DSSC Written Exam Study Guide

DSSC Written Exam Study Guide Quiz
Test your knowledge and prepare for the DSSC Written Exam with our comprehensive quiz! This engaging and informative quiz covers key concepts in network management, Active Directory, Exchange, and more.
- Multiple-choice questions to challenge your understanding
- Focus on practical scenarios for real-world application
- Immediate feedback on your answers
A ___________ -managed network consists of three key components:
SNMP
HIPS
SADR
ACAS
What feature in Active Directory would allow for a domain controller to be provided with information on any object in a forest, regardless of whether the object is a member of its domain?
High-Availability
Global Access List
Global Catalog
Zone Transfer
(Master) Repository
When a secondary DNS server requests a database update from a primary DNS server, the following process is known as a ________________.
Zone Transfer
Send Connector
Conditional Forwarder
Traceroute
In Exchange, what is the acronym DAG short for?
Database Authentication Group
Database Availability Group
Digital Archive Group
Datastore Access Group
Which protocol does ACAS use to e-mail outbound reports?
SSH
HTTPS
SMTP
TCP
TRUE or FALSE: The utilities in the RSAT software suite enhance the performance of the guest operating system in a virtual machine and management capabilities. Although your guest operating systems can run without it, the functionality of the OS would be substantially reduced.
True
False
Which port must be enabled on the ePO server’s firewall in order to communicate with the SQL server?
1433
636
389
8443
Which of the following options IS NOT a major components of HBSS?
Distributed Repositories
Security Center
EPolicy Orchestrator
McAfee Agent
TRUE or FALSE: To apply a GPO to a specific group, both the Read and Apply Group Policy access control entries (ACEs) are required.
True
False
_______________ is a setting that tells the DNS server how long to cache a query or record before requesting an update. _______________is a Microsoft feature that removes outdated DNS resources. This ensures environments using DHCP do not detect duplicate devices based on multiple DNS entries for the same device
Lease Duration; Reservation
Scavenging; TTL
TTL; Scavenging
Reservation; Lease Duration
TRUE or FALSE: If you specify the No Override option for an organizational unit, it prevents the application of policy at that level from higher-level Active Directory containers such as a higher-level organizational unit or domain.
True
False
There are two primary ways of setting up user-created security groups with permissions over a domain: - The first way is by placing one security group (such as a user-created group titled "CP Administrators") within one of the AD built-in security groups (such as Account Operators) that already has permissions in a domain. In this way, our security group’s permissions within the domain are inherited from the other. This process is known as _________________ .
Scavenging
Conditional Forwarding
Group Nesting
Zone Transferring
Privilege Escalation
Which of the following options IS NOT a component of ACAS?
Passive Vulnerability Scanner
Security Center
Distributed Repositories
Nessus
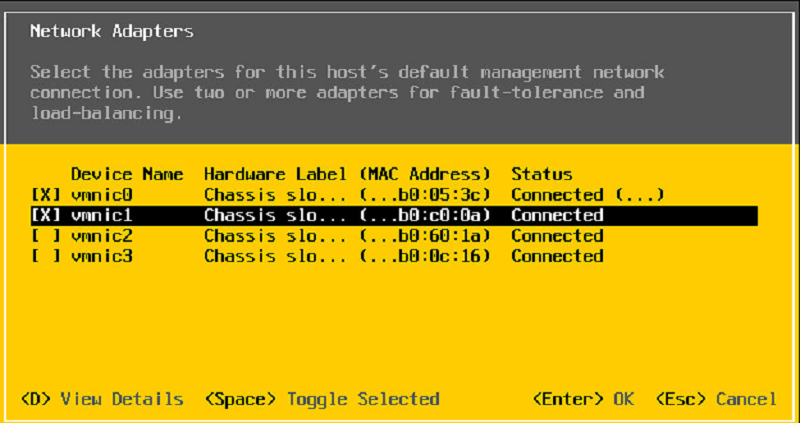
What management console is shown?
ExRCA
VSphere
ESXi
Syslog
EAC
Through virtualization, a hypervisor runs on top of the physical hardware of a server. Instead of the hypervisor itself requesting resources from the physical hardware to create, run, and manage virtual machines, it would instead have a dedicated component solely for this purpose. This component is known as a ____________?
VMkernel
VSwitch
Send Connector
Comptroller
A server running Active Directory Domain Services (AD DS) is called a _____________.
