Sec Test 2
A client computer at 10.10.7.4 is trying to access a Linux server (11.0.1.9) that is running a Tomcat Server application. What TCP dump filter would be best to verify that traffic is reaching the Linux Server eth0 interface?
Tcpdump –i eth0 host 10.10.7.4 and host 11.0.1.9 and port 8080
Tcpdump –i eth0 host 10.10.7.4 and 11.0.1.9
Tcpdump –i eth0 dst 11.0.1.9 and dst port 8080
Tcpdump –i eth0 src 10.10.7.4 and dst 11.0.1.9 and dst port 8080
Which two statements about uRPF are true? (Choose two)
The administrator can configure the allow-default command to force the routing table to use only the default route
In strict mode, only one routing path can be available to reach network devices on a subnet
The administrator can use the show cef interface command to determine whether uRPF is enabled
The administrator can configure the ip verify unicast source reachable-via any command to enable the RPF check to work through HSRP routing groups
It is not supported on the Cisco ASA security appliance
Which three options are fields in a CoA Request code packet? (Choose three)
Length
Calling-station-ID
Authenticator
Acct-session-ID
State
Identifier
When TCP Intercept is enabled in its default mode, how does it react to a SYN request?
It drops the connection
It intercepts the SYN before it reaches the server and responds with a SYN-ACK
It allows the connection without inspection
It monitors the attempted connection and drops it if it fails to establish within 30 seconds
It monitors the sequence of SYN, SYN-ACK, and ACK message until the connection is fully established
Which two options are normal functionalities for ICMP? (Choose two)
Packet filtering
Host detection
Relaying traffic statistics to applications
Path MTU discovery
Router discovery
Port scanning
Which command sequence do you enter to add the host 10.2.1.0 to the CISCO object group?
Object-group network CISCO
Group-object 10.2.1.0
Object network CISCO
Network-object object 10.2.1.0
Object network CISCO
Group-object 10.2.1.0
Object-group network CISCO
Network-object host 10.2.1.0
Which two events can cause a failover event on an active/standby setup? (Choose two)
The stateful failover link fails
The failover link fails
The active unit experiences interface failure above the threshold
The active unit fails
The unit that was previously active recovers.
Within Platform as a Service, Which two components are managed by the customer? (Choose two)
Middleware
Applications
Data
Operating system
Networking
From the list below, which one is the major benefit of AMP Threat GRID?
AMP Threat Grid analyzes suspicious in your network against exactly 400 behavioral indicators
AMP Threat Grid combines Static, and Dynamic Malware analysis with threat intelligence info one combined solution
AMP threat Grid learns ONLY form data you pass on your network and not from anything else to monitor for suspicious behavior. This makes the system much faster and efficient
AMP Threat Grid collects file information from customer servers and run tests on the, to see if they are infected with viruses
Which three statements about PKI on Cisco IOS Software are true? (Choose three)
The match certificate and allow expired-certificate commands are ignored unless the router clock is set
OSCP enables a PKI to use a CRL without time limitations
Different OSCP servers can be configured for different groups of client certificates
OSCP is well-suited for enterprise PKIs in which CRLs expire frequently
Certificate-based ACLs can be configured to allow expired certificates if the peer is otherwise valid
If a certificate-based ACL specifies more than one filed, any one successful filed-to-value test is treated as a match
In which two situations is web authentication appropriate? (Choose two)
When a fallback authentication method is necessary
When 802.1x authentication is required
When WEP encryption must be deployed on a large scale
When devices outside the control of the organization’s It department are permitted to connect to the network
When secure connections to the network are unnecessary
Which two statements about Botnet traffic Filter snooping are true? (Choose two)
It can log and block suspicious connections from previously unknown bad domains and IP addresses
It checks inbound and outbound traffic
It can inspect both IPv4 and IPv6 traffic
It requires the Cisco ASA DNS server to perform DNS lookups
It checks inbound traffic only
It requires DNS packet inspection to be enabled to filter domain names in the dynamic database
Which command on Cisco ASA you can enter to send debug messages to a syslog server?
