Practice questions PAM-DEF

CyberArk PAM-DEF Practice Quiz
Test your knowledge and skills on CyberArk PAM-DEF concepts with this comprehensive quiz. Gain insights into session monitoring, vault management, and privileged access management.
- Multiple choice questions
- Real-world scenarios
- Track your progress
Users are unable to launch web type connection components from the PSM server. Your manager asked you to open the case with cyberark support. Which logs will help the cyberark support team debug the issue? Choose 3.
PSMConsole.log
PSMDebug.log
PSMTrace.log
SessionID.Component.log
PMConsole.log
ITAlog.log
Which CyberArk group does a user need to be part of to view recordings or live monitor sessions?
Auditors
Vault Admin
DR Users
Operators
To ensure all sessions are being recorded, a CyberArk Administrator goes to the master policy and makes configuration changes. What configuration is correct?
Required privileged session monitoring and isolation = inactive; Record and save session activity = active.
Required privileged session monitoring and isolation = inactive; Record and save session activity = inactive.
Required privileged session monitoring and isolation = active; Record and save session activity = active.
Required privileged session monitoring and isolation = active; Record and save session activity = inactive.
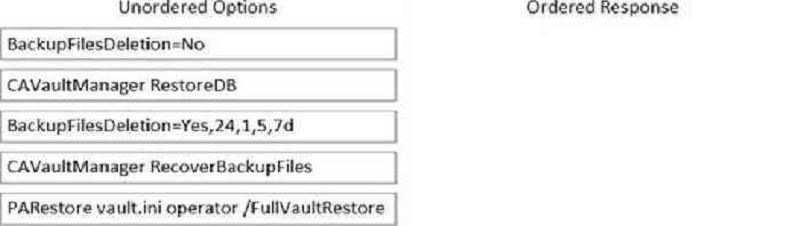
Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence.
BackupFilesDeletion=No > PARestore vault.ini operator /FullVaultRestore > CAVaultManager RecoverBackupFiles > CAVaultManager RestoreDB > BackupFilesDeletion=Yes,24,1,5,7d
BackupFilesDeletion=No > CAVaultManager RecoverBackupFiles > CAVaultManager RestoreDB > PARestore vault.ini operator /FullVaultRestore > BackupFilesDeletion=Yes,24,1,5,7d
CAVaultManager RecoverBackupFiles > BackupFilesDeletion=No > PARestore vault.ini operator /FullVaultRestore > CAVaultManager RestoreDB > BackupFilesDeletion=Yes,24,1,5,7d
CAVaultManager RecoverBackupFiles > CAVaultManager RestoreDB > BackupFilesDeletion=No > PARestore vault.ini operator /FullVaultRestore > BackupFilesDeletion=Yes,24,1,5,7d
Which certificate type do you need to configure the vault for LDAP over SSL?
CA Certificate that signed the certificate used by the External Directory
CA signed Certificate for the Vault server
CA signed Certificate for the PVWA server
Self-signed Certificate for the Vault
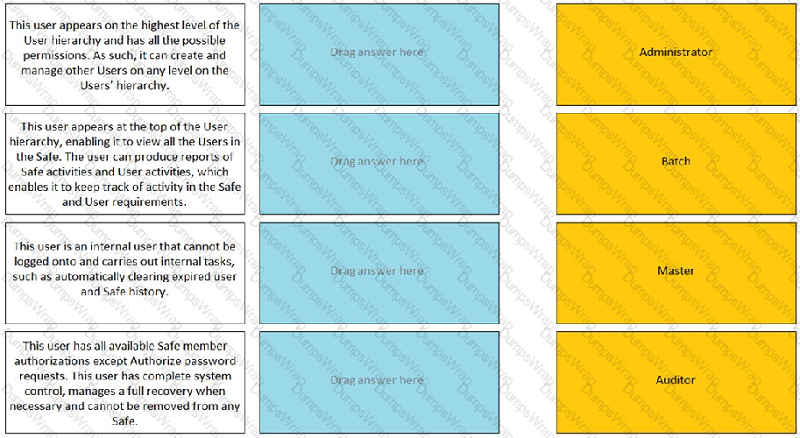
Match the built-in Vault User with the correct definition. ------- ADMINISTRATOR
This user appears on the highest level of the user hierarchy and has all the possible permissions. As such, it can also create and manage other users on any level on the users hierarchy.
This user appears at the top of the user hierarchy, enabling it to view all the users in the safe. The user can produce reports of safe activities and user activities, which enables it to keep track of activity in the safe and user requirements.
This user is an internal user that cannot be logged onto and carries out internal tasks, such as automatically clearing expired user and safe history.
This user has all available safe members authorizations except authorize password request. This user has complete system control, manages a full recovery from necessary and cannot be removed from any safe.

