Weblogic 12c AA II

WebLogic 12c Admin Quiz
Test your knowledge and skills in WebLogic Server 12c with our comprehensive quiz designed for system administrators and Java Enterprise Edition developers.
Features:
- 30 detailed questions covering various aspects of WebLogic Server.
- Immediate feedback on your answers.
- Improve your understanding of JMS, SSL, Coherence, and more!
You are reviewing the scheduled maintenance of your domain after adding a new cluster. Which statement is true when configuring a migratable target within a WebLogic Server cluster? (Choose the best answer.)
A. Allow Post-Migration Script To Run On a Different Machine is selected by default.
B. The default server migration policy is Auto-Migrate Exactly-once Services.
C. The participating cluster should include at least one configured server.
D. An automatically migrated service will always be hosted on the specified User Preferred Server.
Which statement is correct regarding JMS Template configuration? (Choose the best answer.)
A. Message Priority defined for the Template configuration overrides that specified by the producer.
B. Message Expiration Policy cannot be set on the template and needs to be configured for actual destinations that reference the template.
C. JMS Template configuration must include the quota associated with the template.
D. JMS Template configuration must include the message sort order associated with the template.
Your application has an auditing requirement that says that all audit events that have a severity of FAILURE must be logged and a notification must be sent to the application’s monitoring tier. The monitoring tier is implemented as a stateless session bean that provides an entry point called auditlog. The development team has provided you with the code that calls the monitoring tier. How can you meet this requirement using WebLogic Server auditing? (Choose the best answer.)
A. Configure the default audit provider and configure the custom audit provider that calls the monitoring tier.
B. Configure the default audit provider to call the custom audit provider, that calls the monitoring tier.
C. Remove the default audit provider and configure the custom audit provider that calls the monitoring tier.
D. Configure the default audit provider and configure it to use the plug-in class that calls the monitoring tier.
What is true about an extension template? (Choose the best answer.)
A. Can be created from an existing template
B. Can include security realm information
C. Can include Node Manager information
D. Can include administrator username and password
E. Can include administration server information
Which two statements correctly describe the WLST nmGenBootStartupProps command? (Choose two.)
A. The target root directory must be on the same machine on which Node Manager is running.
B. The target root directory must be on the same machine on which the Administration Server is running.
C. The name of a server must be supplied to the nmGenBootStartupProps command; otherwise, the command will fail.
D. If you do not specify a server name using the servername argument, the argument defaults to myServer, which must match a server name in the domain or the command will fail.
E. The nmGenBootStartupProps command generates the Node Manager properties files, boot.properties and startup.properties, for the specified server.
You are developing and managing distributed destination applications for which you do not need to create or designate destination members. Which configuration steps in the Administration Console will help you to create and target a Uniform Distributed Topic so that you can rely on WLS to create the necessary members on the JMS servers to which a JMS module is already targeted? (Choose the best answer.)
A. 1. Expand Services > Messaging, select the JMS Module in which to configure the destination.
2. Click New, select Distributed Topic, and click Next.
3. Enter a Name, JNDI Name and set Destination Type to Uniform.
4. Click Next, select the targeted server, and click Finish to finalize the creation of the topic.
B. 1. Expand Services > Messaging, select Destinations.
2. Click New, select Distributed Topic, and click Next.
3. Enter a Name, JNDI Name and set Destination Type to Uniform.
4. Click Next, and select the JMS Module assigned to this topic.
C. 1. Expand Services > Messaging, select the JMS Module in which to configure the destination.
2. Click New, select Distributed Queue, and click Next.
3. Enter a Name, JNDI Name and set Destination Type to Uniform.
4. Click Next, select the targeted server, and click Finish to finalize the creation of the queue.
D. 1. Expand Services > Messaging, select the JMS Module in which to configure the destination.
2. Click New, select Distributed Topic, and click Next.
3. Enter a Name, JNDI Name and expand Advanced Options.
4. Set Destination Type to Uniform. 5. Click Next, select the targeted server, and click Finish to finalize the creation of the topic.
E. 1. Expand Services > Messaging, select the JMS Module in which to configure the destination.
2. Click New, select Uniform Distributed Topic, and click Next.
3. Enter a Name, JNDI Name and click Next.
4. Select the targeted server and click Finish to finalize the creation of the topic.
Your WebLogic domain consists of deployed applications heavily relying on JMS. Three machines, each hosting a managed server, are part of a cluster. In order to ensure the availability of servers and JMS service on those servers, you are considering the configuration of whole server migration rather than service migration. Which two statements are prerequisite for whole server migration but not for manual service migration? (Choose two.)
A. A singleton service must be configured.
B. A shared file system must be created.
C. Each migratable server must be assigned a floating IP address.
D. Either a database leasing service or a consensus leasing service must be configured.
E. A database leasing service must be configured.
You have configured automatic service migration for your JTA service within a domain named mydomain. You find that after the automatic migration completes certain scripts execute automatically and there is a failure happening in these scripts. Where would you look for these scripts for error correction by default? (Choose the best answer.)
A. /user_projects/domains/mydomain/bin/service_migration
B. /user_projects/domains/mydomain/bin/jta-scripts
C. /user_projects/domains/mydomain/bin/servers/
D. /user_projects/domains/mydomain/bin/
You are tasked with configuring a proxy tier for a WebLogic Server domain that has managed Coherence servers configured. What must the Coherence cache configuration file include as part of this task? (Choose the best answer.)
A. Connection properties to enable push replication between two Coherence clusters connected over a WAN
B. Connection properties to enable Coherence*Extend clients to connect to the cluster via TCP/IP
C. HTTP proxy server settings to enable Coherence caching on the web server tier
D. Network connection settings to enable Coherence caching on the client’s web browser
In order to leverage replication and high availability features of the underlying database, you have configured a JDBC TLOG to persist transaction logs in your database. However, WebLogic Server cannot successfully connect to your database at start up. Which outcome should you expect? (Choose the best answer.)
A. The WebLogic Server instance will start without targeting the data source for your store.
B. The WebLogic Server instance will start without a service for your store.
C. The WebLogic Server instance will start without creating the data source for your store.
D. The WebLogic Server instance will fail to start.
You have an enterprise application that includes a resource adapter module. You are considering leveraging WebLogic Server’s Production Redeployment feature for this application. In preparation for deployment, you decide to create a checklist of items to discuss with the developers of the application. Which item would you omit from your checklist as it is irrelevant to production Redeployment? (Choose the best answer.)
A. Ensure the developers have implemented the weblogic.connector.extensions.Suspendadle interface for the adapter.
B. Ensure that the adapter is accessed by a web or web service module within the application.
C. Ensure the adapter is used in an application-scoped manner, having enable-access-outside-app set to false.
D. Ensure that the adapter is compliant with the JCA 1.5 specification.
One server in your WebLogic domain is experiencing a problem. You want to use the WebLogic Diagnostic Framework (WLDF) to diagnose the problem. The default built-in WLDF module is currently configured on the server, but it does not capture the metrics you need. You have the following requirements: You do not want to delete the existing module. You want to minimize metric data output while troubleshooting the issue. You want to focus your analysis on only the server that is experiencing the problem. What WLDF configuration would achieve this result? (Choose the best answer.)
A. Create a new module and add metrics to it, target the new module to the server with the problem, and then activate the new module alongside the existing module.
B. Deactivate the existing module, create a new module and add metrics to it, set an instance parameter to the server with the problem, and then activate the new module.
C. Deactivate the existing module, create a new module and add metrics to it, target the new module to the cluster with the problem, and then activate the new module.
D. Deactivate the existing module, create a new module and add metrics to it, target the new module to the server with the problem, and then activate the new module.
You are under Oracle Linux and you find the process ID of the WebLogic Managed Server Instance:
a
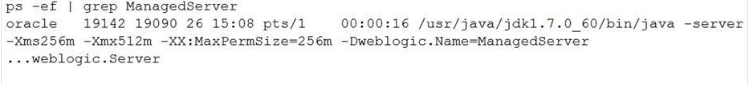
Which two command-line options can you use to issue a thread dump to examine the server for stuck threads? (Choose two.)
A. jstat -class 19142
B. Java weblogic.utils.ThreadDump 19142
C. kill -5 19142
D. jstack 19142
E. kill -3 19142
You are required to configure SSL for an instance of WebLogic Server in a production environment. You have already created your self-signed certificate within the myKeyStore.jks keystore. You must now obtain a new digital certificate from a trusted Certificate Authority. Which command do you use to start the process? (Choose the best answer.)