Logging host
Logging debug-trace
Logging traps
Logging syslog
Which feature does Cisco VSG use to redirect traffic in a Cisco Nexus 1000V Series Switch ?
VPC
VDC
VEM
VPath
Which two statements about ping flood attacks are true? (Choose two)
They attack by sending ping requests to the return address of the network
The use ICMP packets
They attack by sending ping requests to the broadcast address of the network
The attack is intended to overwhelm the CPU of the target victim
They use UDP packets
They use SYN packets
Which best practice can limit inbound TTL expiry attacks?
Setting the TTL value to more than the longest path in the network
Setting the TTL value to zero
Setting the TTL value to less than the longest path in the network
Setting the TTL value equal to the longest path in the network
Which two options are benefits of the Cisco ASA transparent firewall mode? (Choose two)
It can perform dynamic routing
It supports extended ACLs to allow Layer 3 traffic to pass form higher to lower security interfaces
It provides SSL VPN support
It can establish routing adjacencies
It can be added to an existing network without significant reconfiguration
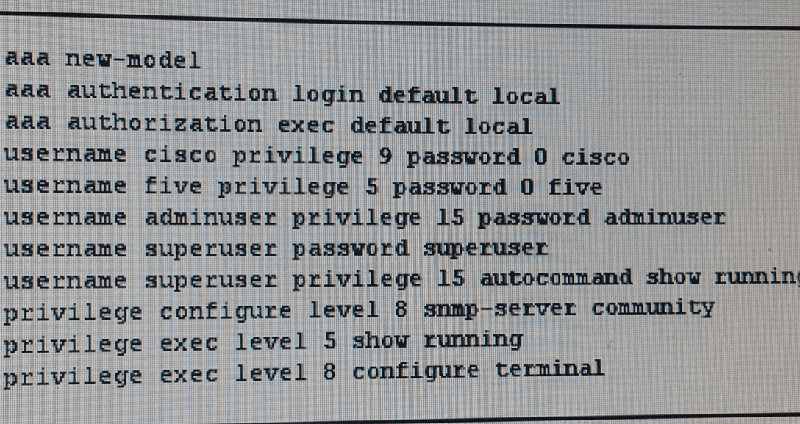
Refer to the exhibit. Which two effects of this configuration are true? (Choose Two)
User five can view usernames and password
User superuser can view the configuration
User superuser can change usernames and passwords
User superuser can view usernames and passwords
User five can execute the show run command
User cisco can view usernames and passwords
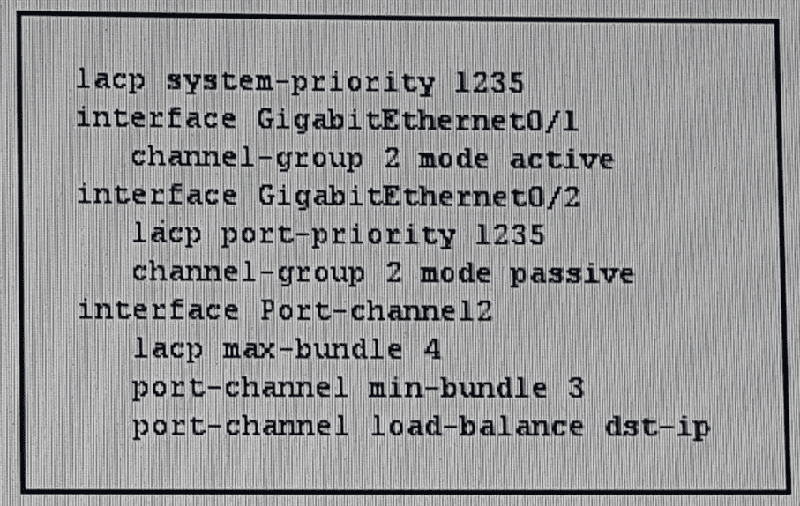
Refer to the exhibit. After you applied this EtherChannel configuration to a Cisco ASA, the EtherChannel failed to come up. Which reason for the problem is the most likely?
