Microsoft 70-697 Practice Test (newly added)
A company has client computers that run Windows 10. The client computer systems frequently use IPSec tunnels to securely transmit data. You need to configure the IPSec tunnels to use 256-bit encryption keys. Which encryption type should you use?
3DES
DES
RSA
AES
You administer a group of 10 client computers that run Windows 10. The client computers are members of a local workgroup. Employees log on to the client computers by using their Microsoft accounts. The company plans to use Windows BitLocker Drive Encryption. You need to back up the BitLocker recovery key. Which two options can you use? (Each correct answer presents a complete solution. Choose two.)
Save the recovery key to a file on the BitLocker-encrypted drive.
Save the recovery key in the Credential Store.
Save the recovery key to OneDrive.
Print the recovery key.
You are using sysprep to prepare a system for imaging. You want to reset the security ID (SID) and clear the event logs. Which option should you use?
/generalize
/oobe
/audit
/unattend
Group Policy is a set of rules which control the working environment of user accounts and computer accounts. Group Policy provides the centralized management and configuration of operating systems, applications and users’ settings in an Active Directory environment. In other words, Group Policy in part controls what users can and can’t do on a computer system. Which one of these policies requires a reboot?
Turn off Windows Defender
Turn off Autoplay for non-volume devices
Disable Active Desktop
Turn off Data Execution Prevention for Explorer
Which term is used to refer to installing apps directly to a device without going through the Windows Store?
SQL Injection
BranchCache
DLL Hijack
Sideloading
You have a desktop computer that runs Windows 8 Enterprise. You add three new 3-terabyte disks. You need to create a new 9-terabyte volume. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
From Disk Management, create a new spanned volume.
From Disk Management, convert all of the 3-terabyte disks to GPT.
From PowerShell, run the New-VirtualDisk cmdlet.
From Disk Management, bring all disks offline.
From Diskpart, run the Convert MBR command.
From PowerShell, run the Add-PhysicalDisk cmdlet.
At home, you use a Windows 10 desktop computer. At work, you use a Windows 10 laptop that is connected to a corporate network. You use the same Microsoft account to log on to both computers. You have a folder with some personal documents on your desktop computer. The folder must be available and synced between both computers. You need to ensure that the latest version of these files is available. What should you do?
Create a folder by using OneDrive for Windows. Move all of the personal documents to the new folder.
Move the folder to the Libraries folder. Go to PC Settings. Under Sync your settings, enable App settings.
Right-click the folder and click Properties. Under Security, provide Full Control for the Microsoft account.
Right-click the folder and select Share With, and then select Homegroup (view and edit).
You have 100 client Windows 10 computers. Users are NOT configured as local administrators. You need to prevent the users from running applications that they downloaded from the Internet, unless the applications are signed by a trusted publisher. What should you configure in the Security settings from the Action Center?
Virus protection
User Account Control
Windows SmartScreen settings
Network Access Protection
You are a systems administrator of a small branch office. Computers in the office are joined to a Windows 8 HomeGroup. The HomeGroup includes one shared printer and several shared folders. You join a new computer to the HomeGroup and try to access the HomeGroup shared folders. You discover that the shared folders are unavailable, and you receive an error message that indicates the password is incorrect. You need to reconfigure the new computer in order to access the HomeGroup resources. What should you do?
Adjust the time settings on the new computer to match the time settings of the HomeGroup computers.
Change the HomeGroup password and re-enter it on the computers of all members of the HomeGroup.
Change the default sharing configuration for the shared folders on the HomeGroup computers.
Reset your account password to match the HomeGroup password.
Your network contains an Active Directory domain. The domain contains 100 Windows 10 client computers. All of the computers secure al connections to computers on the internal network by using IPSec. The network contains a server that runs a legacy application. The server does NOT support IPSec. You need to ensure that some of the Windows 8 computers can connect to the legacy server. The solution must ensure that all other connections are secured by using IPSec. What should you do?
Modify the settings of the Domain Profile.
Create a connection security rule.
Create an inbound firewall rule.
Modify the settings of the Private Profile,
You administer laptop and desktop computers that run Windows 8 Pro. Your company uses Active Directory Domain Services (AD DS) and Active Directory Certificate Services (AD CS). Your company decides that access to the company network for all users must be controlled by two-factor authentication. You need to configure the computers to meet this requirement. What should you do?
