CS0-003 Study Test 4
The Chief Information Officer (CIO) for a large manufacturing organization has noticed a significant number of unknown devices with possible malware infections are on the organization's corporate network.
Which of the following would work BEST to prevent the issue?
Reconfigure the NAC solution to prevent access based on a full device profile and ensure antivirus is installed.
Segment the network to isolate all systems that contain highly sensitive information, such as intellectual property.
Implement certificate validation on the VPN to ensure only employees with the certificate can access the company network.
Update the antivirus configuration to enable behavioral and real-time analysis on all systems within the network.
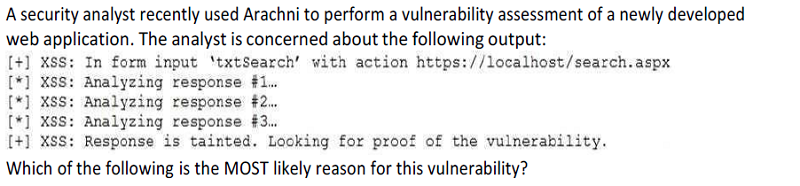
The developer set input validation protection on the specific field of search.aspx.
The developer did not set proper cross-site scripting protections in the header.
The developer did not implement default protections in the web application build.
The developer did not set proper cross-site request forgery protections.
An information security analyst discovered a virtual machine server was compromised by an attacker. Which of the following should be the FIRST step to confirm and respond to the incident?
Pause the virtual machine.
Shut down the virtual machine.
Take a snapshot of the virtual machine.
Remove the NIC from the virtual machine.
The threat intelligence department recently learned of an advanced persistent threat that is leveraging a new strain of malware, exploiting a system router. The company currently uses the same device mentioned in the threat report.
Which of the following configuration changes would BEST improve the organization’s security posture?
Implement an IPS rule that contains content for the malware variant and patch the routers to protect against the vulnerability
Implement an IDS rule that contains the IP addresses from the advanced persistent threat and patch the routers to protect against the vulnerability
