ISM
Why is it important for organizations to implement a backup solution in a data center environment?
Minimize the cost of data protection
Reduce redundant data in a production environment
Improve the integrity of critical data
Ensure the availability of production data
What is a key objective to performing continuous replication?
Reduce the deduplication ratio
Avoid performing data archiving
Avoid performing data backups
Reduce the RPO to near-zero
What accurately describes a software-defined architecture?
Supports only central management of private cloud resources using a pre-defined policy
Provides decentralized, manual, and policy-drive IT resource management
Uses only converged and hyperconverged infrastructures to offer services to companies
Provides a unified management platform for centralized monitoring and administration
Which layer of the OSI model provides the functional and procedural methods to transfer data between network entities?
Application
Session
Presentation
Data link
Which technology combines NAND flash memory into a hard disk drive and is a single, integrated device incorporating both types of storage?
Solid-state hybrid drive
Dual drive
Solid-state drive
Fibre Channel drive
A Fibre Channel switch has eight ports and all ports must be operational 24×7. However, a failure of Port 5 occurs on a particular week as follows: • Monday = 11 AM to 12 PM • Thursday = 7 AM to 11 AM • Saturday = 11 AM to 1 PM What is the availability of Port 5 in that week?
93%
94.1%
97%
95.8%
What is an accurate statement about stretched VLANs?
Requires a change in the VMs' IP addresses to match the addressing scheme at the other sites.
Reduces network bandwidth requirements during VM migration across sites.
Supports migration of VMs across sites without the need to change their network configurations.
Enables automatic modification of VLAN addresses during VM migration across sites.
Which file system uses a MapReduce framework to run applications and a NameNode for managing the file?
Network File System (NFS)
New Technology File System (NTFS)
Common Internet File System (CIFS)
Hadoop Distributed File System (HDFS)
A company's Finance department needs 200 GB of storage for their business applications. A LUN is created with 200 GB and RAID 1 is configured to support the applications. If the cost of storage per GB is $2, what is the chargeback cost to the department for the application storage?
$200
$400
$800
$1500
A company plans to deploy a new application in their environment. The new application requires 2 TB of storage space. During peak workloads, the application is expected to generate 4500 IOPS with a typical I/O size of 4 KB. The capacity of each available disk drive is 250 GB. In addition, the maximum number of IOPS a drive can perform at with a 70% utilization is 90 IOPS. What is the minimum number of disk drives needed to meet the application's capacity and performance requirements for a RAID 0 configuration?
40
70
8
50
Which parameters define information availability in an IT environment?
Capacity, Availability, and Performance
Confidentiality, Integrity, and Availability
Reliability, Accessibility, and Timeliness
Reliability, Integrity, and Performance
Which technology uses the concept that real-life objects can independently share and process information with minimal human interaction?
Deep Learning
Internet of Things
Cloud Computing
Artificial Intelligence
Which functionality does a Control layer provide in a software-defined networking architecture?
Defining the network behavior through various policies.
Making decisions on how the packets should be forwarded.
Forwarding data packets based on the requirements from the Application layer.
Establishing communications between the Infrastructure and Interface layers.
Which state change notifications (SCNs) are issued by an iSNS server to the registered devices?
CPU events
Output events
Input events
Network events
In the event of a disk failure, which RAID level enables quick data reconstruction?
RAID 6
RAID 5
RAID 3
RAID 10
What is a function of the metadata service in an object-based storage device (OSD)?
Manages both physical and logical disks on which the user data is stored.
Manages the storage space for all remote clients.
Maintains the object IDs and file system namespace mappings.
Generates the file system namespace from the file contents.
An Ethernet switch has eight ports and all ports must be operational for 24 hours, from Monday through Friday. However, a failure of Port4 occurs as follows: • Monday = 8 PM to 9 PM • Wednesday 7 PM to 9 PM • Thursday = 6 AM to 9 AM • Saturday = 4 PM to 7 PM What is the MTTR of Port 4?
3 hours
2 hours
28 hours
38 hours
What is an advantage of deploying a purpose-built, disk-based backup appliance in a data center environment?
Lower the recovery time objective of an organization.
Eliminate the need for performing source-based deduplication.
Retain the fixed content for longer periods in the data center.
Convert the capital expenditure to an operational expenditure.
Which data archiving component scans primary storage to find the files that meet the archiving policy?
Archive storage
Archive agent
Archive stub file
Archive database server
When using a bridged iSCSI connection, which components facilitate communication between gateways?
