PAM-DEF Practice
Which CyberArk group does a user need to be part of to view recordings or live monitor sessions?
Auditor
Vault Admin
DR users
Operators
Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence.
BackupFilesDeletion=No > PARestore vault.ini operator /FullVaultRestore > CAVaultManager RecoverBackupFiles > CAVaultManager RestoreDB > BackupFilesDeletion=Yes,24,1,5,7d
BackupFilesDeletion=No > CAVaultManager RecoverBackupFiles > CAVaultManager RestoreDB > PARestore vault.ini operator /FullVaultRestore > BackupFilesDeletion=Yes,24,1,5,7d
CAVaultManager RecoverBackupFiles > BackupFilesDeletion=No > PARestore vault.ini operator /FullVaultRestore > CAVaultManager RestoreDB > BackupFilesDeletion=Yes,24,1,5,7d
CAVaultManager RecoverBackupFiles > CAVaultManager RestoreDB > BackupFilesDeletion=No > PARestore vault.ini operator /FullVaultRestore > BackupFilesDeletion=Yes,24,1,5,7d
Which Automatic Remediation is configurable for a PTA detection of a “Suspected Credential Theft”?
Add to Pending
Rotate Credentials
Reconcile Credentials
Disable Account
To ensure all sessions are being recorded, a CyberArk Administrator goes to the master policy and makes configuration changes. What configuration is correct?
Required privileged session monitoring and isolation = inactive; Record and save session activity = active.
Required privileged session monitoring and isolation = inactive; Record and save session activity = inactive
Required privileged session monitoring and isolation = active; Record and save session activity = active
Required privileged session monitoring and isolation = active; Record and save session activity = inactive
Which certificate type do you need to configure the vault for LDAP over SSL?
The CA Certificate that signed the certificate used by the External Directory
A CA signed Certificate for the Vault server
A CA signed Certificate for the PVWA server
A self-signed Certificate for the Vault
Which values are acceptable in the address field of an account?
It must be a fully qualified domain name (fqdn)
It must be an IP address
It must be a NetBIOS name
Any name that is resolvable on the Central Policy Manager (CPM) server is acceptable.
Which of the following account onboarding method is considered proactive?
Account discovery
Detecting accounts with PTA
Rest API integration with account provisioning software
DNA scan
When creating an onboarding rule, it will be executed upon _____?
All accounts in pending account list
Any future accounts discovered by a discovery process
All of the above
Which onboarding method would you use to integrate CyberArk with your accounts provisioning process?
Accounts Discovery
Auto Detection
Onboarding RestAPI functions
PTA Rules
What is the primary purpose of Dual Control?
Reduced risk of credential theft
More frequent password changes
Non-repudiation (individual accountability)
To force a 'collusion to commit' fraud ensuring no single actor may use a password without authorization.
A newly created platform allows users to access a Linux endpoint. When users click to connect, nothing happens. Which piece of the platform is missing?
PSM-SSH Connection Component
PSM-RDP Connection Component
UnixPrompts.ini
UnixProcess.ini
What is the purpose of the PrivateArk Server service?
Maintains vault metadata.
Makes vault data accessible to components.
Executes password changes.
Sends email alert from the Vault.
Which report provides a list of accounts stored in the vault?
Privileged Accounts Compliance Status
Privileged Accounts Inventory
Entitlement Report
Activity Log
Which report shows the accounts that are accessible to each user?
Activity report
Entitlement report
Privileged Accounts Compliance Status report
Applications Inventory report
What is the purpose of the Immediate Interval setting in a CPM policy?
To control how often the CPM looks for system initiated CPM work
To control how often the CPM looks for user initiated CPM work
To control how long the CPM rests between password
To control the maximum amount of time the CPM will wait for a password change to complete
What is the purpose of the Interval setting in a CPM policy?
To control how often the CPM looks for system initiated CPM work
To control how often the CPM looks for user initiated CPM work
To control how long the CPM rests between password
To control the maximum amount of time the CPM will wait for a password change to complete
Which utilities could you use to change debugging levels on the vault without having to restart the vault? (Choose two)
PAR Agent
PrivateArk Server Central Administration
Edit DBParm.ini in a text editor
Setup.exe
If a user is a member of more than one group that has authorizations on a safe, by default that user is granted ___?
The vault will not allow this situation to occur
Only those permissions that exist on the group added to the safe first
Only those permissions that exist in all groups to which the user belongs
The cumulative permissions of all the groups to which that user belongs
Vault authorizations may be granted to _____?
Vault users
Vault groups
LDAP users
LDAP groups
Which user is automatically added to all safes and cannot be removed?
Auditor
Administrator
Master
Operator
Within the vault, each password is encrypted by:
The server key
The recovery public key
The recovery private key
Its own unique key
What are the functions of the remote control agent service? Choose 3.
