CIS 31-60

IPv6 Networking Knowledge Quiz
Test your understanding of IPv6 networking concepts with this comprehensive quiz! Whether you're preparing for a certification or just want to enhance your knowledge, this quiz covers fundamental aspects of IPv6, ICMP, DHCP, and other networking principles.
Challenge yourself and discover:
- Multiple choice questions on IPv6 configurations.
- Practical scenarios to apply your knowledge.
- Real-world networking challenges.
32 How many bits make up the single IPv6 hextet :10CD:?
4
8
16
32
33 What is the effect of configuring the ipv6 unicast-routing command on a router?
To assign the router to the all-nodes multicast group
To enable the router as an IPv6 router
To permit only unicast packets on the router
To prevent the router from joining the all-routers multicast group
34 Which group of IPv6 addresses cannot be allocated as a host source address
FEC0::/10
FDFF::/7
FEBF::/10
FF00::/8
35 What is the purpose of ICMP messages?
To inform routers about network topology changes
To ensure the delivery of an IP packet
To provide feedback of IP packet transmissions
To monitor the process of a domain name to IP address resolution
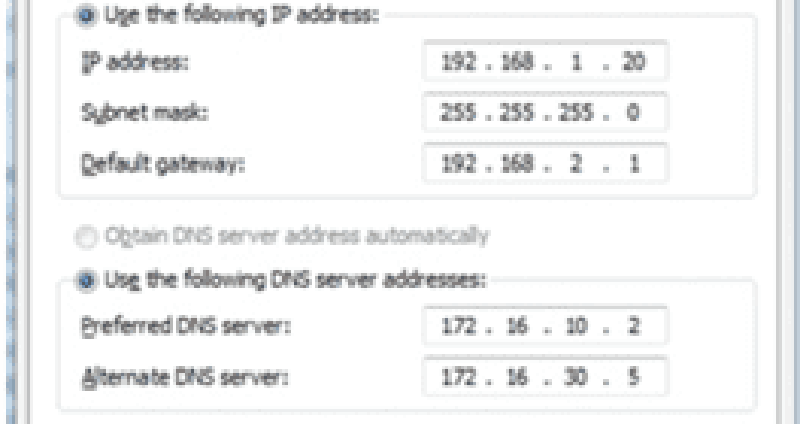
36 Refer to the exhibit. A technician has configured a user workstation with the IP address and default subnet masks that are shown. Although the user can access all local LAN resources, the user cannot access any Internet sites by using either FQDN or IP addresses. Based upon the exhibit, what could account for this failure?
The DNS server addresses are incorrect.
The default gateway address in incorrect.
The wrong subnet mask was assigned to the workstation.
The workstation is not in the same network as the DNS servers.
37 A network administrator needs to monitor network traffic to and from servers in a data center. Which features of an IP addressing scheme should be applied to these devices?
Random static addresses to improve security
Addresses from different subnets for redundancy
Predictable static IP addresses for easier identification
Dynamic addresses to reduce the probability of duplicate addresses
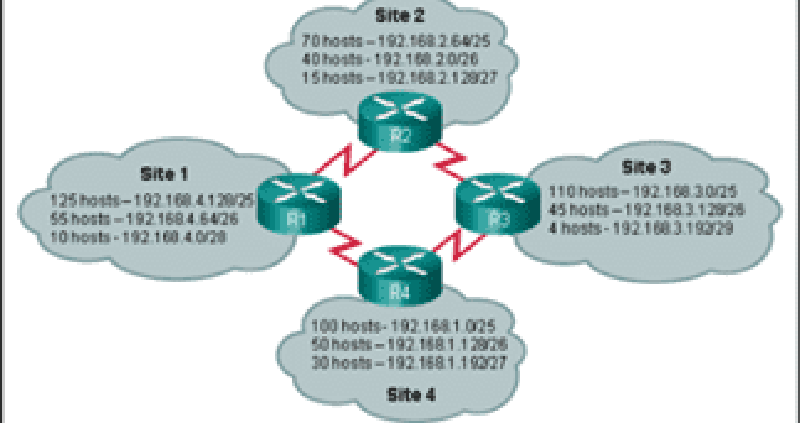
38 Refer to the exhibit. Which IP addressing scheme should be changed?
Site1
Site2
Site3
Site4
39 Which two notations are useable nibble boundaries when subnetting in IPv6? (Choose two.)
/62
/64
/66
/68
/70
40 A host PC has just booted and is attempting to lease an address through DHCP. Which two messages will the client typically broadcast on the network? (Choose two.
