Qz02
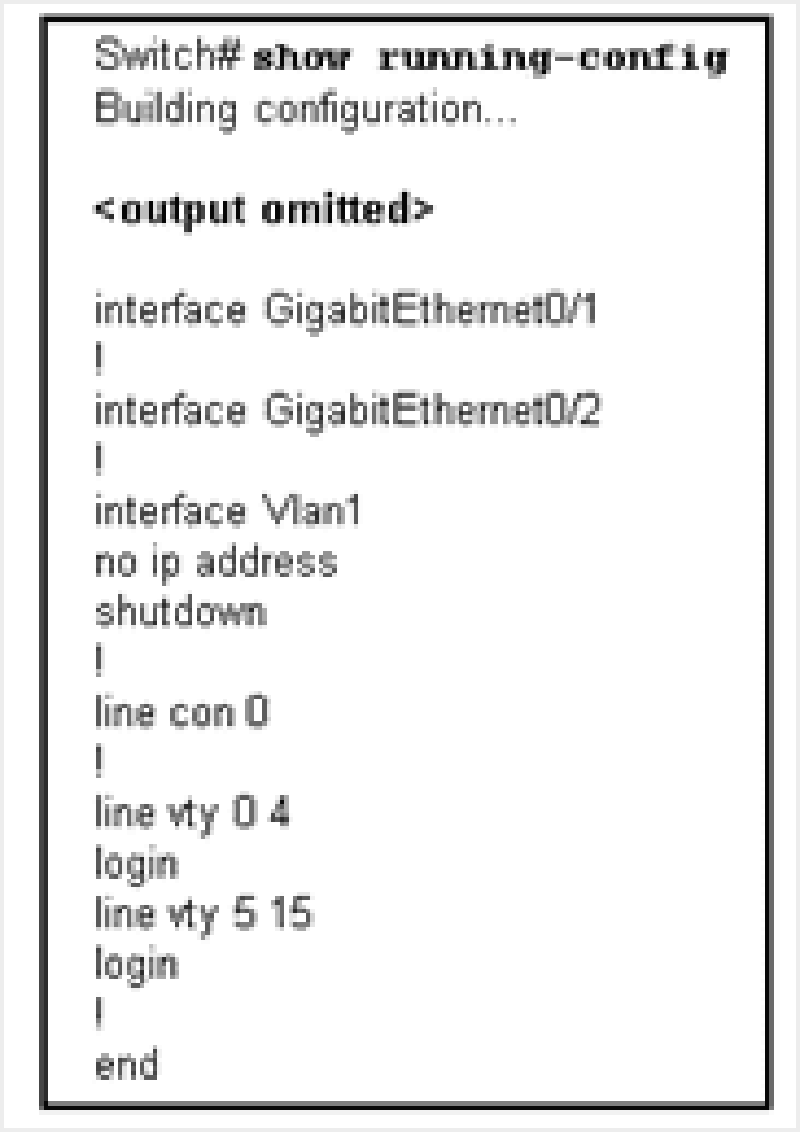
{"name":"Qz02", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Refer to the exhibit. What can be determined from the partial output of the show running-config command?, What are two ways to make a switch less vulnerable to attacks like MAC address flooding, CDP attacks, and Telnet attacks? (Choose two.), A network administrator plugs a new PC into a switch port. The LED for that port changes to solid green. What statement best describes the current status of the port?","img":"https://cdn.poll-maker.com/11-495290/qz0201.png?sz=1200"}
More Quizzes
Nathan is a homewrecker
10512
Gfggfg
320
Simulacro: Auxiliar Administrativo del Estado
111560
Computer Applications in Management
221166
Hardest Real Estate Exams by State - Free Online
201029274
MCQ Test - Free Practice Online
201021287
Manual Software Testing - Free QA Knowledge Check
201024405
OSI Model - Free Networking Basics Practice
201026139
Roman Architecture: Arches, Keystone & Lintels
201022636
Which Ivy League Should I Go To? Free College Fit
201020459
Which Scenario Best Explains Scarcity? Free Economics
201018498
Multiplication Table - Free Times Tables Practice
201018849