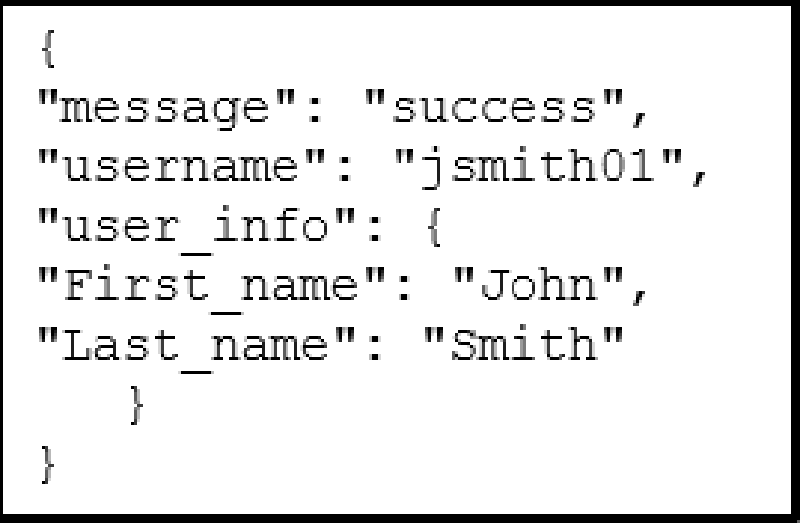
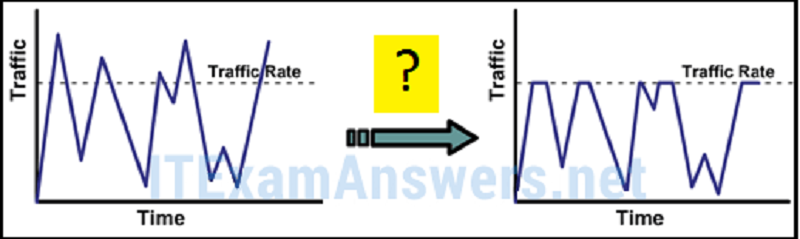
Final 7
{"name":"Final 7", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Test your knowledge about wireless network security and associated technologies with this engaging quiz! Designed for IT professionals and enthusiasts, this quiz covers key concepts related to network infrastructure and security protocols.Challenge yourself with questions about:- Wireless connectivity benefits- Reconnaissance attack purposes- Malware types- Quality of Service (QoS) techniques","img":"https:/images/course1.png"}
More Quizzes
35 Network Ports for Security+
351825
Security Malware
105141
How much of a Pigeon are you?
8415
George Orwell life and literature Quiz
12630
What Race Am I Attracted To? Free Dating Preference
201018847
What Song Should I Sing - Free, Instant Results
201018453
Yo _____ con la maestra - de Futuro Gratis
201017460
Beauxbatons Houses - Which House Are You?
201018928
Central Asia Map - Identify Countries on the Map
201017016
Home Depot Trivia - Test Your Knowledge for Free
201021920
Vocabulary IQ Test - Free Online Word Power Challenge
201018080
Which Sailor Moon Character Are You? Free
201017016