Install smart card readers on all computers. Issue smart cards to all users.
Enable the Password must meet complexity requirements policy setting. Instruct users to log on by using the domain \username format for their username and their strong password.
Create an Internet Protocol security (IPsec) policy that requires the use of Kerberos to authenticate all traffic. Apply the IPsec policy to the domain.
Issue photo identification to all users. Instruct all users to set up and use PIN Logon.
QUESTION 48 Your network contains an Active Directory domain and 100 Windows 10 client computers. All software is deployed by using Microsoft Application Virtualization (App-V) 5.0. Users are NOT configured as local administrators, Your company purchases a subscription to Microsoft Office 365 that includes Office 365 ProPlus. You need to create an App-V package for Office 365 ProPlus. What should you do?
Run the Office Customization Tool (OCT), run the App-V Sequencer and then run Setup /Packager.
Download the Office Deployment Tool for Click-to-Run, run the App-V Sequencer and then run Setup /Ad mm.
Download the Office Deployment Tool for Click-to-Run, run Setup /Download and then run Setup /Packager.
Run the Office Customization Tool (OCT), run Setup /Download and then run the App-V Sequencer
You administer computers that run Windows 8 Enterprise and are members of an Active Directory domain. Some volumes on the computers are encrypted with BitLocker. The BitLocker recovery passwords are stored in Active Directory. A user forgets the BitLocker password to local drive E: and is unable to access the protected volume. You need to provide a BitLocker recovery key to unlock the protected volume. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
Ask the user to run the manage-bde-protectors-disable e: command.
Ask the user for his or her logon name.
Ask the user to run the manage-bde-unlock E:-pw command.
Ask the user for his or her computer name.
Ask the user for a recovery key ID for the protected drive.
You are a systems administrator for your company. The company has employees who work remotely by using a virtual private network (VPN) connection from their computers, which run Windows 8 Pro. These employees use an application to access the company intranet database servers. The company recently decided to distribute the latest version of the application through using a public cloud. Some users report that every time they try to download the application by using Internet Explorer, they receive a warning message that indicates the application could harm their computer. You need to recommend a solution that prevents this warning message from appearing, without compromising the security protection of the computers. What should you do?
Publish the application through a public file transfer protocol (FTP) site.
Publish the application through an intranet web site.
Instruct employees to disable the SmartScreen Filter from within the Internet Explorer settings.
Publish the application to Windows Store.
Your network contains an Active Directory domain. The domain contains 100 Windows 10 client computers. All of the computers secure al connections to computers on the internal network by using IPSec. The network contains a server that runs a legacy application. The server does NOT support IPSec. You need to ensure that some of the Windows 8 computers can connect to the legacy server. The solution must ensure that all other connections are secured by using IPSec. What should you do?
Modify the settings of the Domain Profile
Create a connection security rule
Create an inbound firewall rule
Modify the settings of the Private Profile
You administer computers that run Windows 8 Enterprise in an Active Directory domain in a single Active Directory Site. All user account objects in Active Directory have the Manager attribute populated. The company has purchased a subscription to Windows Intune. The domain security groups are synchronized with the Microsoft Online directory. You create a Windows Intune group that specifies a manager as a membership criterion. You notice that the group has no members. You need to ensure that users that meet the membership criteria are added to the Windows Intune group. What should you do?
Force Active Directory replication within the domain.
Ensure that all user accounts are identified as synchronized users.
Ensure that the user who is performing the search has been synchronized with the Microsoft Online directory.
Synchronize the Active Directory Domain Service (AD DS) with the Microsoft Online directory.
You have a Windows 8.1 Enterprise client computer named Computer1. The Storage Spaces settings of Computer1 are configured as shown in the following exhibit. (Click the Exhibit button.) You plan to create a three-way mirror storage space in the storage pool and to set the size of the storage space to 50 GB. You need to identify the minimum number of disks that must be added to the storage poo! For the planned mirror. How many disks should you identify?
Gratis-54

