العبيد نهائي
Zone-based policy firewall uses three different zones. Which zone has a limited trust?
OUTSIDE
DMZ
INSIDE
A new web server is to be deployed in a network using ZPF. In which Zone the new server could be deployed?
OUTSIDE
DMZ
INSIDE
Zone based firewall divides the network into three security zones. Which zone is used for servers?
OUTSIDE
DMZ
INSIDE
Zone-based policy firewall uses three different zones. Which zone is highly untrusted?
OUTSIDE
DMZ
INSIDE
Zone based firewall divides the network into three security zones. Which zone is highly untrusted?
OUTSIDE
DMZ
INSIDE
Zone-based policy firewall uses three different zones. Which zone is highly trusted?
OUTSIDE
DMZ
INSIDE
Zone based firewall divides the network into three security zones. Which zone is highly trusted?
OUTSIDE
DMZ
INSIDE
In IDS deployment, one switch port is configured to the IDS using the configuration named:
SNAM
SNAP
SPAN
SPAM
Comparing IPS to IDS (Choose Two)
IDS provides alert only
IPS provides alert only
IDS provides alert + action
IPS provides alert + action
What is a signature?
A set of rules that an IDS and an IPS use to detect all intrusion activates
A software that an IDS and an IPS use to detect typical intrusion activity
A software that an IDS and an IPS use to detect all intrusion activity
A set of rules that an IDS and an IPS use to detect typical intrusion activates
Which of the following firewalls is an open-source firewall
CISCO ASA
PfSense
Palo Alto
When an IPS detects an attack, which action can the IPS take to prevent the attack from spreading
Enable bypass mode
Perform a Layer 6 reset
Deny the connection inline
Deploy an antimalware system
When IPS is compared to IDS, which of the following are correct? (Choose two)
IDS is deployed inline
IPS is deployed offline
IPS is deployed inline
IDS is deployed offline
Which of the following are some disadvantages of Network-based IPS
Cannot examine encrypted traffic
Operating system dependent
Provides operating system and application level protection
Protect after decrypting the message
Provides protection specific to a host operating system
Operating system independent
Cost effective
Must be installed in all hosts
Which of the following are some advantages of Network-based IPS(Choose Two)
Cannot examine encrypted traffic
Operating system dependent
Provides operating system and application level protection
Protect after decrypting the message
Provides protection specific to a host operating system
Operating system independent
Cost effective
Must be installed in all hosts
Which of the following are some advantages of Host-based IPS?(Choose Three)
Cannot examine encrypted traffic
Operating system dependent
Provides operating system and application level protection
Protect after decrypting the message
Provides protection specific to a host operating system