The channel-group modes are mismatched
The lacp system-priority and lacp port-priority values are same
The EtherChannel requires three ports, and only two are configured
The EtherChannel is disabled
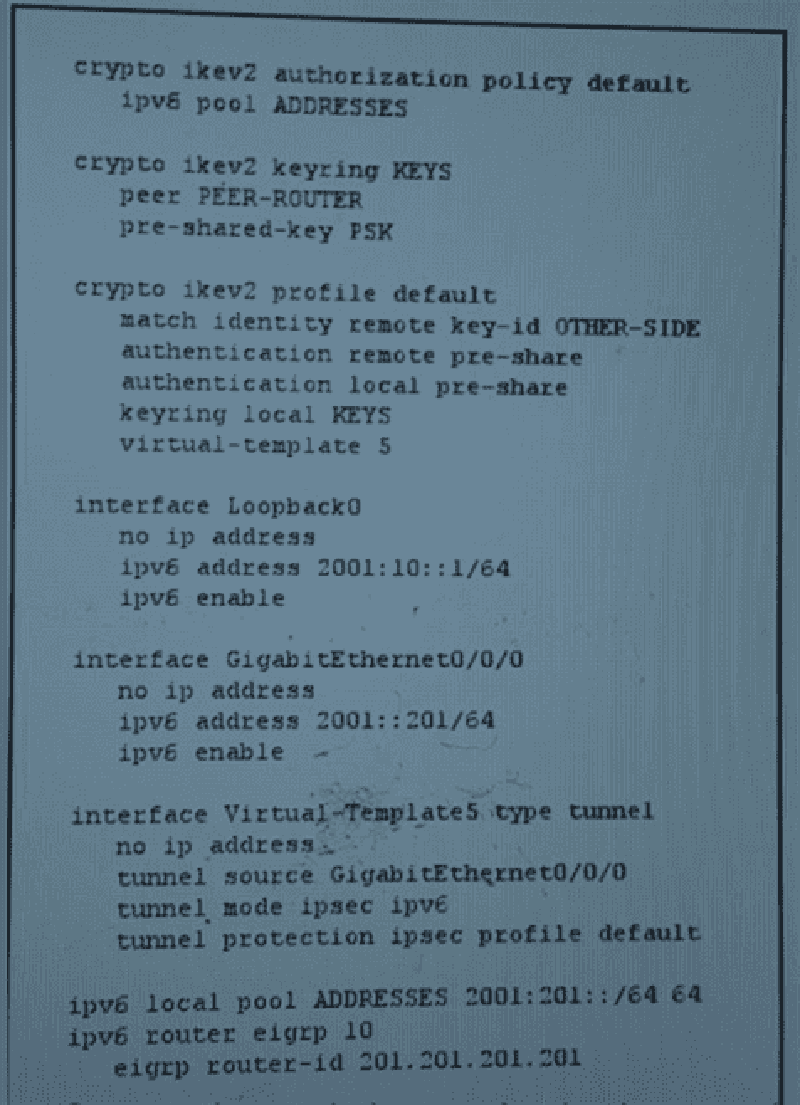
Refer to the exhibit. Which three additional configuration elements must you apply to complete a functional FlexVPN deployment? (Choose three)
0%
0
0%
0
0%
0
0%
0
0%
0
0%
0
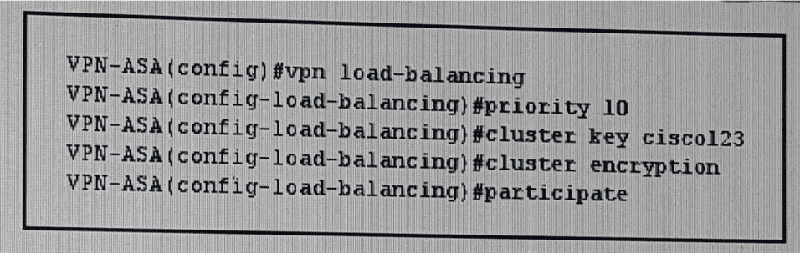
Refer to the exhibit. You applied this VPN cluster configuration to a Cisco ASA and the cluster failed to form. How do you edit the configuration to correct the problem?
Define the maximum allowable number of VPN connections
Define the master/ slave relationship
Enable load balancing
Configure the cluster IP address

Refer to the exhibit. Which effect of this configuration is true?