1
3
4
5
Your company has Windows 10 client computers. All of the computers are managed by using Windows Intune. You need to provide a user with the ability to deploy software to the computers by using Windows Intune. The solution must minimize the number of permissions assigned to the user. Which role should you use?
User management administrator from the Windows Intune account portal
Global administrator from the Windows Intune account portal
Service administrator from the Windows Intune administrator console
Service administrator from the Windows Intune account portal
Your company has a main office and two branch offices named Branch1 and Branch2. The main office contains a file server named Server1 that has BranchCache enabled. Branch1 contains a server named Server2 that is configured as a hosted cache server. All client computers run Windows 8 Enterprise. All of the computers are joined to an Active Directory domain. The BranchCache settings of all the computers are configured as shown in the following exhibit. (Click the Exhibit button.) In the table below, identify the effective setting for the client computers in each branch office. Make one selection in each column. Each correct selection is worth one point.
Gratis-B12

Branch1 Computers will:
Not use BranchCache
Retrieve cached content from peers
Retrieve cached content from Server1
Retrieve cached content from Server2
Your company has a main office and two branch offices named Branch1 and Branch2. The main office contains a file server named Server1 that has BranchCache enabled. Branch1 contains a server named Server2 that is configured as a hosted cache server. All client computers run Windows 8 Enterprise. All of the computers are joined to an Active Directory domain. The BranchCache settings of all the computers are configured as shown in the following exhibit. (Click the Exhibit button.) In the table below, identify the effective setting for the client computers in each branch office. Make one selection in each column. Each correct selection is worth one point.
Gratis-B12

Branch2 Computers will:
Not use BranchCache
Retrieve cached content from peers
Retrieve cached content from Server1
Retrieve cached content from Server2
You provide support for a small company. The company purchases a Windows 10 laptop for an employee who travels often. The company wants to use BitLocker to secure the hard drive for the laptop in case it is lost or stolen. While attempting to enable BitLocker, you receive the error message shown in the following image:
Gratis-B12(1)

A supported configuration for BitLocker is possible on this laptop:
Yes
No
You administer computers that run Windows 8. The computers on your network are produced by various manufacturers and often require custom drivers.
You need to design a recovery solution that allows the repair of any of the computers by using a Windows Recovery Environment (WinRE).
In which order should you perform the actions?
Gratis-RickB30
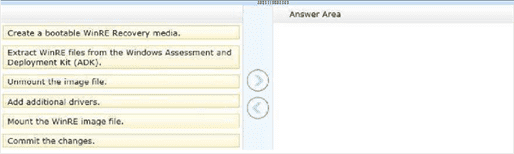
Step 1:
Create a bootable WinRE Recovery media.
Extract WinRE files from the Windows Assessment and Deployment Kit (ADK).
Unmount the image file.
Add additional drivers.
Mount the WinRE image file.
Commit the changes.
You administer computers that run Windows 8. The computers on your network are produced by various manufacturers and often require custom drivers.
You need to design a recovery solution that allows the repair of any of the computers by using a Windows Recovery Environment (WinRE).
In which order should you perform the actions?
Gratis-RickB30

Step 2:
Create a bootable WinRE Recovery media.
Extract WinRE files from the Windows Assessment and Deployment Kit (ADK).
Unmount the image file.
Add additional drivers.
Mount the WinRE image file.
Commit the changes.
You administer computers that run Windows 8. The computers on your network are produced by various manufacturers and often require custom drivers.
You need to design a recovery solution that allows the repair of any of the computers by using a Windows Recovery Environment (WinRE).
In which order should you perform the actions?
Gratis-RickB30