Operating system independent
Cost effective
Must be installed in all hosts
Which of the following are some disadvantages of Host-based IPS(Choose Two)
Cannot examine encrypted traffic
Operating system dependent
Provides operating system and application level protection
Protect after decrypting the message
Provides protection specific to a host operating system
Operating system independent
Cost effective
Must be installed in all hosts
When IPS is compared to IDS, which of the following are correct? (Choose Three)
IPS provides Alert + no action
Both IPS and IDS provide Alerts
IDS provides Alert + action
IDS provides Alert + no action
Both IPS and IDS provide action
IPS provides Alert + action
Which of the following are types of Firewall (Choose 4)
Packet Filter
Stateful firewall
Application firewall
NAT firewall
Physical firewall
IPS
Which of the following commands represents the standard IP ACL
Access list 101 deny tcp any host 192.168.1.1
Access-list 110 permit ip any any
Access-list 2500 deny tcp any host 192.168.1.1 eq 22
Access-list 50 deny 192.168.1.1 0.0.0.255
Match IPS and IDS with advantages and disadvantages
Disadvantages of IDS
Some impact on the network
Advantages of IDS
Stop attacks
Disadvantages of IPS
No impact on the network
Advantages of IPS
Can't stop attacks
Match
Vulnerabilities
Any event or action that could potentially cause Damage
Risk
When attacker accesses a computer system without the authorization
Intrusions
Any condition that leave a system open to harm
Threat
Is a technique that is used to exploit Vulnerability
Attack
A concept that indicate exposure the chance of damage
Match each IPS signature alrarm with its apporpriate description
Pattern-based
Search for abnormal behavior
Honey pot-based
Used to analyze security attacks
Anomaly-based
Same as ACL
Policy-based
Search for a specific pattern
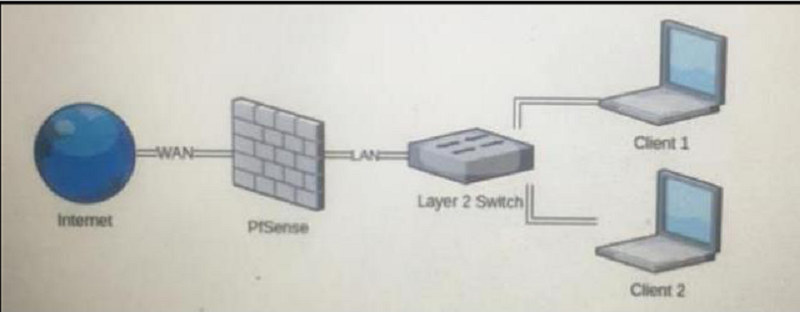
For the given topology above, select correct answers for normal daily network operation (Choose Three)
Client 1 can not connect to client 2
PfSense is a stateful firewall
Client 1 can connect to client 2
Any user from the internet can connect to client 1
Client 2 can connect to the internet
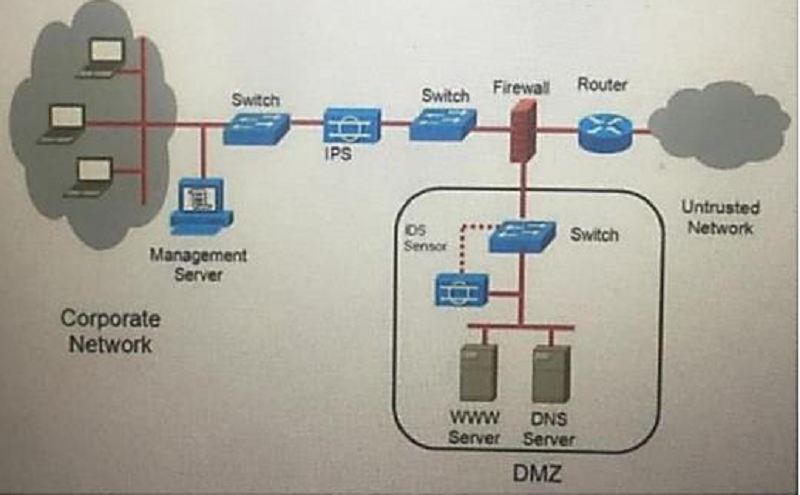
What is an advantage of placing an IPS on the inside of a network
It can provide greater security
It receives every inbound packet
It can provide higher throughput
It receives traffic that has already been filtered
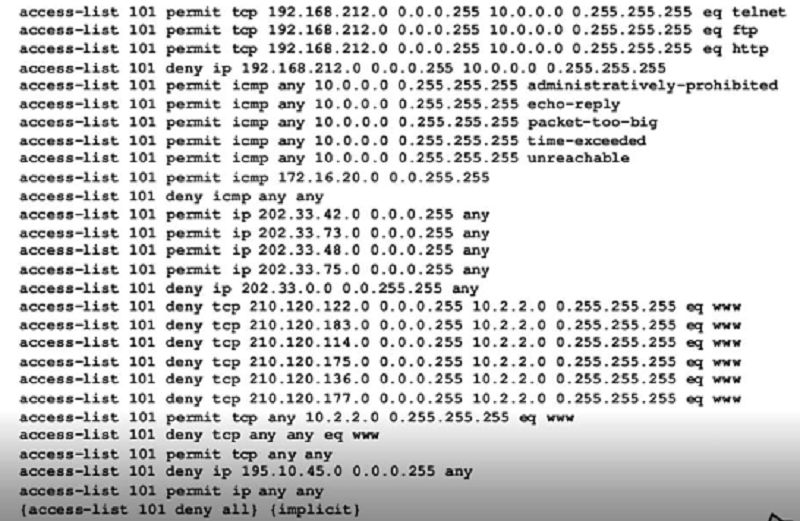
With reference to the above ACL, which of the following is correct? (Choose 2)
All web traffic (www) to 10.2.2.0/24
All FTP traffic is denied
Telnet is permitted from 192.168.212.0/24 to 10.0.0.0/8
All ICMP traffic is denied
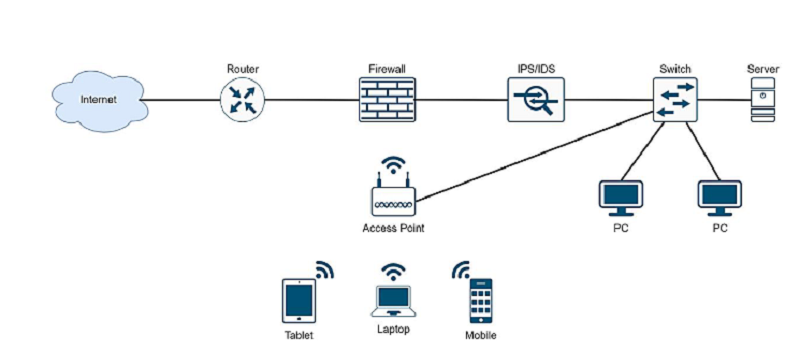
Which device in the above topology has the function of packet filtering?