If the RADIUS server is unreadable, SSH users cannot authenticate
All commands are validate by the RADIUS server before the device executes them
Users accessing the device via SSH and those accessing enable mode are authenticated against the RADIUS server
Users must be in the RADIUS server to access the serial console
Only SSH users are authenticated against the RADIUS server
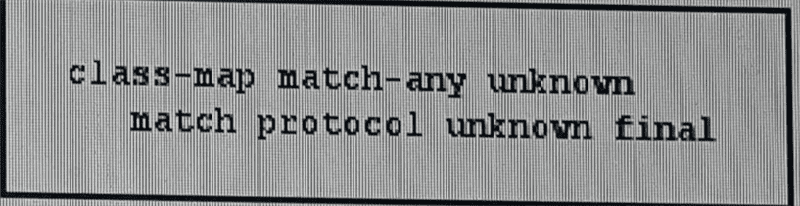
Refer to the exhibit. Which two configurations must you perform to enable the device to use this class map? (Choose two)
Configure PDLM
Configure the ip nbar custom command
Configure the ip nbar protocol discovery command
Configure the transport hierarchy
Configure the DSCP value
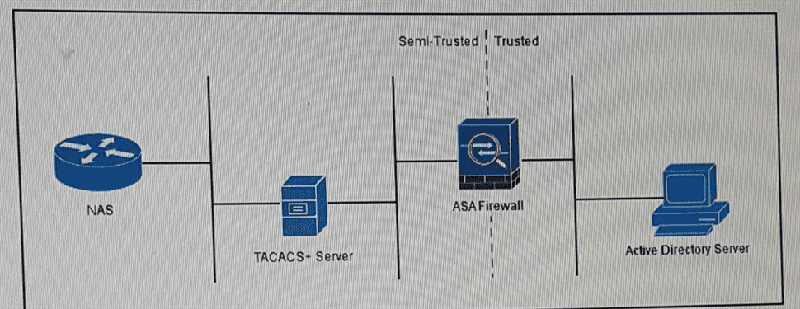
Refer to the exhibit. A user authenticates to the NAS, Which communicates to the TACACS+ server for authentication. The TACACS+ server then accesses the Active Directory Server through the ASA firewall to validate the user credentials which protocol-port pair must be allowed access through the ASA firewall?
DNS over TCP 53
Global catalog over UDP 3268
LDAP over UDP 389
DNS over UDP 53
TACACS+ over TCP 49
SMB over TCP 455
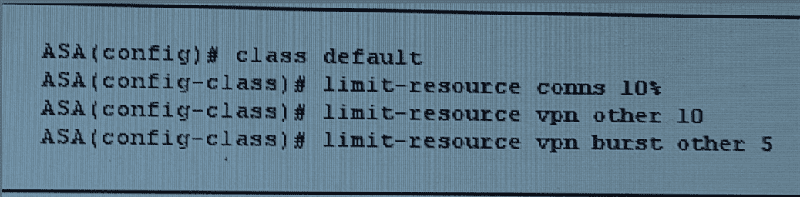
Refer to the exhibit. What is the maximum number of site-to-site VPNs allowed by this configuration?