Implement an IPS rule that contains the IP addresses from the advanced persistent threat and patch the routers to protect against the vulnerability
Implement an IDS rule that contains content for the malware variant and patch the routers to protect against the vulnerability
SIMULATION
Malware is suspected on a server in the environment.
The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware.
Malware is suspected on a server in the environment.
The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware.
INSTRUCTIONS
Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware.
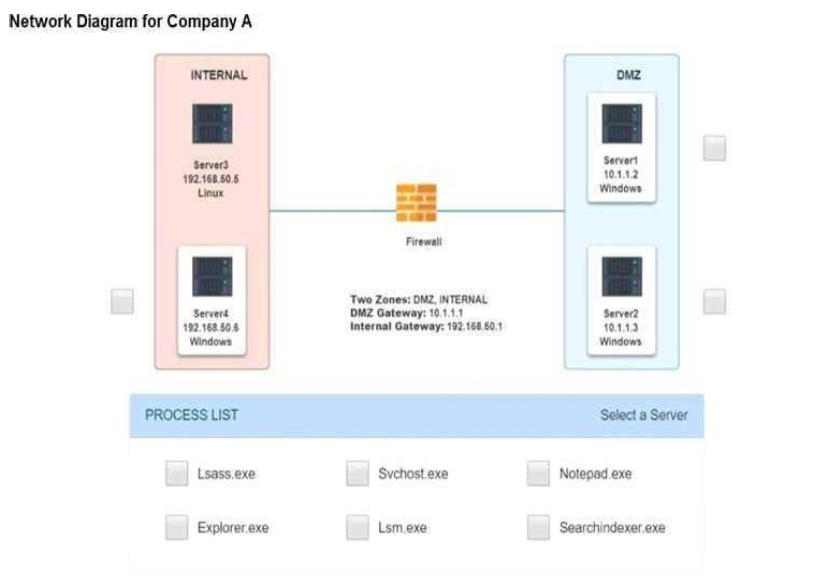
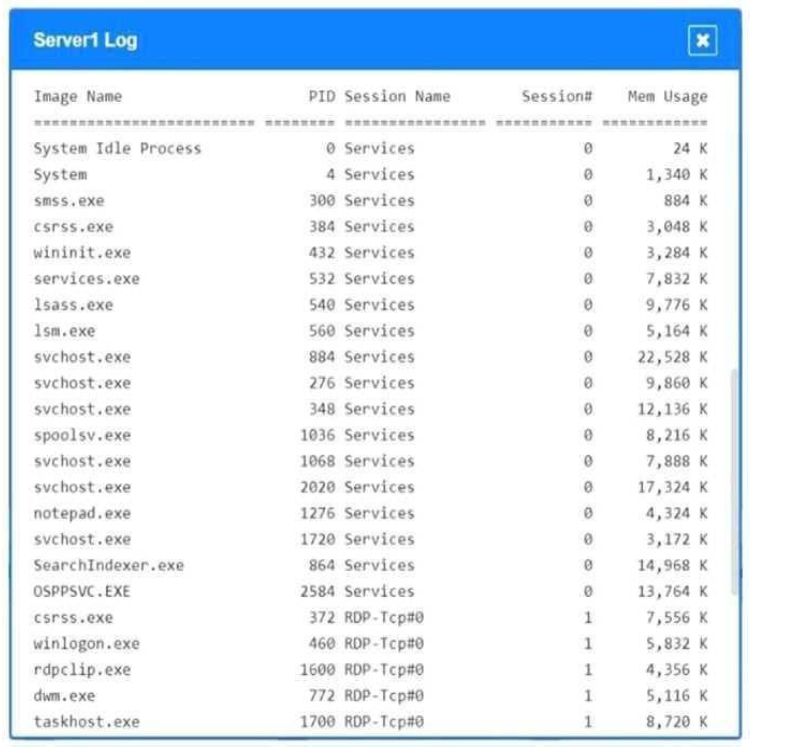
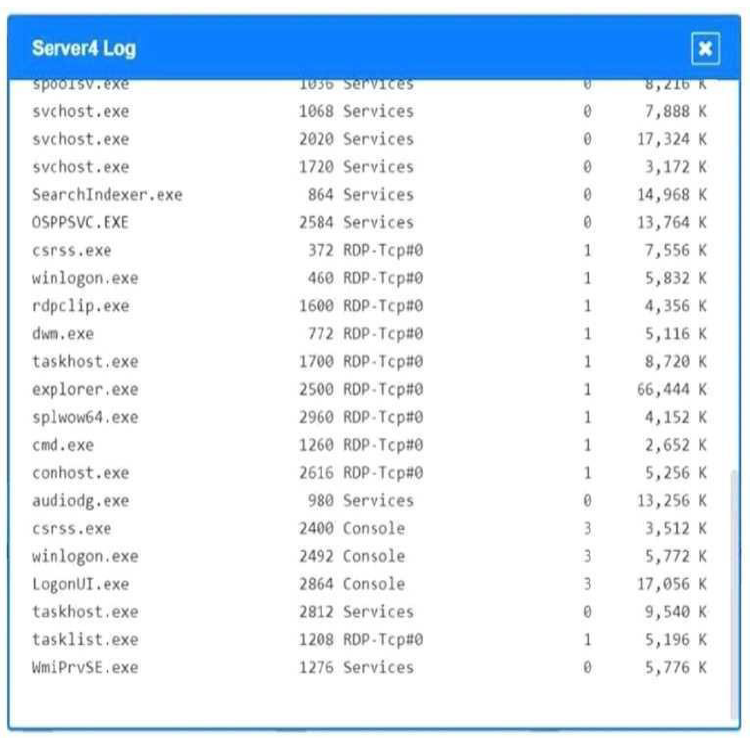
Server 4, svchost.exe
A company’s senior human resources administrator left for another position, and the assistant administrator was promoted into the senior position. On the official start day, the new senior administrator planned to ask for extended access permissions but noticed the permissions were automatically granted on that day. Which of the following describes the access management policy in place at the company?
Mandatory-based
Host-based
Federated access
Role-based
A threat intelligence analyst has received multiple reports that are suspected to be about the same advanced persistent threat. To which of the following steps in the intelligence cycle would this map?
Dissemination
Analysis
Feedback
Requirements
Collection
During an incident investigation, a security analyst acquired a malicious file that was used as a backdoor but was not detected by the antivirus application. After performing a reverse-engineering procedure, the analyst found that part of the code was obfuscated to avoid signature detection. Which of the following types of instructions should the analyst use to understand how the malware was obfuscated and to help deobfuscate it?
MOV
ADD
XOR
SUB
MOVL
A large organization wants to move account registration services to the cloud to benefit from faster processing and elasticity. Which of the following should be done FIRST to determine the potential risk to the organization?
