DAT204
Below are some claims about TCP, select the correct one:
For a TCP connection, the number of unacknowledged bytes can not be larger than the receiver buffer.
The parameter "Receive Window" is a part of the TCP congestion control algorithm.
TCP flow control ensures that the network is not being overloaded.
The number of unacknowledged bytes can be larger than the receiver buffer. (If the variable "Congestion Window" is larger than "Receive Window").
Below are some claims about TCP, select the correct one:
"Fast recovery" denotes the phases in a TCP transmission where the "Congestion Window" increases exponentially (fast).
"Congestion avoidance" is related to the "Receive Window" in the TCP header.
TCP timer expiry triggers "Fast recovery".
"Congestion avoidance" denotes the phases in a TCP transmission where the "Congestion Window" increases linearly.
Which service quality guarantees does SSL give? Select any that are correct.
Data confidentiality
Guaranteed bandwidth
In-order data delivery
Data integrity
None of these
Server authentication
Bounded delay
Reliable data transfer
Which service quality guarantees does TCP give? Select any that are correct.
None of these
Server authentication
Bounded delay
Reliable data transfer
Data integrity
Guaranteed bandwidth
Data confidentiality
In-order data delivery
What is correct about SSL?
SSL always uses AES after the handshake phase
SSL allows agreeing on cryptographic algorithms during the handshake phase.
SSL implements sequence numbers directly in the record itself.
SSL connections are closed simply by sending a TCP FIN segment.
What is the de-facto e-mail encryption scheme described in the textbook?
DSA (Digital Signature Algorithm)
MIME (Multipurpose Internet Mail Extensions)
TLS (Transport Layer Secrity)
PGP (Pretty Good Privacy)
RSA (Rivest-Shamir-Adleman)
Below are some claims about TCP, select the correct one:
A TCP connection must always be reestablished if a router in the underlying IP network goes down so that datagrams can flow in a different direction.
TCP gives a reliable virtual end to end connection over an unreliable IP net.
TCP SYN contains the field "Duration" which tells the receiver how long the connection that is being established shall last.
The TCP header has a minimum length of 32 bytes.
Below are some claims about UDP, select the correct one:
A UDP session socket is identified by the sender and receiver port and IP address.
UDP traffic towards the same application in a server uses a common socket, even if the traffic comes from different clients.
UDP traffic towards the same application in a server uses separate socket when the traffic comes from different clients.
UDP traffic towards different applications in a server uses a common socket if the traffic comes from the same client.
What is the purpose of nonces in an end-point authentication protocol and in the SSL handshake?
Defend against replaying individual packets during an ongoing session.
Defend against connection replay attacks.
Keep track of the sequence numbers.
Keep track of the amount of data sent.
Below are some claims about UDP, select the correct one:
UDP segments with wrong sequence number are discarded.
UDP segments with wrong sequence number are discarded.
UDP segments that are received with the wrong checksum are discarded and retransmitted when the round trip time is expired.
When UDP is used, then any fault correction is up to the application.
Which service quality guarantees does UDP give? Select any that are correct.
Data integrity
Data confidentiality
Bounded delay
In-order data delivery
None of these
Server authentication
Reliable data transfer
Guaranteed bandwidth
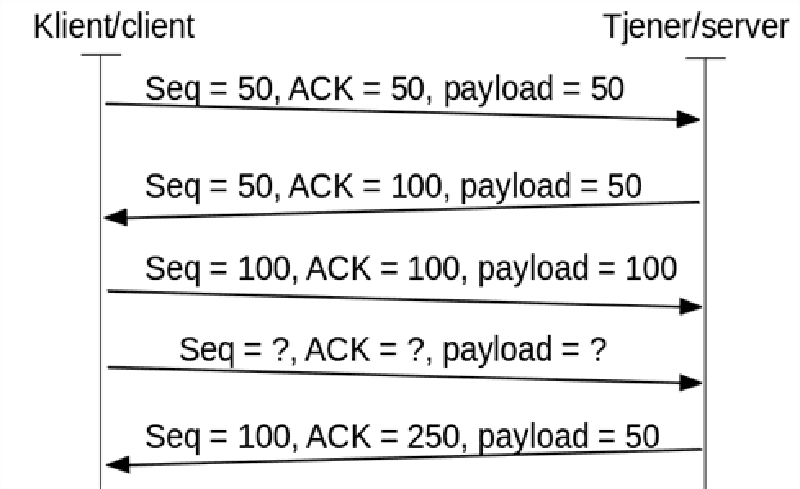
The figure above shows an excerpt of a TCP transmission. What will the sequence number, ACK and payload be in the second last segment in the shown transmission sequence?
Seq = 100, ACK = 150, payload = 50
Seq = 200, ACK = 100, payload = 50
Seq = 100, ACK = 200, payload = 150
Seq = 50, ACK = 200, payload = 50
What is the name of the protocol that enables multiple hosts to share one public IP for communication?