Step 3:
Create a bootable WinRE Recovery media.
Extract WinRE files from the Windows Assessment and Deployment Kit (ADK).
Unmount the image file.
Add additional drivers.
Mount the WinRE image file.
Commit the changes.
You administer computers that run Windows 8. The computers on your network are produced by various manufacturers and often require custom drivers.
You need to design a recovery solution that allows the repair of any of the computers by using a Windows Recovery Environment (WinRE).
In which order should you perform the actions?
Gratis-RickB30

Step 4:
Create a bootable WinRE Recovery media.
Extract WinRE files from the Windows Assessment and Deployment Kit (ADK).
Unmount the image file.
Add additional drivers.
Mount the WinRE image file.
Commit the changes.
You administer computers that run Windows 8. The computers on your network are produced by various manufacturers and often require custom drivers.
You need to design a recovery solution that allows the repair of any of the computers by using a Windows Recovery Environment (WinRE).
In which order should you perform the actions?
Gratis-RickB30

Step 5:
Create a bootable WinRE Recovery media.
Extract WinRE files from the Windows Assessment and Deployment Kit (ADK).
Unmount the image file.
Add additional drivers.
Mount the WinRE image file.
Commit the changes.
You administer computers that run Windows 8. The computers on your network are produced by various manufacturers and often require custom drivers.
You need to design a recovery solution that allows the repair of any of the computers by using a Windows Recovery Environment (WinRE).
In which order should you perform the actions?
Gratis-RickB30

Step 6:
Create a bootable WinRE Recovery media.
Extract WinRE files from the Windows Assessment and Deployment Kit (ADK).
Unmount the image file.
Add additional drivers.
Mount the WinRE image file.
Commit the changes.
You manage Microsoft Intune for a company named Contoso. You have 200 computers that run Windows 10. The computers are Intune clients. You need to configure software updates for the clients.
Which policy template should you use to configure each software updates setting? To answer, drag the appropriate policy templates to the correct settings. Each policy template may be used once, more than once, or not at all.
Gratis-14

Require automatic updates:
Microsoft Intune Agent Settings
Windows Configuration Policy
Windows Custom Policy (Windows 10 and Windows 10 Mobile)
You manage Microsoft Intune for a company named Contoso. You have 200 computers that run Windows 10. The computers are Intune clients. You need to configure software updates for the clients.
Which policy template should you use to configure each software updates setting? To answer, drag the appropriate policy templates to the correct settings. Each policy template may be used once, more than once, or not at all.
Gratis-14

Minimum classification of updates to install automatically:
Microsoft Intune Agent Settings
Windows Configuration Policy
Windows Custom Policy (Windows 10 and Windows 10 Mobile)
You manage Microsoft Intune for a company named Contoso. You have 200 computers that run Windows 10. The computers are Intune clients. You need to configure software updates for the clients.
Which policy template should you use to configure each software updates setting? To answer, drag the appropriate policy templates to the correct settings. Each policy template may be used once, more than once, or not at all.
Gratis-14

Allow immediate installation of updates that do not interrupt Windows:
Microsoft Intune Agent Settings
Windows Configuration Policy
Windows Custom Policy (Windows 10 and Windows 10 Mobile)
You support desktop computers for a company named Fabrikam, Inc. The computers are members of the Active Directory domain named fabrikam.com.
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.
You need to configure the computers to allow Fabrikam users to access the Contoso website without any warning prompts. You also need to use the fewest certificates possible.
Which certificate or certificates should you use?
Gratis-20
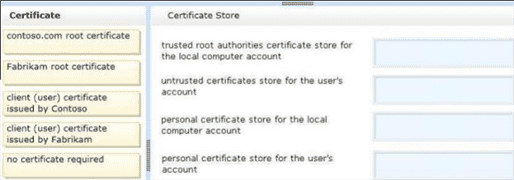
trusted root authorities certificate store for the local computer account:
Contoso.com root certificate
No certificate required
Fabrikam root certificate
Client (user) certificate issued by Contoso
Client (user) certificate issued by Fabrikam
You support desktop computers for a company named Fabrikam, Inc. The computers are members of the Active Directory domain named fabrikam.com.
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.
You need to configure the computers to allow Fabrikam users to access the Contoso website without any warning prompts. You also need to use the fewest certificates possible.
Which certificate or certificates should you use?
Gratis-20

