simply changing a form value that represents the part-number. What is the MOST likely reason for this authorization failure?
The authorization is based on insecure direct object references.
The authorization is based on insecure indirect object references.
The authorization is based on incomplete indirect object references
The authorization is based on incomplete direct object references.
Suppose that two separate actions operate on the same resource and that checks are used to validate if the process is allowed to use the resource. What is the attack called that abuses the time window between the check (TOC) and use (TOU) of the resource?
A session poisoning attack
A race condition attack
An atomic operation attac
An application flow attack
Why is hardening of systems a very important security control?
Third party software is not always written with security in mind.
Third party Firewalls do not protect the exposed services properly.
Third party services are always on and insecure by default and need protection.
Third party software is not both functional and secure out-of-the-box.
Hardening of a system consists of various adjustments. Which of the following is NOT considered hardening of a system?
Applying the latest security patches.
Disabling or removing debug features.
Compiling code with ASLR and DEP protection.
Changing default passwords.
A web application detects an error when handling a request. Instead of displaying full information about the error, a general page including a reference about the error is returned. All information about the error is logged locally, including the reference. What is MOST likely the primary reason for this solution?
This prevents unnecessary leakage of internal information.
This is more user friendly than displaying the full error message.
This prevents unnecessary usage of bandwidth.
This is the preferred way for developers to solve and administer errors
A web application is designed with logging various types of information in mind. Which type of information is MOST important for logging information with regard to security?
Version information of the modules that are started
Stack traces that are generated during an error.
The entrance, duration and exit timestamps of procedure calls.
Increase and decrease of privilege levels for logged-in users.
As a developer you have coded to catch every potential error and you have provided a solution that ensures that the code will not be left in an insecure state. What application security principle is described above?
Complete mediation
Fail securely
Detect intrusion
Fail-safe defaults
As a developer you are concerned about performance and availability of your application. Instead of depending solely on the implementation of a large and extensible server farm, you also implement a solution that limits the amount of resources that can be allocated to a single user. Which purpose BEST describes the reason behind this solution?
To speed up processing
To prevent unexpected behavior
To mitigate a DoS attack
To reduce the server farm
When developing an application that uses cryptography, what is the BEST strategy to choose a cryptographic library?
Develop it yourself: open source libraries can't be trusted. Proof is Heartbleed.
Use an open source library and audit it yourself.
Use a commercial library like RSA's Bsafe; they have been audited by professionals.
Use either an open source or a commercial library and write a security assumption that they are out of scope for your security requirement.
What is the difference between symmetric cryptography and asymmetric cryptography?
Symmetric cryptography is based on symmetric passwords. Asymmetric cryptography allows all passwords.
Symmetric cryptography needs the same operating system for user and browser. Asymmetric cryptography does not.
Symmetric cryptography is based on both user and software using the same key. Asymmetric cryptography uses a public key.
Symmetric cryptography checks a password against a stored password. Asymmetric cryptography uses a randomly added string.
Why is a website, of which the certificate is revoked, a risk?
Because a website with a revoked certificate may not be the website you intended to visit.
Because the certificate authority that gives out the certificate has been proven to be bad.
Because the browser is not working correctly, you are shown this error. You need to update.
It is not a risk, because the original certificate was given out by a trusted certificate authority.
You are assigned to set up a website that uses HTTPS. For this purpose you have requested and installed a certificate that is signed by a well-known CA (Certification Authority). What is NOT something that you have to do in order to implement the HTTPS server securely?
Disable all protocols that are not supported by the server's OS.
Configure the server to allow only strong protocols and ciphers.
Implement HSTS to allow for browser based mitigation.
Configure the server or application to add the 'secure' flag on session cookies.
A Swiss bank needs a non-repudiation requirement for the following functional requirement: "As an account holder, I can transfer money from one account to another." You are asked to help them. What is an appropriate non-repudiation requirement?
All login attempts should be logged.
Transfers can only be done from one of the account holder's accounts.
Every transfer must be logged.
Negative amounts are not allowed.
Given this requirement: "When a user has forgotten his/her password, the user must be able to change it." What is the hidden assumption here?
It is assumed that users should only be able to change their own password.
It is assumed that passwords should have a minimum length
It is assumed that users do not write down their passwords.
It is assumed that a user's identity can be established before changing the password.
What security principle states that access is denied and the security scheme identifies when access is permitted?