Allow remote monitoring of the vault
Send SNMP traps from the vault
Maintain audit data
Allow cyberark services to be managed (start/stop/status) remotely
What is the purpose of the cyberark event notification engine service?
It sends email messages from the central policy manager
It sends email messages from the vault
It processes audit report messages
It makes vault data available to components
What is the purpose of the PrivateArk Database service?
Communicates with components
Sends email alerts from vault
Execute password change
Maintains vault metadata
Which of the following logs contains information about errors related to PTA?
ITAlog.log
Diamond.log
Pm_error.log
WebApplication.log
A vault administrator has associated a logon account to one of their unix root accounts in the vault, when attempting to change the root account password, the central policy manager (CPM) will:
Log in to the system as root, then change the password
Log in to the system as logon account, then change root password
Log in to the system as logon account, run the SU command to log in as root, then change root password
None of the above
Select the best practice for storing the master cd.
Copy the files to the vault server and discard the cd
Copy the content of the cd to a hardware security module (HSM) and discard the cd
Store the cd in a secured location, such as a physical safe
Store the cd in a secure location, such as a physical safe, and copy the contents of the cd to a locker secured with NTFS permissions on the vault
Which service should not be running on the DR vault when the primary production vault is up?
PrivateArk database
PrivateArk server
Cyberark vault disaster recovery service
Cyberark logic container
When managing SSH keys, the central policy manger (CPM) stores the public key:
In the vault
On the target server
Both in vault and target server
Nowhere because the public key can always be generated from the private key
When managing SSH keys, the central policy manger (CPM) stores the private key:
In the vault
On the target server
Both in vault and target server
Nowhere because the private key can always be generated from the public key
Time of day or day of week restrictions on when password changes can occur are configured in the:
Master policy
Platform settings
Safe settings
Account details
Time of day or day of week restrictions on when password verifications can occur are configured in the:
Master policy
Platform settings
Safe settings
Account details
Time of day or day of week restrictions on when password reconciliations can occur are configured in the:
Master policy
Platform settings
Safe settings
Account details
According to the default web options settings, which group grants access to the report page?
PVWAUsers
Vault Administrators
Auditors
PVWAMonitor
Due to network activity, ACME Corp’s PrivateArk Server became active on the OR Vault while the Primary Vault was also running normally. All the components continued to point to the Primary Vault. Which steps should you perform to restore DR replication to normal?
Replicate data from DR Vault to Primary Vault > Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
Shutdown PrivateArk Server on Primary Vault > Replicate data from DR Vault to Primary Vault > Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
Shutdown PrivateArk Server on DR Vault > Replicate data from DR Vault to Primary Vault > Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
Assuming a safe has been configured to be accessible during certain hours of the day, a vault administrator may still access that safe outside of those hours.
True
False
The vault supports subnet based access control.
True
False
When a DR Vault become an active vault, it will automatically revert back to DR mode once the Primary Vault comes back online.
True, this is the default behavior
False, the vault administrator must manually set the DR Vault to DR mode by setting “FailoverMode=no” in the padr.ini file.
True, if the AllowFailback setting is set to “yes” in the padr.ini file
False, the vault administrator must manually set the DR Vault to DR mode by setting “FailoverMode=no” in the dbparm.ini file
Which of the following components can be used to create a tape backup of the vault?
Disaster Recovery
Distributed Vaults
Replicate
High Availability
A simple mail transfer protocol (SMTP) integration is critical for monitoring vault activity and facilitating workflow processes, such as dual control.
True
False
What is the name of the platform parameter that determines the length of time a person is allowed to use a one-time password?
MinValidityPeriod
Interval
ImmediateInterval
Timeout
What is the primary purpose of one-time passwords?
Reduced risk of credential theft
More frequent password changes
Non repudiation (individual accountability)
To force a ‘collusion to commit’ fraud ensuring no single actor may use a password without authorization
What is the primary purpose of exclusive accounts?
Reduced risk of credential theft
More frequent password changes
Non repudiation (individual accountability)
To force a ‘collusion to commit’ fraud ensuring no single actor may use a password without authorization
Which type of automatic remediation can be performed by the PTA in the case of a suspicious password change security event?
Password change
Password reconciliation
Session suspension
Session termination
Which type of automatic remediation can be performed by the PTA in the case of a suspected credential theft security event?
Password change
Password reconciliation
Session suspension
Session termination
Which report could show all accounts that are past their expiration dates?
Privileged Account Compliance Status report
Activity log
Privileged Account Inventory report
Application Inventory report
Which report shows the accounts that are accessible to each user?