Match the built-in Vault User with the correct definition. ------- BATCH
This user appears on the highest level of the user hierarchy and has all the possible permissions. As such, it can also create and manage other users on any level on the users hierarchy.
This user appears at the top of the user hierarchy, enabling it to view all the users in the safe. The user can produce reports of safe activities and user activities, which enables it to keep track of activity in the safe and user requirements.
This user is an internal user that cannot be logged onto and carries out internal tasks, such as automatically clearing expired user and safe history.
This user has all available safe members authorizations except authorize password request. This user has complete system control, manages a full recovery from necessary and cannot be removed from any safe.

Match the built-in Vault User with the correct definition. ------- MASTER
This user appears on the highest level of the user hierarchy and has all the possible permissions. As such, it can also create and manage other users on any level on the users hierarchy.
This user appears at the top of the user hierarchy, enabling it to view all the users in the safe. The user can produce reports of safe activities and user activities, which enables it to keep track of activity in the safe and user requirements.
This user is an internal user that cannot be logged onto and carries out internal tasks, such as automatically clearing expired user and safe history.
This user has all available safe members authorizations except authorize password request. This user has complete system control, manages a full recovery from necessary and cannot be removed from any safe.

Match the built-in Vault User with the correct definition. ------- AUDITOR
This user appears on the highest level of the user hierarchy and has all the possible permissions. As such, it can also create and manage other users on any level on the users hierarchy.
This user appears at the top of the user hierarchy, enabling it to view all the users in the safe. The user can produce reports of safe activities and user activities, which enables it to keep track of activity in the safe and user requirements.
This user is an internal user that cannot be logged onto and carries out internal tasks, such as automatically clearing expired user and safe history.
This user has all available safe members authorizations except authorize password request. This user has complete system control, manages a full recovery from necessary and cannot be removed from any safe.
You are onboarding an account that is not supported out of the box. What should you do first to obtain a platform to import?
Create a service ticket in the customer portal explaining the requirements of the custom platform.
Research common community portals like stackoverflow, reddit, github for an existing platform.
From the platforms page, uncheck the ‘Hide non-supported platforms’ checkbox and see if a platform meeting your needs appears.
Visit the CyberArk marketplace and search for a platform that meet your needs.
You have been asked to identify the up or down status of Vault services. Which CyberArk utility can you use to accomplish this task?
Vault Replicator
PAS Reporter
Remote Control Agent
Syslog
You are logging into CyberArk as the Master user to recover an orphaned safe. Which items are required to log in as Master?
Master CD, Master Password, console access to the Vault server, Private Ark Client
Operator CD, Master Password, console access to the PVWA server, PVWA access
Operator CD, Master Password, console access to the Vault server, Recover.exe
Master CD, Master Password, console access to the PVWA server, Recover.exe
Your organization requires all passwords to be rotated every 90 days. Where can you set this regulatory requirement?
Master Policy
Safe Templates
PVWAConfig.xml
Platform Configuration
