Sec Test 4
Which of these command sequences will send an email to holly@invalid.com using SMTP?
MAIL FROM:<david@invalid.com>
RCPT TO: <holly@invalid.com>
MESSAGE
MAIL FROM:<david@invalid.com>
RCPT TO: <holly@invalid.com>
DATA
HELO invalid.com MAIL
FROM : <david@invalid.com>
RCPT TO: <holly@invalid.com>
BODY
HELO invalid.com
MAIL TO: <holly@invalid.com>
MESSAGE END
Which two statements about the SeND protocol are true?
It counters neighbor discovery threats
It logs IPv6-related threats to an external log server
It supports numerous custom neighbor discovery messages
It supports an autoconfiguration mechanism
It uses IPsec as a baseline mechanism
It must be enabled before you can configure IPv6 addresses
Router (config) #crypto key zeroize public key-chain
Refer to the exhibit. Which effect of this command is true?
The current public key of the router is deleted from the cache when the router reboots, and the router generates a new one
The CA revokes the public key certificate of the router
The router sends a request to the CA to delete the router certificate from its configuration
The router immediately deletes its current public key from the cache and generates a new one
The public key of the remote peer is deleted from the router cache
Which statement about MDM with the Cisco ISE is true?
The MDM’s server certificate must be imported into the Cisco ISE Certificate Store before the MDM and ISE can establish a connection
MDM servers can generate custom ACLs for the Cisco ISE to apply to networks devices
The Cisco ISE supports limited built-in MDM functionality
The Cisco ISE supports a built-in list of MDM dictionary attributes it can use in authorization policies
When a mobile endpoint becomes compliant, the Cisco ISE records the updated device status in its internal database
If mobile endpoint fails posture compliance, both the user and the administrator are notified immediately
A server with IP address 209.165.202.150 is protected behind the inside interface of a Cisco ASA and the Internet on the outside Interface. Users on the Internet need to access the server at anytime, but the firewall administrator does not want to apply NAT to the address of the server because it is currently a public address. Which three of the following commands can be used to accomplish this ? ( Choose three)
Static (outside.inside) 209.165.202.150 209.165.202.150 netmask 255.255.255.255
access-list no-nat permit ip host 209.165.202.150 any
nat(inside) 0 access-list no-nat
Static (inside, outside) 209.165.202.150 209.165.202.150 netmask 255.255.255.255
Nat (inside) 1 209.165.202.150 255.255.255.255
Nonat-control
Nat(inside) 0 209.165.202.150 255.255.255.255
control-plane host
management-interface FastEthernet 0/0 allow ssh snmp
Refer to the exhibit. What is the effect of the given command?
It enables MPP on the FastEthernet 0/0 interface by enforcing rate-limiting for SSH and SNMP management traffic
It enables MPP on the FastEthernet 0/0 interface for SSH and SNMP management traffic and CoPP for all other protocols
It enables MPP on the FastEthernet 0/0 interface, allowing only SSH and SNMP management traffic
It enables QoS policing on the control plane of the FastEthernet 0/0 interface
It enables CoPP on the FastEthernet 0/0 interface for SSH and SNMP management traffic
Which three statements about VRF-Aware Cisco Firewall are true? (Choose three)
It supports both global and per-VRF commands and DoS parameters
It can generate syslog messages that are visible only to individual VPNs
It enables service providers to deploy firewalls on customer devices
It can run as more than one instance