Privileged Account Compliance Status report
Activity log
Entitlement report
Application Inventory report
Access control to passwords is implemented by:
Vault authorizations
Safe authorizations
Master Policy
Platform settings
For an account attached to a platform that requires dual control based on a master policy exception, how would the vault administrator configure a group of users to access a password without approval?
Create an exception to the master policy to exclude the group from the workflow process
Edit the master policy rule and modify the advanced ‘Access Safe without approval’ rule to include the group
On the safe in which the account is stored grant the group the ‘Access Safe without audit’ authorization
On the safe in which the account is stored grant the group the ‘Access Safe without confirmation’ authorization
What is the purpose of the HeadStartInterval setting in a platform?
It determines how far in advance audit data is collected for reports
It instructs the CPM to initiate the password change process certain number of days before expiration
It instructs the AIM provider to ‘skip the cache’ during the defined time period
It alerts users of upcoming password changes a certain number of days before expiration
Which master policy setting must be active in order to have an account checked out by one user for a pre-determined amount of time?
Require dual control password access approval
Enforce check in/check out exclusive access
Enforce one time password access
Enforce check in/check out exclusive access and enforce one time password access
PSM for Windows (previously known as RDP Proxy) supports connections to which of the following target systems?
Windows
Unix
Oracle
All of the above
PSM for SSH (previously known as PSM-SSH Proxy) supports connections to which of the following target systems?
Windows
Unix
Oracle
All of the above
Which keys are required to be present in order to start the PrivateArk Server service? (Choose 2)
Recovery public key
Recovery private key
Server key
Safe key
Which combination of safe member permissions will allow end Users to log in to a remote machine transparently but NOT show or copy the password?
Use Accounts, Retrieve Accounts, List Accounts
Use Accounts, List Accounts
Use Accounts
List Accounts, Retrieve Accounts
Which user can access all passwords in the vault?
Administrator
Any members of vault administrators
Any members of auditors
Master
Which of the following are secure options for storing the contents of the operator CD, while still allowing the contents to be accessible upon a planned vault restart? Choose three correct options.
Store the cd in a physical safe and mount the CD every time vault maintenance is performed
Copy the entire content of the cd to the system safe of the vault
Copy the entire content of the cd to a folder on the vault server and secure it with NTFS permissions
Store the server key in a Hardware Security Module (HSM) and copy the rest of the keys from the cd to a folder on the vault server and secure it with NTFS permissions
One of your users is receiving the error message "ITATS006E Station is suspended for User jsmith" when attempting to sign in to the pvwa. Which utility would you use to correct this problem?
Createcredfile.exe
Cavaultmanager.exe
PrivateArk
PVWA
Via PVWA, a user initiates a PSM connection to the target linux machine using RemoteApp. When the client machine makes a RDP connection to the PSM server, which user will be utilized?
Credentials stored in the vault for the target machine
Shadowuser
PSMConnect
PSMAdminConnect
An auditor needs to login to the PSM in order to live monitor an active session. Which user ID is used to establish the RDP connection to the PSM server?
PSMConnect
PSMMaster
PSMGwUser
PSMAdminConnect
How does the vault administrator apply a new license file?
Upload the license.xml file to the system safe and restart the PrivateArk Server service
Upload the license.xml file to the system safe
Upload the license.xml file to the vault internal safe and restart the PrivateArk Server service
Upload the license.xml file to the vault internal safe
Cyberark implements license limits by controlling the number and types of users that can be provisioned in the vault
True
False
The vault administrator can change the vault license by uploading the new license to the system safe
False
True
Cyberark recommends implementing object level access control on all safes
True
False
For a safe with object level access control enabled, the vault administrator is able to turn off object level access control when it is no longer needed on the safe
True
False
In order to connect to a target device through PSM, the account credentials used for the connection must be stored in the vault
True
False, because the user can also enter credentials manually using Adhoc access
False, because if credentials are not stored in the vault, the PSM will log into the target device as PSMConnect
False, because if credentials are not stored in the vault, the PSM will prompt for credentials
PTA can automatically suspend sessions if suspicious activities are detected in a privileged session, but only if the session is made via the Cyberark PSM.
True
False, the PTA can suspend sessions whether the session is made via the PSM or not.
What is the purpose of the EVD? (Export vault data utility)
To extract vault metadata into an open database platform
To allow editing of vault metadata
To create a backup of the MySQL database
To extract audit data from the vault
A safe was recently created by a user who is a member of the LDAP vault administrator group. Which of the following users does not have access to the newly created safe by default?
Master
Administrator
Auditor
Backup
Which one of these built-in vault users is not automatically added to a safe when it is created?
Master
Administrator
Auditor
Operator
Which one of the following reports is not generated by using the PVWA?