To enable the Automatic response ‘Add to Pending’ within PTA when unmanaged credentials are found, what are the minimum permissions required by PTAUser for the PasswordManager_pending safe?
List Accounts, View Safe members, Add accounts (includes update properties), Update Account content, Update Account properties
List Accounts, Add account (includes update properties), Delete Accounts, Manage Safe
Add Account (includes update properties), Update Account content, Update Account properties, View Audit
View Accounts, Update Account content, Update Account properties, Access Safe without confirmation, Manage Safe, View audit
You have been asked to turn off the time access restrictions for a safe. Where is this setting found?
PrivateArk
RestAPI
Password Vault Web Access (PVWA)
Vault
What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
UnixPrompts.ini
Plink.exe
Dbparm.ini
PVConfig.xml
You have been asked to secure a set of shared accounts in CyberArk whose passwords will need to be used by end users. The account owner wants to be able to track who was using an account at any given moment. Which security configuration should you recommend?
Configure one-time passwords for the appropriate platform in Master Policy.
Configure shared account mode on the appropriate safe.
Configure both one-time passwords and exclusive access for the appropriate platform in Master Policy.
Configure object level access control on the appropriate safe.
In your organization the ‘click to connect’ button is not active by default. How can this feature be activated?
Policies > Master Policy > Allow EPV transparent connections > Inactive
Policies > Master Policy > Session Management > Require privileged session monitoring and isolation > Add Exception
Policies > Master Policy > Allow EPV transparent connections > Active
Policies > Master Policy > Password Management
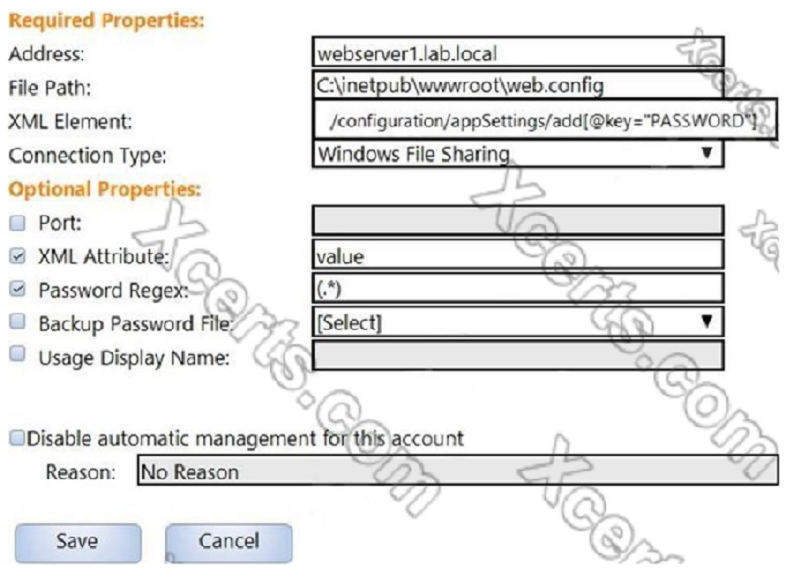
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password. What is the least intrusive way to accomplish this?
Use the ‘change’ button on the usage’s details page.
Use the ‘change’ button on the parent account’s details page.
Use the ‘sync’ button on the usage’s details page.
Use the ‘reconcile’ button on the parent account’s details page.
A Vault Administrator team member can log in to CyberArk, but for some reason, is not given Vault Admin rights. Where can you check to verify that the Vault Admins directory mapping points to the correct AD group?
PVWA > User Provisioning > LDAP Integration > Mapping Criteria
PVWA > User Provisioning > LDAP Integration > Map Name
PVWA > Administration > LDAP Integration > Mappings
PVWA > Administration > LDAP Integration > AD Groups
A newly created platform allows users to access a Linux endpoint. When users click to connect, nothing happens. Which piece of the platform is missing?
PSM-SSH Connection Component
UnixPrompts.ini
UnixProcess.ini
PSM-RDP Connection Component
Which CyberArk utility allows you to create lists of Master Policy Settings, owners and safes for output to text files or MSSQL databases?
Export Vault Data
Export Vault Information
PrivateArk Client
Privileged Threat Analytics
Which PTA sensors are required to detect suspected credential theft?
Logs, Vault Logs
Logs, Network Sensor, Vault Logs
Logs, PSM Logs, CPM Logs
Logs, Network Sensor, EPM
When running a ‘Privileged Accounts Inventory’ Report through the Reports page in PVWA on a specific safe, which permission/s are required on that safe to show complete account inventory information?
List Accounts, View Safe Members
Manage Safe Owners
List Accounts, Access Safe without confirmation
Manage Safe, View Audit
Which usage can be added as a service account platform?
Kerberos Tokens
IIS Application Pools
PowerShell Libraries
Loosely Connected Devices
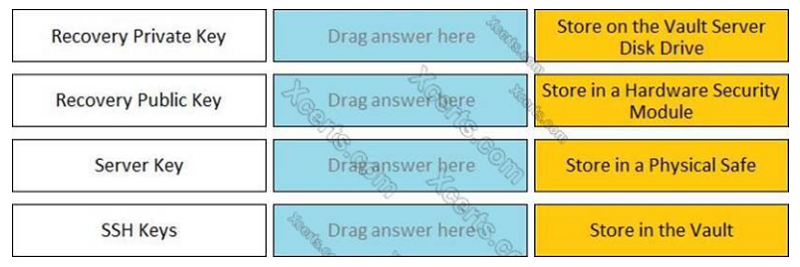
Match each key to its recommended storage location. ---------- RECOVERY PRIVATE KEY
Store on the vault server disk drive
Store in a hardware security module
Store in a physical safe
Store in the vault