A. keytool -gencert -alias myCertName -infile myCertName.csr -outfile myCertName.der
B. keytool -certreq -alias myCertName -file myCertName.csr -keystore myKeyStore.jks
C. keytool -printcertreq -alias myCertName -file myCertName.csr -keystore myKeyStore.jks
D. keytool -genkeypair -alias myCertName -dname "CN=MyCert" -keystore myKeyStore.jks
Review the image below. It depicts the architecture for the WebLogic Server auditing.
b
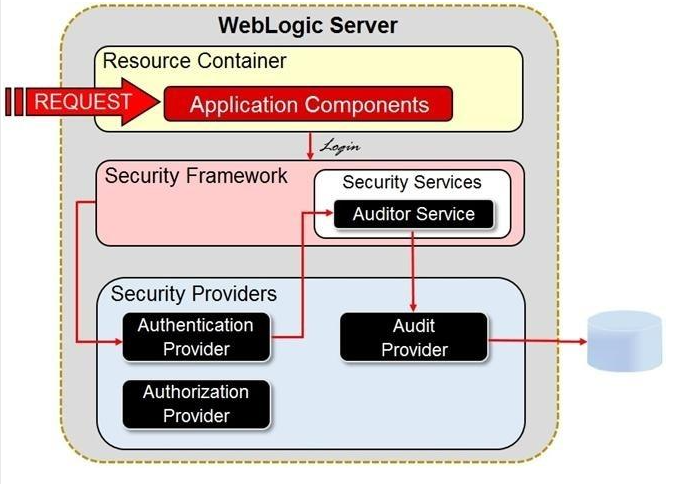
Where in the architecture does WebLogic apply audit configuration parameters that determine if an audit message is logged? (Choose the best answer.)
A. Authorization provider
B. Authentication provider
C. Auditor service
D. Audit provider
You are in the process of validating the architecture of a domain that will serve applications to automate various business activities for a large retailer. The applications rely heavily on JMS and you need to pay special attention to JMS storage. You argue in favor of JDBC-based storage rather than file storage. Your management has asked you to come up with a few key points about why this persistence option would be a better option in case of failure. Which two justifications would support your choice? (Choose two.)
A. JDBC-based stores can be accessed by any client and usually do not reside on the machine that hosts the server.
B. It is easier to recover data from a database rather than from a file.
C. JDBC-based stores are the default choice when creating a new persistent store so it must be an Oracle-recommended choice.
D. JDBC-based stores offer better throughput than file stores.
You are tasked with doing a rolling upgrade of a production domain that will minimize service interruptions. Which is a characteristic of a rolling update? (Choose the best answer.)
A. All the managed servers and node managers need to be shut down.
B. Configuration changes can be made during the rolling update process.
C. An automated backup is part of the rolling update process.
D. The machine hosting the Administration Server must be upgraded first.
E. A major upgrade, for example 11g to 12c, can be accomplished with a rolling update.
You have an Oracle Fusion Middleware domain that uses an Oracle database to store application data and metadata repositories. As part of your disaster recovery configuration, you have set up a passive secondary site. You need to ensure that the data tier components of the primary and secondary sites are in sync so that you can perform a switchover to secondary in case of a disaster scenario. You check with your technical team regarding how to accomplish this requirement. Which Oracle product is the technical team most likely to recommend for achieving data tier synchronization across the two sites? (Choose the best answer.)
A. Oracle Service Bus
B. Oracle ExaLogic
C. Oracle Tuxedo
D. Oracle Data Guard
As the WebLogic domain administrator, you have been asked to create a new cluster and to establish load balancing of JMS destinations across multiple servers for this cluster. Which three configuration options will ensure load balancing of distributed destinations? (Choose three.)
A. Configuring a JMS server and targeting a WebLogic cluster
B. Configuring multiple JMS servers and targeting them to a WebLogic cluster
C. Configuring multiple JMS servers and targeting them to the configured WebLogic Servers
D. Configuring multiple JMS servers and targeting them to a set of migratable targets
E. Configuring a JMS server and targeting it to a set of migratable targets
You are using the WebLogic Diagnostic Framework (WLDF) to monitor your domain for certain scenarios based on runtime data of your running servers. Different groups are responsible for different aspects of the application. As a result, your configuration must fulfill the following requirements: Notifications must be sent only to the correct group that is responsible for the respective part of the application. You must ensure that you can enable and disable monitoring for each level whenever it is needed. How would you configure WLDF watches and notifications to achieve this result? (Choose the best answer.)
A. Configure a single module with a watch for each area, and use a notification filter to send an email to the correct group for each area.
B. Configure a module for each area with a watch that triggers a notification email for the group responsible for that area.
C. Configure a single module with a watch for each area, and each watch triggers a notification email for the group responsible for that area.
D. Configure a module for each area with a watch that uses a notification filter to send an email to the correct group for each area.
Your architecture requires that you create 100 JMS Queues with similar, though not necessarily identical, configuration settings. Which entity will help you carry out the task efficiently? (Choose the best answer.)
A. JMS Distributed Destination
B. JMS Foreign Server
C. JMS Template
D. JMS Destination Key
You have been tasked to create a Domain Template. Which four items can be included in the template? (Choose four.)
A. Windows Start menu entries
B. Log files
C. Java Enterprise Edition (JEE) applications and libraries
D. config.xml and supporting configuration files
E. embedded LDAP cached data
F. Proxy plug-ins
G. Server and services .lck files
H. Unix and Windows start server scripts
You have been asked to assist developers with executing a partial redeployment of static files within a Java EE Web Application deployed to WebLogic Server. The Web Application has already been deployed as an exploded archive directory. Which of the following represents the correct conditions for this to be successful? (Choose the best answer.)
A. The -redeploy argument is used when executing the weblogic.Deployer command.
B. The -distribute argument is used when executing the weblogic.Deployer command.
C. The -distribute argument is used when executing the weblogic.Deployer command and the domain must be in development mode.
D. The -redeploy argument is used when executing the weblogic.Deployer command and the domain must be in development mode.
You are troubleshooting an application that uses a WebLogic server data source. You decide to execute a reset() operation on the corresponding JDBCDataSourceRuntimeMBean. Which statement is true regarding the impact on the application that is using that data source? (Choose the best answer.)
A. A Reset is the equivalent of a Shutdown followed by a Start.
B. A Reset is the equivalent of a Force Suspend followed by a Resume.
C. A Reset is the equivalent of a Suspend followed by a Resume.
D. A Reset is the equivalent of a Force Shutdown followed by a Start.
You are responsible for creating scripts to use Node Manager with a WebLogic Server domain. Which four statements correctly describe the WLST command: nmEnroll? (Choose four.)
A. WLST must NOT be connected to a Node Manager when invoking nmEnroll.
B. The nmEnroll command enables the nmConnect command to be used in a production environment.
C. The nmEnroll command downloads the nm_password.properties and SerializedSystemIni.dat files.
D. WLST must be connected to a Node Manager when invoking nmEnroll.
E. WLST must be connected to an Administration Server when invoking nmEnroll.
F. The nmEnroll command is run once per WebLogic domain per machine unless that domain shares the root directory of the Administration Server.
G. WLST must be offline when invoking nmEnroll.
Coherence is integrated with WebLogic Server in the form of managed Coherence servers. What two options are immediate benefits of running Coherence on WebLogic Servers versus as standalone servers that are not part of the WebLogic domain? (Choose two.)
A. Automatic failure detection and restart of Coherence-based servers
B. Automatic data partition re-balancing of all cached data on running servers
C. monitor Coherence MBeans with the WebLogic Server administration console
D. Life cycle management with the WebLogic Server administration console
E. offload WebLogic Server HTTP session state to Coherence-based servers
You created a user and group using the WebLogic Server default authentication provider. Where are these principals stored? (Choose the best answer.)
A. the WebLogic Server OPSS jps-config.xml security store
B. the WebLogic Server embedded LDAP server
C. the WebLogic Server embedded database security store
D. The default jazn-data.xml file-based security store
Review the following WLST commands.
What happens when these commands are executed? (Choose the best answer.)
A. A diagnostic module named mymodule is created in the domain configuration file and it is enabled on cluster1.
B. A JMS module named mymodule is created without changing the domain configuration file and it is enabled on cluster1.
C. A diagnostic module named mymodule is created without changing the domain configuration file and it is enabled on cluster1.
D. A JMS module named mymodule is created in the domain configuration file and it is enabled on cluster1.
Your clients are connected to distributed destinations to consume messages sent to various JMS topics. Recently, JMS connections got interrupted due to a network failure and your clients dropped their connections as well. How would you ensure seamless failover for your clients when a distributed destination fails? (Choose the best answer.)
A. No action should be needed at the client’s level if the failover is being handled properly at the cluster level.
B. Set the ClientReconnectOptions parameter to Automatic in the Administration Console under the destination configuration general page.
C. Implement an automatic reconnect mechanism in the client exception handler.
D. Set AutomaticClientReconnect to Enabled in the Administration Console under the destination configuration general page.
Which three considerations do you need to keep in mind while configuring a JMS file store in order to ensure the highest possible performance? (Choose three.)
A. Privilege local disks over remotely mounted disks.
B. Compress the file store when there are no more messages.
C. Select the cache-flush synchronous write policy.
D. Dedicate one disk for all file stores.
E. Set MessagesMaximum in your JMS destinations.
As part of a manual migration of JMS-related services, you just configured a custom file store and targeted it to the same migratable target as the JMS server. Which two statements pertain to the successful configuration of this JMS store and the manual migration? (Choose two.)
A. The custom store could be made available to a backup server target with pre-rnigration/post-migration scripts.
B. The custom store should not be targeted to the same migratable target as the migratable service.
C. All the candidate servers in the migratable target should have access to this custom store.
D. The JMS server that is using the default file store should be migrated to a migratable target.
You are tasked with doing a rolling upgrade of a production domain that will minimize user interruptions. What are two characteristics of a rolling upgrade? (Choose two.)