Establish a recovery time objective and a recovery point objective for the systems being moved
Calculate the resource requirements for moving the systems to the cloud
Determine recovery priorities for the assets being moved to the cloud-based systems
Identify the business processes that will be migrated and the criticality of each one
Perform an inventory of the servers that will be moving and assign priority to each one
A security analyst is required to stay current with the most recent threat data and intelligence reports. When gathering data, it is MOST important for the data to be:
Proprietary and timely
Proprietary and accurate
Relevant and deep
Relevant and accurate
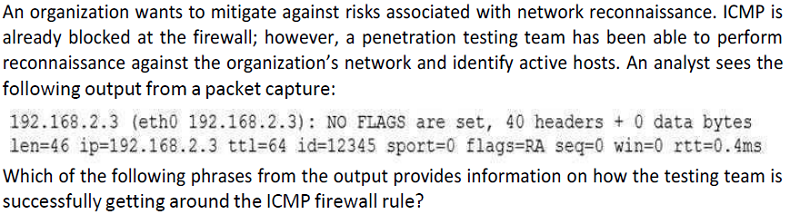
Flags=RA indicates the testing team is using a Christmas tree attack
Ttl=64 indicates the testing team is setting the time to live below the firewall’s threshold
0 data bytes indicates the testing team is crafting empty ICMP packets
NO FLAGS are set indicates the testing team is using hping
The Chief Information Officer (CIO) of a large healthcare institution is concerned about all machines having direct access to sensitive patient information. Which of the following should the security analyst implement to BEST mitigate the risk of sensitive data exposure?
A cloud access service broker system
NAC to ensure minimum standards are met
MFA on all workstations
Network segmentation
A company is moving from the use of web servers hosted in an internal datacenter to a containerized cloud platform. An analyst has been asked to identify indicators of compromise in the containerized environment. Which of the following would BEST indicate a running container has been compromised?
A container from an approved software image has drifted
An approved software orchestration container is running with root privileges
A container from an approved software image has stopped responding
A container from an approved software image fails to start
A company’s data is still being exfiltered to business competitors after the implementation of a DLP solution. Which of the following is the most likely reason why the data is still being compromised?
Printed reports from the database contain sensitive information
DRM must be implemented with the DLP solution
Users are not labeling the appropriate data sets
DLP solutions are only effective when they are implemented with disk encryption
A company has contracted with a software development vendor to design a web portal for customers to access a medical records database. Which of the following should the security analyst recommend to BEST control the unauthorized disclosure of sensitive data when sharing the development database with the vendor?
Establish an NDA with the vendor.
Enable data masking of sensitive data tables in the database.
Set all database tables to read only.
Use a de-identified data process for the development database.
A general contractor has a list of contract documents containing critical business data that are stored at a public cloud provider. The organization’s security analyst recently reviewed some of the storage containers and discovered most of the containers are not encrypted. Which of the following configurations will provide the MOST security to resolve the vulnerability?
Upgrading TLS 1.2 connections to TLS 1.3
Implementing AES-256 encryption on the containers
Enabling SHA-256 hashing on the containers
Implementing the Triple Data Encryption Algorithm at the file level
Which of the following threat classifications would MOST likely use polymorphic code?
Known threat
Zero-day threat
Unknown threat
Advanced persistent threat
An organization has been seeing increased levels of malicious traffic. A security analyst wants to take a more proactive approach to identify the threats that are acting against the organization’s network. Which of the following approaches should the security analyst recommend?
Use the MITRE ATT&CK framework to develop threat models.
Conduct internal threat research and establish indicators of compromise.
Review the perimeter firewall rules to ensure rule-set accuracy.
Use SCAP scans to monitor for configuration changes on the network.
A company’s change management team has asked a security analyst to review a potential change to the email server before it is released into production. The analyst reviews the following change request:
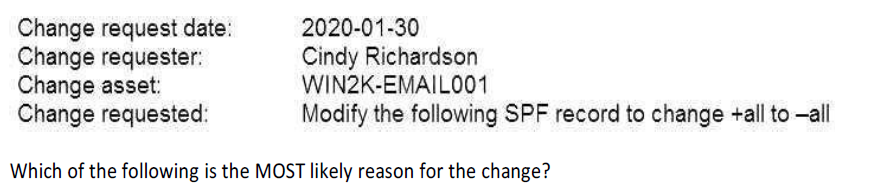
To reject email from servers that are not listed in the SPF record
To reject email from email addresses that are not digitally signed
To accept email to the company’s domain
To reject email from users who are not authenticated to the network
A software development team asked a security analyst to review some code for security vulnerabilities. Which of the following would BEST assist the security analyst while performing this task?
Static analysis
Dynamic analysis
Regression testing
User acceptance testing
The management team assigned the following values to an inadvertent breach of privacy regulations during the original risk assessment:
Probability = 25%
Magnitude = $1,015 per record Total records = 10,000
Two breaches occurred during the fiscal year. The first compromised 35 records, and the second compromised 65 records. Which of the following is the value of the records that were compromised?