Match each key to its recommended storage location. ---------- RECOVERY PUBLIC KEY
Store on the vault server disk drive
Store in a hardware security module
Store in a physical safe
Store in the vault

Match each key to its recommended storage location. ---------- SERVER KEY
Store on the vault server disk drive
Store in a hardware security module
Store in a physical safe
Store in the vault

Match each key to its recommended storage location. ---------- SSH KEY
Store on the vault server disk drive
Store in a hardware security module
Store in a physical safe
Store in the vault
You need to recover an account localadmin02 for target server 10.0.123.73 stored in Safe Team1. What do you need to recover and decrypt the object? (Choose three.)
Recovery Private Key
Recover.exe
Vault data
Recovery Public Key
Server Key
Master Password
What is the easiest way to duplicate an existing platform?
From PrivateArk, copy/paste the appropriate Policy.ini file; then rename it.
From the PVWA, navigate to the platforms page, select an existing platform that is similar to the new target account platform and then click Duplicate; name the new platform.
From PrivateArk, copy/paste the appropriate settings in PVConfiguration.xml; then update the policyName variable.
From the PVWA, navigate to the platforms page, select an existing platform that is similar to the new target account platform, manually update the platform settings and click ‘Save as’ INSTEAD of save to duplicate and rename the platform.
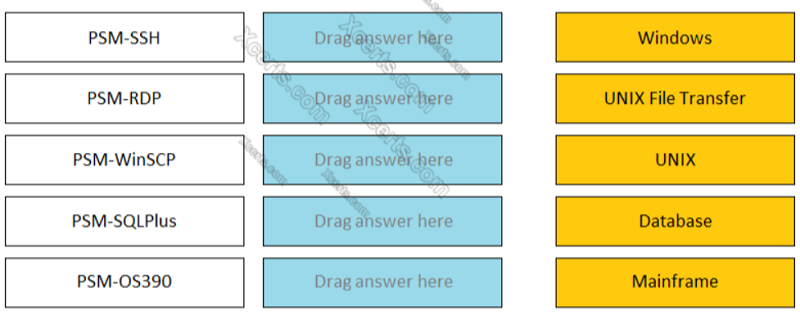
Match the connection component to the corresponding OS/Function. --------- PSM-SSH
Windows
UNIX File Transfer
UNIX
Database
Mainframe

Match the connection component to the corresponding OS/Function. --------- PSM-RDP
Windows
UNIX File Transfer
UNIX
Database
Mainframe

Match the connection component to the corresponding OS/Function. --------- PSM-WinSCP
Windows
UNIX File Transfer
UNIX
Database
Mainframe

Match the connection component to the corresponding OS/Function. --------- PSM-SQLPlus
Windows
UNIX File Transfer
UNIX
Database
Mainframe
The Privileged Access Management solution provides an out-of-the-box target platform to manage SSH keys, called UNIX Via SSH Keys. How are these keys managed?
CyberArk stores Private keys in the Vault and updates Public keys on target systems.
CyberArk stores Public keys in the Vault and updates Private keys on target systems
CyberArk does not store Public or Private keys and instead uses a reconcile account to create keys on demand.
CyberArk stores both Private and Public keys and can update target systems with either key.