Compute system with iSCSI ports and the storage system with only FC ports.
Compute system with FCoE ports and the storage system with iSCSI ports.
Compute system with iSCSI ports and the storage system with Ethernet ports.
Compute system with FC HBA ports and the storage system with only FC ports.
Why is it important for organizations to store, protect, and manage their data?
Reduce the amount of data to be replicated, migrated, and backed up.
Develop new business opportunities by leveraging existing data.
Rapidly develop and deploy modern applications for business improvement.
Reduce the complexity in managing the data center environment.
Which Dell EMC product is a hyper-scale storage infrastructure that provides universal accessibility with support for object and HDFS?
PowerMax
ViPR Controller
Isilon
Elastic Cloud Storage
What is a characteristic of the Orchestration layer in a modern data center architecture?
Interacts directly with physical components across layers to begin provisioning tasks
Enables automated arrangement, coordination, and management of resource provisioning tasks
Allows centralized, automated, and policy-driven management of heterogeneous resources
Enables automatic updates of offerings listed in the service catalog with pre-defined workflows
What is a key advantage of implementing FCIP?
Ensures lossless transmission of FC traffic across data centers over Ethernet.
Enables migration of VMs across data centers by using existing FC networks.
Provides a disaster recovery solution by replicating data across data centers.
Provides a dedicated network for transmission of storage traffic within a data center.
A company is planning to perform a cloud-based backup. They want to send their data over a public network to a cloud backup device. Which security control mechanism helps to protect the data from an attacker?
Demilitarized zone
Data shredding
Multi-factor authentication
Encryption
Which compute system component enables dynamic extension of file system capacity and efficient storage management?
Virtual Memory Manager
Logical Unit Number Masking
Logical Unit Number
Logical Volume Manager
Which data deduplication method increases the probability of identifying duplicate data even when there is only a minor difference between two documents?
Single-instance
File-level
Object-level
Variable-length segment
Which file system uses only UNIX systems for a client-server application protocol and Remote Procedure Call (RPC) for file sharing?
Hadoop Distributed File System (HDFS)
Common Internet File System (CIFS)
Network File System (NFS)
New Technology File System (NTFS)
In an FCoE switch, which function is provided by the Fibre Channel Forwarder (FCF)?
Communication bridge between CEE and IP networks
Communication bridge between CEE and FCIP networks
Communication bridge between FC and FCIP networks
Communication bridge between CEE and FC networks
What is a key advantage of cloning a virtual machine (VM)?
Improves the performance of an existing VM and new VMs.
Ability to run new VMs simultaneously with the same IP address.
Eliminates the need to create multiple snapshots for a VM.
Reduces the time required to create multiple copies of a VM.
Which VMware product has pre-defined workflows that helps to automate and coordinate the service delivery and operational functions in a storage infrastructure?
Horizon
NSX
VRealize Orchestrator
VSphere ESXI
What accurately describes an iSCSI HBA?
Requires a software adapter with built-in functionality
Performs both iSCSI and TCP/IP processing
Requires CPU cycles for TCP/IP processing
Enables transmission of data through iSCSI tunneling
What does an area ID represent in Fibre Channel (FC) addressing?
Port within a group
Group of switches
Group of switch ports
Switch within a group
Which layer contains services that define network behavior through policies and resource requirements in a software-defined networking architecture?
Infrastructure
Application
Interface
Control
When using the erasure coding technique in an object-based storage system, data is divided into 12 data segments and 4 coding segments. What is the maximum number of disk drive failures against which data is protected by the configuration?
3
8
4
12
What accurately describes an Incident in a storage infrastructure?
Unknown root cause of one or more disruptions to service.
Any event that may lead to the disruption of a service.
Any event that may create a change in correcting a known error.
Support request to help access an IT resource.
What accurately describes hypervisor-based continuous data protection?
Journal is stored in a virtual machine.
Virtual appliance is running on a hypervisor.
Virtual appliance runs on a storage system.
Replica volumes are created in the hypervisor.