untrusted certificates store for the user's account:
Contoso.com root certificate
No certificate required
Fabrikam root certificate
Client (user) certificate issued by Contoso
Client (user) certificate issued by Fabrikam
You support desktop computers for a company named Fabrikam, Inc. The computers are members of the Active Directory domain named fabrikam.com.
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.
You need to configure the computers to allow Fabrikam users to access the Contoso website without any warning prompts. You also need to use the fewest certificates possible.
Which certificate or certificates should you use?
Gratis-20

personal certificate store for the local computer account:
Contoso.com root certificate
No certificate required
Fabrikam root certificate
Client (user) certificate issued by Contoso
Client (user) certificate issued by Fabrikam
You support desktop computers for a company named Fabrikam, Inc. The computers are members of the Active Directory domain named fabrikam.com.
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication.
You need to configure the computers to allow Fabrikam users to access the Contoso website without any warning prompts. You also need to use the fewest certificates possible.
Which certificate or certificates should you use?
Gratis-20

personal certificate store for the user's account:
Contoso.com root certificate
No certificate required
Fabrikam root certificate
Client (user) certificate issued by Contoso
Client (user) certificate issued by Fabrikam
You administer Windows 10 Enterprise computers. Your company has a team of technical writers that is preparing technical manuals and help files. The team manager wants to ensure that the technical writers are able to restore any documents that been modified within the last year. You need to ensure that the technical writers can restore Microsoft Word files to any previous versions for up to one year. Which three actions should you perform in sequence?
Gratis-22

Step 1:
Create a network share, configure NTFS, and then share permissions.
Turn on System Protection and create a restore point.
Turn on File History.
Configure the Keep Saved Versions setting.
You administer Windows 10 Enterprise computers. Your company has a team of technical writers that is preparing technical manuals and help files. The team manager wants to ensure that the technical writers are able to restore any documents that been modified within the last year. You need to ensure that the technical writers can restore Microsoft Word files to any previous versions for up to one year. Which three actions should you perform in sequence?
Gratis-22

Step 2:
Create a network share, configure NTFS, and then share permissions.
Turn on System Protection and create a restore point.
Turn on File History.
Configure the Keep Saved Versions setting.
You administer Windows 10 Enterprise computers. Your company has a team of technical writers that is preparing technical manuals and help files. The team manager wants to ensure that the technical writers are able to restore any documents that been modified within the last year. You need to ensure that the technical writers can restore Microsoft Word files to any previous versions for up to one year. Which three actions should you perform in sequence?
Gratis-22

Step 3:
Create a network share, configure NTFS, and then share permissions.
Turn on System Protection and create a restore point.
Turn on File History.
Configure the Keep Saved Versions setting.
You manage update compliance for Windows 10 desktop computers that are part of a domain. You need to configure new desktops to automatically receive updates from an intranet resource that you manage. Which three actions should you perform in sequence?
Gratis-23
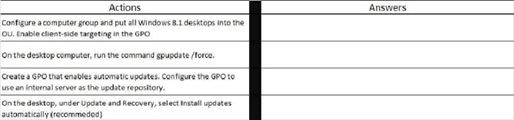
Step 1:
Configure a computer group and put all Windows 8.1 desktops into the OU. Enable client-side targeting in the GPO.
On the desktop computer, run the command gpupdate/force.
Create a GPO that enables automatic updates. Configure the GPO to use an internal server as the update repository.
On the desktop, under the Update and Recovery, select Install updates automatically (recommended).
You manage update compliance for Windows 10 desktop computers that are part of a domain. You need to configure new desktops to automatically receive updates from an intranet resource that you manage. Which three actions should you perform in sequence?
Gratis-23