Default deny
Defense in depth
Least privilege
Input validation
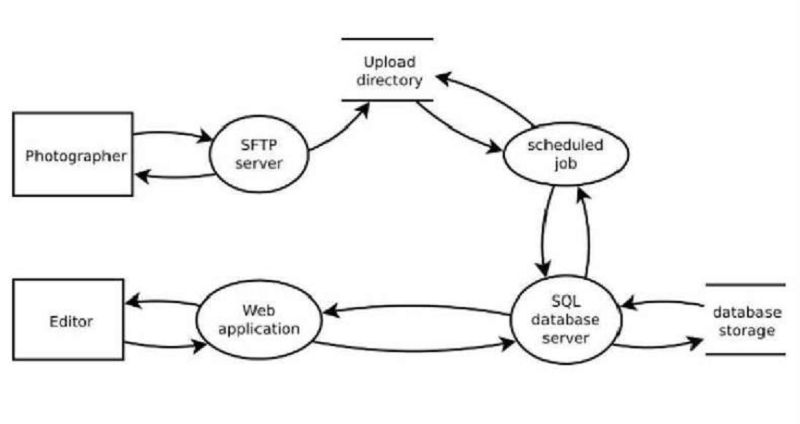
A newspaper has deployed an editing platform. Its architecture is described below and illustrated with a Data Flow Diagram (DFD). 1. Photographers all over the globe can log in and upload photos using SFTP (Secure FTP). 2. The photos are placed in an upload-directory. 3. The system runs a regularly scheduled process to move the photos from the upload-directory into a SQL database. 4. Editors at the office use the web application to browse the photos and add some photos to articles for publication. (There is no photo-editing feature, photos are published as-is). A threat analysis identified this risk: Photographers can create malformed filenames that trigger a shell injection attack. If an attacker uploads a file that contains shell commands, the code that should copy the file will execute those shell commands. The architects replace the SFTP file-upload and the scheduled job with a web interface that inserts the photos directly into the database, hoping to get a more secure system. Choose the BEST answer. Will the system be more secure?
Yes, this solves the problem completely.
Yes, but only if the web interface is free of security problems.
No, this fix does not deal with identity spoofing attacks.
No, this does not fix the problem at all.
Which of the following is NOT a principle of secure design?
Allow for future security enhancements
Design security through secrecy.
Implement least privilege.
Isolate security controls.
Which definition BEST describes a vulnerability scan?
A series of automated tests for known problems.
A test performed by security experts.
A stress test to make the application crash.
A review of vulnerabilities in the design.
Which of the following things should effective security testing involve?
Testing of people
Testing of process
Testing of technology
All of the above
What is a significant disadvantage of MANUALLY inspecting code?
The review is performed too quickly to be thorough, when done manually.
Manual inspection cannot be applied to many situations.
Manual inspection requires significant human thought and skill to be effective.
The manual review requires the assistance of complex technologies.
What is a significant disadvantage of AUTOMATICALLY inspecting code?
It generates a lot of reported issues which need to be scanned manually
Automatic tools still have difficulties in finding issues
Automatic tools cannot detect security issues
Automatic tools don't understand the dataflow and the way of thinking that a developer has
What can be said about manual code reviews?
My code does not require code reviews
Manual code reviews are useless, they should always be automated
Code reviews are a good way to catch the inevitable coding mistakes
Code reviews should be done by an external company
What can be said about testing?
Testing should be done by testers ("developers don't test")
My code does not require testing
Testing should be done as early as possible
It is always hard to automate testing so you need testers for that
Starting from what stage in the SDL are security requirements involved?
Requirements phase
Design phase
Implementation phase
Verification phase
Release phase
Response phase
What is your role in the organization?
Manager
Developer
Tester
Consultant
Support
{"name":"Secure Programmingn Foundation", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Test your knowledge and awareness of security principles and practices with our comprehensive quiz on secure programming. This quiz is designed to provide insights into various topics that specialists in the field must know.47 Engaging QuestionsMultiple Choice FormatImproves Security Awareness","img":"https:/images/course5.png"}
More Quizzes
Secure Application Development Quiz
11623
Secure Application Development Quiz
11632
Christina's Family Quiz
10518
What Scandinavian are you?
6330
Love Destiny - Discover Your True Relationship Path
201016772
Introduction to Programming Practice - Free Online
201017323
Great Gatsby Chapter 7 - Free Online Practice
201017072
Are You a Robot Test - Free Online Self‑Check
201017452
Which Bundesliga Team Should I Support? Free
201017857
Cocktail: Test Your Mixology Knowledge (Free)
201017196
12 Archetypes Test (Free) - Discover Your Jungian Type
201018364
Titanic: Test Your Knowledge of the Historic Ship
201016543