Match the connection component to the corresponding OS/Function. --------- PSM-OS390
Windows
UNIX File Transfer
UNIX
Database
Mainframe
You want to generate a license capacity report. Which tool accomplishes this?
Password Vault Web Access
PrivateArk Client
DiagnoseDB Report
RestAPI
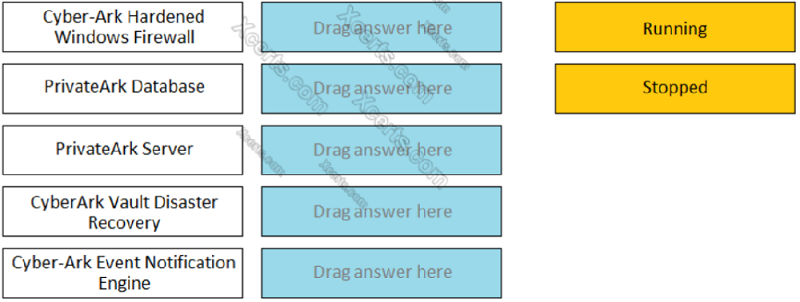
Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode. ------------ CYBERARK HARDENED WINDOWS FIREWALL
Running
Stopped

Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode. ------------ PRIVATEARK DATABASE
Running
Stopped

Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode. ------------ PRIVATEARK SERVER
Running
Stopped

Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode. ------------ CYBERARK VAULT DISASTER RECOVERY
Running
Stopped

Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode. ------------ CYBERARK EVENT NOTIFICATION ENGINE
Running
Stopped
You need to enable the PSM for all platforms. Where do you perform this task?
Platform Management > (Platform) > UI & Workflows
Master Policy > Session Management
Master Policy > Privileged Access Workflows
Administration > Options > Connection Components
How much disk space do you need on the server for a PAReplicate?
500 GB
1 TB
Same as disk size on Satellite Vault
Same as disk size on Primary Vault
In the Private Ark client, how do you add an LDAP group to a CyberArk group?
Select Update on the CyberArk group, and then click Add > LDAP Group
Select Update on the LDAP Group, and then click Add > LDAP Group
Select Member Of on the CyberArk group, and then click Add > LDAP Group
Select Member Of on the LDAP group, and then click Add > LDAP Group
For Digital Vault Cluster in a high availability configuration, how does the cluster determine if a node is down?
The heartbeat is no longer detected on the private network.
The shared storage array is offline.
An alert is generated in the Windows Event log.
The Digital Vault Cluster does not detect a node failure.
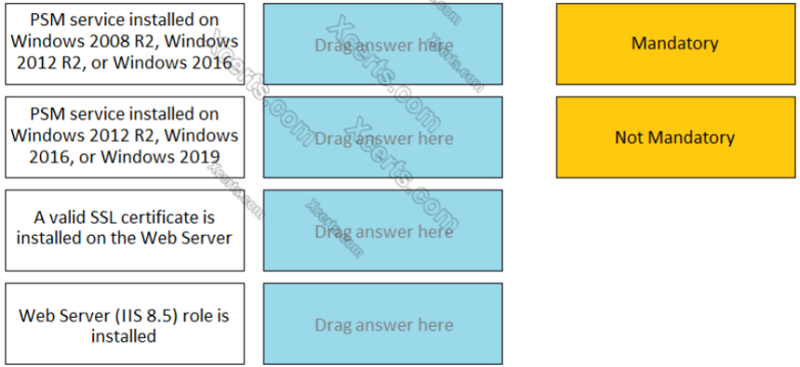
For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check. --------- PSM SERVICE INSTALLED ON WINDOWS 2008 R2, WINDOWS 2012 R2, OR WINDOWS 2016
Mandatory
Non Mandatory

For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check. --------- PSM SERVICE INSTALLED ON WINDOWS 2012 R2, WINDOWS 2016, OR WINDOWS 2019
Mandatory
Non Mandatory

For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check. --------- WEB SERVER (IIS 8.5) ROLE IS INSTALLED
Mandatory
Non Mandatory