Step 2:
Configure a computer group and put all Windows 8.1 desktops into the OU. Enable client-side targeting in the GPO.
On the desktop computer, run the command gpupdate/force.
Create a GPO that enables automatic updates. Configure the GPO to use an internal server as the update repository.
On the desktop, under the Update and Recovery, select Install updates automatically (recommended).
You manage update compliance for Windows 10 desktop computers that are part of a domain. You need to configure new desktops to automatically receive updates from an intranet resource that you manage. Which three actions should you perform in sequence?
Gratis-23

Step 3:
Configure a computer group and put all Windows 8.1 desktops into the OU. Enable client-side targeting in the GPO.
On the desktop computer, run the command gpupdate/force.
Create a GPO that enables automatic updates. Configure the GPO to use an internal server as the update repository.
On the desktop, under the Update and Recovery, select Install updates automatically (recommended).
You work for a small company that uses Windows 10 computers. The computers are joined to a homegroup. You want to share an existing folder named Research. It is located in the Documents folder. You need to give users the ability to change the files in this folder. Which three actions should you perform in sequence?
Gratis-24
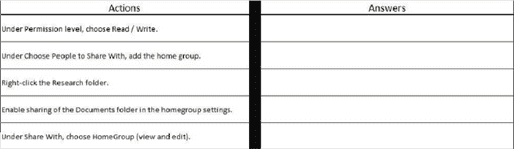
Step 1:
Under Permission level, choose Read/Write.
Under Choose People to Share With, add the home group.
Right-click the Research folder.
Enable sharing of the Documents folder in the homegroup settings.
You work for a small company that uses Windows 10 computers. The computers are joined to a homegroup. You want to share an existing folder named Research. It is located in the Documents folder. You need to give users the ability to change the files in this folder. Which three actions should you perform in sequence?
Gratis-24

Step 2:
Under Permission level, choose Read/Write.
Under Choose People to Share With, add the home group.
Right-click the Research folder.
Enable sharing of the Documents folder in the homegroup settings.
You work for a small company that uses Windows 10 computers. The computers are joined to a homegroup. You want to share an existing folder named Research. It is located in the Documents folder. You need to give users the ability to change the files in this folder. Which three actions should you perform in sequence?
Gratis-24

Step 3:
Under Permission level, choose Read/Write.
Under Choose People to Share With, add the home group.
Right-click the Research folder.
Enable sharing of the Documents folder in the homegroup settings.
You have a Windows 8 computer. You need to migrate from Windows 8 to Windows 10 while retaining as much data as possible. You load the Windows 10 media into the DVD drive. Which three actions should you perform next in sequence?
Gratis-25

Step 1:
Under installation options, choose Keep personal files.
Run the Setup.exe file from the DVD.
Enter the license key.
Under installation options, choose Windows settings.
You have a Windows 8 computer. You need to migrate from Windows 8 to Windows 10 while retaining as much data as possible. You load the Windows 10 media into the DVD drive. Which three actions should you perform next in sequence?
Gratis-25

Step 2:
Under installation options, choose Keep personal files.
Run the Setup.exe file from the DVD.
Enter the license key.
Under installation options, choose Windows settings.
You have a Windows 8 computer. You need to migrate from Windows 8 to Windows 10 while retaining as much data as possible. You load the Windows 10 media into the DVD drive. Which three actions should you perform next in sequence?
Gratis-25