A. Configuration changes can be made during the Rolling Update process.
B. A major upgrade, for example 11g to 12c, can be accomplished with a Rolling Update.
C. The machines can be upgraded in any order.
D. The machine hosting the Administration Server must be upgraded first.
E. Avoid configuration changes until all the servers in the domain have been upgraded.
You need to update a database accessed by an application that uses a WebLogic server data source. It has been decided that the data source on WLS should first be shut down. You have been asked to advise as to whether they should execute a shutdown() or a forceShutdown() on the corresponding JDBCDataSourceRuntimeMBean. Which two statements are true regarding the impact on the application that is using that data source? (Choose two.)
A. The shutdown() operation will fail if there are any reserved connections in use.
B. The forceShutdown() operation will allow 20 seconds for any reserved connections in use to complete prior to destroying the connection.
C. The shutdown() operation will send an HTTP 503 status code to clients.
D. The forceShutdown() operation will immediately cause any in-flight transaction to be rolled back.
E. The shutdown() operation will allow 20 seconds for any reserved connections in use to complete, otherwise the operation will fail.
You have enabled JMS Diagnostic Logging and are analyzing JMS Message delivery and acknowledgment using the generated log entries. For this purpose, you are tracking individual message IDs. What is the default format of the message ID that you would expect to see in the log? (Choose the best answer.)
A. Hexadecimal (e.g., 0xCAE987D’A401)
B. Numeric (e.g., 9018199222001)
C. Floating Point (e.g., 10029920902.10111)
D. Doubly dot delimited (e.g., 683871.1122857923566.0)
Which two objects can be considered potential clients of a Node Manager? (Choose two.)
A. An administration server
B. a WLST session
C. an HTTP server
D. Any other Node Manager
E. A remote JMS client
F. The weblogic.Deployer utility
You are creating a new domain with WLST. Identify three parameters that can be customized with the setOption command. (Choose three.)
A. the JDK that will be used to start the domain
B. The domain name
C. Whether or not the domain will run in production mode
D. The default persistent store type for the domain
E. Whether or not to automatically start the Node Manager
F. The default diagnostic profile for the domain
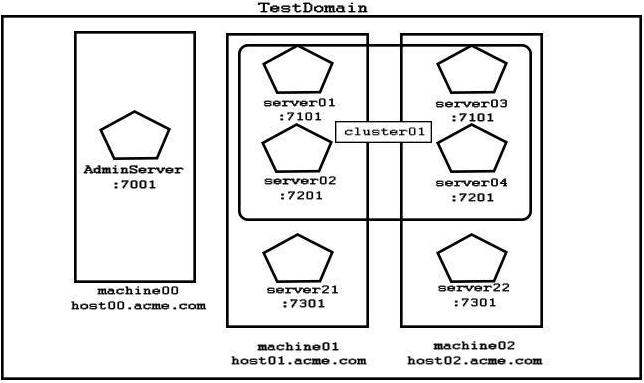
Examine the domain diagram:
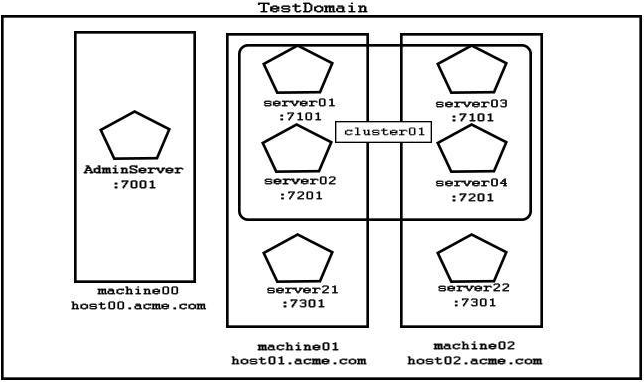
You are asked to write a WLST script that will print the current available heap size for server04.
Assuming: all servers are running you have just started an offline, interactive WLST session a domain-scoped node manager is running on each machine, listening on, port :5556 the username/password "weblogic/Welcome1" maps to a valid domain administrator and Node Manager client
Which two code options will accomplish this task? (Choose two.)
Assuming: all servers are running you have just started an offline, interactive WLST session a domain-scoped node manager is running on each machine, listening on, port :5556 the username/password "weblogic/Welcome1" maps to a valid domain administrator and Node Manager client
Which two code options will accomplish this task? (Choose two.)
A. connect(‘weblogic’,’Welcome1′,’host00.acme.com:7001′) domainRuntime() x = getMBean(‘/ServerRuntimes/server04/JVMRuntime/server04’)print x.getHeapFreeCurrent()
B. connect(‘weblogic’,’Welcome1′,’host02.acme.com:7201′) serverRuntime() x = getMBean(‘/JVMRuntime/server04’)print x.getHeapFreeCurrent()
C. connect(‘weblogic’,’Welcome1′,’host00.acme.com:7001′) serverRuntime() x = getMBean(‘/JVMRuntime/server04’)print x.getHeapFreeCurrent()
D. nmConnect(‘weblogic’,’Welcome1′,’host02.acme.com:5556′) serverRuntimes() x=getMBean(‘/server04/JVMRuntime/server04’) print x.getHeapFreeCurrent()
E. nmConnect(‘weblogic’,’Welcome1′,’host00.acme.com:5556′) domainRuntime() x=getMBean(‘/ServerRuntimes/server04/JVMRuntime/server04’) print x.getHeapFreeCurrent()
In order to leverage replication and high availability features of your back-end database, among other benefits, you are configuring a JDBC TLOG store to persist transaction logs. Since something went wrong during the setup of the TLOG, you are reviewing the configuration considerations for TLOG. Which two guidelines are true for configuring JDBC TLOG stores? (Choose two.)
A. Only one JDBC TLOG store can be configured per WebLogic Server.
B. JDBC TLOG stores should only be configured for RAC databases.
C. Only globally-scoped (not application-scoped) data sources can be targeted to a JDBC TLOG store.
D. Multiple WebLogic Servers can share the same JDBC TLOG store.
You are managing a WebLogic domain that has the default built-in diagnostic module configured for each server in the domain. You have the following requirements: You want to capture metrics that are not collected by any of the built-in diagnostic modules. You want to continue capturing the metrics that are already captured by the existing built-in module. You want your configuration to persist after the server is restarted. What are two approaches you can apply to achieve this result? (Choose two.)
A. Clone the built-in module, add now metrics to it, deactivate the existing module, and activate your new module.
B. Leave the built-in module, create a new module and add metrics to it, and activate your new module alongside the built-in module.
C. Leave the built-in module, create an external resource descriptor module and add metrics to it, and activate your new module alongside the built-in module.
D. Remove the built-in module, create an external resource descriptor module and add built-in and new metrics to it, and activate your new module alongside the built-in module.
Your development team is considering several different types of new applications. You have been asked to advise them concerning which types can be deployed in WebLogic Server leveraging the Production Redeployment feature. Which application deployment type is NOT supported for Production Redeployment? (Choose the best answer.)
A. Enterprise applications (EAR) that contain a Coherence Grid Archive (GAR) module
B. Web service applications that are conversational or that use reliable messaging
C. standalone Enterprise Java Bean (EJB) applications
D. Enterprise applications (EAR) that are accessed by inbound JMS messages
ORACLE_HOME is the Oracle home directory that you specified when installing WebLogic Server. What is the file system location and command for starting the Domain Template Builder? (Choose the best answer.)
A. ORACLE_HOME oracle_commoncommonbin and config_builder.sh
B. ORACLE_HOME oracle_commoncommonbin and temp_builder.sh
C. ORACLE_HOME oracle_commonbin and config_builder.sh
D. ORACLE_HOME oracle_commonbin and temp_builder.sh
You are deploying an application. Which two are common processes for all three staging modes? (Choose two.)
A. The target server receives the deployment command, performs its internal preparation of the deployment, and performs the actual deployment.
B. The administration server executes the deployment process on all targeted servers.
C. The administration server copies all the files to each of the targeted servers.
D. The administration server copies all the files to the appdeploy directory for the targeted servers.
E. The administration server executes the unarchive process in each of the targeted servers.
Under a normal startup scenario, a managed server contacts the administration server to get its configuration information. However in case the administration server is not available, which mechanism can be used by the managed server to start up successfully? (Choose the best answer.)
A. Silent Mode
B. Isolated Mode
C. MSI Mode
D. Cluster Mode
Which three types of information can an Extension Template contain? (Choose three.)
A. JMS
B. JDBC
C. Sample application
D. servers
E. clusters
F. machines
G. Administration username and password
You have a versioned application deployed in your production environment. You have been asked to troubleshoot why the most recent production redeployment appeared to allow the older version to retire too quickly. In this case, the application had active RMI clients, but their subsequent calls were directed to the newer version immediately rather than waiting for the expected five minutes defined by the retirement timeout argument. The script command was: java weblogic.Deployer -adminurl http://localhost:7001 -user weblogic -password Welcome1 -redeploy -name myDeployment -source /myDeployments/myApplication/appX -retiretimeout 300 You expected the older version to remain active (when there are active RMI clients) for five minutes after executing the production redeployment. Which modification should have been made to this command to ensure the older version remains active? (Choose the best answer.)