It enables service providers to implement firewalls on PE devices
It can support VPN networks with overlapping address ranges without NAT
Which two statements about ICMP redirect messages are true? (Choose two)
They are generated by the host to inform the router of an alternate route to destination
The messages contain an ICMP Type 3 and ICMP code 7
Redirects are only punted to the CPU if the packets are also source-routed
By default. Configuring HSRP on the interface disables ICMP redirect functionality
They are generated when a packet enters and exits the same router interface
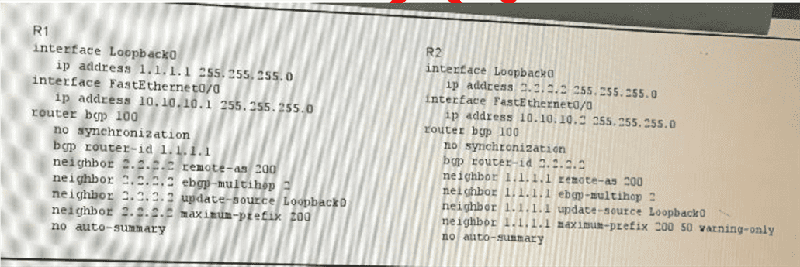
Refer to the exhibit. Which two effects of this configuration are true? (Choose two)
The BGP neighbor session tears down after R1 receives 100 prefixes from neighbor 1.1.1.1
The BGP neighbor session tears down after R1 receives 200 prefixes from neighbor 2.2.2.2
The BGP neighbor session between R1 and R2 re-establishes after 50 minutes
The BGP neighbor session between R1 and R2 re-establishes after 100 minutes
A warning message is displayed on R2 after it Receives 100 prefixes from neighbor 1.1.1.1
A warning message is displayed on R2 after it receives 50 prefixes
Which are the three scanning engines that the Cisco IronPort dynamic vectoring and streaming engine can use to protect against malware? (Choose three)
Symantec
McAfee
F-Secure
TrendMicro
Sophos
Webroot
Which are two features that help to mitigate man-in-the-middle attacks? (Choose two)
ARP Spoofing
ARP sniffing on specific ports
DHCP snooping
Destination MAC ACLs
Dynamic ARP inspection
What are three technologies that can be used to trace the source of an attack in a network environment with multiple exit/entry points? (Choose three)
Remotely-triggered destination-based black holing
ICMP Unreachable messages
Sinkholes
A honey pot
Traffic scrubbing
What IOS feature can prevent header attacks by using packet-header information to classify traffic ?
LLQ
TOS
FPM
CAR
TTL
Which two statements about the role-based access control are true? (Choose two)
Server profile administrators have read and write access to all system logs by default
The user profile on an AAA server is configured with the roles that grant user privileges
If the same user name is used for a local user account and a remote user account, the roles defined in the remote user account override the local user account
A view is created on the Cisco IOS device to leverage role-based access controls
Network administrator have read and write access to all system logs by default
What are two of the valid IPv6 extension headers? (Choose two)
Protocol
Options
Authentication Header
Next Header
Mobility
Hop Limit
Which three of these are properties of RC4? (Choose three)
It is used in AES
It is an asymmetric cipher
It is a stream cipher
It is a symmetric cipher
It is used is SSL
It is a block cipher
At are two important guidelines to follow when implementing VTP? (Choose two)
Enabling VTP pruning on a server will enable the feature for the entire management domain
When using secure mode VTP, only configure management domain passwords on VTP servers
All switches in the VTP domain must run the same version of VTP
Use of the VTP multi-domain feature should be restricted to migration and temporary implementation
CDP must be enabled on all switches in the VTP management domain
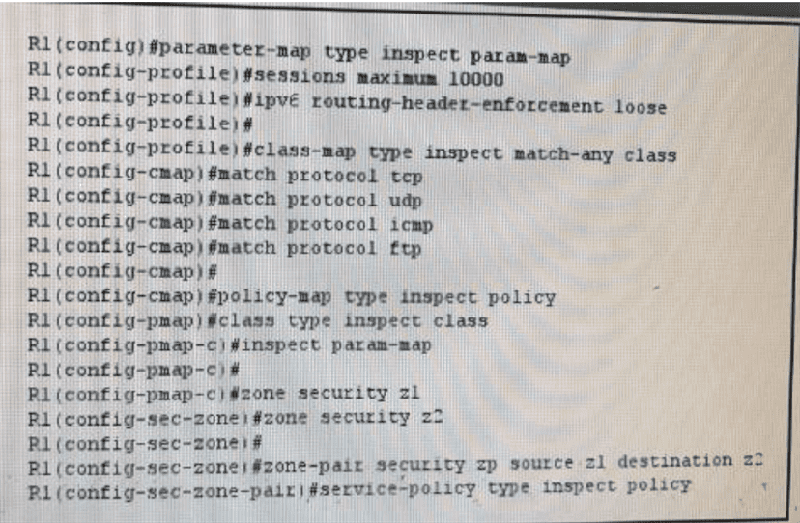
Refer to the exhibit, which two statements about the given IPv6 ZBF configuration are true? (Choose two)
It inspects TCP, UDP, ICMP, and FTP traffic from z1 to z2
T passes TCP, UDP, ICMP, and FTP traffic from z1 to z2