Probability = 25%
Magnitude = $1,015 per record Total records = 10,000
Two breaches occurred during the fiscal year. The first compromised 35 records, and the second compromised 65 records. Which of the following is the value of the records that were compromised?
$10,150
$25,375
$101,500
$2,537,500
An analyst has received a notification about potential malicious activity against a web server. The analyst logs in to a central log collection server and runs the following command: “cat access.log.1 | grep “union”. The output shown below appears:
<68.71.54.117> – – [31/Jan/2020:10:02:31 –0400] “Get /cgi-bin/backend1.sh?id=%20union%20select%20192.168.60.50 HTTP/1.1”
Which of the following attacks has occurred on the server?
Cross-site request forgery
SQL injection
Cross-site scripting
Directory traversal
A security analyst has discovered malware is spreading across multiple critical systems and is originating from a single workstations, which belongs to a member of the cyber-infrastructure team who has legitimate administrator credentials. An analysis of the traffic indicates the workstation swept the networking looking for vulnerable hosts to infect. Which of the following would have worked BEST to prevent the spread of this infection?
Vulnerability scans of the network and proper patching.
A properly configured and updated EDR solution.
A honeypot used to catalog the anomalous behavior and update the IPS.
Logical network segmentation and the use of jump boxes.
A Chief Executive Officer (CEO) is concerned about the company’s intellectual property being leaked to competitors. The security team performed an extensive review but did not find any indication of an outside breach. The data sets are currently encrypted using the Triple Data Encryption Algorithm. Which of the following courses of action is appropriate?
Limit all access to the sensitive data based on geographic access requirements with strict role- based access controls.
Enable data masking and reencrypt the data sets using AES-256.
Ensure the data is correctly classified and labeled, and that DLP rules are appropriate to prevent disclosure.
Use data tokenization on sensitive fields, reencrypt the data sets using AES-256, and then create an MD5 hash.
A company’s Chief Information Security Officer (CISO) published an Internet usage policy that prohibits employees from accessing unauthorized websites. The IT department whitelisted websites used for business needs. The CISO wants the security analyst to recommend a solution that would improve security and support employee morale. Which of the following security recommendations would allow employees to browse non-business-related websites?
Implement a virtual machine alternative.
Develop a new secured browser.
Configure a personal business VLAN.
Install kiosks throughout the building.
In web application scanning, static analysis refers to scanning:
The system for vulnerabilities before installing the application.
The compiled code of the application to detect possible issues.
An application that is installed and active on a system.
An application that is installed on a system that is assigned a static IP.
An organization has the following risk mitigation policy:
Risks with a probability of 95% or greater will be addressed before all others regardless of the impact.
All other prioritization will be based on risk value. The organization has identified the following risks:
All other prioritization will be based on risk value. The organization has identified the following risks:
326

A, B, D, C
A, B, C, D
D, A, B, C
D, A, C, B
DNSSEC
DMARC
STP
S/IMAP
A small business does not have enough staff in the accounting department to segregate duties. The controller writes the checks for the business and reconciles them against the ledger. To ensure there is no fraud occurring, the business conducts quarterly reviews in which a different officer in the business compares all the cleared checks against the ledger.
Which of the following BEST describes this type of control?
Deterrent
Preventive
Compensating
Detective
A security analyst is performing a Diamond Model analysis of an incident the company had last quarter. A potential benefit of this activity is that it can identify:
Detection and prevention capabilities to improve
Which systems were exploited more frequently
Possible evidence that is missing during forensic analysis
Which analysts require more training
The time spent by analysts on each of the incidents
Industry partners from critical infrastructure organizations were victims of attacks on their SCADA devices. The attacks used privilege escalation to gain access to SCADA administration and access management solutions would help to mitigate this risk?
Multifactor authentication
Manual access reviews
Endpoint detection and response
Role-based access control
Which of the following incident response components can identify who is the liaison between multiple lines of business and the pubic?
Red-team analysis
Escalation process and procedures
Triage and analysis
Communications plan
A security analyst identified one server that was compromised and used as a data making machine, and a few of the hard drive that was created. Which of the following will MOST likely provide information about when and how the machine was compromised and where the malware is located?
System timeline reconstruction
System registry extraction
Data carving
Volatile memory analysts
Which of the following is the BEST way to gather patch information on a specific server?
Event Viewer
Custom script
SCAP software
CI/CD
After a series of Group Policy Object updates, multiple services stopped functioning. The systems administrator believes the issue resulted from a Group Policy Object update but cannot validate which update caused the Issue. Which of the following security solutions would resolve this issue?
Privilege management
Group Policy Object management
Change management
Asset management
A business recently acquired a software company. The software company's security posture is unknown. However, based on an assessment, there are limited security controls. No significant security monitoring exists. Which of the following is the NEXT step that should be completed to obtain information about the software company's security posture?