A. Java weblogic.Deployer -adminurl http://localhost:7001 -user weblogic -password Welcome1 -redeploy -name myDeployment -source /myDeployments/myApplication/appX -retiretimeout 300 -rmigraceperiod 300
B. Java weblogic.Deployer -adminurl http://localhost:7001 -user weblogic -password Welcome1 -redeploy -name myDeployment -source /myDeployments/myApplication/appX -retiretimeout 300 -keepsessions
C. Java weblogic.Deployer -adminurl http://localhost:7001 -user weblogic -password Welcome1 -redeploy -name myDeployment -source /myDeployments/myApplication/appX -retiretimeout 300 -timeout 300
D. Java weblogic.Deployer -adminurl http://localhost:7001 -user weblogic -password Welcome1 -redeploy -name myDeployment -source /myDeployments/myApplication/appX -retiretimeout 300 -remote
Which three statements correctly describe a relationship between Node Manager and Administration Server? (Choose three.)
A. An Administration Server can be under Node Manager control: You can start it, monitor it, and restart it using Node Manager.
B. An Administration Server can be a Node Manager client: When you start or stop Managed Servers from the Administration Console, you are accessing Node Manager using the Administration Server.
C. An Administration Server supports the process of starting up a Managed Server with Node Manager: When you start a Managed Server with Node Manager, the Managed Server contacts the Administration Server to obtain outstandingconfiguration updates.
D. By default, the Administration Server starts a Node Manager with the startNM script in the domain’s bin folder.
E. By default, the Administration Server starts a Node Manager with the startNodeManager script in the domain’s config folder.
F. Node Manager requires an Administration Server to be running before it can start any Managed Servers.
G. A Node Manager can be a client of an Administration Server – When Node Manager needs to monitor Managed Servers, it uses the Administration Server’s runtime MBeans.
You are using the Domain Template Builder to create a new template using an existing domain as the source. Which two directories are included by default? (Choose two.)
A. Bin directory
B. Lib directory
C. Servers directory
D. Common directory
E. Logs directory
F. Replication directory
You manage an application that uses SAML tokens from a trusted voucher to provide single sign-on for virtual clients of your WebLogic domain. Your domain uses an identity assertion provider to manage this authentication. Clients are failing to authenticate. Client return codes and server log files do not include any useful information that can he used to discern where the issue lies. What do you do to determine the problem?
A. Configure SAML and provider debugging, perform a test client request, and analyze the server logs for errors.
B. Inspect network packets to examine token data because, for security purposes, the server does not provide detailed information.
C. Configure the security debug log, perform a test client request, and analyze the log for errors.
D. Reorder the SAML identity asserter provider to determine if the problem is related to virtual users.
Your development team has created a GAR deployment that enables Coherence caching for an application. The GAR file is configured to work within both storage-enabled and storage-disabled nodes. How would you package your GAR as part of the WebLogic Server deployment process for your application? (Choose the best answer.)
A. As an EAR module on storage-disabled nodes and standalone on storage-enabled nodes
B. As an EAR module on storage-enabled nodes and standalone on storage-disabled nodes
C. Within a WAR on storage-disabled nodes and within an EAR on storage-enabled nodes
D. Within a WAR on storage-enabled nodes and within an EAR on storage-disabled nodes
Examine the domain diagram:
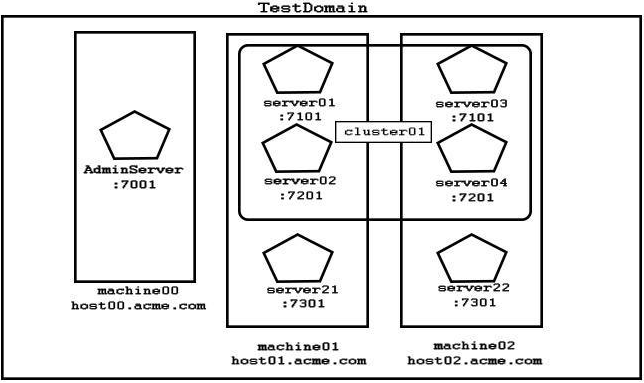
Assume all servers are running and you have an online WLST session connected to the administration server.
Select two code options that would set the variable x as a reference to the machine02 configuration MBean. (Choose two.)
Select two code options that would set the variable x as a reference to the machine02 configuration MBean. (Choose two.)
A. cd(‘/Machines/machine02’) x = cmo
B. x = getMBean("/Machines/machine02")
C. x = cmo.getRef(‘/Machines/machine02’)
D. getRef("/Machines/machine02") x = cmo.currentObj()
E. cmo.getMBean(‘/Machines/machine02’) x = cmo.currObj()
F. cd(‘/Machines/machine02’) x = getRef(cmo)
G. x = getConfiguration(‘/Machines/machine02’)
What is the file extension for a domain extension template? (Choose the best answer.)
A. .jar
B. .zip
C. .ext
D. .tpl
E. .war
F. .ear
You are tasked with creating an Extension Template for an existing domain. What are three options that are presented during the extension creation process? (Choose three.)
A. Use Domain as a Source
B. Use Template as a Source
C. Scripts and Files
D. SQL Script Files
E. Company Name
F. Revision Number
G. Creation Date
H. Operating System requirement
You are implementing leasing functionality within your environment to ensure exclusive ownership of a cluster-wide entity. Which type of leasing requires that Node Manager is configured and running? (Choose the best answer.)
A. high-availability database leasing
B. high-consensus leasing
C. non-database consensus leasing
D. high-availability in-memory leasing
Your developers have decided to use a deployment plan with their applications that will be deployed by WebLogic administrators into one or more WebLogic Server production environments. Which two primary goals can be accomplished by leveraging a deployment plan? (Choose two.)
A. Expose the external resource requirements of the application, such as JNDI names of datasources.
B. Expose additional configurable properties, such as tuning parameters.
C. Expose the targeted servers for deployment.
D. Expose the specific Java EE modules within the application, such as EJBs.
E. Expose access points into the application, such as a WSDL for web services.
You are monitoring a WebLogic JDBC data source and have decided to drop some connections because an earlier peak usage condition has now ended. In addition, this data source has not been enabled for automatic shrinking. What will occur once you execute the shrink() method on that JDBCDataSourceRuntimeMBean?
A. The number of connections in the pool will be reduced to the greater of either the current number of connections in use or to the minCapacity property setting.
B. The number of connections in the pool will be reduced to the current number of connections in use regardless of the minCapacity property setting.
C. The number of connections in the pool will be reduced to the minCapacity property setting regardless of the current number of connections in use.
D. The number of unused connections in the pool will be reduced by half.
You have an application already deployed in a production environment that needs a modification to one of its tuning parameters. Currently, that tuning parameter has a default value since there was neither a deployment descriptor used nor a deployment plan included with the application deployment. You now attempt to use the Administration Console web application to make a dynamic modification to that parameter. Which statement is true? (Choose the best answer.)
A. A new deployment plan will be generated and saved at the indicated location.
B. The modification attempt will fail because there is no deployment descriptor included within the application.
C. The modification attempt will fail because there is no existing deployment plan associated with the application.
D. A new skeleton plan.xml will be generated if a plan folder is detected with the deployed application.
My domain consists of an administration server and two managed servers. During runtime, my administration server has crashed and I wish to start the managed servers in MSI mode. Which two files need to be copied from the admin server to the managed servers when starting them in this mode? (Choose two.)
A. config.xml
B. AdminServer.log
C. SerializedSystemIni.dat
D. access.log
E. MSI.xml
Your domain is experiencing some intermittent problems that you are not able to figure out on your own. You have opened a case with Oracle Support to help you figure out the problem. The support engineer would like to use the WebLogic Diagnostic Framework (WLDF) to obtain an overall view of your WebLogic Server environment to try to narrow the problem to a particular subsystem. What WLDF data does the support engineer request from you? (Choose the best answer.)
A. Diagnostic image snapshot
B. Java Flight Recording of the JVM
C. Instrumentation log
D. Specific harvested metrics
Review the diagram below. It depicts the following: A WebLogic domain that consists of two WebLogic clusters that are each included in a Coherence cluster The Coherence cluster includes a configuration for Coherence*Web HTTP session storage An application deployed on cluster 1 that is configured to use Coherence*Web A client is using a web browser to interact with the application on cluster 1 (via a proxy) The client’s HTTP session is stored by Coherence*Web on the Server in the upper right-hand corner The server where the client’s HTTP session is stored crashes
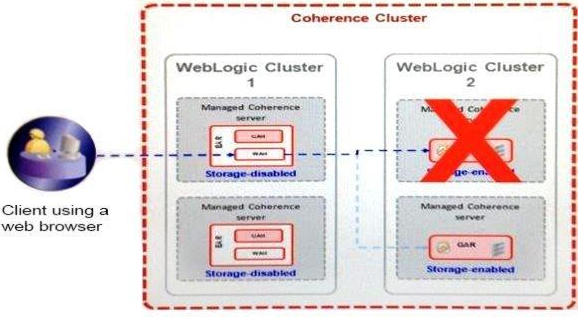
Assuming the next request for an HTTP session attribute is a new attribute that is not stored in a near-cache, the client’s session attribute is fetched from the remaining storage-enabled server in cluster 2.
Why is the session attribute retrieved from this other server’s cache? (Choose the best answer.)
Why is the session attribute retrieved from this other server’s cache? (Choose the best answer.)