10
15
Unlimited
5
0
1
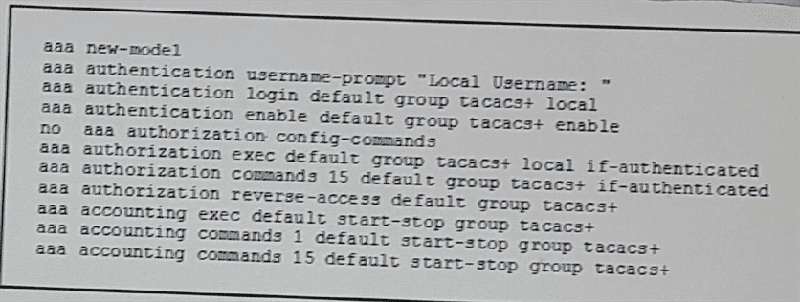
Refer to the exhibit. Which two effects of this configuration are true? (Choose two)
Configuration commands on the router are authorized without checking the TACACS+ server
When a user logs in to privileged EXEC mode, the router will track all user activity
Requests to establish a reverse AUX connection to the router will be authorized against the TACACS+ server
When a user attempts to authenticate on the device, the TACACS+ server will prompt the user to enter the username stored in the router's database
If a user attempts to log in as a level 15 user, the local database will be used for authentication and the TACACS+ will be used for authorization
It configures the router's local database as the backup authentication method for all TTY, console, and aux logins
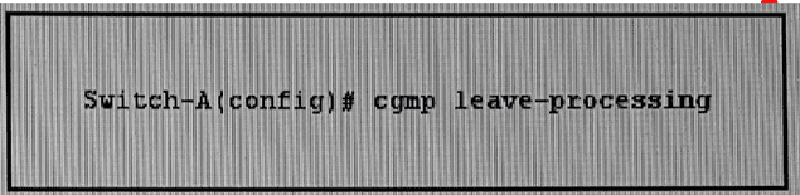
Refer to the exhibit. Which two effects of this configuration are true? (Choose two)
It allows the switch to detect IGMPv2 leave group messages
It optimizes the use of network bandwidth on the LAN segment
IGMPv2 leave group messages are stored in the switch CAM table for faster processing
Host send leave group messages to the Solicited-Node Address multicast address FF02::1:FF00:0000/104
It improves the processing time of CGMP leave messages
Hosts send leave group messages to all-router multicast address when they want to stop receiving data for that group
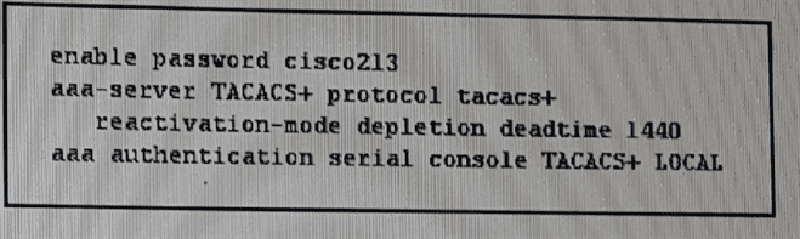
Refer to the exhibit. Which effect of this configuration is true?
Any VPN user with a session time out of 24 hours can access the device
Users attempting to access the console port are authenticated against the TACACS+ server
If the TACACAS+ authentication fails, the ASA uses cisco 123 as its default password
The device tries to reach the server every 24 hours and falls back to the LOCAL database if it fails
The servers in the TACACS+ group0 are reactivated every 1440 seconds
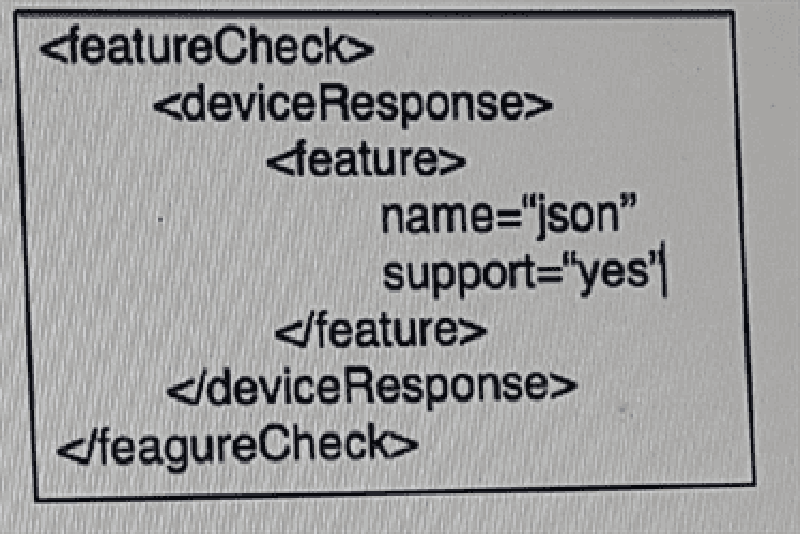
Refer to the exhibit. Which data format is used in this script?