Step 3:
Under installation options, choose Keep personal files.
Run the Setup.exe file from the DVD.
Enter the license key.
Under installation options, choose Windows settings.
You administer Windows 8 Pro computers in your company network. You discover that Sleep, Shut down and Restart are the only options available when you select the Power button as shown in the following exhibit (Click the Exhibit button.) You need to enable hibernation on the computer. Which three steps should you perform in sequence?
Gratis-26
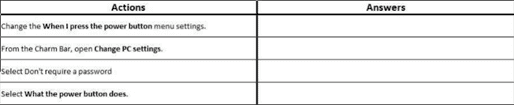
Step 1:
Change the When I press the power button menu settings.
From the Charm Bar, open Change PC Settings.
Select Don't require a password.
Select What the power button does.
You administer Windows 8 Pro computers in your company network. You discover that Sleep, Shut down and Restart are the only options available when you select the Power button as shown in the following exhibit (Click the Exhibit button.) You need to enable hibernation on the computer. Which three steps should you perform in sequence?
Gratis-26

Step 2:
Change the When I press the power button menu settings.
From the Charm Bar, open Change PC Settings.
Select Don't require a password.
Select What the power button does.
You administer Windows 8 Pro computers in your company network. You discover that Sleep, Shut down and Restart are the only options available when you select the Power button as shown in the following exhibit (Click the Exhibit button.) You need to enable hibernation on the computer. Which three steps should you perform in sequence?
Gratis-26

Step 3:
Change the When I press the power button menu settings.
From the Charm Bar, open Change PC Settings.
Select Don't require a password.
Select What the power button does.
You administer 50 laptops that run Windows 7 Professional 32-bit. You want to install Windows 8 Pro 64-bit on every laptop. Users will keep their own laptops. You need to ensure that user application settings, Windows settings, and user files are maintained after Windows 8 Pro is installed. Which four actions should you perform in sequence?
Gratis-27

Step 1:
Run the Scanstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c / hardlink /nocompress command.
Copy the User State Migration Tool (USMT) files and tools to the source computer.
Run the Scanstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c command.
Install Windows 8 Pro on the existing Windows partition with no formatting or repartitioning. Install standard operating environment applications.
Run the Loadstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c / hardlink /nocompress command.
Install Windows 8 Pro by deleting all existing partitions and create a new one. Install standard operating environment applications.
You administer 50 laptops that run Windows 7 Professional 32-bit. You want to install Windows 8 Pro 64-bit on every laptop. Users will keep their own laptops. You need to ensure that user application settings, Windows settings, and user files are maintained after Windows 8 Pro is installed. Which four actions should you perform in sequence?
Gratis-27

Step 2:
Run the Scanstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c / hardlink /nocompress command.
Copy the User State Migration Tool (USMT) files and tools to the source computer.
Run the Scanstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c command.
Install Windows 8 Pro on the existing Windows partition with no formatting or repartitioning. Install standard operating environment applications.
Run the Loadstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c / hardlink /nocompress command.
Install Windows 8 Pro by deleting all existing partitions and create a new one. Install standard operating environment applications.
You administer 50 laptops that run Windows 7 Professional 32-bit. You want to install Windows 8 Pro 64-bit on every laptop. Users will keep their own laptops. You need to ensure that user application settings, Windows settings, and user files are maintained after Windows 8 Pro is installed. Which four actions should you perform in sequence?
Gratis-27

Step 3:
Run the Scanstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c / hardlink /nocompress command.
Copy the User State Migration Tool (USMT) files and tools to the source computer.
Run the Scanstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c command.
Install Windows 8 Pro on the existing Windows partition with no formatting or repartitioning. Install standard operating environment applications.
Run the Loadstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c / hardlink /nocompress command.
Install Windows 8 Pro by deleting all existing partitions and create a new one. Install standard operating environment applications.
You administer 50 laptops that run Windows 7 Professional 32-bit. You want to install Windows 8 Pro 64-bit on every laptop. Users will keep their own laptops. You need to ensure that user application settings, Windows settings, and user files are maintained after Windows 8 Pro is installed. Which four actions should you perform in sequence?
Gratis-27