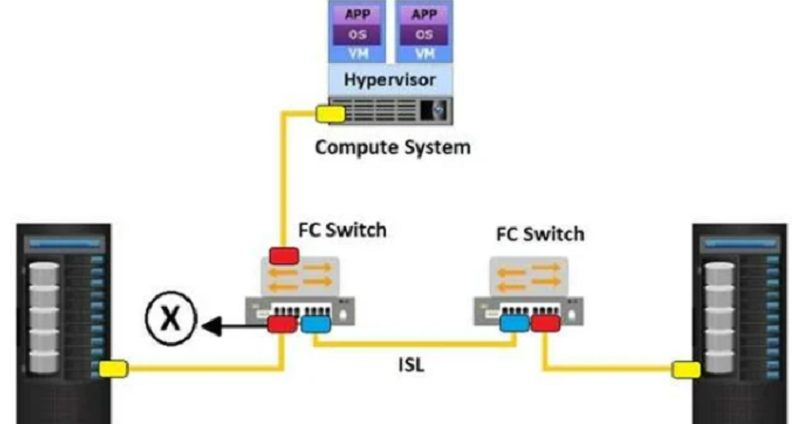
What does the "X" represent in the exhibit?
N_port
NL_port
E_port
F_port
What happens when the size of a write port exceeds the configured write aside size in a block- based storage system?
Write data is lost and a re-write request is sent to the compute system
Write aside size is automatically reconfigured to the new write I/O size
Warning message to reduce the size of write I/O is displayed
Cache is bypassed and I/O is written directly to storage
42) Which Dell EMC product is a software-defined storage platform that abstracts, pools, and automates a data center’s physical storage infrastructure?
PowerMax
VxFlex OS
XtremIO
ViPR Controller
Which product provides an organization with the power to search and analyze vast amounts of data in one place and helps administrators to discover suspicious event trends?
VMware AppDefense
VMware AirWatch
Dell Charge Auditor
Dell Intrust
Which exhibit represents a Type 2 hypervisor?
0%
0
0%
0
0%
0
0%
0
What is a key benefit for performing local replication?
Provide disaster recovery as a service offering
Reduce the time to perform data backups
Enable operational recovery of data if there is a data loss
Enable data recovery in the event of a site-level disaster
In an SDS environment, which protocol supports the resource-oriented architecture for the development of scalable and lightweight web applications while adhering to a set of constraints?
NFS
FTP
REST
CIFS
An organization wants to use an application for their business communication. However, they do not have the skills or the time to deploy and manage an application in-house. Which recommended cloud service model will meet their requirement?
Infrastructure as a Service
Software as a Service
Platform as a Service
Database as a Service
Which cloud deployment model allows provisioning of a cloud infrastructure only for use by a single organization having multiple consumers?
Private cloud
Public cloud
Multi-cloud
Hybrid Cloud
What accurately describes the scale-out storage architecture?
Provides the capability to maximize its capacity by adding nodes to the cluster.
Provides a fixed capacity ceiling that limits scalability beyond a storage system.
Restricts scalability to the limits of the storage controllers.
Scales the capacity only within a single storage system.
Which Dell EMC product provides a software-defined platform that supports both block and file storage services?
Xtremio
FAST VP
PowerMax
VPLEX
Which product delivers virtualized or hosted desktops and applications through a single platform?
VMware Horizon
Dell EMC VxRail Appliance
VMware NSX
Dell PowerEdge servers
A backup administrator has defined a backup policy. The policy requires full backups to be performed at 10 PM every Sunday and incremental backups performed at 10 PM the remaining days. If files were accidentally deleted Wednesday morning, how many backup copies are required to restore the files?
3
4
2
5
What is an advantage of implementing file-level virtualization in a data center environment?
Provides non-disruptive file mobility across file servers or NAS devices.
Provides dynamic distribution of files across NAS clients.
Provides the capability to access files from any device.
Provides automated scaling of file systems across NAS servers.
Which Dell EMC product creates a server and IP-based SAN from direct-attached server storage to deliver flexible and scalable performance and capacity on demand?
ViPR Controller
VxFlex OS
PowerMax
XtremIO
What is a benefit of link aggregation?
Saves bandwidth by restricting traffic to a specific potentially congested ISL.
Improves ISL utilization by increasing the network traffic on a specific ISL.
Optimizes fabric performance by distributing network traffic across ISLs.
Yields a higher throughput by combining two parallel ISLs into a single physical ISL.
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events. Which IDPS technique uses a database that contains known attack patterns?
Role-based
Signature-based
Profile-based
Anomaly-based
What is the objective of security control?
Maximize the attack surfaces and maximize the attack vector
Minimize the attack surfaces and minimize the work factors
Maximize the attack surfaces and minimize the attack vector
Minimize the attack surfaces and maximize the work factors
Which functionality is provided by a process login in a Fibre Channel (FC) SAN environment?