Develop an asset inventory to determine the systems within the software company
Review relevant network drawings, diagrams and documentation
Perform penetration tests against the software company's Internal and external networks
Baseline the software company's network to determine the ports and protocols in use
An organization is developing software to match customers' expectations. Before the software goes into production, it must meet the following quality assurance guidelines
• Uncover all the software vulnerabilities.
• Safeguard the interest of the software's end users.
• Reduce the likelihood that a defective program will enter production.
• Preserve the Interests of me software producer.
• Uncover all the software vulnerabilities.
• Safeguard the interest of the software's end users.
• Reduce the likelihood that a defective program will enter production.
• Preserve the Interests of me software producer.
Which of me following should be performed FIRST?
Run source code against the latest OWASP vulnerabilities
Document the life-cycle changes that look place
Ensure verification and vacation took place during each phase
Store the source code in a software escrow
Conduct a static analysis of the code
A security analyst identified some potentially malicious processes after capturing the contents of memory from a machine during incident response. Which of the following procedures is the NEXT step for further in investigation?
Data carving
Timeline construction
File cloning
Reverse engineering
A company has a cluster of web servers that is critical to the business. A systems administrator installed a utility to troubleshoot an issue, and the utility caused the entire cluster to 90 offline. Which of the following solutions would work BEST prevent to this from happening again?
Change management
Application whitelisting
Asset management
Privilege management

Proxy server
SQL server
Windows domain controller
WAF appliance
DNS server
Which of the following organizational initiatives would be MOST impacted by data severity issues?
Moving to a cloud-based environment
Migrating to locally hosted virtual servers
Implementing non-repudiation controls
Encrypting local database queries
A company wants to ensure confidential data from its storage media files is sanitized so the drives cannot oe reused. Which of the following is the BEST approach?
Degaussing
Shreoding
Formatting
Encrypting
White reviewing incident reports from the previous night, a security analyst notices the corporate websites were defaced with po mcai propaganda.
Which of the following BEST Describes this type of actor?
Hacktivist
Nation-state
Insider threat
Organized crime
The IT department is concerned about the possibility of a guest device infecting machines on the corporate network or taking down the company's singe internet connection. Which of the following should a security analyst recommend to BEST meet the requirements outlined by the IT Department?
Require the guest machines to install the corporate-owned EDR solution.
Configure NAC to only alow machines on the network that are patched and have active antivirus.
Place a firewall In between the corporate network and the guest network.
Configure the IPS with rules that will detect common malware signatures traveling from the guest network.
A team of network security analysts is examining network traffic to determine if sensitive data was exfitrated. Upon further investigation, the analysts believe confidential data was compromised.
Which of me following capabilities would BEST defend against this type of sensitive data eifiitration?
Deploy an edge firewall
Implement DLP
Deploy EDR
Encrypt the hard drives
A development team has asked users to conduct testing to ensure an application meets the needs of the business. Which of the following types of testing docs this describe?
Acceptance testing
Stress testing
Regression testing
Penetration testing
As part of an Intelligence feed, a security analyst receives a report from a third-party trusted source. Within the report are several detrains and reputational information that suggest the company's employees may be targeted for a phishing campaign. Which of the following configuration changes would be the MOST appropriate for Mergence gathering?
Update the whitelist
Develop a malware signature
Sinkhole the domains
Update the Blacklist
An organization recently discovered that spreadsheet files containing sensitive financial data were improperly stored on a web server. The management team wants to find out if any of these files were downloaded by pubic users accessing the server. The results should be written to a text file and should induce the date. time, and IP address associated with any spreadsheet downloads. The web server's log file Is named webserver log, and the report We name should be accessreport.txt. Following is a sample of the web servefs.log file:
2017-0-12 21:01:12 GET /index.htlm - @4..102.33.7 - return=200 1622
Which of the following commands should be run if an analyst only wants to include entries in which spreadsheet was successfully downloaded?
More webserver.log | grep * xIs > accessreport.txt
More webserver.log > grep ''xIs > egrep -E 'success' > accessreport.txt
More webserver.log | grep ' -E ''return=200 | accessreport.txt
More webserver.log | grep -A *.xIs < accessreport.txt
Which of the following describes the mam difference between supervised and unsupervised machine-learning algorithms that are used in cybersecurity applications?
Supervised algorithms can be used to block attacks, while unsupervised algorithms cannot.
Supervised algorithms require security analyst feedback, while unsupervised algorithms do not.
Unsupervised algorithms are not suitable for IDS systems, white supervised algorithms are.