Step 4:
Run the Scanstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c / hardlink /nocompress command.
Copy the User State Migration Tool (USMT) files and tools to the source computer.
Run the Scanstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c command.
Install Windows 8 Pro on the existing Windows partition with no formatting or repartitioning. Install standard operating environment applications.
Run the Loadstate.exe c:\store / i:migdocs.xml /i:migapp.xml /v:13 /c / hardlink /nocompress command.
Install Windows 8 Pro by deleting all existing partitions and create a new one. Install standard operating environment applications.
You administer desktop computers that run Windows 8 Enterprise and are members of an Active Directory domain. A new security policy states that all traffic between computers in the research department must be encrypted and authenticated by using Kerberos V5. You need to configure the requested traffic authentication settings by using Windows Firewall with Advanced Settings.
Gratis-28

Which three actions should you perform in sequence?
Step 1:
Select Require authentication for inbound and outbound connection, and then for authentication method, select Computer (Kerberos V5).
Select Allow on app or feature through Windows Firewall.
Click to expand Inbound Rule, and then select New Rule.
Select the rule type Isolation, and then add the IP addresses of the research department computers.
Click to expand Outbound Rule, and then select New Rule.
Click to expand Connection Security Rule, and then select New Rule.
Select the rule type Server-to-Server, and then add the IP addresses of the research department computers.
You administer desktop computers that run Windows 8 Enterprise and are members of an Active Directory domain. A new security policy states that all traffic between computers in the research department must be encrypted and authenticated by using Kerberos V5. You need to configure the requested traffic authentication settings by using Windows Firewall with Advanced Settings.
Gratis-28

Which three actions should you perform in sequence?
Step 2:
Select Require authentication for inbound and outbound connection, and then for authentication method, select Computer (Kerberos V5).
Select Allow on app or feature through Windows Firewall.
Click to expand Inbound Rule, and then select New Rule.
Select the rule type Isolation, and then add the IP addresses of the research department computers.
Click to expand Outbound Rule, and then select New Rule.
Click to expand Connection Security Rule, and then select New Rule.
Select the rule type Server-to-Server, and then add the IP addresses of the research department computers.
You administer desktop computers that run Windows 8 Enterprise and are members of an Active Directory domain. A new security policy states that all traffic between computers in the research department must be encrypted and authenticated by using Kerberos V5. You need to configure the requested traffic authentication settings by using Windows Firewall with Advanced Settings.
Gratis-28

Which three actions should you perform in sequence?
Step 2:
Select Require authentication for inbound and outbound connection, and then for authentication method, select Computer (Kerberos V5).
Select Allow on app or feature through Windows Firewall.
Click to expand Inbound Rule, and then select New Rule.
Select the rule type Isolation, and then add the IP addresses of the research department computers.
Click to expand Outbound Rule, and then select New Rule.
Click to expand Connection Security Rule, and then select New Rule.
Select the rule type Server-to-Server, and then add the IP addresses of the research department computers.
{"name":"Microsoft 70-697 Practice Test (newly added)", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"A company has 100 client computers that run Windows 10 Enterprise. A new company policy requires that all client computers have static IPv6 addresses. You need to assign static IPv6 addresses to the client computers. Which Network Shell (netsh) command should you run?, Refer to the diagram. Screenshot-3 If a user is logged into the computer, and an update requires a restart, the computer will:, Refer to the diagram Screenshot-3 Windows updates will be downloaded from:","img":"https://www.quiz-maker.com/3012/images/ogquiz.png"}
More Quizzes
Το κουίζ της εβδομάδας
740
Test Your Understanding!
520
The Animal Center: Find Your Spirit Animal Test
23120
Listo para comprar casa ?
840
Albert Einstein IQ - Are You Smarter?
201018927
NBA MVP - Test Your Knowledge of Award Winners
201017319
Christian Theology Test - Free Knowledge Assessment
201017066
Rob Zombie's Halloween Movie - Free
201021238
The Person-Centered Therapist Is Best Described As a -
201019530
Anterior Thigh Muscles - Label Each Muscle
201018371
Body Language Test - Decode Nonverbal Cues (Free)
201021466
What Type of Sagittarius Am I? Free Archetype
201018221