DHCPDISCOVER
DHCPOFFER
DHCPREQUEST
DHCPACK
DHCPNACK
41 What is the purpose of the network security accounting fun
To require users to prove who they are
To determine which resources a user can access
To keep track of the actions of a user
To provide challenge and response questions
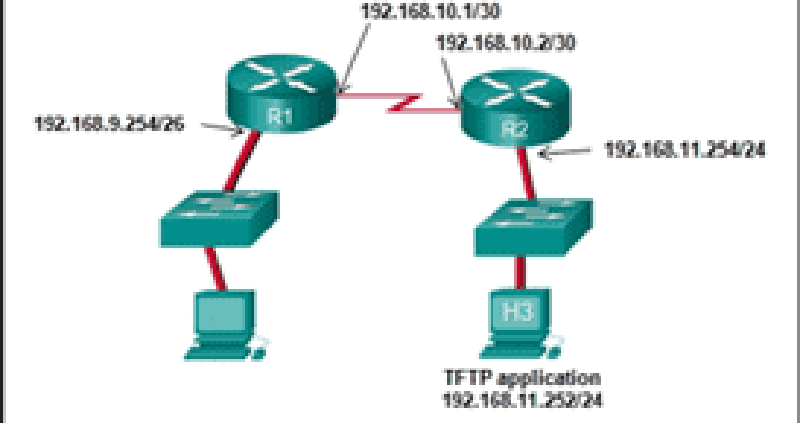
42 Refer to the exhibit. The network administrator enters these commands into the R1 router: R1# copy running-config tftp Address or name of remote host [ ]? When the router prompts for an address or remote host name, what IP address should the administrator enter at the prompt?
192.168.9.254
192.168.10.1
192.168.10.2
192.168.11.252
192.168.11.254
44 What two preconfigured settings that affect security are found on most new wireless routers? (Choose two.)
Broadcast SSID
MAC filtering enabled
WEP encryption enabled
PSK authentication required
Default administrator password
45 Which type of wireless security generates dynamic encryption keys each time a client associates with an AP?
EAP
PSK
WEP
WPA
46 Fill in the blank. ....* is a best-effort, connectionless application layer protocol that is used to transfer files.
47 Which two components are necessary for a wireless client to be installed on a WLAN? (Choose two.)
Media
Wireless NIC
Custom adapter
Crossover cable
Wireless bridge
Wireless client software