Unsupervised algorithms produce more false positives. Than supervised algorithms.
A company is experiencing a malware attack within its network. A security engineer notices many of the impacted assets are connecting outbound to a number of remote destinations and exfiltrating data. The security engineer also see that deployed, up-to-date antivirus signatures are ineffective.
Which of the following is the BEST approach to prevent any impact to the company from similar attacks in the future?
IDS signatures
Data loss prevention
Port security
Sinkholeing
After a remote command execution incident occurred on a web server, a security analyst found the following piece of code in an XML file:
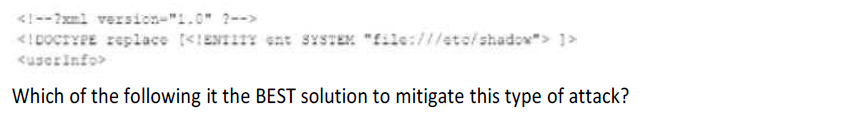
Implement a better level of user input filters and content sanitization.
Property configure XML handlers so they do not process sent parameters coming from user inputs.
Use parameterized Queries to avoid user inputs horn being processed by the server.
Escape user inputs using character encoding conjoined with whitelisting.
A routine vulnerability scan detected a known vulnerability in a critical enterprise web application. Which of the following would be the BEST next step?
Submit a change request to have the system patched
Evaluate the risk and criticality to determine it further action is necessary
Notify a manager of the breach and initiate emergency procedures
Remove the application from production and Inform the users
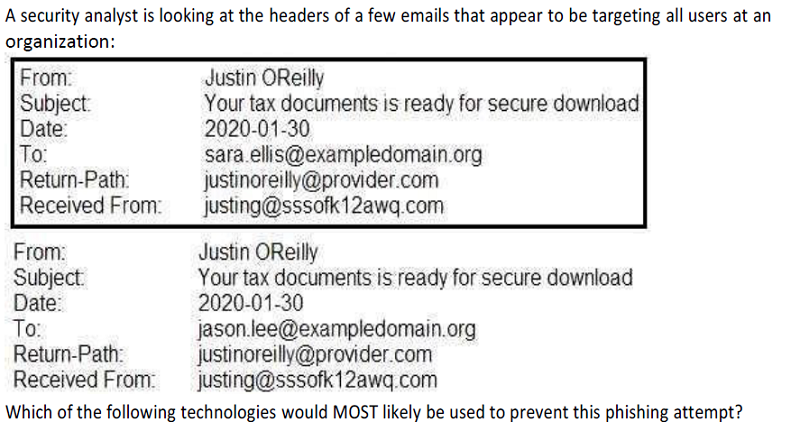
The Chief information Officer of a large cloud software vendor reports that many employees are falling victim to phishing emails because they appear to come from other employees. Which of the following would BEST prevent this issue
Induce digital signatures on messages originating within the company
Require users authenticate to the SMTP server
Implement DKIM to perform authentication that will prevent this Issue
Set up an email analysis solution that looks for known malicious Iinks within the email
A financial organization has offices located globally. Per the organization’s policies and procedures, all executives who conduct Business overseas must have their mobile devices checked for malicious software or evidence of tempering upon their return. The information security department oversees the process, and no executive has had a device compromised. The Chief information Security Officer wants to Implement an additional safeguard to protect the organization's data.
Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
Implement a mobile device wiping solution for use if a device is lost or stolen
Install a DLP solution to track data now
Install an encryption solution on all mobile devices
Train employees to report a lost or stolen laptop to the security department immediately
In response to an audit finding, a company's Chief information Officer (CIO) instructed the security department to Increase the security posture of the vulnerability management program. Currency, the company's vulnerability management program has the following attributes: Which of the following would BEST Increase the security posture of the vulnerably management program?
Expand the ports Being scanned lo Include al ports increase the scan interval to a number the business win accept without causing service interruption. Enable authentication and perform credentialed scans.
Expand the ports being scanned to Include all ports. Keep the scan interval at its current level Enable authentication and perform credentialed scans.
Expand the ports being scanned to Include at ports increase the scan interval to a number the business will accept without causing service Interruption. Continue unauthenticated scans.
Continue scanning the well-known ports increase the scan interval to a number the business will accept without causing service Interruption. Enable authentication and perform credentialed scans.
A security analyst is scanning the network to determine if a critical security patch was applied to all systems in an enterprise. The Organization has a very low tolerance for risk when it comes to resource availability. Which of the following is the BEST approach for configuring and scheduling the scan?
Make sure the scan is credentialed, covers at hosts in the patch management system, and is scheduled during business hours so it can be terminated if it affects business operations.
