SYO-701v13.65
51 After a recent ransomware attack on a company's system, an administrator reviewed the log files. Which of the following control types did the administrator use?
A. Compensating
B. Detective
C. Preventive
D. Corrective
52.After a security awareness training session, a user called the IT help desk and reported a suspicious call. The suspicious caller stated that the Chief Financial Officer wanted credit card information in order to close an invoice. Which of the following topics did the user recognize from the training?
A. Insider threat
B. Email phishing
C. Social engineering
D. Executive whaling
53.Security controls in a data center are being reviewed to ensure data is properly protected and that human life considerations are included. Which of the following best describes how the controls should be set up?
A. Remote access points should fail closed.
B. Logging controls should fail open.
C. Safety controls should fail open.
D. Logical security controls should fail closed.
55 A company's legal department drafted sensitive documents in a SaaS application and wants to ensure the documents cannot be accessed by individuals in high-risk countries. Which of the following is the most effective way to limit this access?
A. Data masking
B. Encryption
C. Geolocation policy
D. Data sovereignty regulation
56 An enterprise has been experiencing attacks focused on exploiting vulnerabilities in older browser versions with well-known exploits. Which of the following security solutions should be configured to best provide the ability to monitor and block these known signature-based attacks?
A. ACL
B. DLP
C. IDS
D. IPS
57 Which of the following is a primary security concern for a company setting up a BYOD program?
A. End of life
B. Buffer overflow
C. VM escape
D. Jailbreaking
58 An employee clicked a link in an email from a payment website that asked the employee to update contact information. The employee entered the log-in information but received a "page not found" error message. Which of the following types of social engineering attacks occurred?
A. Brand impersonation
B. Pretexting
C. Typosquatting
D. Phishing
After a company was compromised, customers initiated a lawsuit. The company's attorneys have requested that the security team initiate a legal hold in response to the lawsuit. Which of the following describes the action the security team will most likely be required to take?
A. Retain the emails between the security team and affected customers for 30 days.
B. Retain any communications related to the security breach until further notice.
Retain any communications between security members during the breach response.
D. Retain all emails from the company to affected customers for an indefinite period of time.
Which of the following is the most likely to be used to document risks, responsible parties, and thresholds?
A. Risk tolerance
B. Risk transfer
C. Risk register
D. Risk analysis

Which of the following attacks is most likely occurring?
A. Password spraying
B. Account forgery
C. Pass-t he-hash
D. Brute-force
A company is planning to set up a SIEM system and assign an analyst to review the logs on a weekly basis. Which of the following types of controls is the company setting up?
A. Corrective
B. Preventive
C. Detective
D. Deterrent
An organization is struggling with scaling issues on its VPN concentrator and internet circuit due to remote work. The organization is looking for a software solution that will allow it to reduce traffic on the VPN and internet circuit, while still providing encrypted tunnel access to the data center and monitoring of remote employee internet traffic. Which of the following will help achieve these objectives?
A. Deploying a SASE solution to remote employees
B. Building a load-balanced VPN solution with redundant internet
C. Purchasing a low-cost SD-WAN solution for VPN traffic
D. Using a cloud provider to create additional VPN concentrators
After an audit, an administrator discovers all users have access to confidential data on a file server. Which of the following should the administrator use to restrict access to the data quickly?
A. Group Policy
B. Content filtering
C. Data loss prevention
D. Access control lists
65 One of a company's vendors sent an analyst a security bulletin that recommends a BIOS update. Which of the following vulnerability types is being addressed by the patch?
A. Virtualization
B. Firmware
C. Application
D. Operating system
66 While troubleshooting a firewall configuration, a technician determines that a "deny any" policy should be added to the bottom of the ACL. The technician updates the policy, but the new policy causes several company servers to become unreachable. Which of the following actions would prevent this issue?
A. Documenting the new policy in a change request and submitting the request to change management
B. Testing the policy in a non-production environment before enabling the policy in the production network
C. Disabling any intrusion prevention signatures on the 'deny any* policy prior to enabling the new policy
D. Including an 'allow any1 policy above the 'deny any* policy
An attacker posing as the Chief Executive Officer calls an employee and instructs the employee to buy gift cards. Which of the following techniques is the attacker using?