Virtual Machine
Organizational Unit
Domain Controller
Global Catalog
_____ is an allocation of CPU and memory resources.
Resource Pool
Datastore
VSAN
Virtual Machine
TRUE or FALSE: Best practice for Global group use is to add user accounts to Universal groups first; then those universal groups can be nested within a Global group.
True
False
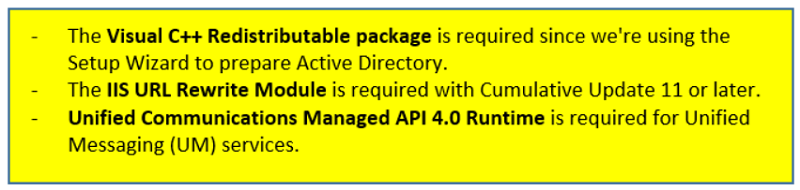
The above steps are taken to install which server solution?
Microsoft Exchange
CAS
ESXi
ExRCA
Windows Server 2022
Which of the following options IS NOT a function of ACAS?
Data Loss Prevention
Network Discovery
Automated network vulnerability scanning
Device configuration assessment
Step by step instructions to install a DISA-provided software image can be found where?
Manpower
Software Center
MARFORCYBER homepage
DoD Patch Repository
-- provides extra security via external antivirus and anti-spam filters.
Edge transport
Mailbox
Management tools
-- holds user databases, as well as provides transport services for routing mail and access services that enable client connections.
Edge transport
Mailbox
Management tools
-- this option would be used for allowing a different server within your domain the ability to help manage your Exchange organization.
Edge transport
Mailbox
Management tools
Active Directory structures are arrangements of information about ___________ which fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Microsoft recommends using ___________ to provide structural hierarchy to a domain within Active Directory.
Objects; security groups
Objects; organizational units
Organizational units; security groups
Organization units; clusters
___________________________ is the use of a computer’s physical components to support the software that creates and manages VMs. Its use effectively eliminates the drawbacks of its alternatives: Full Virtualization (imposes significant system overhead) and Paravirtualization (typically requires extensive modifications for the OS to use)
Group Nesting
Desktop Virtualization
IE Enhanced Security Configuration
Hardware Assisted Virtualization
Sysprep
Links the name of a domain to its physical ip address.
Host(A)
Start of Authority(SoA)
NameServer(NS)
Mail Exchange(MX)
Points client queries to the authoritative DNS server for resolution.
Host(A)
Start of Authority(SoA)
NameServer(NS)
Mail Exchange(MX)
Essentially a documentary record, containing some administrative information such as when the domain was last updated.
Host(A)
Start of Authority(SoA)
NameServer(NS)
Mail Exchange(MX)
Directs email to a mail server.
Host(A)
Start of Authority(SoA)
NameServer(NS)
Mail Exchange(MX)
7. _____ is a hypervisor that installs directly onto your physical server.
Bare-metal/Type 1
Windows
VSphere
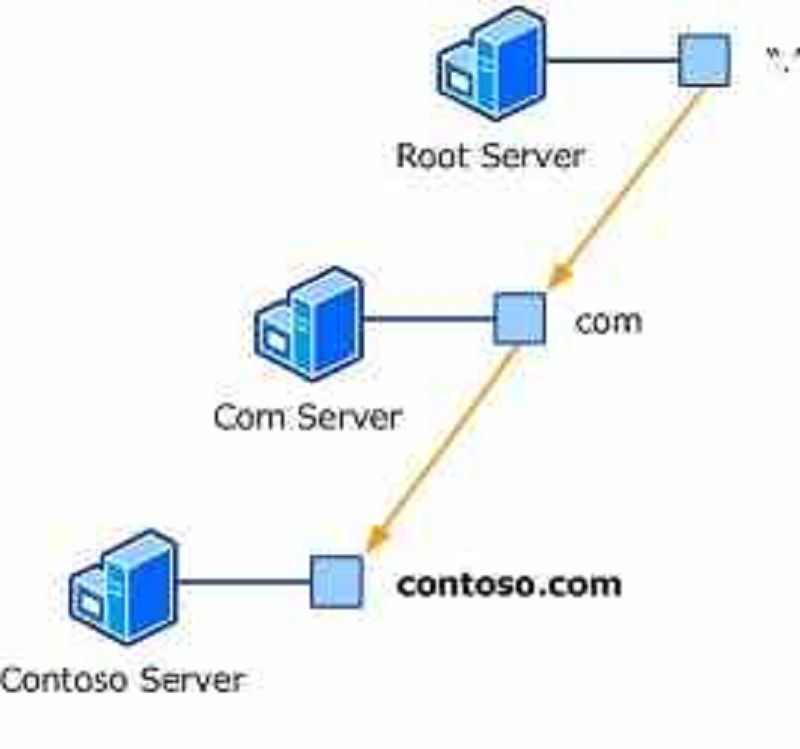
What is being shown in this picture?