Establishes a connection to the fabric between an N_port and an F_port
Exchange ULP-related parameters between two N_ports
Exchanges service relevant parameters between an N_port and an F_port
Establishes a session that occurs between two E_ports
What is an accurate statement about a virtual SAN (VSAN)?
Events causing traffic disruptions in one VSAN are propagated to other VSANs
Each VSAN has its own fabric services, configuration, and set of FC addresses
Nodes that are present in different VSANs should not have the same FC address
Every VSAN created on a physical SAN must have the same fabric configuration
Which Internet of Things (IoT) component is responsible for the automation of operations by applying a force based on the dynamics of data?
Sensor
Gateway
Switch
Actuator
In a compute-based storage area network (SAN), what is a function of the metadata manager?
Provides an interface to the software-defined storage controller.
Controls all data read and write operations in a compute-based SAN.
Performs the I/O operations on the local storage of a compute system as requested by a client.
Holds cluster-wide mapping information and load balancing in a compute-based SAN.
Which security mechanism ensures secure access to internal assets while enabling Internet-based access to selected resources?
Virtual local area network
Virtual private network
Demilitarized zone
Discovery domain
In an archiving environment, how is a content address created in a content addressable storage (CAS) system to store an object?
By using the physical address of the storage device.
From the binary representation of an object.
From the metadata of an object.
By using the logical address of the memory space.
What is the goal of a business continuity solution?
Reduce the amount of investment in protecting an organization's business-related data.
Ensure information availability that is required to conduct vital business operations.
Avoid a disaster in a data protection environment to control the loss of data.
Eliminate security threats in a data protection environment for continuous access to data.
Which management function involves configuring LUN masking to restrict hosts from accessing a specific LUN in a data center environment?
Performance management
Change management
Configuration management
Security management
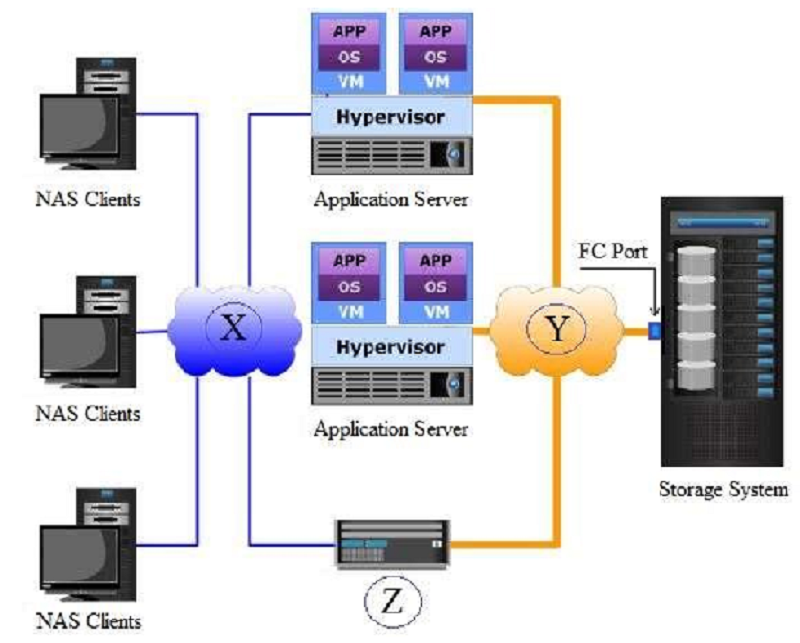
Based on the exhibit, what does the "X", "Y", and "Z" represent in a NAS environment?
X = IP Network, Y = FC SAN, and Z = NAS Gateway
X = FC SAN, Y = IP Network, and Z = NAS Gateway
X = FC SAN, Y = NAS Gateway, and Z= IP Network
X = IP Network, Y = NAS Gateway, and Z = FC SAN
Which technology decouples the OS, applications, and user state from a physical compute system?
Storage virtualization
Desktop virtualization
Thin client virtualization
Application virtualization
What accurately describes virtual SAN (VSAN) trunking?
Increases the number of E_ports used for the ISLs to transfer multiple VSAN traffic.
Reduces the utilization of ISLs by removing all the ISLs configured between the FC switches.
Increases the complexity of managing the FC SAN with an increase in the number of ISLs.
Reduces the number of ISLs between switches that are configured with multiple VSANs.
What is an accurate statement about Governance?