A. Smishing
B. Disinformation
C. Impersonating
D. Whaling
68 Which of the following is the most likely outcome if a large bank fails an internal PCI DSS compliance assessment?
A. Fines
B. Audit findings
C. Sanctions
D. Reputation damage
69 Which of the following would be the best way to handle a critical business application that is running on a legacy server?
A. Segmentation
B. Isolation
C. Hardening
D. Decommissioning
During a security incident, the security operations team identified sustained network traffic from a malicious IP address: 10.1.4.9. A security analyst is creating an inbound firewall rule to block the IP address from accessing the organization's network. Which of the following fulfills this request?
A. access-list inbound deny ig source 0.0.0.0/0 destination 10.1.4.9/32
B. access-list inbound deny ig source 10.1.4.9/32 destination 0.0.0.0/0
C. access-list inbound permit ig source 10.1.4.9/32 destination 0.0.0.0/0
D. access-list inbound permit ig source 0.0.0.0/0 destination 10.1.4.9/32
71 Which of the following is the most likely to be included as an element of communication in a security awareness program?
A. Reporting phishing attempts or other suspicious activities
B. Detecting insider threats using anomalous behavior recognition
C. Verifying information when modifying wire transfer data
D. Performing social engineering as part of third-party penetration testing
72 Which of the following describes a security alerting and monitoring tool that collects system, application, and network logs from multiple sources in a centralized system?
A. SIEM
B. DLP
C. IDS
D. SNMP

Which of the following is the best explanation for what the security analyst has discovered?
A. The user jsmith's account has been locked out.
B. A keylogger is installed on [smith's workstation
C. An attacker is attempting to brute force ismith's account.
D. Ransomware has been deployed in the domain.
Which of the following must be considered when designing a high-availability network?
A. Ease of recovery
B. Ability to patch
C. Physical isolation
D. Responsiveness
E. Attack surface
F. Extensible authentication
A company has begun labeling all laptops with asset inventory stickers and associating them with employee IDs. Which of the following security benefits do these actions provide? (Choose two.)
A. If a security incident occurs on the device, the correct employee can be notified.
B. The security team will be able to send user awareness training to the appropriate device.
C. Users can be mapped to their devices when configuring software MFA tokens.
D. User-based firewall policies can be correctly targeted to the appropriate laptops.
E. When conducting penetration testing, the security team will be able to target the desired laptops.
F. Company data can be accounted for when the employee leaves the organization.
76 A security administrator is deploying a DLP solution to prevent the exfiltration of sensitive customer data. Which of the following should the administrator do first?
A. Block access to cloud storage websites.
B. Create a rule to block outgoing email attachments
C. Apply classifications to the data.
D. Remove all user permissions from shares on the file server
A security manager created new documentation to use in response to various types of security incidents. Which of the following is the next step the manager should take?
A. Set the maximum data retention policy.
B. Securely store the documents on an air-gapped network
C. Review the documents' data classification policy.
D. Conduct a tabletop exercise with the team.
78 Which of the following is required for an organization to properly manage its restore process in the event of system failure?
A. IRP
B. DRP
C. RPO
D. SDLC
79 Which of the following practices would be best to prevent an insider from introducing malicious code into a company's development process?
A. Code scanning for vulnerabilities
B. Open-source component usage
C. Quality assurance testing
D. Peer review and approval
80 An organization is leveraging a VPN between its headquarters and a branch location. Which of the following is the VPN protecting?
A. Data in use
B. Data in transit
C. Geographic restrictions
D. Data sovereignty
81 A systems administrator set up a perimeter firewall but continues to notice suspicious connections between internal endpoints. Which of the following should be set up in order to mitigate the threat posed by the suspicious activity?
A. Host-based firewall
B. Web application firewall
C. Access control list
D. Application allow list
Users at a company are reporting they are unable to access the URL for a new retail website because it is flagged as gambling and is being blocked. Which of the following changes would allow users to access the site?