Forward Lookup
AD Synchronization
Encapsulation
Zone Delegation
What is the primary network virtualization and cloud computing vendor utilized by the Marine Corps?
McAfee
NetApp
MCEN
VMware
The following protocols are most commonly associated with what type of network service?
-Session Initiation Protocol (SIP)
-Skinny Client Control Protocol (SCCP)
-Real-time Transport Protocol (RTP)
-Media Gateway Control Protocol (MGCP) -H.323
File Share
Print Server
DNS
VoIP
What is the following URL an example of? https://webmail.apps.mil/mail/
DISA Homepage
OWA
DoD Patch Repository
Forward Lookup Zone
_______________ is a setting that tells the DNS server how long to cache a query or record before requesting an update.
Lease Duration
DNS Reservation
DHCP Reservation
TTL
Which of the following options IS NOT a component of ACAS?
Distributed Repositories
Passive Vulnerability Scanner
SecurityCenter
Nessus

Which management console is shown?
Registry Editor
Server Manager
Group Policy Management Console
Active Directory
When processing the GPO, the system checks the __________ associated with the GPO. If an ___________ denies the computer or user access to the GPO, the system does not apply the policy settings specified by the GPO.
Access Control List (ACL); Access Control Entry (ACE)
Super-Agent Distributed Repositories (SADR); Access Control Entry (ACE),
Access Control List (ACL), ePolicy Orchestrator (ePo)
SADR; ePo
__________ is the primary network storage vendor utilized by the Marine Corps.
NetApp
VSAN
RAID
VSphere
If the McAfee Agent on a client machine loses contact with the ePO server, it will
Enforce the last policy it pulled
Pull policies from the internet
Run a local backup policy
Pause until contact is re-established
WHICH TYPE OF GROUP SCOPE IS BEING DESCRIBED?
This scope is used for assigning access to permissions, and making any changes in the access list of a resource (i.e., managing resource permissions).
-- Example: assigning access to a printer
-- only group that can have members from outside the forest.
Universal
Global
Domain Local
None of the Above
__________ functions as a virtual computer system with its own CPU, memory, network interface, and storage.
Stub Zone
Domain Controller
Organizational Unit
Virtual Machine
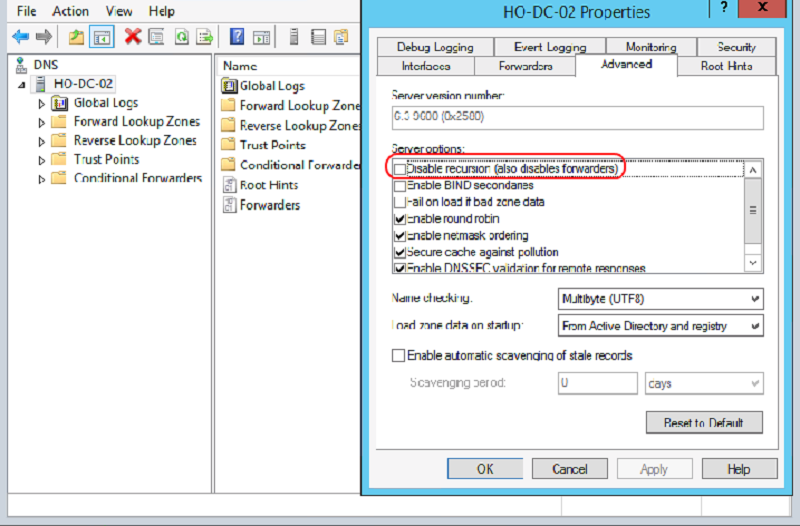
What type of management console is depicted?
DHCP
DNS
VSphere Client
GPO
An administrator can specify which security groups are affected by a GPO by using _______________ .