A. Coherence*Web stores sessions in a distributed cache on the back end and the request fails over to the new location after partition re-balancing takes place.
B. Coherence*Web stores sessions in a replicated cache on the back end and the request fails over to the new location automatically.
C. Coherence*Web stores sessions in a shared disk cache on the back end and Coherence*Web automatically load balances requests.
D. Coherence*Web stores sessions in a cache that is backed by a database cache loader. The data is fetched from the database and placed into the cache on the new server.
You are creating a Domain Template to simplify the process of deploying a domain across multiple hosts. Which five types of information can be included in a Domain Template? (Choose five.)
A. Domain configuration, those included in the config.xml file
B. Java Enterprise Edition (Java EE) applications and shared libraries
C. Windows and UNIX server start scripts
D. Windows Start menu entries
E. Custom folders and files
F. LDAP data
G. JTA log
H. e-mail notification settings
I want to configure automatic migration of pinned services from an unhealthy server to another target in the cluster. I wish to configure consensus leasing for this purpose. Which two statements are true in this scenario? (Choose two.)
A. Set the cluster "Migration Basis" policy to Consensus.
B. Migratable server should be associated with a node manager.
C. Set the server "Migration Basis" policy to Consensus.
D. A high availability database must be configured to manage consensus leasing information.
In your production environment, you have deployed an application that is accessing a registered Java EE shared library as well as an application deployment plan. In addition, both the library and the application annotations for some of their configuration properties. You are attempting to understand the current state of the properties that have been used in this deployment. From greatest to least, what is the correct order of precedence that is used by WebLogic Server when applying configuration properties during deployment? (Choose the best answer.)
A. Deployment Plan, Application descriptors, Library descriptors, Application annotations, Library annotations
B. Deployment Plan, Application annotations, Library annotations, Application descriptors, Library descriptors
C. Deployment Plan, Library descriptors, Application descriptors, Library annotations, Application annotations
D. Deployment Plan, Application descriptors, Application annotations, Library descriptors, Library annotations
E. Deployment Plan, Library descriptors, Library annotations, Application descriptors, Application annotations
My JMS Server uses a persistent file store. I need to ensure that the size of the persistent store does not exceed 1GB. Which option can I use to configure this? (Choose the best answer.)
A. Set the weblogic.store.FileSize to 1GB.
B. Set the weblogic.store.MaxFileSize to 1GB.
C. Set the weblogic.store.TotalFileSize to 1GB.
D. The file size limit must be configured at the operating system level.
Even though your company has a thorough procedure for testing applications in a pre-production environment prior to production deployment, you have decided to conduct additional testing of a particular application after it is deployed. You choose to deploy the application in administration mode. Which three statements are true? (Choose three.)
A. The application deployment must use the -redeploy option using a unique version string.
B. You must configure an administration port for the entire domain, or an administration channel for the targeted server.
C. The application must first be distributed to the targeted server prior to starting it in administration mode.
D. The application cannot have any dependencies on any shared Java EE libraries.
E. After testing, the application can be dynamically transitioned to start accepting all client requests.
The administration server is a major component of a WebLogic domain. I need to make available a standby administration server in case the main administration server in the domain crashes. Which utility will help me in doing this? (Choose the best answer.)
A. Configuration Wizard
B. Domain Template Builder
C. pack/unpack
D. Enterprise Manager
In order to increase scalability and high availability you are configuring WebLogic clustering with JMS distributed destinations. Which recommendation will ensure optimal load balancing of the message processing?
A. The machines that host the cluster should have similar processing power, disk space, and memory.
B. The cluster should include at least one configurable server.
C. The cluster should use unicast communication.
D. All servers in the cluster should be assigned to the same WebLogic machine.
Examine the domain diagram:
Assume all servers are up and running and you have just started an offline WLST interactive session. Assume further that the username/password "weblogic/
Welcome1" maps to a valid administrator.
You type two lines of WLST code: connect(‘weblogic’,’Welcome1′,’host02.acme.com:7101′) print cmo.getType() + ‘:’ + cmo.getName()
What will be printed? (Choose the best answer.)
Welcome1" maps to a valid administrator.
You type two lines of WLST code: connect(‘weblogic’,’Welcome1′,’host02.acme.com:7101′) print cmo.getType() + ‘:’ + cmo.getName()
What will be printed? (Choose the best answer.)
A. Domain:TestDomain
B. DomainRuntime:server03
C. Server:server03
D. Machine:machine02
E. Session:weblogic
You are concerned with messages being received systematically. You designed Message-Driven beans (MDB) to guarantee the most reliable way to consume messages. In which three scenarios would JMS always redeliver a message? (Choose three.)
A. When the onMessaqe() method of the MDB throws a Java error
B. When the transaction the MDB participates in eventually fails and rolls back
C. When the onMessage() method fails to acknowledge the reception of the message
D. When messages are not being sent as part of a transaction
E. When messages are non-persistent
Some of the messages entering a JMS queue are expiring and are being removed from the queue. You need better insight regarding these expired messages. Which mechanism helps achieve this? (Choose the best answer.)
A. Set the "Log Expired Message" attribute to true for the queue.
B. Associate an ExpirationEventHandler object for the queue.
C. Enable Message Life Cycle logging for the JMS Queue.
D. Configure an Expiration Event Handler for the JMS Queue which logs the expired message properties.
You need to ensure that when a failed admin server instance is restarted on another machine with a different IP address, the managed server is able to establish connection with the newly started instance. Which technique will ensure that the connection can be made? (Choose the best answer.)
A. Configure a DNS name for AdminServer which maps to multiple IP addresses and specify this DNS name during managed server startup.
B. Specify multiple admin server IP addresses during managed server startup.
C. Use WLST to update the AdminServer IP address for a running managed server.
D. Update the host file for a running managed server instance.
Which three statements are correct regarding the WLST create command? (Choose three.)
A. When the create command is used with WLST online, the connection must be to the administration server.
B. The type of MBean being created must be a child type of the current management object.
C. The correct order of the mandatory parameters for the create statement is name followed by childMBeanType.
D. The create command is used to create any configuration or runtime management bean.
E. The create command returns a WLSTProgress object.
You intend to introduce ordering in message processing for your JMS destination by creating a destination key. Which statement is true about the JMS Destination Key configuration? (Choose the best answer.)
A. A JMS Destination Key cannot be specified using WLST.
B. A JMS Destination Key cannot be used to sort messages in a Last In First Out order.
C. A JMS Destination Key allows a user-defined sort key.
D. A Destination Key can be applied to the message body.
You are configuring the principals needed to fulfill the security requirements of an application within a sandbox environment that uses the WebLogic Serverembedded LDAP server. The given security requirements provided have outlined the following facts about some test principals:
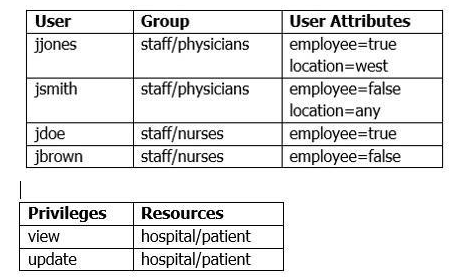
One security requirement states that internal patient data can be viewed only by physicians who are employees.
What is an appropriate way to fulfill this security requirement from a principal perspective using the provided information?
What is an appropriate way to fulfill this security requirement from a principal perspective using the provided information?
A. Create an authorization policy that grants access if a user is a member of the physicians group and their employee attribute is true, bypassing the use of a role entirely.
B. Create an ACL that grants access if a user is a member of the physicians group and their employee attribute is true, bypassing the use of a role entirely.
C. Create authorization policies for individual users whose employee attribute is true creating a constraint-only model, bypassing the use of a role entirely.
D. Create an authorization policy that denies access if a user is a member of the physicians group and their employee attribute is false, bypassing the use of a role entirely.
What does the WLST command pwd() do?
A. Displays the current location in the configuration or runtime bean hierarchy.
B. Displays the location in the file system where the current WLST session was launched.
C. Initiates an operation to change the current WLST user’s password.
D. Prints the name of the current domain.
E. Prints the name of the current server.
For some reason, servers in your domain are failing. The host machines are pingable and the WebLogic JVM processes are running but the getState() method on the ServerRuntimeMBean reports FAILED. In the future, when this happens, you want these failed servers to be shut down and then restarted automatically without human intervention. At the same time, you want to constrain how much time will be spent restarting those servers and how many restart attempts will be made. Pick the two options that would help with this situation. (Choose two.)
A. For each server (or cluster), set RestartInterval to an appropriate positive integer.
B. When starting Node Manager, use the WLST nmStart command and pass in a WLST properties object with RestartMax set to an appropriate positive integer.
C. Start the servers by executing the restartManagedWebLogic.sh script in the domain’s /bin directory.
D. Make sure all managed servers are members of a cluster with ReplicationGroupsEnabled set to true.
Which are three valid actions of the Post Domain Creation process? (Choose three.)
A. Import LDAP data from XML files.
B. Run pack and unpack commands for managed servers on remote machines.
C. Run any SQL scripts to generate database artifacts.
D. Use WLST to run the postdomain.py script.
E. Run the root.sh script.
F. Assign DNS names to all the hosts.
G. Run the RCU utility for each hosted application.
Which three Weblogic server entities can be set up for service level migration? (Choose three.)