A. Creating a firewall rule to allow HTTPS traffic
B. Configuring the IPS to allow shopping
C. Tuning the DLP rule that detects credit card data
D. Updating the categorization in the content filter
83 A software development manager wants to ensure the authenticity of the code created by the company. Which of the following options is the most appropriate?
A. Testing input validation on the user input fields
B. Performing code signing on company-developed software
C. Performing static code analysis on the software
D. Ensuring secure cookies are use
84 A security engineer is implementing FDE for all laptops in an organization. Which of the following are the most important for the engineer to consider as part of the planning process? (Select two).
A. Key escrow
B. TPM presence
C. Digital signatures
D. Data tokenization
E. Public key management
F.Certificate authority linking
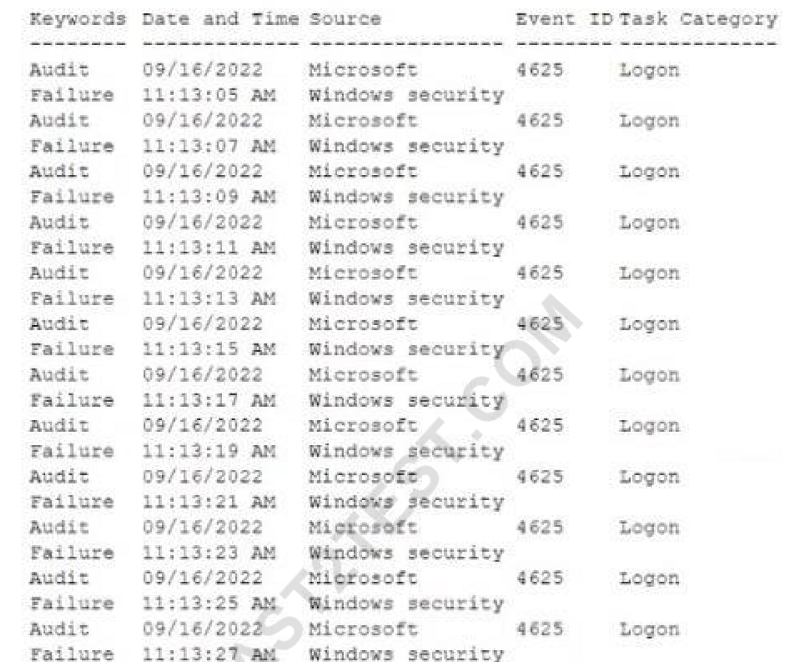
Which of the following best describes the action captured in this log file?
A. Brute-force attack
B. Privilege escalation
C. Failed password audit
D. Forgotten password by the user
86 Which of the following factors are the most important to address when formulating a training curriculum plan for a security awareness program? (Select two).
A. Channels by which the organization communicates with customers
B. The reporting mechanisms for ethics violations
C. Threat vectors based on the industry in which the organization operates
D. Secure software development training for all personnel
E. Cadence and duration of training events
87 A security analyst is reviewing alerts in the SIEM related to potential malicious network traffic coming from an employee's corporate laptop. The security analyst has determined that additional data about the executable running on the machine is necessary to continue the investigation. Which of the following logs should the analyst use as a data source?
A. Application
B. IPS/IDS
C. Network
D.Endpoint
88 Which of the following should a security administrator adhere to when setting up a new set of firewall rules?
A. Disaster recovery plan
B. Incident response procedure
C. Business continuity plan
D. Change management procedure
89 Which of the following threat actors is the most likely to be hired by a foreign government to attack critical systems located in other countries?
A. Hacktivist
B. Whistleblower
C. Organized crime
D. Unskilled attacker
90 A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
A. Changing the remote desktop port to a non-standard number
Setting up a VPN and placing the jump server inside the firewall
C. Using a proxy for web connections from the remote desktop server
D. Connecting the remote server to the domain and increasing the password length
91 A systems administrator works for a local hospital and needs to ensure patient data is protected and secure. Which of the following data classifications should be used to secure patient data?
A. Private
B. Critical
C. Sensitive
D. Public
92 Which of the following vulnerabilities is associated with installing software outside of a manufacturer's approved software repository?