Delegation Wizard
Global Catalog
EAC
DNS Management console
Access Control List (ACL) Editor
The primary function of a ________________ is to authenticate and validate users on a network, including group policies, user credentials, and computer names to determine and validate user access. Any additionally roles you install are therefore secondary functions.
Virtual Machine
Organizational Unit
Global Catalog
Domain Controller
Which management tool IS NOT created as part of a standard Microsoft Exchange installation?
EAC
ExRCA
Exchange Management Shell
Exchange Toolbox
In any network environment hosting services, at least one DC should be configured to be a DNS server because _______________________
External DNS queries require access to a domain controller to be properly routed
It allows the use of AD-integrated lookup zones, which improve security and simplify zone replication
It reduces the vulnerability surface by combining roles onto one VM, with the added benefit of eliminating the most common need for deploying an Edge Transport server as well
IP address-to-URL resolution would fail otherwise
_________________ is the process of monitoring network traffic at the packet layer to determine Topology, Clients, Applications, Profiling, and System Compromise Detection.
Passive Vulnerability Scanning
Multi Threat Scanning
Network Vulnerability Scanning
Application Vulnerability Scanning
Tasks that require this level of access are forest-wide and are executed very rarely over the life of an AD forest. Such tasks include adding either a child domain of tree domain to an existing forest, and software that requires updates to the Configuration partition of an AD forest, such as Exchange Server
Schema Admins
Enterprise Admins
Administrators
Access to this group gives an administrator the ability to modify the definitions and attributes of nearly every object type (users, computers, etc) that can be created in a forest, however there are very few instances where this would become necessary. Common examples for which it would be necessary include updating AD to a new version of Windows or installing Exchange, which adds numerous attributes to user objects
Schema Admins
Enterprise Admins
Administrators
Effectively grant users in them the same rights as the Domain Admins security group with very slight differences that generally do not affect Administrative decision-making.
Schema Admins
Enterprise Admins
Administrators
The general recommendation of vcpus you should allocate to your domain controller is _____.
2
3
4
1
WHAT IS BEING DESCRIBED? Outdated documentation pertaining to a network architecture and its devices will negatively impact troubleshooting capabilities when network issues occur. This includes delays in resolution, as well as potential misconfigurations. Therefore, it is of the upmost importance new developments are being tracked properly, and records of a network are kept current.
Incident Management
Preventative Maintenance
Ticket Management
Decentralization
Change Management
To speed up propagation in DNS you would switch your _____ to a shorter time frame. To reduce server overhead it.
TTL
Lease duration
DCHP reservation
DNS reservation
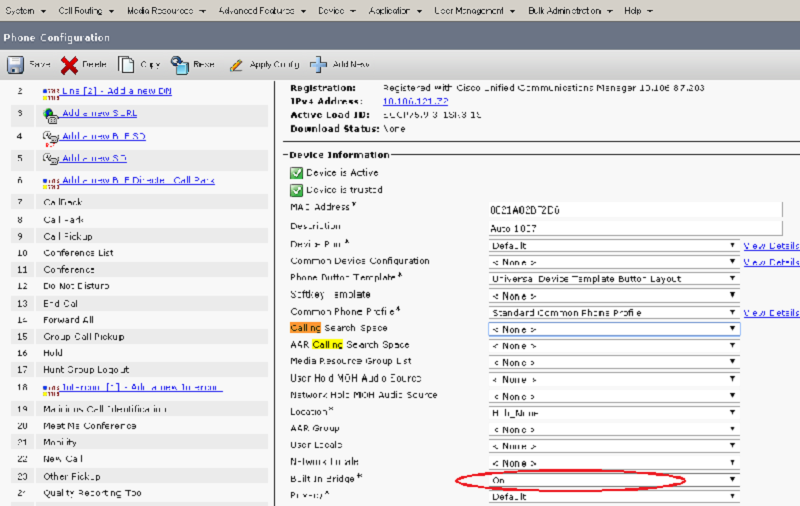
Which management console is being shown?
VSwitch Manager
ACL Editor
Call Manager
VSphere
TRUE OR FALSE: The utilities in the VMware tools software suite enhance the performance of the guest operating system in a virtual machine and management capabilities. Although your operating system can run without it, the functionality of the OS would be substantially reduced.
True
False
________ converts an IP address to a network resource name or URL.
Send Connector
DHCP
Stub Zone
Forward Lookup Zone
Reverse Lookup Zone
TRUE OR FALSE: In the three-component architecture of ACAS, Security Center provides a web interface for administration.