Accounts inventory
Application inventory
Active/non active users
Compliance status
Vault admins must manually add the auditors group to newly created safes so auditors will have sufficient access to run reports.
True
False
Accounts Discovery allows secure connection to domain controllers
True
False
Platform settings are applied to
Entire Vault
Network areas
Safes
Individual accounts
Which of the following PTA detections require the deployment of a Network Sensor or installing the PTA Agent on the domain controller? (Choose 2)
Suspected Credential Theft
Over-Pass-The Hash
Golden Ticket
Unmanaged Privileged Access
Which of the following PTA detections are included in the Core PAS offering? (Choose 2)
Suspected Credential Theft
Over-Pass-The Hash
Golden Ticket
Unmanaged Privileged Access
Which is the purpose of a linked account?
To ensure that a particular collection of accounts all have the same password.
To ensure a particular set of accounts all change at the same time.
To connect the CPM to a target system.
To allow the use of additional passwords within a password management process.
Users who have the ‘Access Safe without confirmation’ safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
True
False
Which credentials does CyberArk use when managing a target account?
Those of the service account for the CyberArk Password Manager service
A Domain Administrator account created for this purpose
The credentials of the target account
An account assigned by the Master Policy
What is the process to remove object level access control from a Safe?
Uncheck the 'Enable Object Level Access Control' box in the Safe Properties in PrivateArk.
Uncheck the 'Enable Object Level Access Control' on the Safe Details page in the PVWA.
Remove all ACLs from the Safe.
This cannot be done.
What is the purpose of the password verify process?
To test that CyberArk is storing accurate credentials for accounts.
To change the password of an account according to organizationally defined password rules.
To allow CyberArk to manage unknown or lost credentials.
To generate a new complex password.
What is the purpose of the password change process?
To test that CyberArk is storing accurate credentials for accounts.
To change the password of an account according to organizationally defined password rules.
To allow CyberArk to manage unknown or lost credentials.
To generate a new complex password.
What is the purpose of the password reconcile process?
To test that CyberArk is storing accurate credentials for accounts.
To change the password of an account according to organizationally defined password rules.
To allow CyberArk to manage unknown or lost credentials.
To generate a new complex password.
The Accounts Feed contains:
Accounts that were discovered by CyberArk in the last 30 days
Accounts that were discovered by CyberArk that have not yet been onboarded
All accounts added to the vault in the last 30 days
All users added to CyberArk in the last 30 days
A user has successfully conducted a short PSM session and logged off. However, the user cannot access the Monitoring tab to view the recordings. What is the issue?
The user is not a member of the Auditors group
The PSM service is not running
The user is not a member of the PVWAMonitor group
The user must login as PSMAdminConnect
When a DR vault server becomes an active vault, it will automatically fail back to the original state once the primary vault comes back online.
True, this is the default behaviour
False, it is not possible
True, if the AllowFailback setting is set to ‘yes’ in the padr.ini file
True, if the AllowFailback setting is set to ‘yes’ in the dbparm.ini file
You are onboarding an account that is not supported out of the box. What should you do first to obtain a platform to import?
Create a service ticket in the customer portal explaining the requirements of the custom platform.
Research common community portals like stackoverflow, reddit, github for an existing platform.
From the platforms page, uncheck the ‘Hide non-supported platforms’ checkbox and see if a platform meeting your needs appears.
Visit the CyberArk marketplace and search for a platform that meet your needs.
You have been asked to identify the up or down status of Vault services. Which CyberArk utility can you use to accomplish this task?
Vault Replicator
PAS Reporter
Remote Control Agent
Syslog
You are logging into CyberArk as the Master user to recover an orphaned safe. Which items are required to log in as Master?
Master CD, Master Password, console access to the Vault server, Private Ark Client
Operator CD, Master Password, console access to the PVWA server, PVWA access
Operator CD, Master Password, console access to the Vault server, Recover.exe
Master CD, Master Password, console access to the PVWA server, Recover.exe
Your organization requires all passwords to be rotated every 90 days. Where can you set this regulatory requirement?
Master Policy
Safe Templates
PVWAConfig.xml
Platform Configuration
To enable the Automatic response ‘Add to Pending’ within PTA when unmanaged credentials are found, what are the minimum permissions required by PTAUser for the PasswordManager_pending safe?
List Accounts, View Safe members, Add accounts (includes update properties), Update Account content, Update Account properties
List Accounts, Add account (includes update properties), Delete Accounts, Manage Safe
Add Account (includes update properties), Update Account content, Update Account properties, View Audit
View Accounts, Update Account content, Update Account properties, Access Safe without confirmation, Manage Safe, View audit
You have been asked to turn off the time access restrictions for a safe. Where is this setting found?