Make sure the scan is uncredentialed, covers at hosts in the patch management system, and Is scheduled during of business hours so it has the least impact on operations.
Make sure the scan is credentialed, has the latest software and signature versions, covers all external hosts in the patch management system and is scheduled during off-business hours so it has the least impact on operations.
Make sure the scan is credentialed, uses a ironed plug-in set, scans all host IP addresses in the enterprise, and is scheduled during off-business hours so it has the least impact on operations.
An analyst receives artifacts from a recent Intrusion and is able to pull a domain, IP address, email address, and software version. When of the following points of the Diamond Model of Intrusion Analysis does this intelligence represent?
Infrastructure
Capabilities
Adversary
Victims
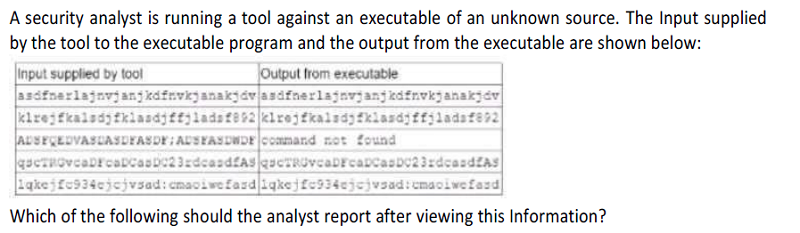
A dynamic library that is needed by the executable a missing
Input can be crafted to trigger an Infection attack in the executable
The toot caused a buffer overflow in the executable's memory
The executable attempted to execute a malicious command
After examine a header and footer file, a security analyst begins reconstructing files by scanning the raw data bytes of a hard disk and rebuilding them. Which of the following techniques is the analyst using?
Header analysis
File carving
Metadata analysis
Data recovery
Which of following allows Secure Boot to be enabled?
EFuse
UEFI
MSM
PAM
A security analyst is researching ways to improve the security of a company's email system to mitigate emails that are impersonating company executives. Which of the following would be BEST for the analyst to configure to achieve this objective?
A TXT record on the name server for SPF
DNSSEC keys to secure replication
Domain Keys identified Man
A sandbox to check incoming mad
A company stores all of its data in the cloud. All company-owned laptops are currently unmanaged, and all users have administrative rights. The security team is having difficulty identifying a way to secure the environment. Which of the following would be the BEST method to protect the company's data?
Implement UEM on an systems and deploy security software
Implement DLP on all workstations and block company data from being sent outside the company
Implement a CASB and prevent certain types of data from being downloaded to a workstation
Implement centralized monitoring and logging for an company systems
Which of me following are reasons why consumer IoT devices should be avoided in an enterprise environment? (Select TWO)
Message queuing telemetry transport does not support encryption.
The devices may have weak or known passwords.
The devices may cause a dramatic Increase in wireless network traffic.
The devices may utilize unsecure network protocols.
Multiple devices may interface with the functions of other loT devices.
The devices are not compatible with TLS 12.
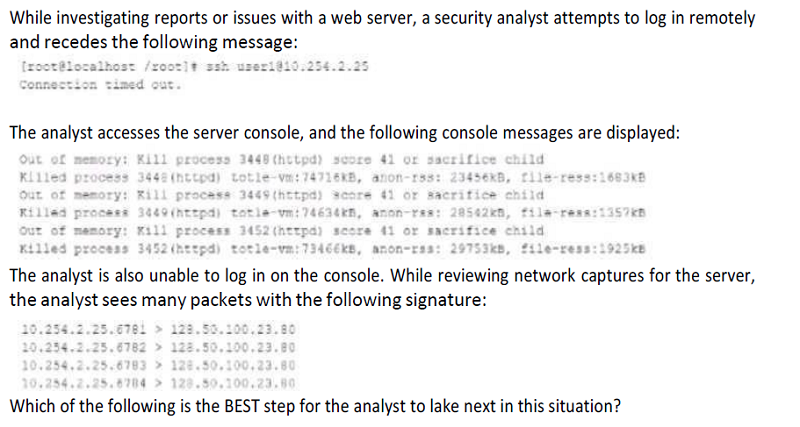
Load the network captures into a protocol analyzer to further investigate the communication with 128.30.100.23, as this may be a botnet command server
After ensuring network captures from the server are saved isolate the server from the network take a memory snapshot, reboot and log in to do further analysis.
Corporate data is being exfilltrated from the server Reboot the server and log in to see if it contains any sensitive data.
Cryptomining malware is running on the server and utilizing an CPU and memory. Reboot the server and disable any cron Jobs or startup scripts that start the mining software.
A company recently experienced a breach of sensitive information that affects customers across multiple geographical regions. Which of the following roles would be BEST suited to determine the breach notification requirements?