True
False
____________ is a hypervisor that installs directly onto your physical server.
RSAT
HBSS
Active Directory
ESXi
VMWare tools
Which is NOT a module of HBSS?
HIPS
PVS
VSE
DLP
In network administration, what symbol is most commonly used as a wildcard for a single digit between 0 and 9?
I
^
*
%
What is being described?
- Type 1 (native or bare-metal) runs directly on the host's hardware to control the hardware and to manage guest operating systems. Ex: VMware ESXi, Microsoft Hyper-V.
- Type 2 (hosted) runs on conventional operating systems just as other computer programs do, ex: Oracle VM VirtualBox, VMware Workstation Pro
Partition
BIOS
DAG
Active Directory
Hypervisor
-- holds user databases, as well as provides transport services for routing mail and access services that enable client connections.
Mailbox
Edge Transport
Management Tools
-- provides extra security via external antivirus and anti-spam filters.
Mailbox
Edge Transport
Management Tools
-- this option would be used for allowing a different server within your domain the ability to help manage your Exchange organization.
Mailbox
Edge Transport
Management Tools
_______ includes the checking and servicing performed by personnel for maintaining equipment in satisfactory operating condition. This is achieved by accomplishing systematic inspection, detection, and correction of incipient failures either before they occur or before they develop into major defects.
PMCS
Incident / Ticket Management
IG Audit
Change Management
-- Removes PC-specific information from the Windows image, including the PC's security identifier (SID). This allows you to capture the image and apply it to other PCs. This is known as "generalizing the PC".
Error Checking
Hard drive reset
Last Known Good Configuration
Disk Defragmentation
Sysprep
Select all of the following options that are Types of Repositories in ACAS.
Organizational
Host
Offline
Regional
Local
Remote
Corporate
Domain
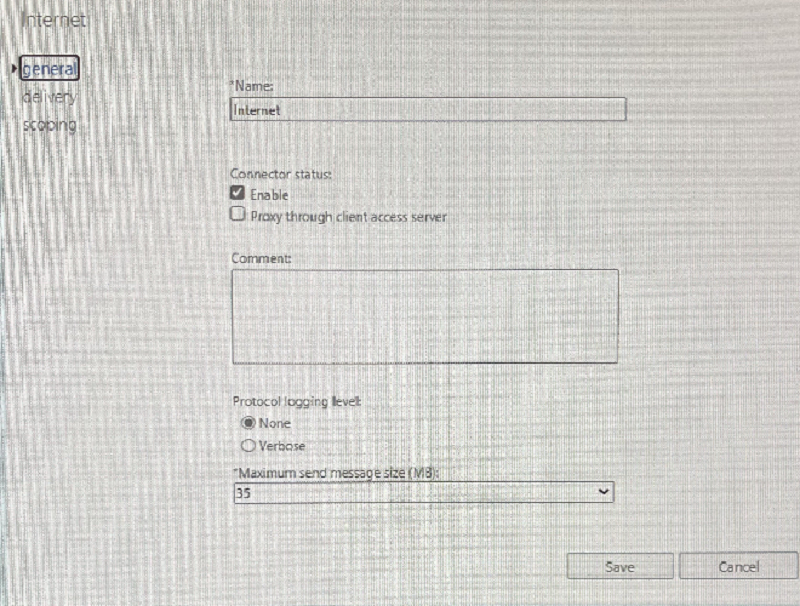
According to the image, what is being configured?
Send Connector
Reverse Lookup Zone
Edge Transport Server
DAG
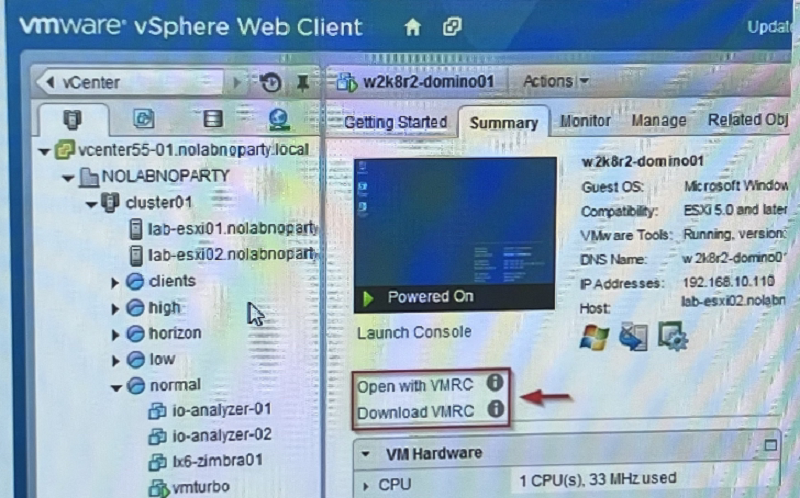
On which of these vSphere objects would ESXi be directly installed on?