PrivateArk
RestAPI
Password Vault Web Access (PVWA)
Vault
What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
UnixPrompts.ini
Plink.exe
Dbparm.ini
PVConfig.xml
You have been asked to secure a set of shared accounts in CyberArk whose passwords will need to be used by end users. The account owner wants to be able to track who was using an account at any given moment. Which security configuration should you recommend?
Configure one-time passwords for the appropriate platform in Master Policy.
Configure shared account mode on the appropriate safe.
Configure both one-time passwords and exclusive access for the appropriate platform in Master Policy.
Configure object level access control on the appropriate safe.
In your organization the ‘click to connect’ button is not active by default. How can this feature be activated?
Policies > Master Policy > Allow EPV transparent connections > Inactive
Policies > Master Policy > Session Management > Require privileged session monitoring and isolation > Add Exception
Policies > Master Policy > Allow EPV transparent connections > Active
Policies > Master Policy > Password Management
Which PTA sensors are required to detect suspected credential theft?
Logs, Vault Logs
Logs, Network Sensor, Vault Logs
Logs, PSM Logs, CPM Logs
Logs, Network Sensor, EPM
Which CyberArk utility allows you to create lists of Master Policy Settings, owners and safes for output to text files or MSSQL databases?
Export Vault Data
Export Vault Information
PrivateArk Client
Privileged Threat Analytics
A Vault Administrator team member can log in to CyberArk, but for some reason, is not given Vault Admin rights. Where can you check to verify that the Vault Admins directory mapping points to the correct AD group?
PVWA > User Provisioning > LDAP Integration > Mapping Criteria
PVWA > User Provisioning > LDAP Integration > Map Name
PVWA > Administration > LDAP Integration > Mappings
PVWA > Administration > LDAP Integration > AD Groups
Which usage can be added as a service account platform?
Kerberos Tokens
IIS Application Pools
PowerShell Libraries
Loosely Connected Devices
When running a ‘Privileged Accounts Inventory’ Report through the Reports page in PVWA on a specific safe, which permission/s are required on that safe to show complete account inventory information?
List Accounts, View Safe Members
Manage Safe Owners
List Accounts, Access Safe without confirmation
Manage Safe, View Audit
What is the easiest way to duplicate an existing platform?
From PrivateArk, copy/paste the appropriate Policy.ini file; then rename it.
From the PVWA, navigate to the platforms page, select an existing platform that is similar to the new target account platform and then click Duplicate; name the new platform.
From PrivateArk, copy/paste the appropriate settings in PVConfiguration.xml; then update the policyName variable.
From the PVWA, navigate to the platforms page, select an existing platform that is similar to the new target account platform, manually update the platform settings and click ‘Save as’ INSTEAD of save to duplicate and rename the platform.
The Privileged Access Management solution provides an out-of-the-box target platform to manage SSH keys, called UNIX Via SSH Keys. How are these keys managed?
CyberArk stores Private keys in the Vault and updates Public keys on target systems.
CyberArk stores Public keys in the Vault and updates Private keys on target systems.
CyberArk does not store Public or Private keys and instead uses a reconcile account to create keys on demand.
CyberArk stores both Private and Public keys and can update target systems with either key.
You want to generate a license capacity report. Which tool accomplishes this?
Password Vault Web Access
PrivateArk Client
DiagnoseDB Report
RestAPI
How much disk space do you need on the server for a PAReplicate?
500 GB
1 TB
Same as disk size on Satellite Vault
Same as disk size on Primary Vault
Which of the following statements are NOT true when enabling PSM recording for a target Windows server? (Select all that apply)
The PSM software must be installed on the target server.
PSM must be enabled in the Master Policy (either directly, or through exception).
PSMConnect must be added as a local user on the target server.
RDP must be enabled on the target server.
Which Built-In group grants access to the ADMINISTRATION page?
PVWAMonitor
PVWAUsers
Auditors
Vault Admins
What is the purpose of the Allowed Safes parameter in a CPM policy? (Select all that apply)
To improve performance by reducing CPM workload.
To prevent accidental use of a policy in the wrong safe.
To allow users to access only the passwords they should be able to access.
To enforce Least Privilege in CyberArk.
You are creating a Dual Control workflow for a team’s safe. Which safe permissions must you grant to the Approvers group?
List accounts, Authorize account request
Retrieve accounts, Access Safe without confirmation
Retrieve accounts, Authorize account request
List accounts, Unlock accounts
You receive this error: ‘Error in changepass to user domain\user on domain server(\domain.(winRc=5) Access is denied.’ Which root cause should you investigate?
The account does not have sufficient permissions to change its own password.
The domain controller is unreachable.
The password has been changed recently and minimum password age is preventing the change.
The CPM service is disabled and will need to be restarted.
You are creating a shared safe for the help desk. What must be considered regarding the naming convention?