API
JSON
JavaScript
YANG
XML
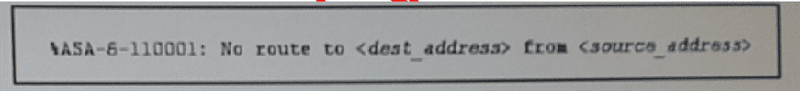
Refer to the exhibit. Which meaning of this error message on a Cisco ASA is true?
The route map redistribution is configured incorrectly
The host is connected directly to the firewall
A packet was denied and dropped by an ACL
The default route is undefined
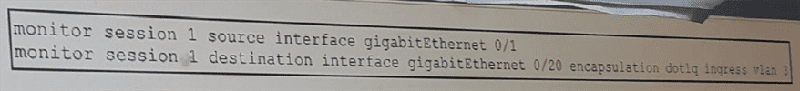
Refer to the exhibit. What are two functionalities of this configuration? (Choose two)
The encapsulation command is used to do deep scan on dot1q encapsulation traffic
Traffic will not be able to pass on gigabitEthernet 0/1
The ingress command is used for an IDS to send a reset on Vlan 3 only
Traffic will only be sent to gigabitEthernt 0/20
Source interface should always be a VLAN
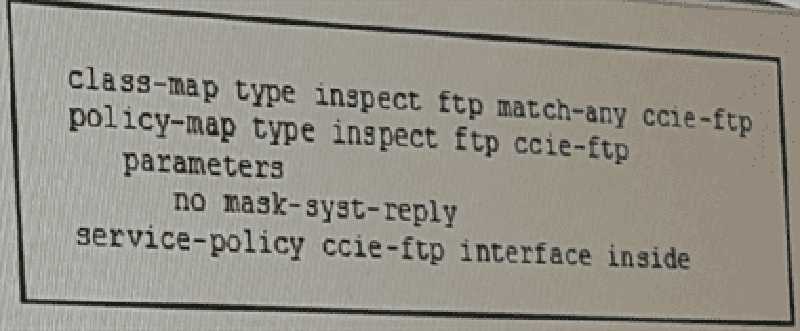
Refer to the exhibit. What are two effects of the given configuration? (Choose two)
The connection will remain open if the PASV reply command includes 5 commas
TCP connections will be completed only to TCP ports from 1 to 1024
FTP clients will be able to determine the server’s system type
The client must always send the PASV reply
E connection will remain open if the size of the STOR command is greater than a fixed constant
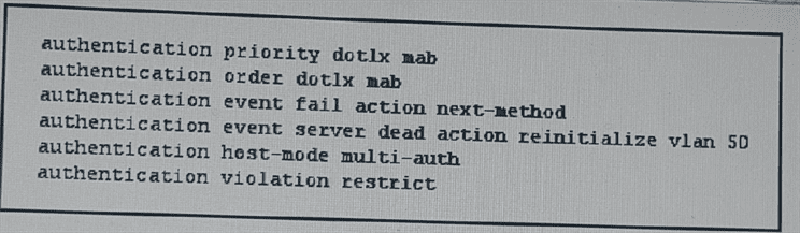
Refer to the exhibit. Which two effects of this configuration are true? (Choose two)
If the TACACS+ server is unreachable, the switch places hosts on critical ports in VLAN 50
The device allows multiple authenticated sessions for a single MAC address in the voice domain
If multiple hosts have authenticated to the same port, each can be in their own assigned VLAN
If the authentication priority is changed the order in which authentication is preformed also changes
The switch periodically sends an EAP-Identity-Request to the endpoint supplicant
The port attempts 802.1x authentication first, and then falls back to MAC authentication bypass

Refer to the exhibit. Which effect of this configuration is true?