Authorize policy-making decisions
Restrict access to certain users
Ensure removal of security risks
Demonstrate adherence to polices
What is a benefit of using an existing IP-based network infrastructure for storage connectivity?
Ensure security by allowing only localized data movement
Provide a dedicated network for storage
Provide the ability to extend the network over long distances
Ensure lossless transmission of FC traffic over Ethernet
Which Converged Network Adapter (CNA) component encapsulates Fibre Channel (FC) frames into Ethernet frames?
Fibre Channel Forwarder
Fibre Channel HBA
PCIe Bus
FCoE ASIC
Why are organizations moving towards a modern data center implementation?
Deploy only unified and converged IT resources to reduce the management complexity.
Ability to be agile, operate in real time, and develop intelligent products.
Reduce the cost of managing data center components by using a self-service catalog.
Develop modern applications in the public cloud without having the right skill set in-house.
What is an impact of a Denial-of-Service attack?
Computing resources are exhausted and made unavailable to users
User’s accounts and data are compromised by malicious insiders
Privileges are intentionally misused to compromise data security
User’s credentials are eavesdropped by the attacker
Which exhibit represents a Type 1 hypervisor?
0%
0
0%
0
0%
0
0%
0
Why is it important to deploy virtual machine (VM) storage migration in a data center environment?
Reduce a company’s overall storage system capacity requirements
Improve the security of applications running inside VMs on the migrated storage system
Enable efficient management of storage capacity across storage systems
Enable VMs to continue functioning even if the source data is lost due to a failure
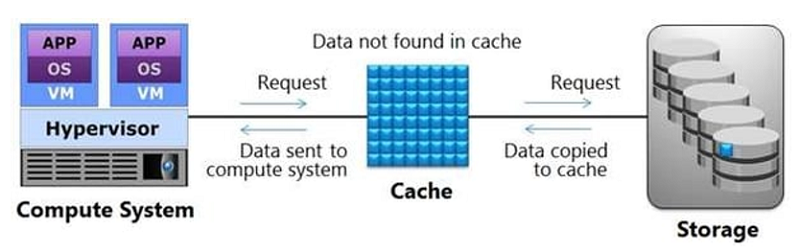
Which operation is represented in the exhibit?
Write-through Cache
Write-back Cache
Read Cache Miss
Read Cache Hit
Which product enables employees to enroll their mobile devices in an enterprise environment and ensures secure access from the devices to the enterprise resources?
Dell PowerEdge
Dell InTrust
VMware AirWatch
VMware AppDefense
In a Fibre Channel (FC) protocol stack, what is the function of the FC-2 layer?
Provides standards for the physical interface, media, and transmission of bits
Provides transmission words, primitive signals, and link initialization
Provides application interfaces and maps several protocols to FC layers
Provides FC addressing, structure, and organization of data
If a company has experienced a passive attack on its IT infrastructure, how is the company's security impacted?
Information privacy is compromised.
Data is altered by an unauthorized user.
Availability of data is affected
Access to services is denied.
When implementing a full mesh topology in a Fibre Channel (FC) SAN environment, what is the effect when there is an increase in the number of switches?
Reduces the available node ports for ISL connectivity.
Reduces the available switch ports for node connectivity.
Increases the hop count for compute to storage traffic.
Increases the load on the ISLs due to traffic aggregation.
What is an accurate statement about variable prefetching?
Many blocks that have recently been written to storage by the compute system are retrieved and placed in cache
Storage system prefetches many non-contiguous blocks of data, with varied sizes, from cache.
Many non-contiguous blocks that are not currently required can be retrieved from cache in advance.
Storage system prefetches data in multiples of the original I/O request size from the compute system.
What is an example of a Performance Management task?
Selecting an appropriate RAID type for a storage pool.
Scanning applications and databases to identify vulnerabilities.
Removing unused resources from a service and reassigning them to another.
Planning and architecting data backup and replication solutions.
Which Dell EMC product enables continuous protection for any PIT recovery and offers multi-site support?
SourceOne
SRDF
Avamar
RecoverPoint
A company has virtualized their data center and wants to deploy a recovery-in-place backup approach. What is the advantage of this type of approach?
Eliminates the need to transfer the image from the backup device to the primary storage before it is restarted.
Acquires backup services through a self-service portal
Reduces the recovery point objective to restore the data to any previous point-in-time using backed up VMs
Eliminates the backup impact on the application servers
Why is it important for organizations to implement a multi-site remote replication solution?