For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check. --------- A VALID SSL CERTIFICATE IS INSTALLED ON THE WEB SERVER
Mandatory
Non Mandatory
In a rule using ‘Privileged Session Analysis and Response’ in PTA, which session options are available to configure as responses to activities?
Suspend, Terminate, None
Suspend, Terminate, Lock Account
Pause, Terminate, None
Suspend, Terminate
A user requested access to view a password secured by dual-control and is unsure who to contact to expedite the approval process. The Vault Admin has been asked to look at the account and identify who can approve their request. What is the correct location to identify users or groups who can approve?
PVWA> Administration > Platform Configuration > Edit Platform > UI & Workflow > Dual Control> Approvers
PVWA> Policies > Access Control (Safes) > Safe Members > Workflow > Authorize Password Requests
PVWA> Account List > Edit > Show Advanced Settings > Dual Control > Direct Managers
PrivateArk > Admin Tools > Users and Groups > Auditors (Group Membership)
You are creating a Dual Control workflow for a team’s safe. Which safe permissions must you grant to the Approvers group?
List accounts, Authorize account request
Retrieve accounts, Access Safe without confirmation
Retrieve accounts, Authorize account request
List accounts, Unlock accounts
You receive this error: ‘Error in changepass to user domain\user on domain server(\domain.(winRc=5) Access is denied.’ Which root cause should you investigate?
The account does not have sufficient permissions to change its own password.
The domain controller is unreachable
The password has been changed recently and minimum password age is preventing the change.
The CPM service is disabled and will need to be restarted.
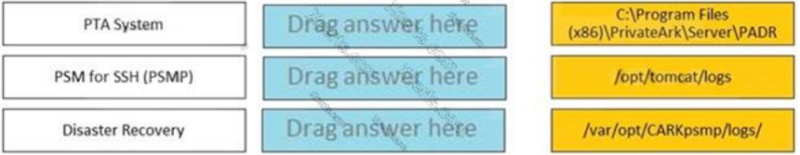
Match each component to its respective Log File location. ------- PTA SYSTEM
/opt/tomcat/logs
/var/opt/CARKpsmp/logs/
C:\Program Files (x86)\PrivateArk\Server\PADR

Match each component to its respective Log File location. ------- PSM FOR SSH (PSMP)
/opt/tomcat/logs
/var/opt/CARKpsmp/logs/
C:\Program Files (x86)\PrivateArk\Server\PADR

Match each component to its respective Log File location. ------- DISASTER RECOVERY
/opt/tomcat/logs
/var/opt/CARKpsmp/logs/
C:\Program Files (x86)\PrivateArk\Server\PADR
You are creating a shared safe for the help desk. What must be considered regarding the naming convention?
Ensure your naming convention is no longer than 20 characters.
Combine environments, owners and platforms to minimize the total number of safes created.
Safe owners should determine the safe name to enable them to easily remember it.
The use of these characters V:*<>".| is not allowed.
Due to network activity, ACME Corp’s PrivateArk Server became active on the DR Vault while the Primary Vault was also running normally. All the components continued to point to the Primary Vault. Which steps should you perform to restore DR replication to normal?
Replicate data from DR Vault to Primary Vault > Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
Shutdown PrivateArk Server on Primary Vault > Replicate data from DR Vault to Primary Vault > Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
Shutdown PrivateArk Server on DR Vault > Replicate data from DR Vault to Primary Vault > Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
Operating System Username
Host IP Address
Client Hostname
Operating System Type (Linux/Windows/HP-UX)
Vault IP Address
Time Frame
A new HTML5 Gateway has been deployed in your organization. Where do you configure the PSM to use the HTML5 Gateway?
Administration > Options > Privileged Session Management > Configured PSM Servers > Connection Details > Add PSM Gateway
Administration > Options > Privileged Session Management > Add Configured PSM Gateway Servers
Administration > Options > Privileged Session Management > Configured PSM Servers > Add PSM Gateway
Administration > Options > Privileged Session Management > Configured PSM Servers > Connection Details
Which built-in report from the reports page in PVWA displays the number of days until a password is due to expire?
Privileged Accounts Inventory
Privileged Accounts Compliance Status
Activity Log
Privileged Accounts CPM Status
To use PSM connections while in the PVWA, what are the minimum safe permissions a user or group will need?
List Accounts, Use Accounts
List Accounts, Use Accounts, Retrieve Accounts
Use Accounts
List Accounts, Use Accounts, Retrieve Accounts, Access Safe without confirmation
In a default CyberArk installation, which group must a user be a member of to view the reports page in PVWA?
PVWAMonitor
ReportUsers
PVWAReports
Operators
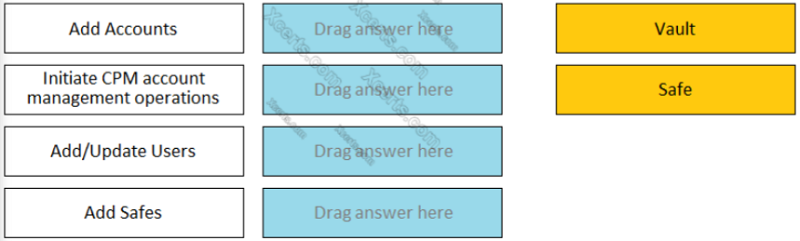
Match each permission to where it can be found. ---------- INTIATE CPM ACCOUNT MANAGEMENT OPERATION
Safe
Vault