Legal counsel
Chief Security Officer
Human resources
Law enforcement
A security analyst is handling an incident in which ransomware has encrypted the disks of several company workstations. Which of the following would work BEST to prevent this type of Incident in the future?
Implement a UTM instead of a stateful firewall and enable gateway antivirus.
Back up the workstations to facilitate recovery and create a gold Image.
Establish a ransomware awareness program and implement secure and verifiable backups.
Virtualize all the endpoints with dairy snapshots of the virtual machines.
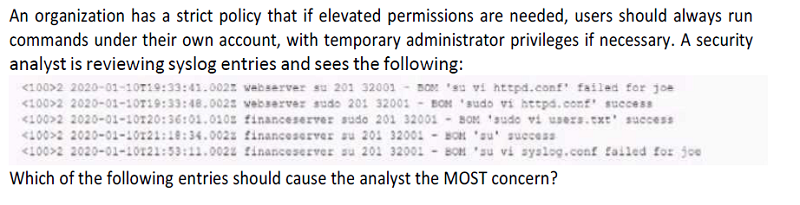
<100>2 2020-01-10T19:33:41.003z webserver su 201 32001 = BOM ' su vi httpd.conf' failed for joe
<100>2 2020-01-10T20:36:36.0010z financeserver su 201 32001 = BOM ' sudo vi users.txt success
<100> 2020-01-10T19:33:48.003z webserver sudo 201 32001 = BOM ' su vi syslog.conf failed for joe
<100> 2020-01-10T19:34..003z financeserver su 201 32001 = BOM ' su vi success
<100> 2020-01-10T19:33:48.003z webserver sudo 201 32001 = BOM ' su vi httpd.conf' success

Patch or reimage the device to complete the recovery
Restart the antiviruses running processes
Isolate the host from the network to prevent exposure
Confirm the workstation's signatures against the most current signatures
A computer hardware manufacturer developing a new SoC that will be used by mobile devices. The SoC should not allow users or the process to downgrade from a newer firmware to an older one. Which of the following can the hardware manufacturer implement to prevent firmware downgrades?
Encryption
EFuse
Secure Enclave
Trusted execution
A small organization has proprietary software that is used internally. The system has not been wen maintained and cannot be updated with the rest or the environment. Which of the following is the BEST solution?
Virtualize the system and decommission the physical machine
Remove it from the network and require air gapping
Implement privileged access management for identity access
Implement MFA on the specific system
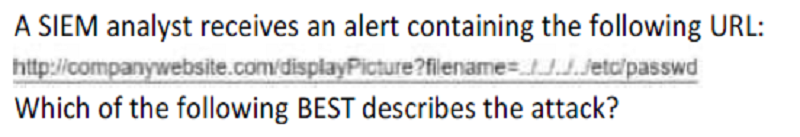
Password spraying
Buffer overflow
Insecure object access
Directory traversal
An organization is focused on restructuring its data governance programs and an analyst has been Tasked with surveying sensitive data within the organization. Which of the following is the MOST accurate method for the security analyst to complete this assignment?
Perform an enterprise-wide discovery scan.
Consult with an internal data custodian.
Review enterprise-wide asset Inventory.
Create a survey and distribute it to data owners.
During an incident response procedure, a security analyst collects a hard drive to analyze a possible vector of compromise. There is a Linux swap partition on the hard drive that needs to be checked. Which of the following, should the analyst use to extract human-readable content from the partition?
Strings
Head
Fsstat
Dd
{"name":"CS0-003 Study Test 4", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"The Chief Information Officer (CIO) for a large manufacturing organization has noticed a significant number of unknown devices with possible malware infections are on the organization's corporate network. Which of the following would work BEST to prevent the issue?, An information security analyst discovered a virtual machine server was compromised by an attacker. Which of the following should be the FIRST step to confirm and respond to the incident?","img":"https://www.quiz-maker.com/3012/CDN/97-4795700/301.png?sz=1200"}
More Quizzes
SSC / TK Readiness test
13610
Reaction Types
5241
How well do you know me?
1368
Which Dragon Age Inquisition Character Are You?
6362
Godfather Actors - How Well Do You Know the Cast?
201034415
English 9 Final Exam - Free Grade 9 Practice
201024110
IC3 Spark Key Applications Practice Test - Free
201020740
Advertising: Test Your Ad Knowledge Free Online
201027376
Medical Prefix: Acro- Meaning & Practice
201026637
Addition - Free Basic Math Practice Online
201028445
Percent Yield - Free Actual & Theoretical Practice
201036289
Leadership & Ethics - Free Interactive Practice
15819465