48 Consider the following range of addresses:
The prefix-length for the range of addresses is /60
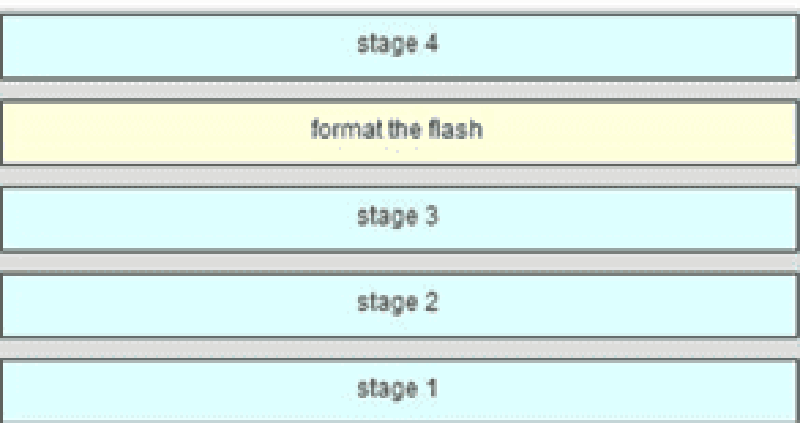
49 Match the phases to their correct stage in the router bootup process. (Not all options are used.)
50 A host is accessing an FTP server on a remote network. Which three fun
Regenerating data signals
Acting as a client or a server
Providing a channel over which messages travel
Applying security settings to control the flow of data
Notifying other devices when errors occur
Serving as the source or destination of the messages
51 When is a dial-up connection used to connect to an ISP?
When a cellular telephone provides the service
When a high-speed connection is provided over a cable TV network
When a satellite dish is used
When a regular telephone line is used
52 On a school network, students are surfing the web, searching the library database, and attending an audio conference with their sister school in Japan. If network traffic is prioritized with QoS, how will the traffic be classified from highest priority to lowest priority?
Audio conference, database, HTTP
Database, HTTP, audio conference
Audio conference, HTTP, database
Database, audio conference, HTTP
53 During normal operation, from which location do most Cisco routers run the IOS?
RAM
Flash
NVRAM
Disk drive
54 Which keys act as a hot key combination that is used to interrupt an IOS process?
Ctrl-Shift-X
Ctrl-Shift-6
Ctrl-Z
Ctrl-C
55 Refer to the exhibit. An administrator wants to change the name of a brand new switch, using the hostname command as shown. What prompt will display after the command is issued?? console: Switch(config) # hostname HR Switch
HR Switch(config)#?
Switch(config)#?
HRSwitch(config)#?
HR(config)#?
Switch#
56 A technician uses the ping 127.0.0.1 command. What is the technician testing?
The TCP/IP stack on a network host
Connectivity between two adjacent Cisco devices
Connectivity between a PC and the default gateway
Connectivity between two PCs on the same network
Physical connectivity of a particular PC and the network
57 What is the correct order for PDU encapsulation?
0%
0
58 Which device should be used for enabling a host to communicate with another host on a different network?
Switch
Hub
Router
Host
59 A network technician is measuring the transfer of bits across the company backbone for a mission critical application. The technician notices that the network throughput appears lower than the bandwidth expected. Which three factors could influence the differences in throughput? (Choose three.)
The amount of traffic that is currently crossing the network
The sophistication of the encapsulation method applied to the data
The type of traffic that is crossing the network
The latency that is created by the number of network devices that the data is crossing
The bandwidth of the WAN connection to the Internet
The reliability of the gigabit Ethernet infrastructure of the backbone
60 Which characteristics describe fiber optic cable? (Choose two.)
It is not affected by EMI or RFI.
Each pair of cables is wrapped in metallic foil.
It combines the technique of cancellation, shielding and twisting to protect data.
It has a maximum speed of 100 Mbps.
It is the most expensive type of LAN cabling.
{"name":"CIS 31-60", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"Test your understanding of IPv6 networking concepts with this comprehensive quiz! Whether you're preparing for a certification or just want to enhance your knowledge, this quiz covers fundamental aspects of IPv6, ICMP, DHCP, and other networking principles.Challenge yourself and discover:Multiple choice questions on IPv6 configurations.Practical scenarios to apply your knowledge.Real-world networking challenges.","img":"https:/images/course2.png"}
More Quizzes
Geggegeeg
1478
CCNA 2 SRWE 1-4
673425
Q9 Group Sales Tool POC Sales Feedback Survey
1780
Filing Statuses, Dependents, & Deductions
1050
Smart Brain Test - Free IQ & Logic Online
201021971
Equivalent Expressions - 50 Free Algebra Questions
201017503
How Old Is Alice Cullen? Take the Twilight - Free
201022864
1995 - How Well Do You Remember the Year?
201022093
Subject-Verb Agreement Practice Test - Free Online
201018422
The Treasure of Lemon Brown - Free With Answers
201018732
Misophonia Test - Free to Identify Sound Triggers
201016476
Lymphatic System - Free Immune System Practice
201016258