A. Jailbreaking
B. Memory injection
C. Resource reuse
D. Side loading
93 A security analyst locates a potentially malicious video file on a server and needs to identify both the creation date and the file's creator. Which of the following actions would most likely give the security analyst the information required?
A. Obtain the file's SHA-256 hash.
B. Use hexdump on the file's contents.
C.Check endpoint logs.
D. Query the file's metadata.
94 A cyber operations team informs a security analyst about a new tactic malicious actors are using to compromise networks. SIEM alerts have not yet been configured. Which of the following best describes what the security analyst should do to identify this behavior?
A. [Digital forensics
B. E-discovery
C. Incident response
D. Threat hunting
95 Which of the following enables the use of an input field to run commands that can view or manipulate data?
A. Cross-site scripting
B.Side loading
C. Buffer overflow
D. SQL Injection
96 An administrator finds that all user workstations and servers are displaying a message that is associated with files containing an extension of .ryk. Which of the following types of infections is present on the systems?
A. Virus
B.Trojan
C. Spyware
D. Ransomware
97 Which of the following best practices gives administrators a set period to perform changes to an operational system to ensure availability and minimize business impacts?
A. Impact analysis
B. Scheduled downtime
C. Backout plan
D. Change management boards
A Chief Information Security Officer wants to monitor the company's servers for SQLi attacks and allow for comprehensive investigations if an attack occurs. The company uses SSL decryption to allow traffic monitoring. Which of the following strategies would best accomplish this goal?
A.Logging all NetFlow traffic into a SIEM
B. Deploying network traffic sensors on the same subnet as the servers
C. Logging endpoint and OS-specific security logs
D.Enabling full packet capture for traffic entering and exiting the servers
99 A systems administrator is working on a solution with the following requirements: * Provide a secure zone. * Enforce a company-wide access control policy. * Reduce the scope of threats. Which of the following is the systems administrator setting up?
A. Zero Trust
B. AAA
C. Non-repudiation
D. CIA
100 An enterprise is trying to limit outbound DNS traffic originating from its internal network. Outbound DNS requests will only be allowed from one device with the IP address 10.50.10.25. Which of the following firewall ACLs will accomplish this goal?
A. Access list outbound permit 0.0.0.0/0 0.0.0.0/0 port 53 Access list outbound deny 10.50.10.25/32 0.0.0.0/0 port 53
B. Access list outbound permit 0.0.0.0/0 10.50.10.25/32 port 53 Access list outbound deny 0.0.0.0/0 0.0.0.0/0 port 53
Access list outbound permit 0.0.0.0/0 0.0.0.0/0 port 53 Access list outbound deny 0.0.0.0/0 10.50.10.25/32 port 53
Access list outbound permit 0.0.0.0/0 0.0.0.0/0 port 53 Access list outbound deny 0.0.0.0/0 10.50.10.25/32 port 53
{"name":"SYO-701v13.65", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"51 After a recent ransomware attack on a company's system, an administrator reviewed the log files. Which of the following control types did the administrator use?, 52.After a security awareness training session, a user called the IT help desk and reported a suspicious call. The suspicious caller stated that the Chief Financial Officer wanted credit card information in order to close an invoice. Which of the following topics did the user recognize from the training?, 53.Security controls in a data center are being reviewed to ensure data is properly protected and that human life considerations are included. Which of the following best describes how the controls should be set up?","img":"https://www.quiz-maker.com/3012/CDN/97-4755899/screenshot-2024-01-02-at-10-53-16-am.png?sz=1200-00000000000973401734"}
More Quizzes
Get yourself a crush
10515
EPPD's World Bee Day 2020 Quiz
1050
How well do you know you sister?
1050
Carbohydrates and Nutrition Quiz
9440
Fallout 4 Companion - Which Wasteland Partner Are You?
201017660
Electron Transport Chain - Free ETC Biology Practice
201019810
Glee - Test Your Gleek Knowledge
201020699
What Kind of Bike Should I Get? - Find Your Ride
201017868
Which Disney Prince Is Your Soulmate? - Free
201017939
OKR, SOW & More - Business Acronyms (Free)
201015902
The Good Doctor - How Well Do You Know the Show?
201018156
East Asia Physical Map - Free Online Practice
201020291