NAT
ARP
IP
BGP
DHCP
TCP
DNS
A Hash-based Message Authentication Code (MAC) can be used to:
provide message confidentiality
Produce an efficient public-key encryption scheme
provide message authenticity
provide message non-repudiation
Provide message integrity
When an IPv6 datagram is to be forwarded from a router that supports IPv6 to a IPv4 router, what happens with the IPv6 datagram?
The IPv6 datagram is simply discarded.
The router de-encapsulates the segment from the IPv6 datagram, and re-encapsulates it into an IPv4 datagram.
The IPv6 datagram is encapsuled into an IPv4 datagram and forwarded to the IPv4 router.
The IPv6 datagram is discarded. The sender then recieves an error message telling to resend the datagram as an IPv4 datagram.
Which layers in the TCP/IP model are involved when a router forwards packets?
Link layer
Application layer
Network layer
Physical layer
Transport layer
How are IP addresses usually assigned to PCs that are connected to a network?
DHCP
Magic
DNS
NAT
BGP
ARP
According to the book, what are the two most important Internet protocols?
POP3 (Post Office Protocol 3)
OSPF (Open Shortest Path First)
HTTP (Hypertext Transfer Protocol)
TLS/SSL (Transport Layer Security/Secure Sockets Layer)
TCP (Transmission Control Protocol)
IP (Internet Protocol)
SMTP (Simple Mail Transfer Protocol)
UDP (User Datagram Protocol)
BGP (Border Gateway Protocol)
Pick the right claim
MAC addresses are assigned by a DHCP server
The ARP protocol returns the MAC address that corresponds to the IP address of a host on the local network. The connection between the hosts are then saved in the ARP table.
An ethernet switch can not handle both IPv4 and IPv6 traffic without dedicated software for each protocol stack.
If the CRC field in an ethernet-frame shows that the frame contains an error, the frame will be discarded and ICMP gives a reply to the sender so that the frame can be retransmitted.
What is the de-facto standard for inter-AS routing?
The Link-State Algorithm (LS)
BGP – Border Gateway Protocol
OSPF – Open Shortest Path First
The Distance-Vector Algorithm (DV)
Pick the right statement about the link layer.
The link layer cannot offer any form of reliable delivery.
The link layer is implemented only in hardware.
The link layer is the place in the protocol stack where software meets hardware.
The link layer is implemented only in software.
Select the correct requirements for secure use of symmetric encryption.
A trusted third-party must be available.
Sender and receiver must keep the key secure.
Sender and receiver must share a secret key in a secure way.
Secret keys must be certified by a trusted certification authority.
A strong encryption algorithm.
Select the correct statement(s) about public key certificates and certification authorities.
A digital certificate includes the identity of its owner and public key.
The signature on a digital certificate is verified using the public key of the issuer.
Digital certificates are signed by the issuer.
Digital certificates are not public.
A digital certificate verifies the identity of the sender of the certificate.
Which layers in the TCP/IP model are normally processed when a router builds the routing tables?
Transport layer
Physical layer
Network layer
Link layer
Application layer
Public-key cryptography may provide:
Data availability
Symmetric key encryption
Data confidentiality encrypting with the secret key
Data authenticity
Digital dignature
In which layer does the following protocols belong? : ARP
Link Layer
Transport Layer
Network Layer
Application Layer
Physical Layer
In which layer does the following protocols belong? : BGP
Link Layer
Transport Layer
Application Layer
Network Layer
Physical Layer
In which layer does the following protocols belong? : DHCP
Network Layer
Transport Layer
Link Layer
Application Layer
In which layer does the following protocols belong? : IPv6
Transport Layer
Application Layer
Physical Layer
Link Layer
Network Layer
In which layer does the following protocols belong? : TCP
Application Layer
Transport Layer
Network Layer
Link Layer
Application Layer message
Bytes
Response
Request
Datagram
Segment
Bits
Frame
Protocol Stack
Message
Transport Layer message
Bytes
Response
Request
Datagram
Segment
Bits
Frame
Protocol Stack
Message
Network Layer message
Bytes
Response
Request
Datagram
Segment
Bits
Frame
Protocol Stack
Message
Link Layer message
Bytes
Response
Request
Datagram
Segment
Bits
Frame
Protocol Stack
Message
Physical Layer message
Bytes
Response
Request
Datagram
Segment
Bits
Frame
Protocol Stack
Message
All protocol layers together are called
Bytes
Response
Request
Datagram
Segment
Bits
Frame
Protocol Stack
Message
{"name":"DAT204", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Application Layer, Transport Layer","img":"https://cdn.poll-maker.com/24-909750/tcpsekvensv2017-finished.png?sz=1200"}
More Quizzes
100
Hh
100
Which old obscure mcyt series should you watch
5226
CACE LEVEL 4 UNIT 3 EXAM
211026
Ultimate Top 200 Brand & Generic Drugs - Test Now!
201074966
Think You Know Slugterra? Take the Ultimate Now!
201030996
Free Local Business Engagement
201029263
Think You Can Ace the Chemistry Chapter 2 Test? Free!
201026160
Discover Your Inner Cop: Jump Street Character
201026160
Flat Track Derby Association: Test Your Skills
201038696
Are You Famous-ish? Take the Ultimate Stardom
201025679
Investments
15825679