Perform synchronous replication with low network bandwidth
Recover data to any point-in-time in the event of a remote site failure
Provide consistent near-zero RPO in the event of source and remote site failures
Ensure data protection is always available if there are any single site failures
What accurately describes a shared pool in virtual provisioning?
Should contain only homogeneous disk drive types.
Supports a single RAID protection level.
Consists of only a virtual storage volume.
Should contain only physical drives with different sizes.
Which technology is used in the media and entertainment industry to enable content-based search activity and to create video subtitles using natural language processing?
Machine learning
Social networking
Cloud computing
Internet of things
A company wants to implement a Fibre Channel (FC) SAN topology. The implementation will involve deploying four switches for localized compute and storage system connectivity. In addition, to meet their applications’ performance requirements, they need a maximum of one ISL and redundant connections for their compute to storage traffic. Which topology should be recommended?
Full mesh topology
Partial mesh topology
Single-switch topology
Bus topology
Why is it important for organization to deploy intelligent storage systems in their data centers?
Reduce the complexity of managing information by creating silos of storage
Reduce the amount of data to be replicated, migrated, and backed up
Effectively migrate data from a data center to the cloud at no cost
Effectively store and manage information across data centers
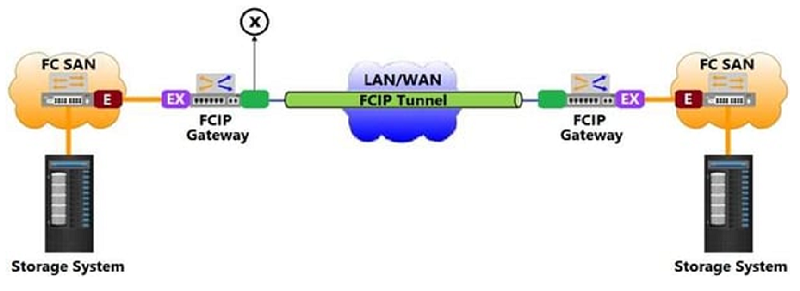
Based on the exhibit, what does the "X" represent in the FCIP tunnel configuration?
EX_port
VE_port
VX_port
F_port
A consumer is interested in a service that provides multiple operating systems and programming frameworks for application development and deployment. Which recommended cloud service model will meet these requirements?
Platform as a Service
Storage as a Service
Software as a Service
Infrastructure as a Service
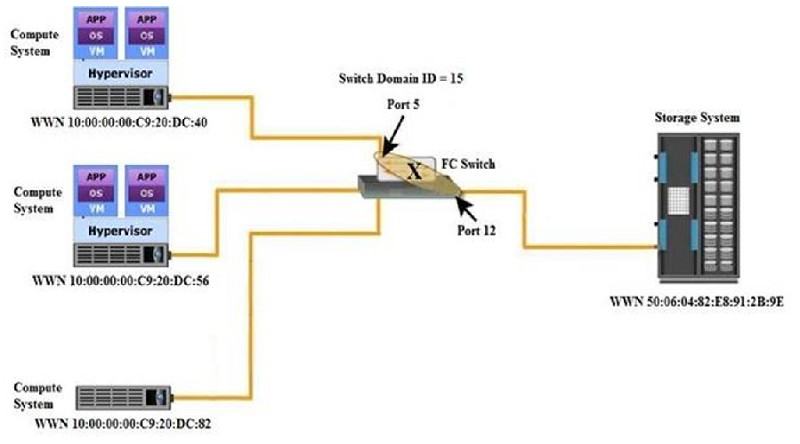
Which type of zoning does the "X" represent?
Fabric zoning
Mixed zoning
Port zoning
WWN zoning
What accurately describes an object-based storage device (OSD)?
Objects are created based on the name and location of the file
Objects exist at the same level in the address space
Numerous objects can be stored in a single namespace
One object can be placed inside another object
An Ethernet switch has eight ports and all ports must be operational for 24 hours; from Monday through Friday. However, a failure of Port 5 occurs as follows: - Tuesday = 6 AM to 7 AM - Thursday = 5 PM to 9 PM - Friday = 8 AM to 9 AM What is the MTBF of Port 5?