Inspects TCP, UDP, ICMP, and FTP from z2 to z1
It passes TCP, UDP, ICMP, and FTP traffic in both directions between z1 and z2
It provides backward compatibility with legacy IPv4 inspection
It provides backward compatibility with legacy IPv6 inspection
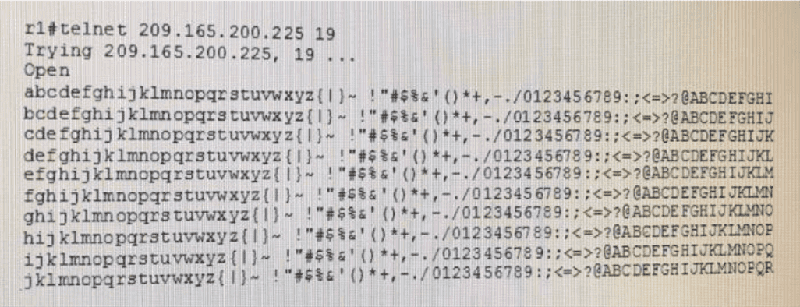
Exhibit which service or feature must be enabled on 209.165.200.255 produce the given output/
The finger service
A BOOTp server
A TCP small server
The PAD service
Which statement about the Cisco AMP Virtual Private Cloud Appliance is true for deployments in air-gape mode?
The appliance can perform disposition lookup against either the Protect DB or the AMP public cloud.
The appliance evaluates files against the threat intelligence and disposition information residing on the Update Host.
The Update Host automatically downloads updates and deploys them to the Protect DB on a daily basis.
The appliance can perform disposition lookups against the Protect DB without an Internet Connection.
The amp-sync tool syncs the threat-intelligence repository on the appliance directly with AMP public cloud.
What is an example of a stream cipher?
RC4
Blowfish
DES
RC5
Which two statements about the BGP TTL security check are true? (Choose two)
It is more useful for iBGP sessions than eBGP sessions.
The default TTL for all neighbor session packets is 255 when eBGP is configured.
It secures incoming eBGP session only
It Protects the BGP process from DOS attacks
It enforces each BGP packet’s maximum TTL value
Which two statements about Cisco ASA authentication using LDAP are true? (Choose two)
It uses attribute maps to map the AD memberOf attribute to the cisco ASA Group-Poilcy attribute
It uses AD attribute maps to assign users to group policies configured under the WebVPN context
The Cisco ASA can use more than one AD memberOf attribute to match a user to multiple group policies
It can assign a group policy to a user based on access credentials
It can combine AD attributes and LDP attributes to configure group policies on the Cisco ASA
It is a closed standard that manages directory-information services over distributed networks
Which three statements about SCEP are true?(Choose three)
It Supports online certification revocation.
Cryptographically signed and encrypted message are conveyed using PKCS#7.
The certificate request format uses PKCS#10.
It supports multiple cryptographic algorithms, including RSA.
CRL retrieval is support through CDP (Certificate Distribution Point) queries.
It supports Synchronous granting.
What are three features that are enabled by generating change of Authorization (CoA) requests in a push model?(Choose three)
Host termination
Mac identification
Session identification
Session termination
Host reauthentication
Session reauthentication
Which three statements about the keying methods used by MACSec are true? (Choose three.)
Key management for host-to-switch and switch-to-switch MACSec sessions is provided by MKA.
A valid mode for SAP is NULL.
MKA is implemented as an EAPoL packet exchange.
SAP is enabled by default for Cisco TrustSec in manual configuration mode.
SAP is not supported on switch SVIs.
SAP is supported on SPAN destination ports.
What is the purpose of the BGP TTL security check?
The BGP TTL security check is used for iBGP session.
The BGP TTL security check protects against CPU utilization-based attacks.
The BGP TTL security check checks for a TTL value in packet header of less than or equal to for successful peering.
The BGP TTL security check authenticates a peer.
The BGP TTL security check protects against routing table corruption.