Match each permission to where it can be found. ---------- ADD SAFE
Safe
Vault

Match each permission to where it can be found. ---------- ADD/UPDATE USERS
Safe
Vault

Match each permission to where it can be found. ---------- ADD ACCOUNT
Safe
Vault
You are onboarding 5,000 UNIX root accounts for rotation by the CPM. You discover that the CPM is unable to log in directly with the root account and will need to use a secondary account. How should this be configured to allow for password management using least privilege?
Configure each CPM to use the correct logon account.
Configure each CPM to use the correct reconcile account.
Configure the UNIX platform to use the correct logon account.
Configure the UNIX platform to use the correct reconcile account.
You are creating a new Rest API user that utilizes CyberArk Authentication. What is a correct process to provision this user?
Private Ark Client > Tools > Administrative Tools > Users and Groups > New > User
Private Ark Client > Tools > Administrative Tools > Directory Mapping > Add
PVWA > User Provisioning > LDAP Integration > Add Mapping
PVWA > User Provisioning > Users and Groups > New > User
Which command configures email alerts within PTA if settings need to be changed post install?
/opt/tomcat/utility/emailConfiguration.sh
/opt/PTA/emailConfiguration.sh
/opt/PTA/utility/emailConfig.sh
/opt/tomcat/utility/emailSetup.sh
Which permissions are needed for the Active Directory user required by the Windows Discovery process?
Domain Admin
LDAP Admin
Read/Write
Read
To manage automated onboarding rules, a CyberArk user must be a member of which group?
Vault Admins
CPM User
Auditors
Administrators
Your organization has a requirement to allow users to ‘check out passwords’ and connect to targets with the same account through the PSM. What needs to be configured in the Master policy to ensure this will happen?
Enforce check-in/check-out exclusive access = active; Require privileged session monitoring and isolation= active
Enforce check-in/check-out exclusive access = inactive; Require privileged session monitoring and isolation = inactive
Enforce check-in/check-out exclusive access = inactive; Record and save session activity = active
Enforce check-in/check-out exclusive access = active; Record and save session activity = inactive
When onboarding multiple accounts from the Pending Accounts list, which associated setting must be the same across the selected accounts?
Platform
Connection Component
CPM
Vault
In PVWA, you are attempting to play a recording made of a session by user jsmith, but there is no option to ‘Fast Forward’ within the video. It plays and only allows you to skip between commands instead. You are also unable to download the video. What could be the cause?
Recording is of a PSM for SSH session.
The browser you are using is out of date and needs an update to be supported.
You do not have the ‘View Audit’ permission on the safe where the account is stored.
You need to update the recorder settings in the platform to enable screen capture every 10000 ms or less.
If the AccountUploader Utility is used to create accounts with SSH keys, which parameter do you use to set the full or relative path of the SSH private key file that will be attached to the account?
KeyPath
KeyFile
ObjectName
Address
You received a notification from one of your CyberArk auditors that they are missing Vault level audit permissions. You confirmed that all auditors are missing the Audit Users Vault permission. Where do you update this permission for all auditors?
Private Ark Client > Tools > Administrative Tools > Directory Mapping > Vault Authorizations
Private Ark Client > Tools > Administrative Tools > Users and Groups > Auditors > Authorizations tab
PVWA User Provisioning > LDAP integration > Vault Auditors Mapping > Vault Authorizations
PVWA> Administration > Configuration Options > LDAP integration > Vault Auditors Mapping > Vault Authorizations
A new domain controller has been added to your domain. You need to ensure the CyberArk infrastructure can use the new domain controller for authentication. Which locations must you update?
On the Vault server in Windows\System32\Etc\Hosts and in the PVWA Application under Administration > LDAP Integration > Directories > Hosts
On the Vault server in Windows\System32\Etc\Hosts and on the PVWA server in Windows\System32\Etc\Hosts
In the Private Ark client under Tools > Administrative Tools > Directory Mapping
On the Vault server in the certificate store and on the PVWA server in the certificate store
Which statement is correct concerning accounts that are discovered, but cannot be added to the Vault by an automated onboarding rule?
They are added to the Pending Accounts list and can be reviewed and manually uploaded.
They cannot be onboarded to the Password Vault.
They must be uploaded using third party tools.
They are not part of the Discovery Process.
Which item is an option for PSM recording customization?
Windows events text recorder with automatic play-back
Windows events text recorder and universal keystrokes recording simultaneously
Universal keystrokes text recorder with windows events text recorder disabled
Custom audio recording for windows events
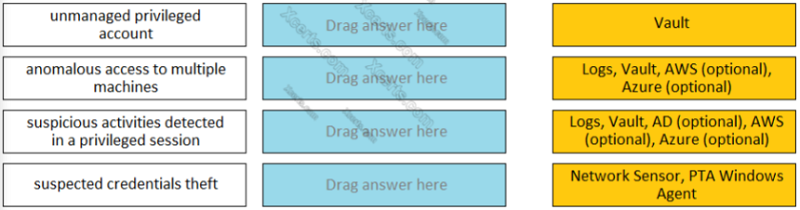
Match each PTA alert category with the PTA sensors that collect the data for it. --------------- UNMANAGED PRIVILEGED ACCOUNT
Logs, Vault, AD (optional), AWS (optional), Azure (Optional)
Network Sensor, PTA Windows Agent
Vault
Logs, Vault, AWS (optional), Azure (optional)