Ensure your naming convention is no longer than 20 characters
Combine environments, owners and platforms to minimize the total number of safes created
Safe owners should determine the safe name to enable them to easily remember it
The use of these characters V:*<>".| is not allowed
A user requested access to view a password secured by dual-control and is unsure who to contact to expedite the approval process. The Vault Admin has been asked to look at the account and identify who can approve their request. What is the correct location to identify users or groups who can approve?
PVWA> Policies > Access Control (Safes) > Safe Members > Workflow > Authorize Password Requests
PVWA> Account List > Edit > Show Advanced Settings > Dual Control > Direct Managers
PrivateArk > Admin Tools > Users and Groups > Auditors (Group Membership)
PVWA> Administration > Platform Configuration > Edit Platform > UI & Workflow > Dual Control> Approvers
Which built-in report from the reports page in PVWA displays the number of days until a password is due to expire?
Privileged Accounts Inventory
Privileged Accounts Compliance Status
Activity Log
Privileged Accounts CPM Status
To use PSM connections while in the PVWA, what are the minimum safe permissions a user or group will need?
List Accounts, Use Accounts
List Accounts, Use Accounts, Retrieve Accounts
Use Accounts
List Accounts, Use Accounts, Retrieve Accounts, Access Safe without confirmation
In a default CyberArk installation, which group must a user be a member of to view the reports page in PVWA?
PVWAMonitor
ReportUsers
PVWAReports
Operators
Which statement is correct concerning accounts that are discovered, but cannot be added to the Vault by an automated onboarding rule?
They are added to the Pending Accounts list and can be reviewed and manually uploaded.
They cannot be onboarded to the Password Vault
They must be uploaded using third party tools
They are not part of the Discovery Process
A new domain controller has been added to your domain. You need to ensure the CyberArk infrastructure can use the new domain controller for authentication. Which locations must you update?
On the Vault server in Windows\System32\Etc\Hosts and in the PVWA Application under Administration > LDAP Integration > Directories > Hosts
On the Vault server in Windows\System32\Etc\Hosts and on the PVWA server in Windows\System32\Etc\Hosts
In the Private Ark client under Tools > Administrative Tools > Directory Mapping
On the Vault server in the certificate store and on the PVWA server in the certificate store
If the AccountUploader Utility is used to create accounts with SSH keys, which parameter do you use to set the full or relative path of the SSH private key file that will be attached to the account?
KeyPath
KeyFile
ObjectName
Address
You are creating a new Rest API user that utilizes CyberArk Authentication. What is a correct process to provision this user?
Private Ark Client > Tools > Administrative Tools > Users and Groups > New > User
Private Ark Client > Tools > Administrative Tools > Directory Mapping > Add
PVWA > User Provisioning > LDAP Integration > Add Mapping
PVWA > User Provisioning > Users and Groups > New > User
Which command configures email alerts within PTA if settings need to be changed post install?
/opt/tomcat/utility/emailConfiguration.sh
/opt/PTA/emailConfiguration.sh
/opt/PTA/utility/emailConfig.sh
/opt/tomcat/utility/emailSetup.sh
Which permissions are needed for the Active Directory user required by the Windows Discovery process?
Domain Admin
LDAP Admin
Read/Write
Read
To manage automated onboarding rules, a CyberArk user must be a member of which group?
Vault Admins
CPM User
Auditors
Administrators
When onboarding multiple accounts from the Pending Accounts list, which associated setting must be the same across the selected accounts?
Platform
Connection Component
CPM
Vault
Your organization has a requirement to allow users to ‘check out passwords’ and connect to targets with the same account through the PSM. What needs to be configured in the Master policy to ensure this will happen?
Enforce check-in/check-out exclusive access = active; Require privileged session monitoring and isolation= active
Enforce check-in/check-out exclusive access = inactive; Require privileged session monitoring and isolation = inactive
Enforce check-in/check-out exclusive access = inactive; Require privileged session monitoring and isolation = inactive
Enforce check-in/check-out exclusive access = active; Record and save session activity = inactive
In PVWA, you are attempting to play a recording made of a session by user jsmith, but there is no option to ‘Fast Forward’ within the video. It plays and only allows you to skip between commands instead. You are also unable to download the video. What could be the cause?
Recording is of a PSM for SSH session
The browser you are using is out of date and needs an update to be supported
You do not have the ‘View Audit’ permission on the safe where the account is stored
You need to update the recorder settings in the platform to enable screen capture every 10000 ms or less
Your customer, ACME Corp, wants to store the Safes Data in Drive D instead of Drive C. Which file should you edit?
TSparm.ini
Vault.ini
DBparm.ini
User.ini
A new HTML5 Gateway has been deployed in your organization. Where do you configure the PSM to use the HTML5 Gateway?