A downloadable ACL is applied after an AV pair ACL
For all users, entries in a downloadable ACL are given priority over entries in an AV pair ACL
The downloadable ACL and the AV pair ACL entries are merged together, one ACE at a time
The downloadable ACL and AV pair ACL are merged immediately when the RADIUS server is activated
The downloadable ACL and AV pair ACL are merged after three connection attempts are made to the RADIUS server
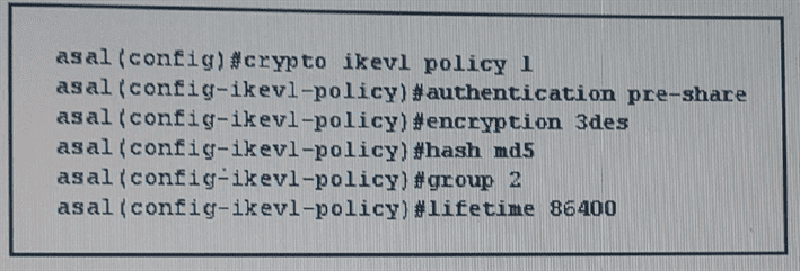
Refer to the exhibit. Which level of encryption is set by this configuration?
56-bit
168-bit
1024-bit
192-bit
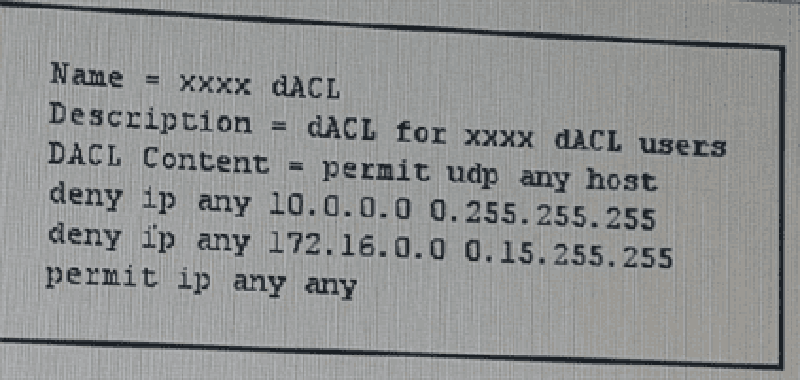
Refer to the exhibit. For which type of user is this downloadable ACL appropriate?
Onsite contractors
Management
Network administrators
Employees
Guest users
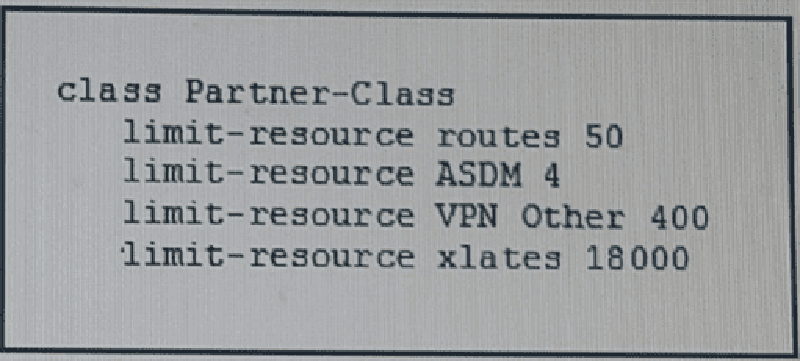
Refer to the exhibit. Which effect of this configuration is true?
It creates a default class
It creates a resource class
It oversubscribes VPN sessions for the given class
It allows each context to use all available resources
Which description of SaaS is true?
A service offering that allowing developers to build their own applications
Service offering a software environment in which applications can be build and deployed
A service offering on-demand licensed applications for end users
A service offering on-demand software downloads
What are two characteristics of RPL, used in loT environments? (Choose two)
It is an Exterior Gateway Protocol
It is a Interior Gateway Protocol
It is a hybrid protocol
It is link-state protocol
It is a distance-vector protocol
Which command is required for bonnet filter on Cisco aASA to function properly
Dynamic-filter inspecttcp/80
Dynamic-filter whitelist
Inspect botnet
Inspect dns dynamic-filter-snoop
Which two statements about Cisco URL Filtering on Cisco IOS Software are true?(Choose Two)
By default, it allows all URLs when the connection to the filtering server is down.
It supports Websense and N2H2 filtering at the same time.
It supports local URL lists and third-party URL filtering servers.
By default, it uses ports 8 and 22.
It supports HTTP and HTTPS traffic.
It requires minimal CPU time.