A. JMS Server
B. JOLT Service
C. JTA Transaction Recovery Service
D. User Defined Singleton Service
E. JDBC Service
F. JNDI Service
Poor ventilation and cooling in and around the machine that hosts your administration server and a clustered managed server causes a local hard drive failure and thus both servers crash as well. This is the first time this crash has occurred in production but an automatic Whole Server Migration kicks in as expected. The clustered server migrates to a machine on which it has never run before, and for that reason the server cannot be started on this new machine. Which action could have helped to launch this migrated clustered server? (Choose the best answer.)
A. Shut down and relaunch the Node Manager.
B. Ensure that the Administration Server is up when the server migration is being performed.
C. First restart the Administration Server, remove this managed server from the cluster, restart it manually, and then target it back to the cluster.
D. Use a shared disk/NFS for all the migratable servers in the cluster.
E. Copy the Node Manager security files to the new machine that hosts your migrated server.
You want to use the WebLogic Diagnostic Framework (WLDF) to monitor some historic MBean attribute values in your WebLogic domain.

Which WLDF component do you use to accomplish this? (Choose the best answer.)
A. the Harvester with a metric collection definition
B. a Watch on a metric collection definition
C. the MBean Collector with a metric collection definition
D. the Archiver with a metric collection definition
You are analyzing the JMSDeliveryMode header field for all the messages for all the queues deployed to your JMSServer. Which two values do you expect to find for this header? (Choose two.)
A. PERSISTENT
B. NON_PERSISTENT
C. TRANSIENT
D. PERMANENT
E. MULTIMODE
F. EXACTLY_ONCE
You are considering targeting your JMS servers to dynamic clusters to benefit from dynamic scaling. However, you have been advised to keep in mind some of the associated limitations. What are two valid limitations and considerations for clustered JMS services? (Choose two.)
A. Store-and-Forward agents cannot be targeted to a cluster (dynamic or mixed).
B. WLST in offline mode does not support the get and set commands to target JMS servers to a dynamic cluster.
C. A sub-deployment cannot be targeted to a duster.
D. Targeting a messaging bridge to a dynamic cluster is not supported.
You are asked to create a WLST script to make live updates to a domain that has its administration server running. You want your script to mimic the actions of a WebLogic administrator by using the administration console and clicking the "Lock and Edit" button. What commands would accomplish this?
A. edit() followed by startEdit()
B. lockDomain() followed by edit()
C. domainConfig() followed by cd(‘Edit’)
D. getLock(0) followed by edit()
E. clearPending() followed by lockDomain()
F. lockDomain() followed by editDomain()
We find the JMSRedelivered header set for a particular message on the receiver. In which two scenarios is this expected to happen? (Choose two.)
A. The application has already received the message, but did not acknowledge it.
B. The session’s recover() method was called to restart the session beginning after the last acknowledged message.
C. The sender calls the redeliver() method for the message.
D. The sending application crashes after sending the message.
A hardware load-balancer (HWLB) is positioned as the primary entry point into your WebLogic Server domain. Aspects of your application use SSL to protect data on the network from your clients to your domain.
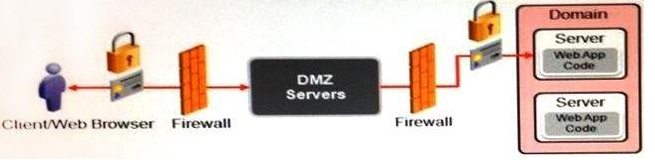
Which configuration provides the best performance for your domain? (Choose the best answer.)
A. Configure the HWLB to use an SSL hardware accelerator and terminate SSL.
B. Configure the HWLB to use pass-through SSL, configure an SSL hardware accelerator on WebLogic, and terminate SSL.
C. Configure the HWLB to delegate SSL handling to the WebLogic Proxy Plug-in and terminate SSL.
D. Configure the HWLB to use pass through SSL to the WebLogic Server that it connects to, and terminate SSL.
You successfully configured a new dynamic cluster but haven’t launched any of the dynamic servers. You want to change the configuration for one specific server. Which parameter can you modify for that server before starting up the dynamic clustered servers for the first time?
A. Listen port number of individual dynamic servers
B. Machine name that hosts a dynamic server
C. Dynamic server name
D. Replication groups
E. No parameters can be modified.
You need to make sure that a JMS Message never expires. What value should you set for the JMSExpiration header? (Choose the best answer.)
A. 0
B. 999
C. 1000
D. 1
The image below depicts a high-level diagram of configuration auditing within WebLogic Server. When Administrators make configuration changes to the WebLogic Server domain, those changes are sent to the audit provider for logging.
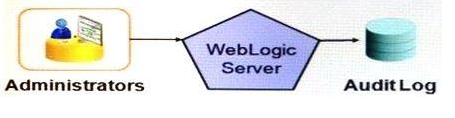
What task must be performed in order to make configuration audit messages in the log meaningful to an observer?
A. Define unique users for all administrators.
B. Configure a persistent store for log messages.
C. Configure the CONFIG severity level.
D. Define the audit message listener for audit messages.
Your WebLogic domain is experiencing a problem. You want to use the WebLogic Diagnostic Framework (WLDF) to diagnose the problem. You have a support case open with Oracle Support, and they have requested a diagnostic image of your server that is experiencing the problem. The problem is not predictable or reproducible on-demand, but you noticed that the number of requests waiting to execute increases dramatically when the problem does occur. The problem also seems to occur at any time of the day or night. How would you approach reliably capturing a diagnostic image that contains data that is relevant to the problem that is occurring?
A. Configure a WLDF watch that triggers a diagnostic image action when the number of requests waiting to execute exceeds a certain threshold.
B. Configure WebLogic overload protection to automatically trigger a diagnostic image when the number of requests waiting to execute exceeds a certain threshold.
C. Manually monitor the number of requests waiting to execute and create a diagnostic image when you see the number of requests waiting to execute exceeds a certain threshold.
D. Configure the server health failure action to trigger a diagnostic image when the number of requests waiting to execute exceeds a certain threshold.
You are required to configure a Coherence cluster for a WebLogic domain. Review the image below for the architecture of the WebLogic domain.
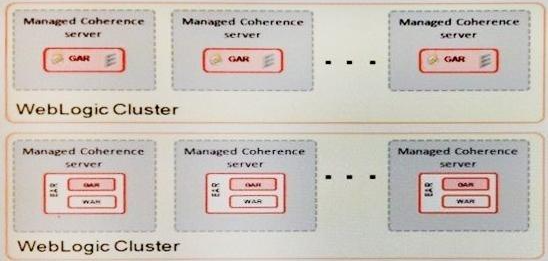
The configuration represents the following:
Two WebLogic clusters of n number of servers each One cluster contains an EAR deployment that contains a WAR module and a GAR module
One cluster contains a GAR deployment
Application data flows into the cluster with the EAR deployment and then to the cluster with the standalone GAR deployment
Based on this configuration, what is the typical configuration of a Coherence cluster for this domain?
Two WebLogic clusters of n number of servers each One cluster contains an EAR deployment that contains a WAR module and a GAR module
One cluster contains a GAR deployment
Application data flows into the cluster with the EAR deployment and then to the cluster with the standalone GAR deployment
Based on this configuration, what is the typical configuration of a Coherence cluster for this domain?
A. Single Coherence cluster that includes both WebLogic clusters. EAR cluster is storage-disabled. GAR cluster is storage-enabled.
B. Single Coherence cluster that includes both WebLogic clusters/EAR cluster is storage-enabled. GAR cluster is storage-disabled.
C. A Coherence cluster for each WebLogic cluster. EAR and GAR clusters use a replicated topology with storage enabled.
D. Single Coherence cluster that includes both WebLogic clusters.EAR and standalone GAR clusters are both storage-enabled.
You are planning to use WebLogic JMS for implementing my enterprise messaging architecture. Which messaging paradigm is invalid in this context? (Choose the best answer.)
A. Point to Point messaging
B. Publish Subscribe messaging
C. Datagram messaging
D. Persistent messaging
What are two differences between a group and a role? (Choose two.)
A. Groups are static and roles are dynamic and conditional.
B. Roles can be scoped to applications and groups are only global.
C. Roles are static and groups are dynamic and conditional.
D. Groups can be scoped to applications and roles are only global.
E. Groups can contain roles but roles cannot contain groups.
A Web Module needs specific tuning. The Development team fine tunes the module in the deployment descriptor (weblogic.xml) as follows:
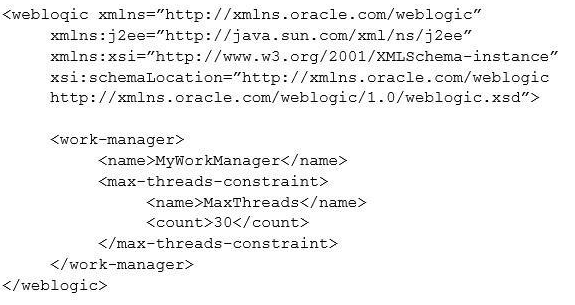
Which two are true? (Choose two.)