Administration > Options > Privileged Session Management > Configured PSM Servers > Connection Details > Add PSM Gateway
Administration > Options > Privileged Session Management > Add Configured PSM Gateway Servers
Administration > Options > Privileged Session Management > Configured PSM Servers > Add PSM Gateway
Administration > Options > Privileged Session Management > Configured PSM Servers > Connection Details
You need to enable the PSM for all platforms. Where do you perform this task?
Platform Management > (Platform) > UI & Workflows
Master Policy > Session Management
Master Policy > Privileged Access Workflows
Administration > Options > Connection Components
Which option in the Private Ark client is used to update users Vault group memberships?
Update > General tab
Update > Authorizations tab
Update > Member Of tab
Update > Group tab
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
Operating System Username
Host IP Address
Client Hostname
Operating System Type (Linux/Windows/HP-UX)
Vault IP Address
Time Frame
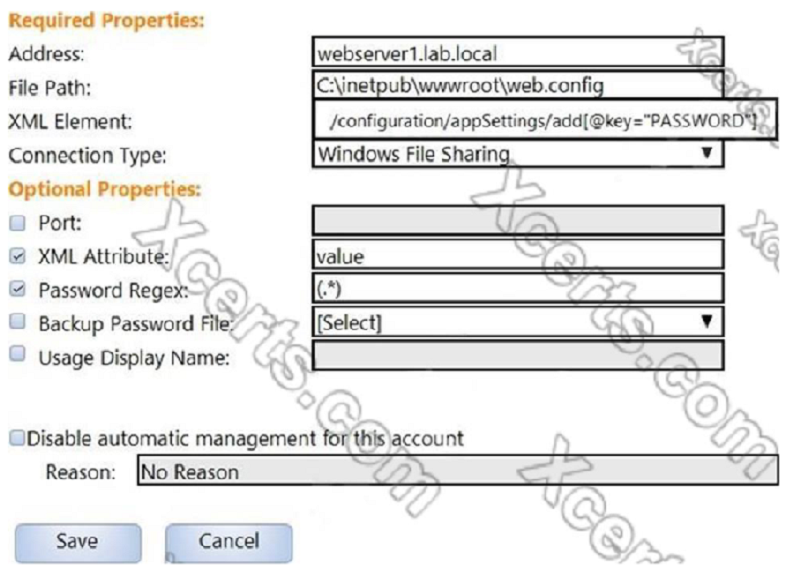
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password. What is the least intrusive way to accomplish this?
Use the ‘change’ button on the usage’s details page.
Use the ‘change’ button on the parent account’s details page.
Use the ‘sync’ button on the usage’s details page.
Use the ‘reconcile’ button on the parent account’s details page.
Users are unable to launch web type connection components from the PSM server. Your manager asked you to open the case with cyberark support. Which logs will help the cyberark support team debug the issue? Choose 3.
PSMConsole.log
PSMDebug.log
PSMTrace.log
PMConsole.log
ITAlog.log
The Password upload utility can be used to create safes.
True
False
The System safe allows access to the Vault configuration files.
True
False
As long as you are a member of the Vault Admins group you can grant any permission on any safe.
True
False
The password upload utility must run from the Central Policy Manager (CPM) server.
True
False
A user with administrative privileges to the vault can only grant other users’ privileges that he himself has.
True
False
Which of the following properties are mandatory when adding accounts from a file? Choose 3.
Safe name
Platform ID
All required properties specified in the platform
Username
Address
Hostname
Which of the following can be configured in the master policy? (Choose all that apply)
Dual control
One time password
Exclusive passwords
Password reconciliation
Ticketing integration
Required properties
Custom connection components
Password aging rules
Which of the following statements are NOT true when enabling PSM recording for a target Windows server? Choose all that apply.
The PSM software must be installed on the target server.
PSM must be enabled in the Master Policy (either directly, or through exception).
PSMConnect must be added as a local user on the target server.
RDP must be enabled on the target server.
Which item is an option for PSM recording customization?
Windows events text recorder with automatic play-back
Windows events text recorder and universal keystrokes recording simultaneously
Universal keystrokes text recorder with windows events text recorder disabled
Custom audio recording for windows events
In the Private Ark client, how do you add an LDAP group to a CyberArk group?
Select Update on the CyberArk group, and then click Add > LDAP Group
Select Update on the LDAP Group, and then click Add > LDAP Group
Select Member Of on the CyberArk group, and then click Add > LDAP Group
Select Member Of on the LDAP group, and then click Add > LDAP Group
For Digital Vault Cluster in a high availability configuration, how does the cluster determine if a node is down?
The heartbeat is no longer detected on the private network.