38 hours
30 hours
40 hours
32 hours
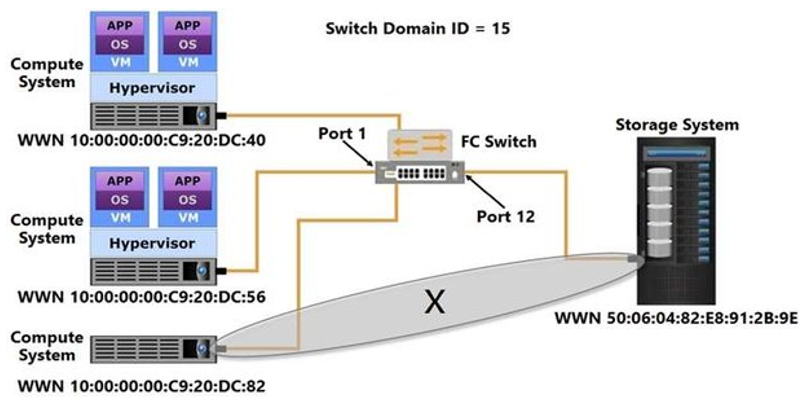
104) Which type of zoning does the "X” represent?
Fabric zoning
Mixed zoning
Port zoning
WWN zoning
What is determined by the amount of space configured for the journal in continuous data protection (CDP) replication?
Amount of space the source and replica volumes require
Amount of data that can be restored to a specific point
Length of time the recovery points can go back
Length of time required to recover the data
A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 2 occurs on a particular week as follows: - Monday = 10 AM to 12 PM - Wednesday = 4 PM to 9 PM - Thursday = 4 PM to 7 PM - Friday = 3 PM to 6 PM - Saturday = 9 AM to 1 PM What is the availability of Port 2 in that week?
80%
71.6%
78.3%
70%
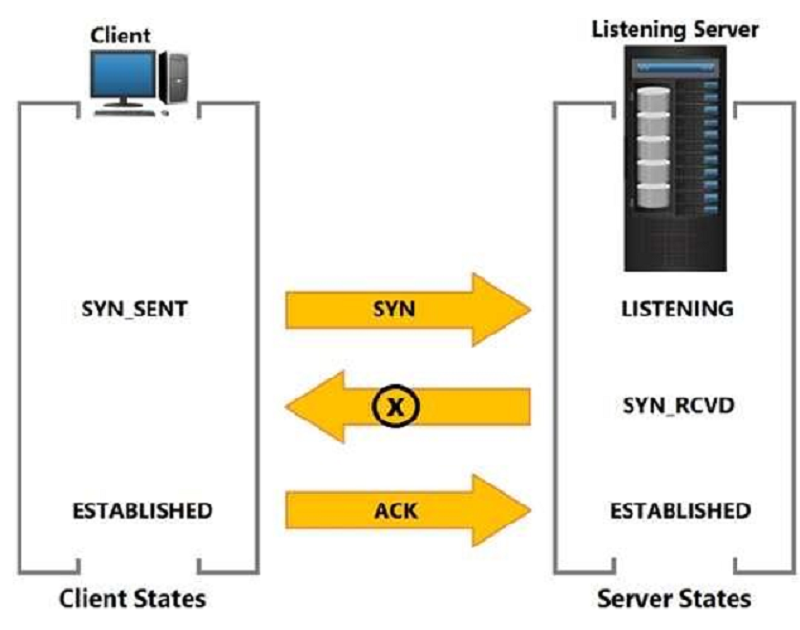
Based on the exhibit, what does the "X” represent?
SYN ACK
ACK SYN
SYN NACK
NACK SYN
What does the "variability” characteristic of big data signify?
Diversity in the formats and types of data generated from various sources
Importance in obtaining the right information from data at all possible contexts
Importance in the quality of data gathered from a number of sources
Cost-effectiveness and business value obtained from massive volumes of data
What is an accurate statement about scale-out NAS?
Supports only data replication for protecting data
Pools node resources in a cluster to work as multiple NAS devices
Creates a different file system for each node in the cluster
Stripes data across nodes with mirror or parity protection
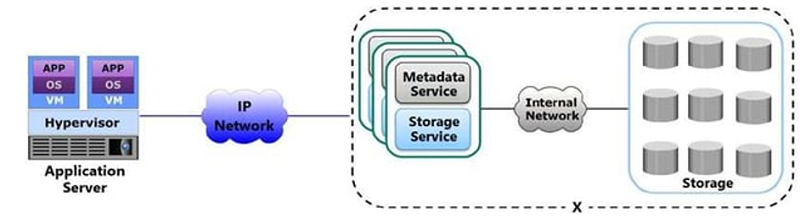
Based on the exhibit, which type of storage device does the "X” represent?