A. MyWorkManager is an application-scoped Work Manager.
B. Add the line MyWorkManager before tags in weblogic.xml to make the Web Module use the Work Manager MyWorkManager.
C. MyWorkManager is a Global Work Manager.
D. MyWorkManager is a Default Work Manager.
E. Once the application is deployed and started on a Managed WebLogic Server, MyWorkManager will appear under Environment/Work Managers on the WebLogic Console.
Which two automatic migration scenarios require node manager for all migratable services? (Choose two.)
A. Consensus leasing
B. Database leasing with no pre and post migration scripts
C. Database leasing with pre and post migration scripts
D. Synchronous leasing
Which two statements are true about the role of cluster master in whole server migration? (Choose two.)
A. There is exactly one cluster master in the cluster at a given point of time.
B. The cluster master must host all the pinned services in the cluster.
C. Any managed server in the cluster can serve as the cluster master.
D. A cluster master must always be different from a singleton master.
E. The cluster master must always be started with the node manager.
You are trying to set up a JMS Session with a specified acknowledgment mode. You want the application that receives the message to explicitly take care of the acknowledgment. Which option represents a valid choice for the acknowledgment mechanism that you can use? (Choose the best answer.)
A. AUTO_ACKNOWLEDGE
B. CLIENT_ACKNOWLEDGE
C. DUPS_OK_ACKNOWLEDGE
D. DEFAULT_ACKNOWLEDGE
You created a script to monitor your WebLogic Server WLS Execute Thread:
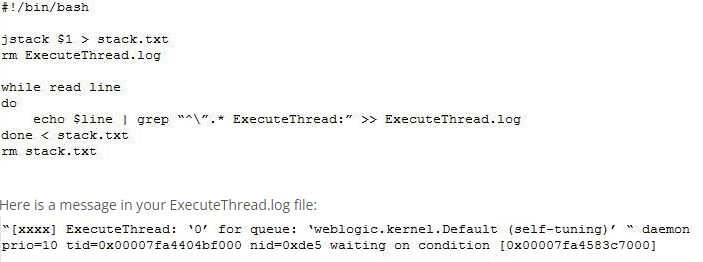
What is the value of xxxx if the thread has been running a request for twenty minutes, assuming a default configuration?
A. SRANDBY
B. ACTIVE
C. STUCK
D. RUNNING
E. WAITING
F. ADMIN
G. FAILED
A current production WebLogic Server (WLS) domain needs to be upgraded without affecting the users. What are the five steps to follow for a Rolling Update? (Choose five.)
A. Back up the contents of your domain.
B. Use pack and unpack to upgrade each of the servers in the machine.
C. Shut down the servers in a single machine.
D. Repeat the process for all machines in the domain.
E. Restart the servers in the machine.
F. Repeat the process for all domains in the machine.
G. Upgrade the servers in the machine.
You have a multithreaded application that looks up the WebLoqic JMS ConnectionFactory object from the JNDI tree. Which statement is correct in this scenario? (Choose the best answer.)
A. It is not permitted. A multithreaded application cannot access the ConnectionFactory object.
B. The access to ConnectionFactory object MUST be synchronized.
C. The ConnectionFactory object can be referenced in a multithreaded application without any special considerations.
D. Multiple threads trying to use the ConnectionFactory object simultaneously will throw an exception.
E. In a multithreaded scenario, connection objects cannot be safely created from the ConnectionFactory.
Your WebLogic Server (WLS) environment consists of multiple domains. Which is a true statement about WLS domains? (Choose the best answer.)
A. Multiple domains can use the same or separate WLS installation while running on the same machine.
B. Domains require a minimum of one managed server.
C. Multiple domains require separate WLS installations while running on the same machine.
D. Multiple domains require individual Node Managers while running on the same machine.
E. Multiple domains can share the same administration server.
You are asked to configure Node Manager for your production environment. You are considering whether to use the Java version or the script-based version of Node Manager. Which statement correctly describes the difference between the two versions?
A. If you are installing WebLogic Server on a Windows system, you must use the Java version of Node Manager.
B. The script-based version of Node Manager can be used in conjunction with inetd on supported UNIX systems.
C. The script-based version of Node Manager requires a larger footprint than the Java version.
D. When Node Manager is used for consensus leasing, you may see faster performance with the script-based version.
Your organization is using a Multi data source (MDS) on WebLogic Server to support applications connecting to an Oracle RAC database. You have been tasked with configuring a new callback handler for the MDS. Which two statements are true concerning related MDS options and behavior? (Choose two.)
A. Callback handlers are optional when using the Failover MDS Algorithm.
B. If the Failover Callback Handler attribute is set on the MDS, the Test Frequency attribute is no longer used.
C. Callback handlers are called for both failover and failback decisions.
D. You can register only one callback handler for each WebLogic server.
You are managing and monitoring durable subscribers for your JMS topics to ensure that all the subscribers would receive persistent messages. However, JMS connections are currently restricted, so only one connection with the same client ID could exist in the scope of your cluster. On which page of the Administration Console can you set Client ID Policy to unrestricted in order to lift this restriction? (Choose the best answer.)
A. Topic > Monitoring > Durable Subscribers
B. Connection Factory > Configuration > Client
C. Topic > Configuration > Thresholds and Quotas
D. Topic > Configuration > Overrides
E. Topic > Configuration > Durable Subscribers
F. JMS Server > Configuration > Durable Subscribers
Examine the domain diagram:
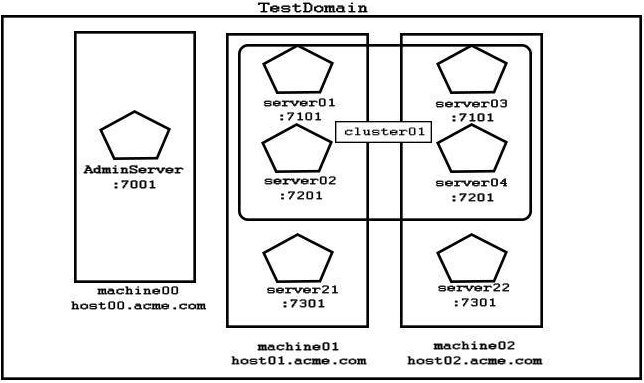
What is the correct path within the configuration hierarchy to the MBean that contains the log rotation parameters for server04? (Choose the best answer.)
A. /Servers/server04/Log/server04
B. /server04/log/rotation
C. /Cluster01/server04/log
D. /Machine02/server04/log
E. /Logs/server04
F. /TestDomain/server04/log
G. /server04/log
You want to create a WebLogic Server (WLS) Work Manager with a Response Time Request Class of one second. You start to create the following WLST script:
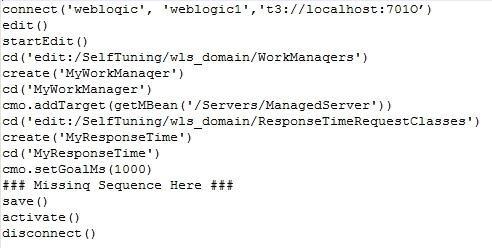
Which two can replace the missing sequence to finish this script? (Choose two.)
A. cmo.addTarget(getMBean(‘/Servers/ManagedServer’)) cd(‘edit:/SelfTuning/wls_domain/WorkManagers/MyWorkManager’) cmo.setResponseTimeRequestClass(getMBean (‘/SelfTuning/wls_domain/ResponseTimeRequestClasses/MyResponseTime’))
B. managedServer=getMBean(‘/Servers/ManagedServer’) cmo.addTarget(managedServer) cmo.setWorkManaqer(getMBean(‘/SelfTuning/wls_domain/WorManagers/MyWorkManager’))
C. cd(‘edit:/Servers/ManagedServer’) cmo.addTarget(getMBean (‘/SelfTuning/wls_domain/ResponseTimeRequestClasses/MyResponseTime’)) cmo.addTarget (getMBean(‘/SelfTuning/wls_domain/WorkManagers/ MyWorkManager’))
D. managedServer=getMBean(‘/Servers/ManagedServer’) cmo.addTarget(managedServer) cd(‘edit:/SelfTuning/wls_domain/WorkManagers/MyWorkManager’) cmo.setResponseTimeRequestClass(getMBean (‘/SelfTuning/wls_domain/ResponseTimeRequestClasses/MyResponseTime’))
E. cmo.addTarqet(‘/Servers/ManagedServer’) cd(‘/SelfTuning/wls_domain/WorkManagers/MyWorkManager’) cmo.setResponseTimeRequestClass (‘/SelfTuning/wls_domain/ResponseTimeRequestClasses/MyResponseTime’)
You are creating and configuring a production WebLogic Server (WLS) domain that is highly available. Which three WebLogic Server features allow you to best accomplish this requirement? (Choose three.)
A. Multiple standalone managed servers
B. Load Balancer
C. Cluster
D. DNS caching
E. Whole-server migration
F. Machine migration
You are troubleshooting an issue with a WLS data source. However, your attempt to execute a manual test on the connection pool fails when you invoke the testPool() method on the corresponding JDBCDataSourceRuntimeMBean. Which configuration condition would contribute to the failure of executing the test? (Choose the best answer.)
A. The TestTableName property is either not set or is set to an invalid SQL statement.
B. The TestFrequencySeconds property is set to a value greater than 0.
C. The TestReservedConnections property is enabled.
D. The ManualTestEnabled property is set to false.
E. The ConnectionReserveTimeoutSeconds property is set to a value other than -1.
My JMS file store size has grown very large and is using up a significant chunk of the disk. I need to reduce the file size during the maintenance window without impacting any relevant information. Which utility enables me to do this? (Choose the best answer.)