The shared storage array is offline.
An alert is generated in the Windows Event log.
The Digital Vault Cluster does not detect a node failure.
In a rule using ‘Privileged Session Analysis and Response’ in PTA, which session options are available to configure as responses to activities?
Suspend, Terminate, None
Suspend, Terminate, Lock Account
Pause, Terminate, None
Suspend, Terminate
You are onboarding 5,000 UNIX root accounts for rotation by the CPM. You discover that the CPM is unable to log in directly with the root account and will need to use a secondary account. How should this be configured to allow for password management using least privilege?
Configure each CPM to use the correct logon account.
Configure each CPM to use the correct reconcile account.
Configure the UNIX platform to use the correct logon account.
Configure the UNIX platform to use the correct reconcile account.
You received a notification from one of your CyberArk auditors that they are missing Vault level audit permissions. You confirmed that all auditors are missing the Audit Users Vault permission. Where do you update this permission for all auditors?
Private Ark Client > Tools > Administrative Tools > Directory Mapping > Vault Authorizations
Private Ark Client > Tools > Administrative Tools > Users and Groups > Auditors > Authorizations tab
PVWA User Provisioning > LDAP integration > Vault Auditors Mapping > Vault Authorizations
PVWA> Administration > Configuration Options > LDAP integration > Vault Auditors Mapping > Vault Authorizations
You need to recover an account localadmin02 for target server 10.0.123.73 stored in Safe Team1. What do you need to recover and decrypt the object? (Choose three.)
Recovery Private Key
Recover.exe
Vault data
Recovery Public Key
Server Key
Master Password
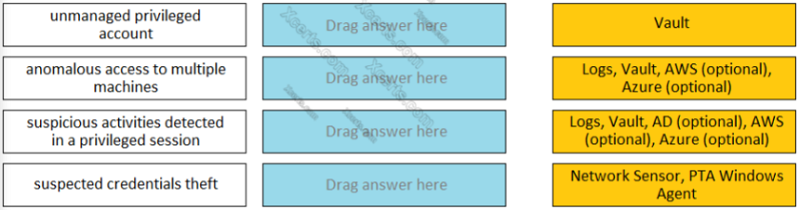
Match each PTA alert category with the PTA sensors that collect the data for it. Select and Place for UNMANAGED PRIVILEGED ACCOUNT
Vault
Log, Vault, AWS (Optional), Azure (Optional)
Log, Vault, AD (Optional), AWS (Optional), Azure (Optional)
Network Sensor, PTA Windows Agent

Match each PTA alert category with the PTA sensors that collect the data for it. Select and Place for ANOMALOUS ACCESS TO MULTIPLE
Vault
Log, Vault, AWS (Optional), Azure (Optional)
Log, Vault, AD (Optional), AWS (Optional), Azure (Optional)
Network Sensor, PTA Windows Agent

Match each PTA alert category with the PTA sensors that collect the data for it. Select and Place for SUSPICIOUS ACTIVITIES DETECTED IN A PRIVILEGED SESSION
Vault
Log, Vault, AWS (Optional), Azure (Optional)
Log, Vault, AD (Optional), AWS (Optional), Azure (Optional)
Network Sensor, PTA Windows Agent

Match each PTA alert category with the PTA sensors that collect the data for it. Select and Place for SUSPECTED CREDENTIAL THEFT
Vault
Log, Vault, AWS (Optional), Azure (Optional)
Log, Vault, AD (Optional), AWS (Optional), Azure (Optional)
Network Sensor, PTA Windows Agent
{"name":"PAM-DEF Practice", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Which CyberArk group does a user need to be part of to view recordings or live monitor sessions?, Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence., Which Automatic Remediation is configurable for a PTA detection of a “Suspected Credential Theft”?","img":"https://www.quiz-maker.com/3012/CDN/78-3629470/afaffaffafa.png?sz=1200"}
More Quizzes
Good habits or bad habits
1050
Final 6
10559
Understanding Sentinel Events Quiz
7423
Your birthday present!
So this year your birthday present is......(insert drum roll)......a weekend away with me!
Now I thought of planning everything but I thought it would be even better if you had a say in the matter. So, I have utilised this technology which will use your personality to decide what we do.
I love you!
520
Marine Corps Trivia - Test Your USMC Knowledge
201017921
Horror Movie Trivia with Answers - Free Online
201021785
Risk Management and Security Controls - Free
201017000
Schitt's Creek Trivia - Prove You're a Superfan
201021666
CPSI Practice Test - Free Playground Safety Inspector
201016587
What Should I Name My Cat? Take the Cat Name
201018436
What Gem Am I in Steven Universe? Free Personality
201016819
Funny Trivia Questions and Answers - 201+ Free
201015317