Unified-based
File-based
Block-based
Object-based
What creates a large-scale SAN without storage systems and uses local storage of existing compute systems?
Software-defined network
Storage-based SAN
Compute-based SAN
Software-defined compute
A company plans to deploy a new application in their environment. The new application requires 5 TB of storage space. During peak workloads, the application is expected to generate 3000 IOPS with a typical I/O size of 3 KB. The capacity of each available disk drive is 750 GB. In addition, the maximum number of IOPS a drive can perform at with a 70% utilization is 90 IOPS. What is the minimum number of disk drives needed to meet the application’s capacity and performance requirements for a RAID 0 configuration?
40
7
34
50
In a RAID 6 array with four disks, what is the total usable data storage capacity on the array if the disk size is 200 GB?
200 GB
600 GB
800 GB
400 GB
Which Dell EMC product is a disk-based backup and recovery solution that provides inherent source-based deduplication?
Data Domain
SRDF
Avamar
TimeFinder
What is an accurate statement about Storage Class Memory (SCM)?
SCM can be addressed at the bit or word level
SCM has volatile memory
SCM read and write speeds are slower than flash
SCM is faster than DRAM
What is the primary advantage of RAID 6 compared to RAID 5?
Low rebuild time for data
High available storage capacity
Low write penalty
High resiliency
An organization plans to deploy a deduplication solution in ther data center environment. They are concerned about the application servers performance and a long backup window during backups. However, they want to retain ther existing backup application. Which deduplication solution(s) should be recommended?
Target-base deduplication
Source-based with variable-length deduplication
Source-based with fixed-length block deduplication
Source-based global deduplication
Why is it important for organizations to deploy business continuity solutions in their data center environment?
Avoid security risks that destroys the business data
Employ compliance requirements for data protection
Eliminate the time required for maintenance of IT resources in the data center
Reduce the cost of protecting data within and outside data centers
In a NAS environment, which file system provides a public or open variation of the Server Message Block (SMB) protocol and uses the TCP/IP protocol?
Commem Internet File System (CIFS)
New Technology File System (NTFS)
Network File System (NFS)
Hadoop Distributed File System (HDFS)
What is a function of a continuous data protection (CDP) appliance?
Migrates deduplicated data from the source volume to the target volume during replication
Manages both local and remote replications within and across data centers
Stores all data that has changed from the time the replication session started
Intercepts writes to the production volume and splits each write into two copies
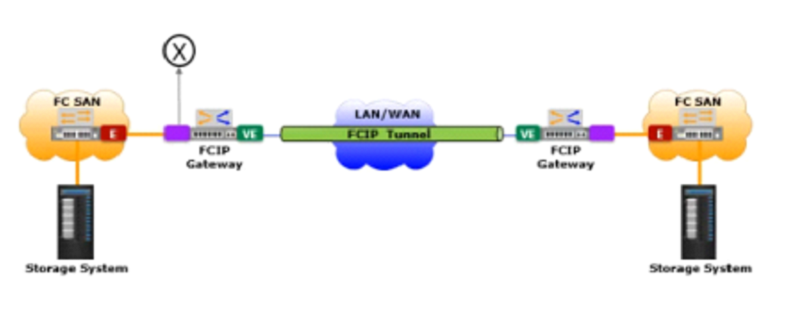
Based on the exhibit, what does the 'X' represent in the FCIP tunnel configuration?
E_port
EX_port
F_port
VE_port
{"name":"ISM", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Why is it important for organizations to implement a backup solution in a data center environment?, What is a key objective to performing continuous replication?, What accurately describes a software-defined architecture?","img":"https://www.quiz-maker.com/3012/CDN/75-3469507/1.png?sz=1200-00000000281000005300"}
More Quizzes
Gk
320
Lets see who won the quiz
100
Semana 1 - ION 1 e ION 2
1160
Quotes
1588
Free Planning Permission Knowledge Test
201024582
Free America Story of Us WWII Worksheet
201022858
Fun Mathzes for Adults: Test Your Skills Now!
201025011
Which Cimorelli Band Member Are You? Personality
201033867
Test Your Astros Trivia: Ultimate Houston Astros
201023776
First Communion Test Questions: Ultimate Eucharist
201083490
Ace Your Arizona Food Handlers Practice Test - Free
201038654
Free Music vs Crypto Identification
201028946