A. weblogic.store.Compacter
B. weblogic.store.Admin
C. weblogic.store.Reducer
D. weblogic.file.FileUtil
I am configuring the security policy for my JMS module. I am specifying some security conditions for the module. Which two security conditions are valid in this context? (Choose two.)
A. The JMS module can be accessed only between 1 pm and 6 pm.
B. The JMS module should throw a custom security exception on invalid access.
C. The JMS module can process only 50 messages at a time.
D. The JMS module can be accessed only by users belonging to the Operators group.
E. The JMS module can be accessed in a receive-only mode.
Review the digital certificate below.
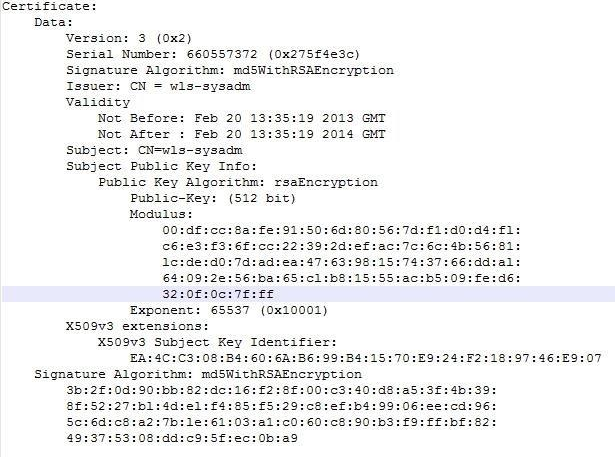
Based on what the certificate contains, which statement is true? (Choose the best answer.)
A. It is a self-signed digital certificate with no certification chain.
B. It is an authentic digital certificate with a valid certification chain.
C. It is a digital certificate for a private key with a valid certification chain.
D. It is an authentic root CA certificate with a valid certification chain.
You are using the administration console to monitor messages in a queue.Which three tasks can be performed while doing this monitoring? (Choose three.)
A. Create a new message in the queue.
B. Duplicate a message.
C. Monitor the content of a message.
D. Delete the message from the queue.
E. Merge two messages.
F. Alter the ordering of the messages.
Which three tools allow you to create a Domain Template? (Choose three.)
A. JDeveloper
B. Pack command
C. Smart Template Wizard
D. weblogic.Build
E. Domain Template Builder
F. WLST
G. Archive command
On a WebLogic Managed Server you administer, you have the following log:You investigate and find a Web Module named MyApp with the following deployment descriptor weblogic.xml: Which two are true? (Choose two.)
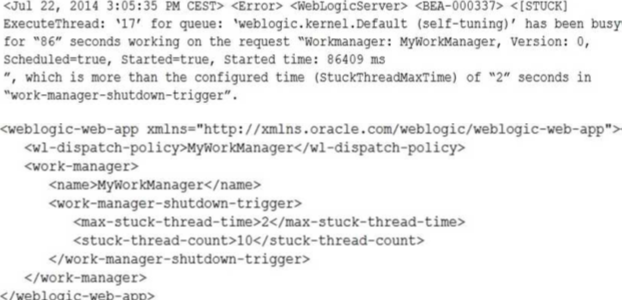
A. Access to Web Module MyApp now returns an HTTP Error: 503 Service unavailable.
B. The ExecuteThread: ‘17’ is now available because WebLogic Server automatically stops stuck threads.
C. When the WebLogic Managed Server is restarted the Web Module will be in Admin mode.
D. If another thread is stuck the error number will be in the WebLogic log file.
E. The health status of the Managed Server where the application is deployed is now warning due to the subsystem pooltread.
What is the difference between a WebLogic Diagnostic Framework (WLDF) watch and a notification? (Choose the best answer.)
A. A watch compares WLDF instrumentation data to a rule and sends a notification SMS text message.
B. A notification compares WebLogic log data to a rule and notifies a watch when the rule is true.
C. A notification compares WLDF instrumentation data to a rule and notifies a watch when the rule is true.
D. A watch compares WLDF metric data to a rule and triggers a certain notification action.
Your application includes a message driven bean (MDB) that is listening to messages on a JMS Queue. You need to ensure that every message is processed exactly once by the MDB. Which configuration allows you to achieve this requirement? (Choose the best answer.)
A. Add an exception handler for the onMessage method in the MDB.
B. Set the Redelivery Limit for the Queue to zero
C. Use container-managed transactions, so that messages are redelivered if unacknowledged.
D. Set the MDB instance count to 1 in the deployment descriptor.
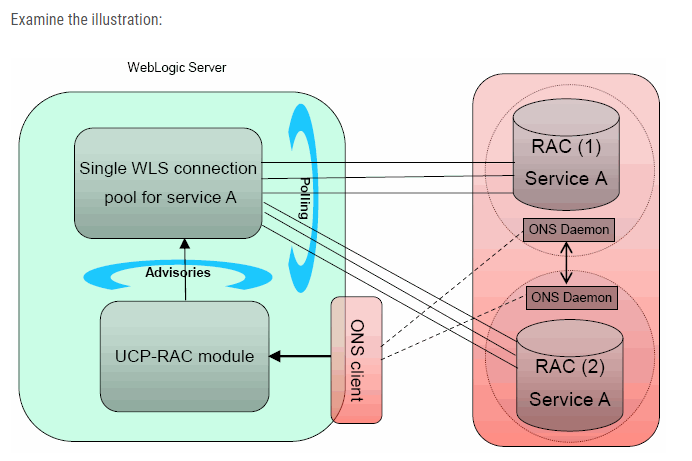
Which best describes the above illustration?
A. Depicts an Active GridLink Data Source between WebLogic Server and an Oracle Database service that includes two RAC nodes
B. Depicts a FAN-disabled Data Source between WebLogic Server and an Oracle Database service that includes two RAC nodes
C. Depicts a Multi Data Source between WebLogic Server and an Oracle Database service that includes two RAC nodes
D. Depicts a Data Source using SCAN between WebLogic Server and an Oracle Database service that includes two RAC nodes
Review this scenario of an application running on a storage-disabled, managed Coherence server that uses a Coherence two-tier near cache: Cache data is already written to the distributed cache. There is a local near cache configured on the application side (storage-disabled node). Application requests the data from Coherence twice. Assuming this is the server\\'s first access of this data from the cache, how many network round trips between Coherence cluster instances take place in total? (Choose the best answer.)
A. 3
B. 4
C. 1
D. 2
You have been tasked with deploying and targeting a new application to every server in a WebLogic cluster. Some servers are running on machines that have access to a common shared file system, while other servers do not have that same access. Currently, the default deployment staging mode for all servers in the cluster is set to STAGE ?however, you wish to avoid having the AdminServer automatically copy the application to the servers (in that cluster) with shared file system access. Which two approaches would satisfy the above requirement? (Choose two.)
A. Change the default deployment staging mode for all servers to EXTERNAL_STAGE, and then copy the application to all servers.
B. Change the default deployment staging mode for the servers with access to the shared file system to NO_STAGE, then copy the application to the shared file system.
C. Change the staging mode of the application to EXTERNAL_STAGE when you are deploying it to the cluster.
D. Leave the default deployment staging mode for all servers as STAGE, but copy the application to the shared file system prior to deployment.
What is the first action to take during a Rolling Update? (Choose the best answer.)
A. Change the Startup Mode to Development; Production Mode is not supported.
B. Remove all managed servers from any cluster and reassign them after the update.
C. Do a Force Shutdown of all the servers, including the Administration Server.
D. Back up your applications, database schema, other application data, and domains.
E. Stop all Node Managers that support the domain to be updated.
You are configuring two-way SSL for a WebLogic Server domain. As a security professional, you realize that even if a client certificate is authentic, it is always possible for a valid certificate to become compromised. Which two options can you configure for WebLogic Server to check if a certificate it receives has been compromised? (Choose two.)
A. Certification Revocation List
B. Certificate Revocation Status Protocol
C. Online Revocation Status Protocol
D. Online Certificate Status Protocol
{"name":"Weblogic 12c AA II", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Test your knowledge and skills in WebLogic Server 12c with our comprehensive quiz designed for system administrators and Java Enterprise Edition developers.Features:30 detailed questions covering various aspects of WebLogic Server.Immediate feedback on your answers.Improve your understanding of JMS, SSL, Coherence, and more!","img":"https:/images/course8.png"}
More Quizzes
21_30
10517
Enterprise JavaChapter End Evaluation Odd Roll Nos
10522
Quiz 2
10511
Vad kan Markdalsnäs om 50-talet?
940
Guess the Celebrity Face - Can You Name Them?
201018748
Arcana Definition - Major Arcana Meanings
201018133
Do I Want a Divorce - Free Self-Assessment
201018357
1.06 Inequalities - Free Practice Test
201016247
Family Guy Color Test - Which Character Likes You?
201017776
Rhetorical Devices Test: Free Interactive Practice
201017055
Internal Medicine - Free Clinical Knowledge Practice
201017776
Which of the Following Is Not True of Credit Scores?
201017243