Switch
Router
Firewall
IPS
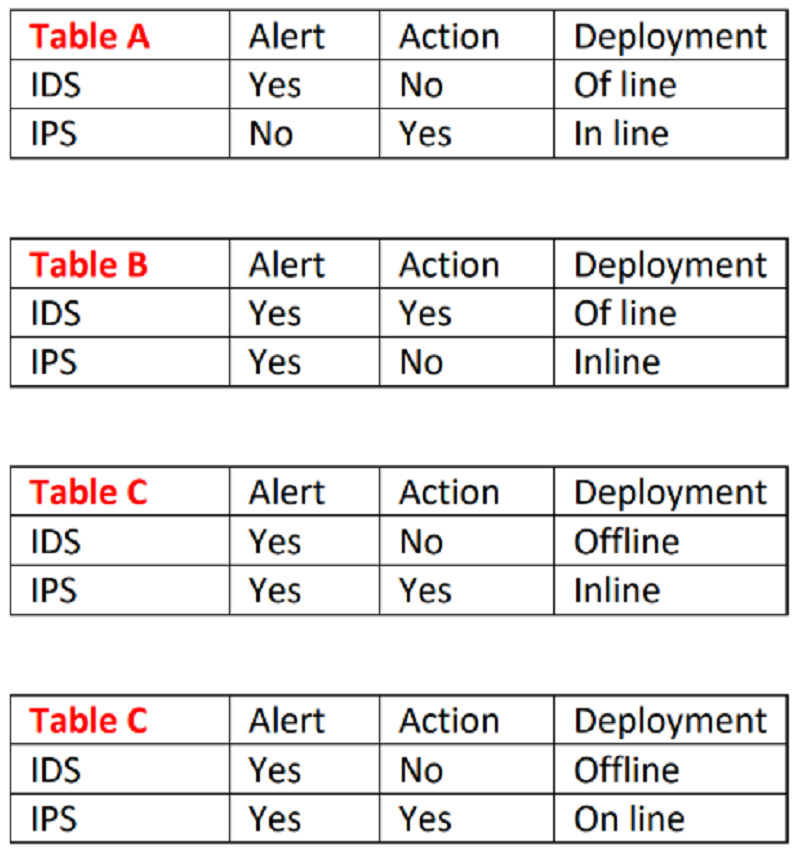
Which of the above tables is correct regarding IDS and IPS operations and deployment?
Table D
Table A
Table C
Table B
It is recommended to place Extended ACL close to the source
True
False
It is recommended to place standard ACL close to the destination
True
False
IPS can examine the entire content of the packet
True
False
Firewall examines only the source IP address
True
False
Digital signature is a set of rules that an IDS and an IPS use to detect all intrusion activities
True
False
To mitigate MAC address attacks
Disable tracking and DTP on access ports
Secure unused ports
Explicitly configure trunk ports and change native VLAN
Configure port security
The hacker is
A clever programmer capable of developing new programs and coding changes to existing programs to make them more efficient
A network professional that uses sophisticated programming skills to ensure that networks are not vulnerable to attack
A person who tries to gain unauthorized access to devices on the internet
Individuals who run programs to prevent or slow network access to a large number of users, or corrupt or wipe out data on servers
All above answers are correct
All above answers are not correct
SSH can be used to
Remote secure access through line vty
Unsecure remote access to a network device
Secure access through the device console
Which of the following is another name for a black hat hacker
Script kiddies
Ethical hacker
Security auditor
Cybercriminal
Which of the following is another name for a white hat hacker?
Script kiddies
Ethical hacker
Security auditor
Cybercriminal
If you are contracted to do a penetration test inside a company network, and submit a final report to the higher management, what type of hackers you are?