Vmturbo
Normal
Lab-esxi2.nola
Cluster01
NOLABNOPARTY
TRUE OR FALSE: vSAN combines multiple physical storage disk drive components into one (or more) logical units. Data is distributed across the drives depending on the required level of redundancy and performance (referred to in terms of "levels")
True
False
TRUE OR FALSE: To apply a GPO to a specific group, both the Read and Write access control entries (ACEs) are required.
True
False
TRUE OR FALSE: Best practice for Universal group use is to add user accounts to Global groups first, then those global groups can be nested within a Universal group.
True
False
Network providing services will typically have some form of service desk to track and resolve network issues. Procedures for operating in a service desk range from someone with a simple hand-held logbook to a large hierarchy with many echelons for routing an issue. Having established procedures for dealing with network problems allows for quicker resolutions through progress tracking, as well as the ability for the end user to stay informed and thusly develop their own contingencies while the problem is being resolved.
Change Management
Incident / Ticket Management
Decentralization
Preventative Maintenance
Which of the following descriptions BEST defines ACAS?
A software set of information security tools used for vulnerability scanning, automated vulnerability scanning and device configuration assessment.
Authenticates and authorizes all users and computers in a Windows domain-type network, assigning and enforcing security policies for all computers and installing or updating software.
Security program used by the DoD with the primary function of providing type-1 encryption to network traffic.
Software security suite based on McAfee's ePO and HIPS.
A _________ is the base component of the Mailbox server high availability and resilience framework built into Microsoft Exchange Server. A _________ consists of up to 16 Mailbox servers that hosts a set of databases and provides automatic database-level recovery from failures that affect individual servers or databases.
PST
EAC
DAG
ExRCA
Which of the following statements DOES NOT describe Virtualization?
The emulation of software using hardware
A simulation upon which other software runs
The use of software to allow a piece of hardware to run multiple operating system images at the same time
Technology that allows for computing environments to be independent of physical infrastructure
TRUE OR FALSE: the primary location of DNS records is within the Forward Lookup Zones folder.
True
False
Which description BEST defines what a domain controller is?
A network server that automatically provides and assigns IP addresses, default gateways and other network parameters to client devices
A server whose primary function is to authenticate and validate users on a network, including group policies, user credentials, and computer names to determine and validate user access
A collection of settings that defines what a system will look like and how it will behave for a defined group of users
Software that creates and runs virtual machines
A _______ zone would be used regarding a location outside our geographical area. It contains a read-only copy of the database file transferred from a Primary Zone (from the other location). This makes the zone data available locally instead of querying the main DNS server across a WAN link. This zone cannot process updates, only retrieve them. Its purpose is to provide fault tolerance and load balancing.
Primary (Master)
Secondary
Stub
DMZ
None of the Above
TRUE or FALSE: In network administration, a physical server is most commonly referred to as a "bridge".
True
False
{"name":"DSSC Written Exam Study Guide", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Test your knowledge and prepare for the DSSC Written Exam with our comprehensive quiz! This engaging and informative quiz covers key concepts in network management, Active Directory, Exchange, and more.Multiple-choice questions to challenge your understandingFocus on practical scenarios for real-world applicationImmediate feedback on your answers","img":"https:/images/course3.png"}
More Quizzes
ITEC MIDTERMS
452231
Principles of Information Security CH1
23120
How Well Do You Know Drqgon?
10511
One quiz
210
Landolt C Test Online - Check Your Visual Acuity Free
201024501
Ready for Marriage: Is Your Boyfriend Ready?
201021233
Addition - Free Basic Math Practice Online
201023171
Ninja Test: Discover Your Inner Warrior - Free
201021613
Community Health Nursing PNLE - Part 3 Free
201021876
My Little Pony Trivia - Test Your MLP Knowledge
201019979
Why Don't People Like Me - Free Self-Assessment
201019874
Dark Souls - Test Your Knowledge (Free Online)
201020085