RTR-A (config-if)# ipv6 mld report-link-local-group
Refer to the exhibit. Which effect of this configuration is true?
It enables the host to send MLD report messages for nonlink Local groups
It enables hosts to send MLD report messages for group in 224.0.0.0/24
It configures the node to generate a link-local group report when it joins the solicited-node multicast group
It enables MLD query messages for all link-local groups
It enables local group membership for MLDv1 and MLDv2.
On a Cisco Wireless LAN Controller (WLC), which web policy enables failed Layer 2 authentication to fall back to WebAuth authentication with a user name and password?
On MAC Filter Failure
Authentication
Splash Page Web Redirect
Conditional Web Redirect
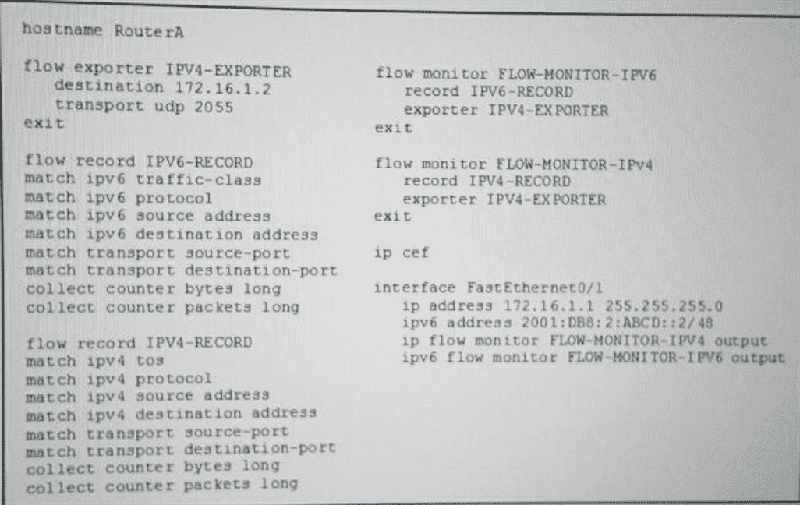
Refer to the exhibit. Flexible NetFlow is failing to export IPv6 flow records from RouterA to your flow collector. What action can you take to allow the IPv6 flow records to be sent to the collector?
Configure the output-features command for the IPV4-EXPORTER
ADD the ipv6 cef command to the configuration
Set the Netflow export protocol to v5
Create a new flow exporter with an IPv6 destination and apply it to the flow monitor.
Remove the ip cef command from the configuration
Which two statements about MACsec are true? (Choose two)
It maintains network intelligence as it applied to router uplinks and downlinks.
It works in conjunction with IEEE 802.1X -2010 port-based access control.
It uses symmetric-key encryption to protect data confidentiality.
It encrypts packets at Layer 3, which allows devices to handle packets in accordance with network polices.
It can be enabled on individual port at Layer 3 to allow MACsec devices to access the network.
It can use IEEE 802.1x master keys to encrypt wired and wireless links
What are three pieces of data you should review in response to a suspected SSL MITM attack? (Choose three)
The IP address of the SSL server
The MAC address of the attacker
The MAC address of the SSL server
The X.509 certificate of the SSL server
The DNS name of the SSL server
The X.509 certificate the of attacker
{"name":"Sec Test 4", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Which of these command sequences will send an email to holly@invalid.com using SMTP?, Which two statements about the SeND protocol are true?, Router (config) #crypto key zeroize public key-chain Refer to the exhibit. Which effect of this command is true?","img":"https://cdn.poll-maker.com/25-959540/screen-shot-2018-01-19-at-9-34-21-am.png?sz=1200"}
More Quizzes
Mennyit tudsz Márai Sándorról?
520
Teste - Wemap Quizz
1589
What type of gamer am I?
320
Alimentos
1267
Free Housing Affordability: Test Your Knowledge
201028204
The Outsiders First Chapter: Test Your Knowledge!
201045014
Discourse in STEM Classrooms
15825354
Free Love Language Test for Couples - Discover Your Match
201029782
Social Sci of Human Movement
15830474
Do I Have a Shopping Addiction? Free to Find Out!
201030474
Think You Love Yourself? Take Our Do I Love Myself!
201027080
Which City Should You Live In? Take This Personality
201030474