Grey hat hacker
Black hat hacker
White hat hacker
CIA stands for
Confidentiality, integrity, Authentication
Confidentiality, integrity, Availability
Confidentiality, integrity, Access of network
Computer, integrity, Availability
DDOS
Overwhelming the target with traffic from multiple sources
Overwhelming the target with traffic from single sources
Attacking several targets
Malware is
Any software used to protect the PC from viruses
Any software used to disrupt computer operations
Any software used to clean up the disk
Trojan horse
It's a malicious code that is attached to executable files
It's a malware that carries out malicious operations under the guise the desired function
The attacker attempts to trick people to reveal secret information
Replicate themselves by independently exploiting vulnerabilities in networks
Virus
It's a malicious code that is attached to executable files
It's a malware that carries out malicious operations under the guise the desired function
The attacker attempts to trick people to reveal secret information
Replicate themselves by independently exploiting vulnerabilities in networks
Worm
It's a malicious code that is attached to executable files
It's a malware that carries out malicious operations under the guise the desired function
The attacker attempts to trick people to reveal secret information
Replicate themselves by independently exploiting vulnerabilities in networks
Authentication is
Reviewing log files
Defining the allows and denials of resource and object access for a specific identity
Who are you
How are you
Authorization is
Who are you?
What you can do
Reviewing log files
Proving that you are that identity
Accounting is
What you can do
Proving that you are that identity
Defining the allows and denials of resource and object access for a specific identity
What you have done
To mitigate VLAN Attacks (Choose Three)
Configure Dynamic ARP inspection (DAI) and Identity trusted ports
Disable trucking and DTP on access ports.
Configure DHCP Snooping and rate limit untrusted access ports.
Configure port security.
Secure unused ports.
Pre-requisite : DHCP snooping must be enabled
Explicitly configure trunk ports and change Native VLAN
To mitigate ARP attacks (Choose Two)
Secure unused ports
Disable tracking and DTP on access ports
Configure root guard
Prerequisite: DHCP snooping must be enabled
Configure dynamic ARP inspection (DAI) and identity trusted ports
Configure port security
Configure DHCP snooping and rate limit and trusted access ports
Social engineering
It's a malicious code that is attached to executable files
Replicate themselves by independently exploiting vulnerabilities in networks
It's a malware that carries out malicious operations under the guise the desired function
The attacker attempts to trick people to reveal secret information
To mitigate STP attacks (Choose Three)
Configure BPD guard
Explicitly configure trunk ports and change native VLAN
Configure root guard
Configure portFast
Configure port security
Configure DHCP snooping and rate limit and trusted access ports
Which of the following are examples of (something where you are) authentication factors? (Choose Two)
Retinal patterns
Password
IP address
ID card
Location
PIN
Finger prints
Key
Handprints
Which of the following are examples of (something you are) authentication factors? (Choose Three)
Retinal patterns
Password
IP address
ID card
Location
PIN
Finger prints
Key
Handprints
Which of the following are examples of (something you know) authentication factors? (Choose Two)
Retinal patterns
Password
IP address
ID card
Location
PIN
Finger prints
Key
Handprints
Which of the following are examples of (something you have) authentication factors? (Choose Two)
Retinal patterns
Password
IP address
ID card
Location
PIN
Finger prints
Key
Handprints
Which one of the following passwords is strong?
Fsas3alG
Dayorange
Mike
Elppa
To mitigate DHCP attacks
Explicitly configure trunk ports and change native VLAN
Secure unused ports
Configure DHCP snooping and rate limit and trusted access ports
Configure dynamic ARP inspection (DAI) and identity trusted ports
When TACACS+ is compared to RADIUS: (Choose Four)
TACACS+ uses TCP
TACACS+ is standard
TACACS+ encrypts entire packet
RADIUS is a standard
RADIUS uses UDP
Which of the following are components of AAA? (Choose 3)
Authentication
Accounting
Authorization
Administration
MAC filtering is a whitelist of MAC addresses that can connect
True
False
{"name":"العبيد نهائي", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Zone-based policy firewall uses three different zones. Which zone has a limited trust?, A new web server is to be deployed in a network using ZPF. In which Zone the new server could be deployed?, Zone based firewall divides the network into three security zones. Which zone is used for servers?","img":"https://www.quiz-maker.com/3012/CDN/94-4601615/screenshot-87.png?sz=1200"}
More Quizzes
Edebiyat
21100
OPB x The Bridge National Coming Out Day Quiz
840
Main
100
Mr.T Quizzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz
210
Think You're a Megan Mullally Expert? Free Trivia!
201035375
Appropriate Synonyms English: Boost Your Vocabulary!
201034394
Master Patient Positioning: Free Positioning Test
201036425
Think You Know NCAA Rules? Take the Free Compliance Test!
201055682
Signal Processing
15829959
Zodiac Compatibility Test: Discover Your Perfect Match
201028357
Free ESL Praxis Practice
201023397
Free Trig Identities
201027772