Which two options are open-source SDN controllers? (Choose two)
OpenContrail
OpenDaylight
Big Cloud Fabric
Virtual Application Networks SDN Controller
Application Policy Infrastructure Controller
Which two statements about DTLS are true? (Choose two)
It uses two simultaneous IPsec tunnels to carry traffic
If DPD is enabled. DTLS can fall back to a TLS connection
It is disabled by default if you enable SSL VPN on the interface
If DTLS is disabled on an interface, then SSL VPN connections must use SSL/TLS tunnels
Because if requires two tunnels, it may experience more latency issues than SSL connections
Which three statements about Dynamic ARP inspection on Cisco switches are true? (Choose three)
The trusted database can be manually configured using the CLI
Dynamic ARP inspection is supported only on access ports
Dynamic ARP inspection does not perform ingress security checking
DHCP snooping is used to dynamically build the trusted database
Dynamic ARP inspection checks ARP packets against the trusted database
Dynamic ARP inspection checks ARP packets on trusted and untrusted ports
Which option is benefit of VRF Selection using Policy-Based Routing for packets to different VPNs?
It increases the router performance when longer subnet masks are in use
It supports more than one VPN per interface
It allows bidirectional traffic flow between the service provider and the CEs
It automatically enables fast switching on all directly connected interfaces
It can use global routing tables to forward packets if the destination address matches the VRF configure on the interface
Every PE router in the service provider MPLS cloud can reach every customer network
Which command is used to enable 802.1x authorizationon an interface?
Authentication port-control auto
Aaa authorization auth-proxy default
Aaa authorization network default group tacacs+
Authentication control-direction both
Authentication open
What are the two most common methods that security auditors use to assess an organization’s security processes? (Choose two)
Social engineering attempts
Penetration testing
Physical observation
Document view
Interviews
Policy assessment
Which two statements about Cisco VSG are true? (Choose two)
It uses optional IP-to-virtual machine mappings to simplify management of virtual machines
According to Cisco best practices, the VSG should use the same VLAN for VSM-VEM control traffic and management traffic
It has built-in intelligence for redirecting traffic and fast-path offload.
Because it is deployed at layer 2, It can be inserted without significant reengineering of the network .
It can be integrated with VMWarevCenter to provide transparent provisioning of policies and profiles.
It uses the Cisco VSG user agent to register with the Cisco Prime Network Services Controller
Which two statements about NVGRE are true? (Choose two)
It allows a virtual machine to retain its MAC and IP addresses when it is moved to different hypervisor on a different L3 network
The virtual machines reside on a single virtual network regardless of their physical location
NVGRE endpoints can reside within a virtual machine
The network switch handles the addition and removal of NVGRE encapsulation
It supports up to 32 million virtual segments per instance
Which three statements about RLDP are true? (Choose three )
It detects rouge access points that are connected to the wired network
It can detect rouge APs operating only on 5 GHz
It can detect rouge APs that use WPA encryption
It can detect rouge APs that use WEP encryption
Active Rouge containment can be initiated manually against rouge devices detected on the wired network
The AP is unable to serve clients while the RLDP process is active
{"name":"Sec Test 2", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"What are the two different modes in which Private AMP cloud can be deployed? (Choose two), Which three commands can you use to configure VXLAN on a Cisco ASA firewall?(Choose three), Which Cisco ISE profiler service probe can collect information about Cisco Discovery Protocol?","img":"https://cdn.poll-maker.com/24-940394/screen-shot-2017-12-29-at-8-02-56-pm.png?sz=1200-00531000000887505300"}
More Quizzes
Which Raven Cycle Character Are You
10514
100
THE 1940s
1059
C2 Marketing - HỆ THỐNG THÔNG TIN VÀ NGHIÊN CỨU MARKETING
1780
Free Dyslexia: Test Your Knowledge & Debunk Myths
201029254
Free AP World Hist: Industrial Revolution
201025214
Think You Know Your Voice? Take This Free Voice Type Test!
201030264
Business Law Test: Free - Prove Your Knowledge
201030985
Which The Bear Character Are You? Discover Your TV Match
201025673
Which Nickname Suits You Best? Discover Yours Free!
201034816
Advanced Jazz Saxophone
15819914
Elec Music Techniques II
15828026