Match each PTA alert category with the PTA sensors that collect the data for it. --------------- ANOMALOUS ACCESS TO MULTIPLE MACHINES
Logs, Vault, AD (optional), AWS (optional), Azure (Optional)
Network Sensor, PTA Windows Agent
Vault
Logs, Vault, AWS (optional), Azure (optional)

Match each PTA alert category with the PTA sensors that collect the data for it. --------------- SUSPICIOUS ACTIVITIES DETECTED IN A PRIVILEGED SESSION
Logs, Vault, AD (optional), AWS (optional), Azure (Optional)
Network Sensor, PTA Windows Agent
Vault
Logs, Vault, AWS (optional), Azure (optional)

Match each PTA alert category with the PTA sensors that collect the data for it. --------------- SUSPECTED CREDENTIALS THEFT
Logs, Vault, AD (optional), AWS (optional), Azure (Optional)
Network Sensor, PTA Windows Agent
Vault
Logs, Vault, AWS (optional), Azure (optional)
Your customer, ACME Corp, wants to store the Safes Data in Drive D instead of Drive C. Which file should you edit?
TSparm.ini
Vault.ini
DBparm.ini
User.ini
Which option in the Private Ark client is used to update users Vault group memberships?
Update > General tab
Update > Authorizations tab
Update > Member Of tab
Update > Group tab
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
Safe Name
Platform ID
All required properties specified in the Platform
Username
Address
Hostname
Which Automatic Remediation is configurable for a PTA detection of a ‘Suspected Credential Theft’?
Add to Pending
Rotate Credentials
Reconcile Credentials
Disable Account
{"name":"Practice questions PAM-DEF", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Test your knowledge and skills on CyberArk PAM-DEF concepts with this comprehensive quiz. Gain insights into session monitoring, vault management, and privileged access management.Multiple choice questionsReal-world scenariosTrack your progress","img":"https:/images/course1.png"}
More Quizzes
Thycotic - PAM
14757
ITEC MIDTERMS
452231
Pidar test
4268
Play This Quiz On English And Sanskrit Names For Yoga Poses
1050
Biology Trivia - Test Your Knowledge for Free
201016559
Tomodachi Life Personality - Which Mii Are You?
201017676
Fluids and Conservation Laws - Free Practice
15815254
PAT Maths Questions - Free Practice Online
201016559
Equilibrium - Free Chemistry Practice
201019032
Birthday: What Your Birth Date Says About You
201016559
Basic Accounting - Free Fundamentals Practice
15815576
What Card Am I? - Discover Your Playing Card Persona
201018472